Network Security
Troubleshoot Expired Server Certificates (PAN-OS)
Table of Contents
Expand All
|
Collapse All
Network Security Docs
Troubleshoot Expired Server Certificates (PAN-OS)
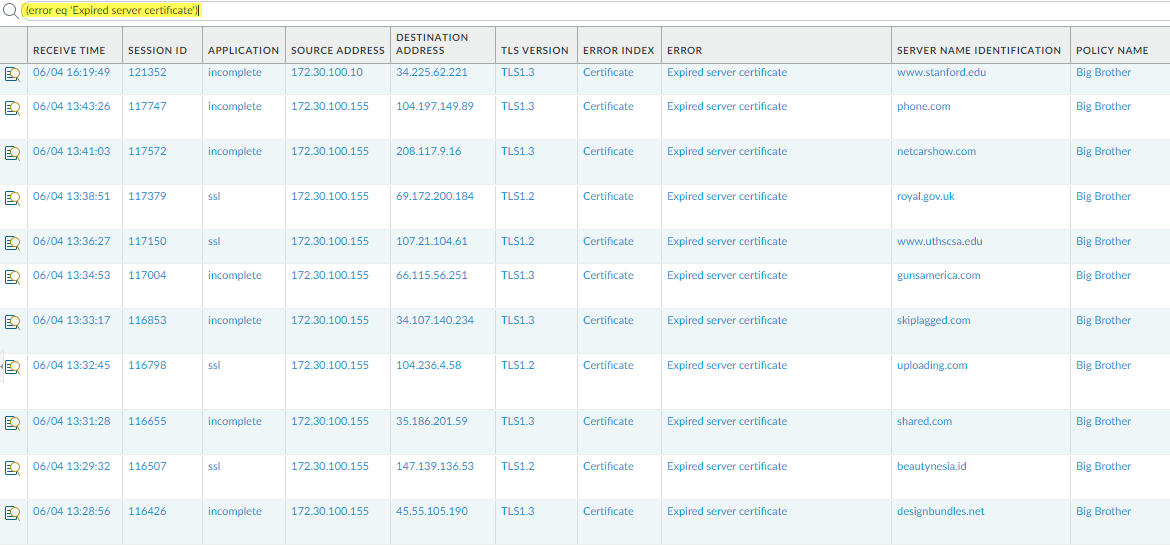
- Filter the decryption logs for expired certificates using the query (error eq ‘Expired server certificate’).
![]() This query identifies servers that generate Expired server certificate errors. The NGFW blocks access to these servers because of the expired certificate.(Optional) Double-check the certificate expiration date at the Qualys SSL Labs site.Enter the hostname of the server (Server Name Identification column of the decryption log) in the Hostname field and Submit it to view certificate information for the host.Filter the decryption logs (MonitorLogsDecryption) for certificates that will expire soon using a query that identifies upcoming certificate end dates.For example, if today’s date is February 1, 2020, and you want to give yourself two months to evaluate and prepare in case sites don’t update their certificates, query the decryption logs for certificates that expire April 1, 2020 or earlier (notafter leq ‘2020/4/01’)):
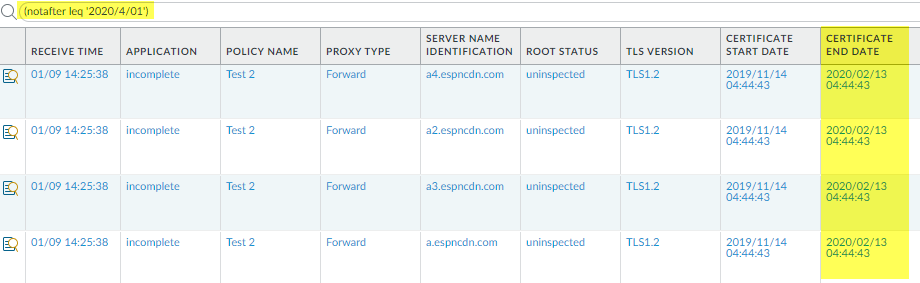
This query identifies servers that generate Expired server certificate errors. The NGFW blocks access to these servers because of the expired certificate.(Optional) Double-check the certificate expiration date at the Qualys SSL Labs site.Enter the hostname of the server (Server Name Identification column of the decryption log) in the Hostname field and Submit it to view certificate information for the host.Filter the decryption logs (MonitorLogsDecryption) for certificates that will expire soon using a query that identifies upcoming certificate end dates.For example, if today’s date is February 1, 2020, and you want to give yourself two months to evaluate and prepare in case sites don’t update their certificates, query the decryption logs for certificates that expire April 1, 2020 or earlier (notafter leq ‘2020/4/01’)):![]() The Certificate End Date column shows the exact date on which the certificate expires.Determine the action to take for sites with expired certificates.
The Certificate End Date column shows the exact date on which the certificate expires.Determine the action to take for sites with expired certificates.- If you don’t need to access the site for business purposes, the safest action is to continue blocking access to the site.
- If you need to access the site for business purposes, take one of the following actions:
- Contact the administrator of the site with the expired certificate and notify them that they need to update or renew their certificate.
- Create a decryption policy rule that targets sites with expired certificates that you need for business purposes. Then, create and attach a decryption profile that allows access to sites with expired certificates. Apply the rule exclusively to business-critical sites. As sites update their certificate, promptly remove them from the rule.