Import a Custom Threat Signature from Snort and Suricata Rules
Table of Contents
Expand all | Collapse all
-
- About Custom Application Signatures
- Create a Custom Application Signature
- Create a Custom L3 & L4 Vulnerability Signature
- Import a Custom Threat Signature from Snort and Suricata Rules
- Test a Custom Signature
- Custom Signature Pattern Requirements
- Testing Pattern Performance Impact
-
-
- dhcp-req-chaddr
- dhcp-req-ciaddr
- dhcp-rsp-chaddr
- dhcp-rsp-ciaddr
- dns-req-addition-section
- dns-req-answer-section
- dns-req-authority-section
- dns-req-header
- dns-req-protocol-payload
- dns-req-section
- dns-rsp-addition-section
- dns-rsp-answer-section
- dns-rsp-authority-section
- dns-rsp-header
- dns-rsp-protocol-payload
- dns-rsp-ptr-answer-data
- dns-rsp-queries-section
- email-headers
- file-data
- file-elf-body
- file-flv-body
- file-html-body
- file-java-body
- file-mov-body
- file-office-content
- file-pdf-body
- file-riff-body
- file-swf-body
- file-tiff-body
- file-unknown-body
- ftp-req-params
- ftp-req-protocol-payload
- ftp-rsp-protocol-payload
- ftp-rsp-banner
- ftp-rsp-message
- gdbremote-req-context
- gdbremote-rsp-context
- giop-req-message-body
- giop-rsp-message-body
- h225-payload
- http-req-cookie
- http-req-headers
- http-req-host-header
- http-req-host-ipv4-address-found
- http-req-host-ipv6-address-found
- http-req-message-body
- http-req-mime-form-data
- http-req-ms-subdomain
- http-req-origin-headers
- http-req-params
- http-req-uri
- http-req-uri-path
- http-req-user-agent-header
- http-rsp-headers
- http-rsp-non-2xx-response-body
- http-rsp-reason
- icmp-req-code
- icmp-req-data
- icmp-req-type
- icmp-req-protocol-payload
- icmp-rsp-data
- icmp-rsp-protocol-payload
- icmp-req-possible-custom-payload
- ike-req-headers
- ike-rsp-headers
- ike-req-payload-text
- ike-rsp-payload-text
- imap-req-cmd-line
- imap-req-first-param
- imap-req-params-after-first-param
- imap-req-protocol-payload
- imap-rsp-protocol-payload
- irc-req-params
- irc-req-prefix
- jpeg-file-scan-data
- jpeg-file-segment-data
- jpeg-file-segment-header
- ldap-req-searchrequest-baseobject
- ldap-rsp-searchresentry-objectname
- ms-ds-smb-req-share-name
- ms-ds-smb-req-v1-create-filename
- ms-ds-smb-req-v2-create-filename
- msrpc-req-bind-data
- mssql-db-req-body
- netbios-dg-req-protocol-payload
- netbios-dg-rsp-protocol-payload
- netbios-ns-req-protocol-payload
- netbios-ns-rsp-protocol-payload
- nettcp-req-context
- oracle-req-data-text
- pe-dos-headers
- pe-file-header
- pe-optional-header
- pe-section-header
- pe-body-data
- pop3-req-protocol-payload
- pop3-rsp-protocol-payload
- pre-app-req-data
- pre-app-rsp-data
- rtmp-req-message-body
- rtsp-req-headers
- rtsp-req-uri-path
- sip-req-headers
- snmp-req-community-text
- smtp-req-argument
- smtp-rsp-content
- smtp-req-protocol-payload
- smtp-rsp-protocol-payload
- ssh-req-banner
- ssh-rsp-banner
- ssl-req-certificate
- ssl-req-chello-sni
- ssl-req-client-hello
- ssl-req-protocol-payload
- ssl-req-random-bytes
- ssl-rsp-cert-subjectpublickey
- ssl-rsp-certificate
- ssl-rsp-protocol-payload
- ssl-rsp-server-hello
- tcp-context-free
- telnet-req-client-data
- telnet-rsp-server-data
- udp-context-free
- unknown-req-tcp-payload
- unknown-rsp-tcp-payload
- unknown-req-udp-payload
- unknown-rsp-udp-payload
-
- dnp3-req-func-code
- dnp3-req-object-type
- dns-rsp-tcp-over-dns
- dns-rsp-txt-found
- ftp-req-params-len
- http-req-connect-method
- http-req-content-length
- http-req-cookie-length
- http-req-dst-port
- http-req-header-length
- http-req-param-length
- http-req-no-host-header
- http-req-no-version-string-small-pkt
- http-req-simple-request
- http-req-uri-path-length
- http-req-uri-tilde-count-num
- http-rsp-code
- http-rsp-content-length
- http-rsp-total-headers-len
- iccp-req-func-code
- ike-req-payload-type
- ike-rsp-payload-type
- ike-req-payload-length
- ike-rsp-payload-length
- ike-version
- imap-req-cmd-param-len
- imap-req-first-param-len
- imap-req-param-len-from-second
- irc-req-protocol-payload
- irc-rsp-protocol-payload
- ntlm-req-auth-v1
- ntlm-req-auth-v2
- open-vpn-req-protocol-payload
- pfcp-req-msg-type
- pfcp-rsp-msg-type
- smtp-req-helo-argument-length
- smtp-req-mail-argument-length
- smtp-req-rcpt-argument-length
- sctp-req-ppid
- ssl-req-client-hello-ext-type
- ssl-req-client-hello-missing-sni
- ssl-rsp-version
- stun-req-attr-type
- panav-rsp-zip-compression-ratio
- Context Qualifiers
-
Import a Custom Threat Signature from Snort and Suricata Rules
Strata Cloud Manager supports importation of Snort and Suricata rules to create
custom signatures usable by the Palo Alto Networks NGFWs.
