Network Security
PAN-OS & Panorama
Table of Contents
Expand All
|
Collapse All
Network Security Docs
PAN-OS & Panorama
Leveraging a Feed URL as the source in an EDL allows for dynamic enforcement of SaaS
application traffic without the need for you to host and maintain your own EDL source.
- Visit the EDL Hosting Service and identify the Feed URL for your SaaS application.Review the Microsoft 365 documentation for more information which Feed URL is best for your use case. Additionally, consider the SaaS application and location of users accessing the SaaS application when identifying a Feed URL to. For example, if you have a branch in Germany that only needs to access Exchange Online, select a Feed URL from theService Area: Exchange OnlineforGermany.For a policy-based forwarding policy rule, use an IP-based Feed URL.
- (Best Practices) Create a certificate profile to authenticate the EDL Hosting Service.
- Download the GlobalSign Root R1 certificate.
- Import the GlobalSign Root R1 certificate.
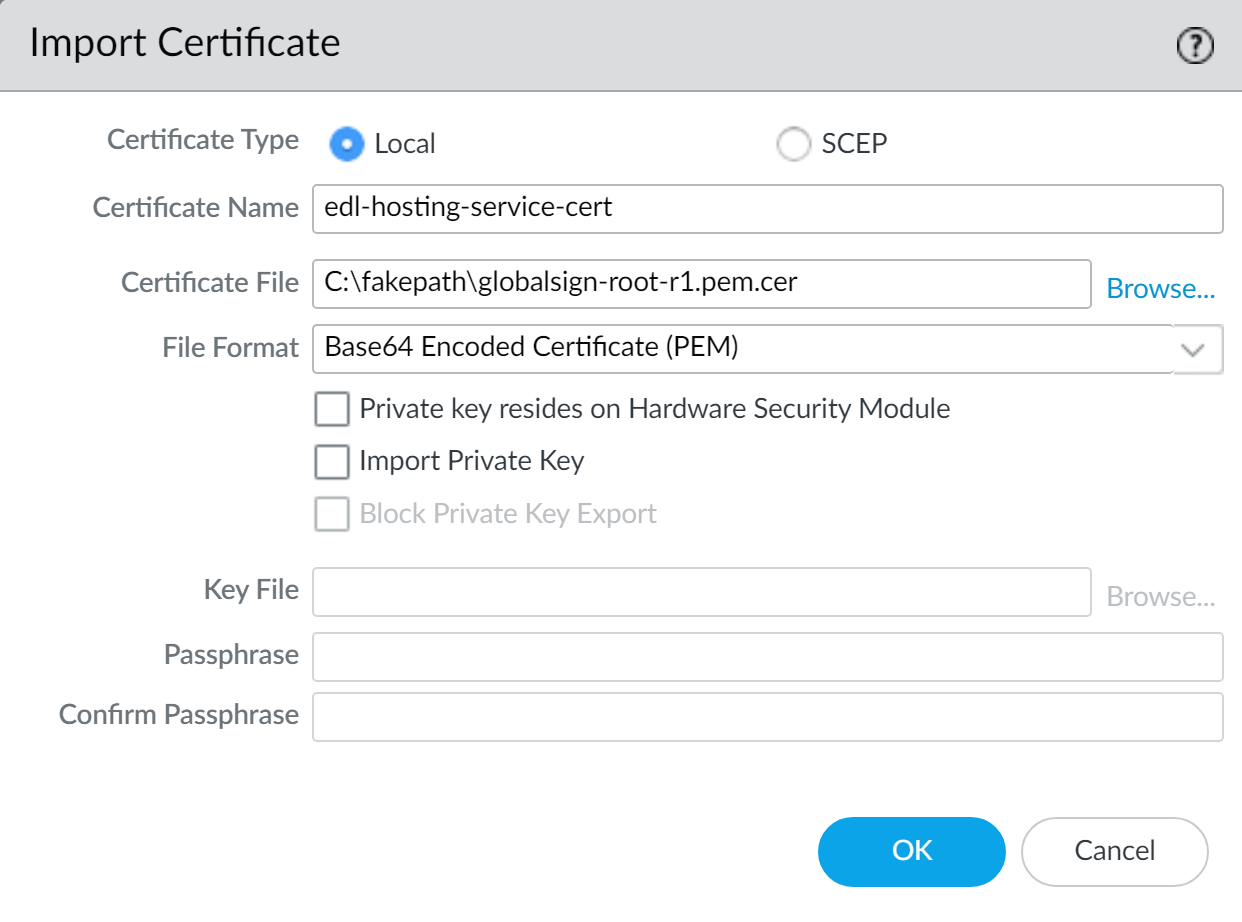
- SelectandDeviceCertificate ManagementCertificatesImporta new certificate.
- ForCertificate Type, selectLocal.
