Device Security
Send Vulnerabilities to SIEM
Table of Contents
Expand All
|
Collapse All
Device Security Docs
Send Vulnerabilities to SIEM
Manually send device vulnerabilities from Device Security through Cortex XSOAR
to SIEM.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
One of the following subscriptions:
One of the following Cortex XSOAR setups:
|
From Device Security, send a device vulnerability to SIEM from the
Vulnerability Details page. You can also do this in the Actions menu in the
Vulnerabilities section on the Device Details page.
By integrating Device Security through Cortex XSOAR with a third-party SIEM server,
XSOAR automatically exports data about devices, security alerts, and device
vulnerability in periodic incremental updates from Device Security to SIEM. Therefore,
it might be unnecessary to send a vulnerability to SIEM manually. However, if you
haven’t performed a bulk export to SIEM and you want to send a device vulnerability
that wasn’t exported through the automatic incremental update process, then you can
use this option to send it manually.
Strata Cloud Manager
Manually send device vulnerabilities from Device Security in Strata Cloud Manager
through Cortex XSOAR to SIEM.
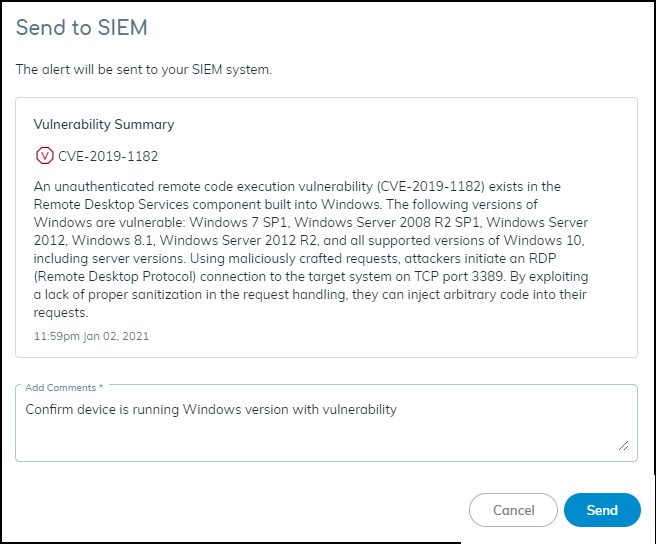
- Select a vulnerability to investigate.Log in to Device Security in Strata Cloud Manager, click RisksVulnerabilities, click a vulnerability name, and then select the check box of an active instance that you want to investigate.The Send to SIEM panel appears.
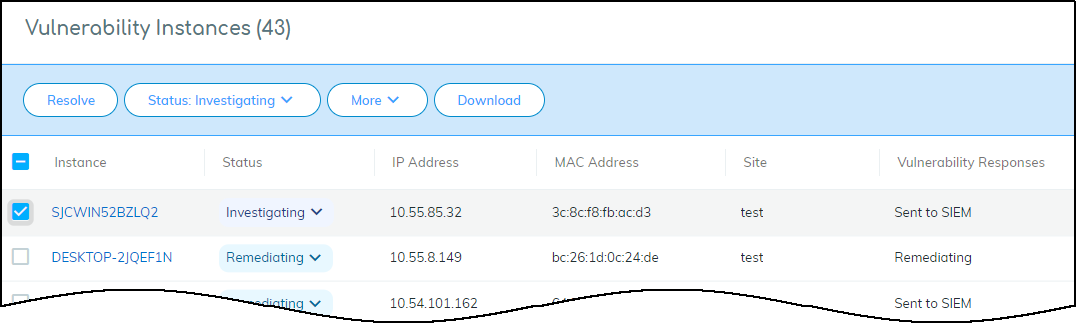
![]() Add a comment.After you enter a comment, the Send button changes from gray to blue, indicating that you can proceed.Click Send.After you click Send, a link appears. When you click it, a new browser window opens to the Cortex XSOAR playbook for this action.To confirm that the vulnerability was sent, click the link to the XSOAR playbook for this action.For the link in Device Security to open the corresponding playbook in Cortex XSOAR, you must already be logged in to your XSOAR instance before clicking it.The green boxes in the playbook indicate that a particular step was successfully performed. Following the path through the playbook gives you feedback about whether an action was carried out successfully or, if not, where the process changed course.Also, the action “Sent to SIEM” appears in the Vulnerability Responses column. If you don’t see this column, click the Columns icon () and select Vulnerability Responses.
Add a comment.After you enter a comment, the Send button changes from gray to blue, indicating that you can proceed.Click Send.After you click Send, a link appears. When you click it, a new browser window opens to the Cortex XSOAR playbook for this action.To confirm that the vulnerability was sent, click the link to the XSOAR playbook for this action.For the link in Device Security to open the corresponding playbook in Cortex XSOAR, you must already be logged in to your XSOAR instance before clicking it.The green boxes in the playbook indicate that a particular step was successfully performed. Following the path through the playbook gives you feedback about whether an action was carried out successfully or, if not, where the process changed course.Also, the action “Sent to SIEM” appears in the Vulnerability Responses column. If you don’t see this column, click the Columns icon () and select Vulnerability Responses.![]()
![]()
Legacy IoT Security
Manually send device vulnerabilities from the Device Security portal
through Cortex XSOAR to SIEM.
- Select a vulnerability to investigate.Log in to the Device Security portal, click VulnerabilitiesVulnerability OverviewAll Vulnerabilities, click a vulnerability name, and then select the check box of an active instance that you want to investigate.The Send to SIEM panel appears.
![]() Add a comment.After you enter a comment, the Send button changes from gray to blue, indicating that you can proceed.Click Send.After you click Send, a link appears. When you click it, a new browser window opens to the Cortex XSOAR playbook for this action.To confirm that the vulnerability was sent, click the link to the XSOAR playbook for this action.For the link in Device Security to open the corresponding playbook in Cortex XSOAR, you must already be logged in to your XSOAR instance before clicking it.The green boxes in the playbook indicate that a particular step was successfully performed. Following the path through the playbook gives you feedback about whether an action was carried out successfully or, if not, where the process changed course.Also, the action “Sent to SIEM” appears in the Vulnerability Responses column. If you don’t see this column, click the Columns icon () and select Vulnerability Responses.
Add a comment.After you enter a comment, the Send button changes from gray to blue, indicating that you can proceed.Click Send.After you click Send, a link appears. When you click it, a new browser window opens to the Cortex XSOAR playbook for this action.To confirm that the vulnerability was sent, click the link to the XSOAR playbook for this action.For the link in Device Security to open the corresponding playbook in Cortex XSOAR, you must already be logged in to your XSOAR instance before clicking it.The green boxes in the playbook indicate that a particular step was successfully performed. Following the path through the playbook gives you feedback about whether an action was carried out successfully or, if not, where the process changed course.Also, the action “Sent to SIEM” appears in the Vulnerability Responses column. If you don’t see this column, click the Columns icon () and select Vulnerability Responses.![]()
![]()