You can use Strata Cloud Manager to translate Snort and Suricata rules into custom
Palo Alto Networks threat signatures. You
can then register the custom signatures on Palo Alto Networks NGFWs that belong to
the current scope, and all sub-folders contained within it. that you specify and use
these customer signatures in your Vulnerability Protection and Anti-Spyware Security
Profiles.
If you use Panorama to manage your NGFWs, you can also use the IPS Signature Converter Plugin for
Panorama to convert Snort and Suricata rules into custom Palo Alto Networks threat
signatures.
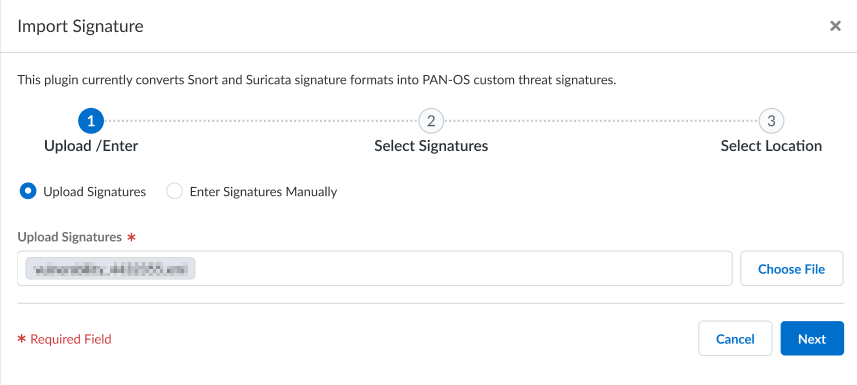
- Log in to the Strata Cloud Manager.Select ManageConfigurationNGFW and Prisma AccessSecurity Services and then select Anti-Spyware or Vulnerability Protection, depending on the signature type.From the Custom Signatures tab, select Add Custom Signature and then Import Signature.You can import signatures contained in a text-based file or manually by submitting the signature details. IPS rules, regardless of the import format, should be structured according to the IPS rule type (Snort or Suricata) that is being imported. At a minimum, each IPS rule must be separated by a new line and without any empty lines.Binary file types, such as a .pdf or .docx, cannot be imported.
- Upload Signatures-Select Choose File to specify the text file containing the IPS signatures to be converted.
![]()
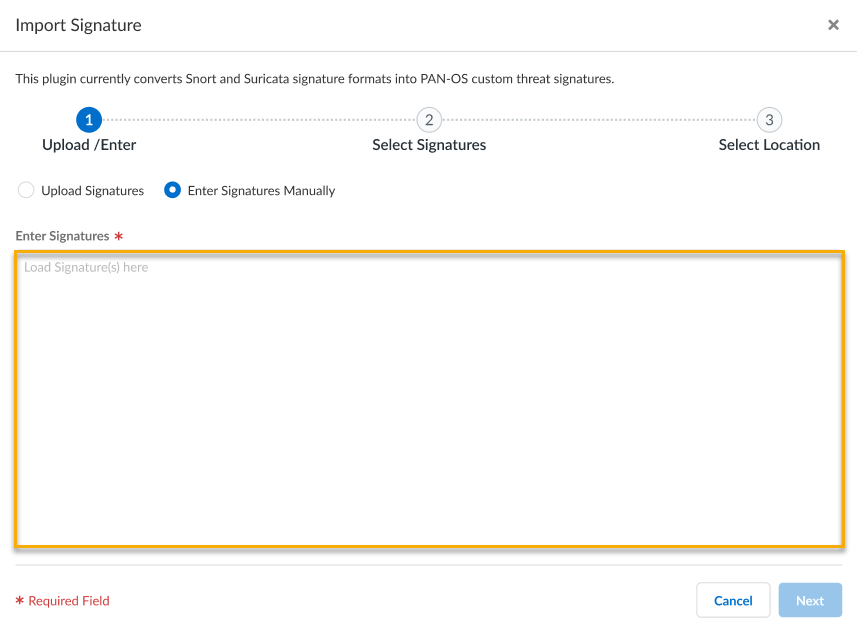
- Enter Signatures Manually-Copy and paste or type in the IPS signature contents into the text editor.
