Network Security
Create a Security Profile Group (PAN-OS & Panorama)
Table of Contents
Expand All
|
Collapse All
Network Security Docs
Create a Security Profile Group (PAN-OS & Panorama)
Create a security profile group and add it to a Security policy.
To get started, you’ll need to:
- Add a profile groupWhen adding a Security Profile Group to your configuration, begin by providing a descriptive name and optional description to identify the purpose and functionality of the group.
- Choose your Security Profiles Select the security profiles you wish to include within the group. These profiles can encompass various security aspects such as antivirus, antispyware, vulnerability protection, URL Filtering, and more. Customize each selected profile based on specific security rules and threat prevention needs.After configuring the profiles, associate the profile group with Security policy rules to ensure consistent and comprehensive threat prevention. Implement this association by editing existing security rules or creating new ones, referencing the Security Profile Group accordingly.
- Review your Security Profile GroupRegularly reviewing and updating your Security Profile Groups is crucial to adapt to evolving threats and security requirements. This iterative process involves fine-tuning profile settings and incorporating new threat intelligence to optimize security efficacy. By effectively utilizing security profile groups, you can streamline Security policy management, achieve granular threat prevention, and fortify your network against a wide array of cyberthreats.
Use the following steps to create a security profile group and add it to a security
policy.
- Create a security profile group.If you name the group default, the firewall will automatically attach it to any new rules you create. This is a time saver if you have a preferred set of security profiles that you want to make sure get attached to every new rule.
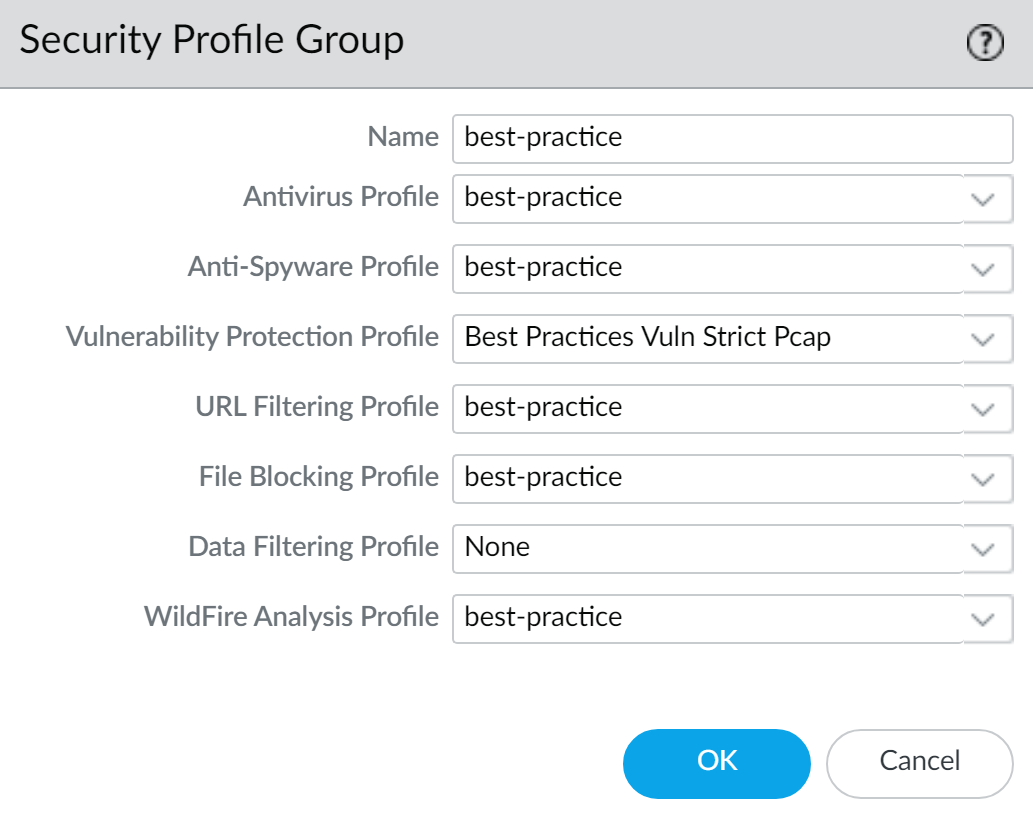
- Select ObjectsSecurity Profile Groups and Add a new security profile group.Give the profile group a descriptive Name, for example, Threats.If the firewall is in Multiple Virtual System Mode, enable the profile to be Shared by all virtual systems.Add existing profiles to the group.
![]() Click OK to save the profile group.Add your security profile to a Security policy.
