Manually Configure a SAML Identity Provider Through the Common Services
Table of Contents
Expand all | Collapse all
- Get Started with Common Services: Identity & Access
-
- Add an Identity Federation
- Manually Configure a SAML Identity Provider
- Upload SAML Identity Provider Metadata
- Get the URL of a SAML Identity Provider
- Clone SAML Identity Provider Configuration
- Add or Delete an Identity Federation Owner
- Configure Palo Alto Networks as a Service Provider
- Delete an Identity Federation
- Map a Tenant for Authorization
- Update Tenant Mapping for Authorization
- PAN Resource Name Mapping Properties
- Manage Single Tenant Transition to Multitenant
- Release Updates
Manually Configure a SAML Identity Provider Through the Common Services
Learn how to manually configure a SAML identity provider
through Common Services.
After you add an identity federation and
you choose to configure a Security Assertion Markup Language (SAML)
provider manually, you complete the following steps.
- Use one of the various ways to access Common ServicesIdentity & Access.Manually configure a SAML provider from Common ServicesIdentity & AccessIdentity Federations.
![]() Select Configure Identity Provider.
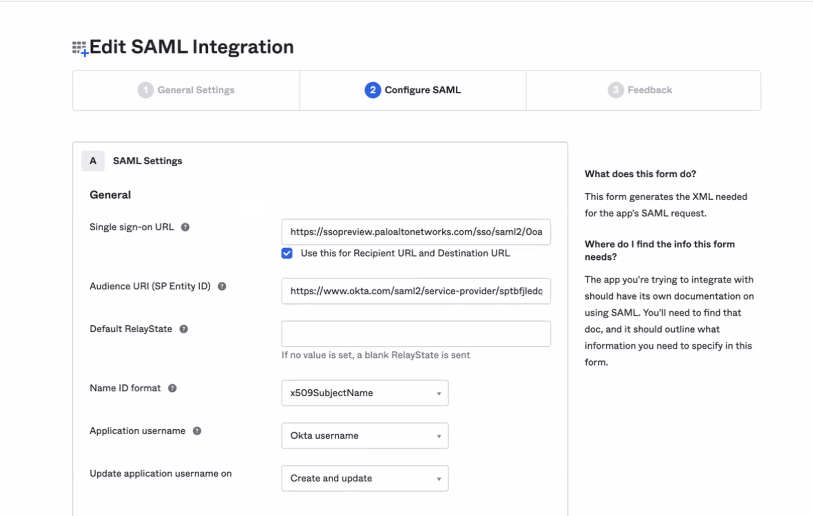
Select Configure Identity Provider.![]() Select Enter ManuallyNext.Go to your identity provider’s console, download the certificate, and take note of all the provider’s details. The console details look similar to the following, but all providers are slightly different.
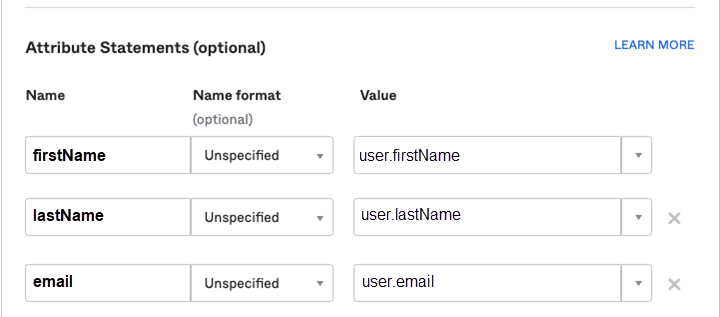
Select Enter ManuallyNext.Go to your identity provider’s console, download the certificate, and take note of all the provider’s details. The console details look similar to the following, but all providers are slightly different.![]() In your identity provider’s console, set up the Attribute Statements for firstName of user.firstName, lastName of user.lastName, and email of user.email. Without them, you will only see a blank name in the hub or Strata Cloud Manager. The console details look similar to the following, but all providers are slightly different.
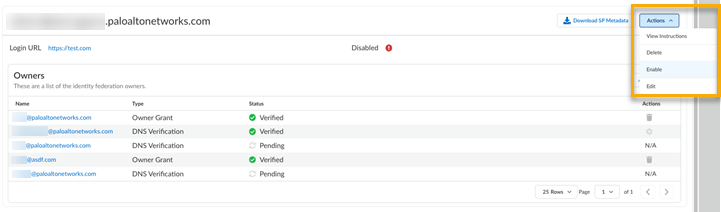
In your identity provider’s console, set up the Attribute Statements for firstName of user.firstName, lastName of user.lastName, and email of user.email. Without them, you will only see a blank name in the hub or Strata Cloud Manager. The console details look similar to the following, but all providers are slightly different.![]() Upload Certificate for your identity provider certificate. Use .crt files only.Enter your Identity Provider ID.Enter your Identity Provider SSO URL.Select Next.The Configure Identity Provider button is replaced with the Login URL that you configured. The Login URL is how Palo Alto Networks knows where to send the user when they log in. This is disabled by default. Select ActionsEnable.
Upload Certificate for your identity provider certificate. Use .crt files only.Enter your Identity Provider ID.Enter your Identity Provider SSO URL.Select Next.The Configure Identity Provider button is replaced with the Login URL that you configured. The Login URL is how Palo Alto Networks knows where to send the user when they log in. This is disabled by default. Select ActionsEnable.![]()