![]()
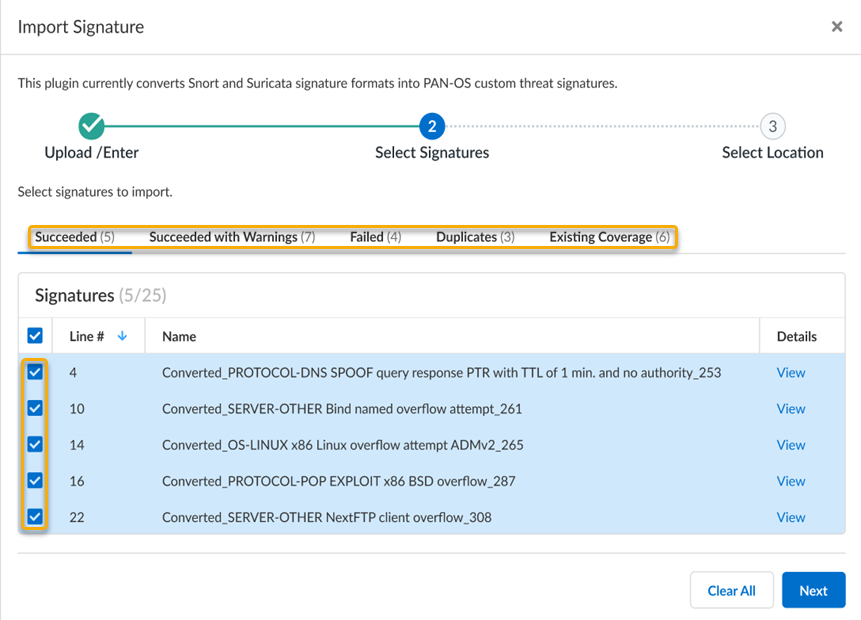
Select Next to continue with the conversion preview.The IPS signature conversion results are shown with various statuses for each of the detected entries found in the imported file. Each status type, at a minimum, displays the signature location in the file (based on the line number), as well as an option to View details. You can select valid signature entries for conversion and importation to Strata Cloud Manager.![]()
- Succeeded—Signatures that have been successfully converted. The detected signature name is also shown, with the prefix Converted_.
- Succeeded with Warnings—Signatures containing rules with unsupported contents. The detected signature name with the prefix Converted_ is shown, as well as any warnings generated during conversion.
- Failed—Signatures that failed the conversion process.
- Duplicates—Signatures that have duplicates contained in the same file. The location of the signature duplicate(s) are shown.
- Existing Coverage—Signatures that match against a predefined, Palo Alto Networks generated threat signature. The signatures with existing coverage are shown.
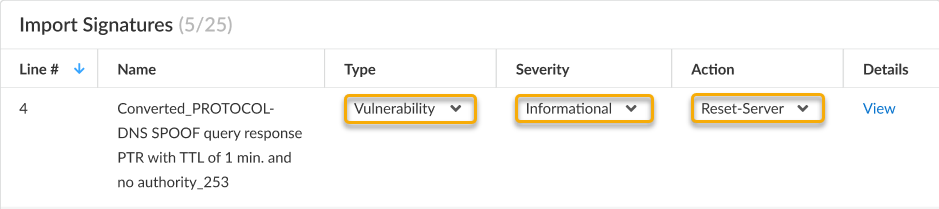
Click Next after selecting the signature(s) that you want to import.For each signature that you selected, you can update the Type, Severity level, and Action. These define how signatures are defined and applied when used within security policies.The default Severity level and Action for a converted signature is inherited from the Snort or Suricata signature; while the Type is set to Vulnerability by default.![]()
- Type—Select either Vulnerability or Spyware, depending on how the signature should be categorized. This is set to Vulnerability by default.
- Severity level—Select from Critical, High, Medium, Informational, or Low. For details on severity levels, refer to: Log Types and Severity Levels.
- Action—Select from Alert, Drop, Reset-Client, Reset-Server, Reset-Both, and Allow. For details on actions, refer to: Actions in Security Profiles.
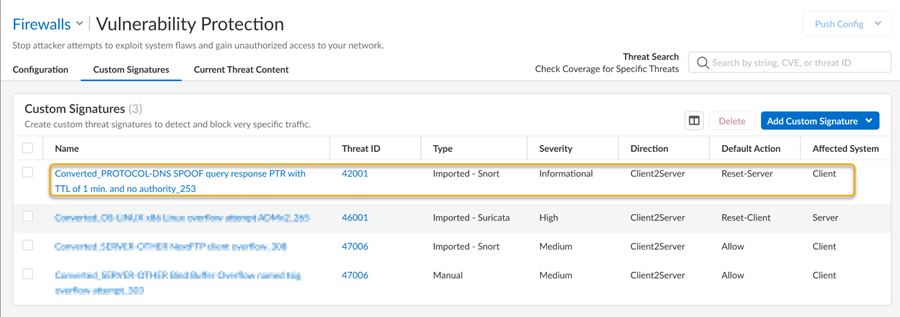
Click Import when finished.The newly added custom signatures and the current configuration are displayed under the associated security service type, either Vulnerability or Anti-Spyware.![]() Push your configuration changes to the NGFWs contained within the scope.
Push your configuration changes to the NGFWs contained within the scope.