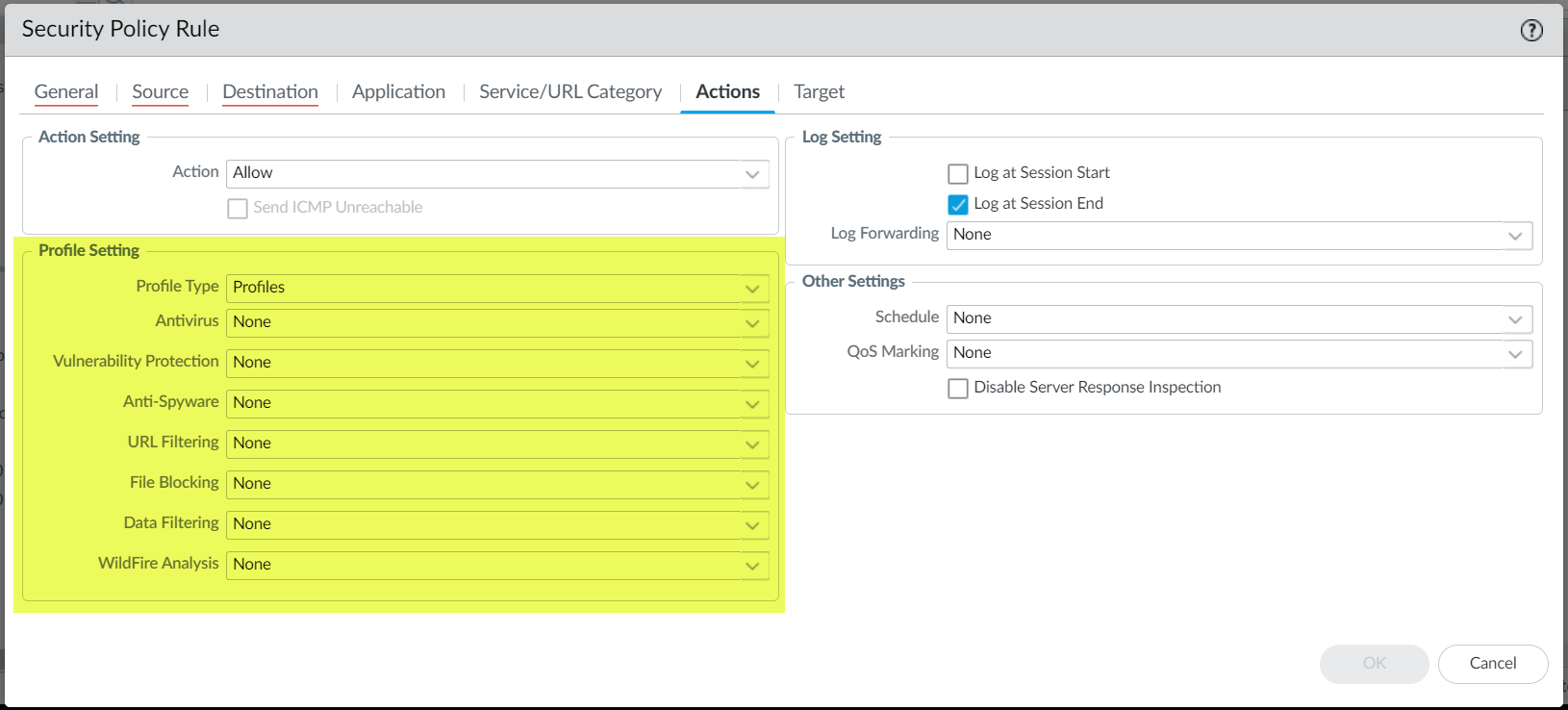
Click OK to save the profile group.Add your security profile to a Security policy.- Select PoliciesSecurity and Add or modify a security security rule.Select the Actions tab.In the Profile Setting section, select Profiles for the Profile Type.Select the profiles you want to add to your security rule.
![]() Click OK to save the security rule and Commit your changes.
Click OK to save the security rule and Commit your changes.Set Up or Override a Default Security Profile Group
A Security Profile Group streamlines the management and application of security settings, allowing you to apply a set of predefined profiles to traffic based on their security requirements.Additionally, you can set up a default Security Profile Group to be used in new security rules, or to override an existing default group. When you create a new Security policy, the default profile group is automatically selected as the policy’s profile settings, and traffic matching the policy are checked according to the settings defined in the profile group (you can choose to manually select different profile settings if desired).If you have an existing default Security Profile Group, and you don't want that set of profiles to be attached to a new security rule, you can override the default Security Profile Group and select a different profile group.Use the following options to set up a default Security Profile Group or to override your default settings.- Set up a default security profile group.
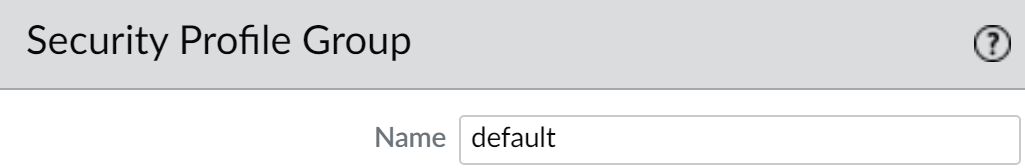
- Select ObjectsSecurity Profile Groups and add a new security profile group or modify an existing security profile group.Name the security profile group default:
![]() Click OK and Commit.Confirm that the default security profile group is included in new Security policies by default:
Click OK and Commit.Confirm that the default security profile group is included in new Security policies by default:- Select PoliciesSecurity and Add a new Security policy.
- Select the Actions tab and view the Profile Setting fields:
![]() By default, the new Security policy correctly shows the Profile Type set to Group and the default Group Profile is selected.
By default, the new Security policy correctly shows the Profile Type set to Group and the default Group Profile is selected.
Override a default security profile group.If you have an existing default security profile group, and you do not want that set of profiles to be attached to a new Security policy, you can continue to modify the Profile Setting fields according to your preference. Begin by selecting a different Profile Type for your policy (PoliciesSecuritySecurity Policy RuleActions).