- Enter a descriptiveCertificate Name.
- For theCertificate File, selectBrowseand select the certificate you converted in the previous step.
- For theFile Format, selectBase64 Encoded Certificate (PEM).
- ClickOK.
![]()
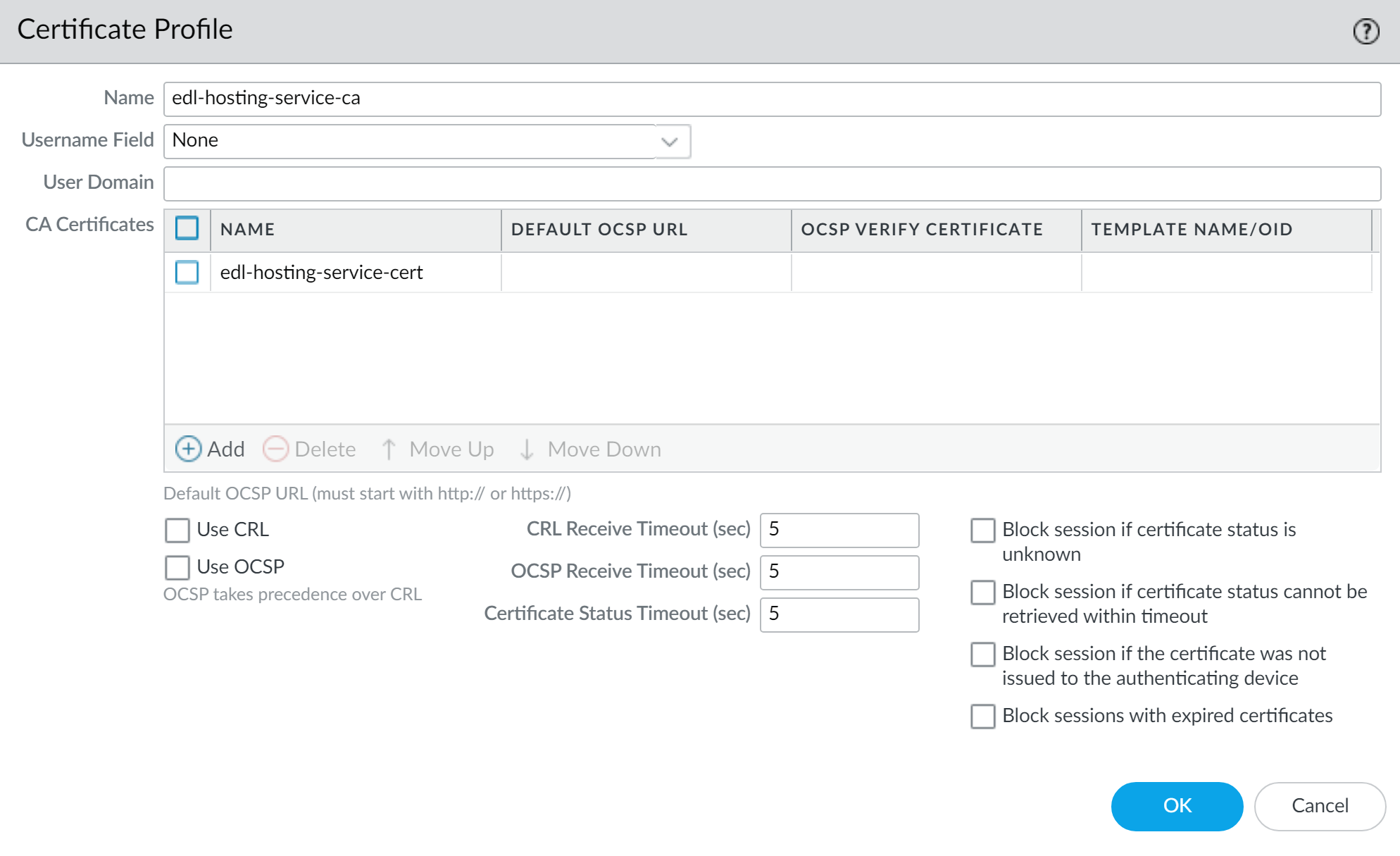
- Create a certificate authority (CA) certificate profile.
- SelectandDeviceCertificate ManagementCertificate ProfileAdda new certificate profile.
- Enter a descriptiveName.
- For theCA Certificates,Addthe certificate you imported in the previous step.
- ClickOK.
![]()
- Commit.
- Create an EDL using a Feed URL from the EDL Hosting Service.
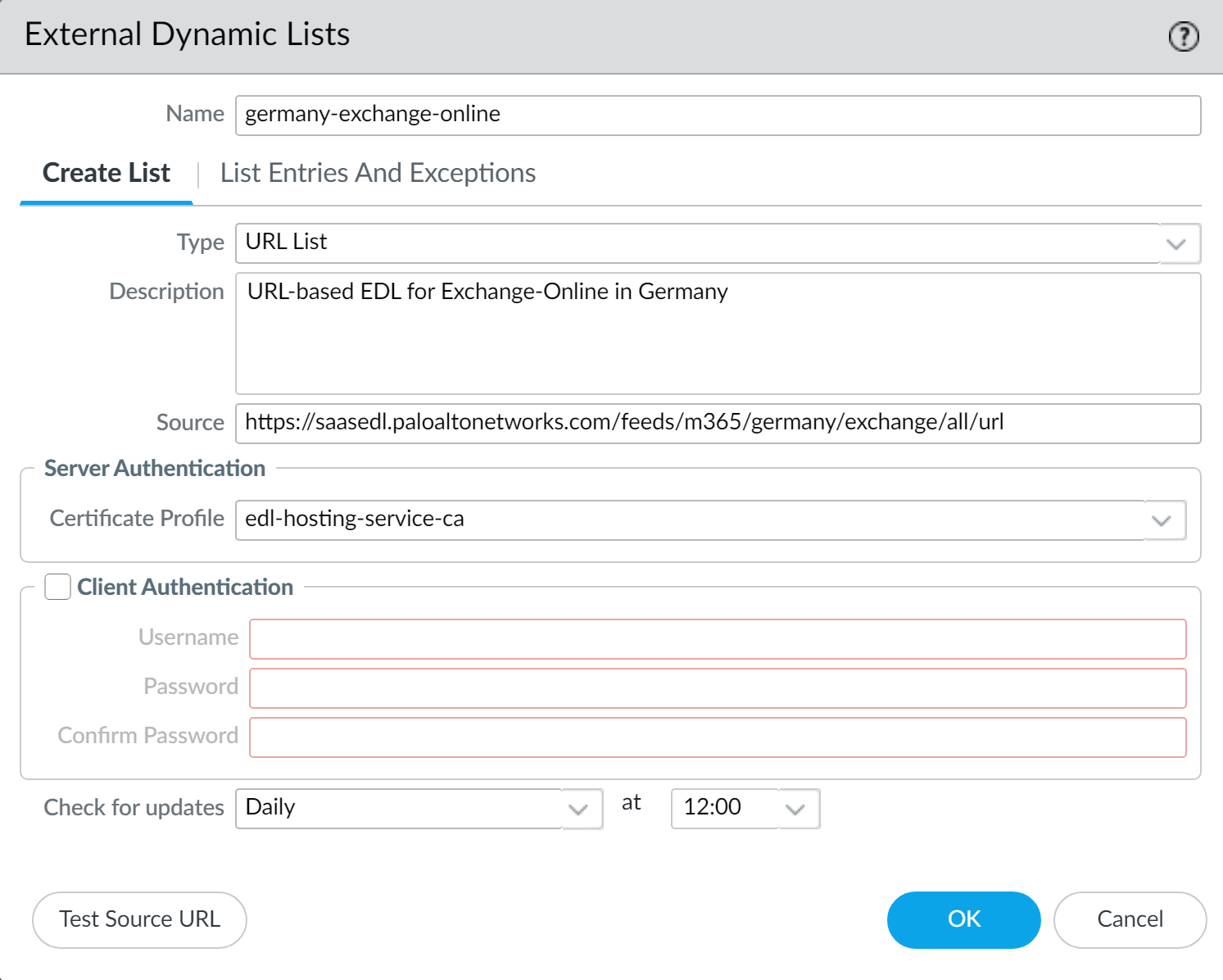
- SelectandObjectsExternal Dynamic ListsAdda new EDL.
- Enter a descriptiveNamefor the EDL.
- Select the EDLType.
- For an IP-based EDL, selectIP List.
- For a URL-based EDL, selectURL List.
- (Optional) Enter aDescription for the EDL
- Enter the Feed URL as the EDLSource.Enforce all endpoints within a specific Feed URL. Adding an excluding a specific endpoint from a Feed URL can cause connectivity issues to the SaaS application.
- (Best Practices) Select theCertificate Profileyou created in the previous step.
- Specify the frequency the firewall shouldCheck for updatesto match the update frequency of the Feed URL.For example, if the Feed URL is updated daily by Palo Alto Networks then configure the EDL to check for updatesDaily.Palo Alto Networks displays the update frequency for each Feed URL in the EDL Hosting Service. Feed URLs are automatically updated with any new endpoints.
- ClickTest Source URLto verify that the firewall can access the Feed URL from the EDL Hosting Service.
- ClickOK.
![]()
- When you enforce policy on an EDL from the EDL Hosting Service where the EDL is the source, be specific when configuring which users have access to the SaaS application to avoid over-provisioning access to the application.Leverage App-ID alongside EDLs in a security rule for additional strict enforcement of SaaS application traffic.