Prisma Access
Configure Secure Inbound Access for Remote Networks
Table of Contents
Expand All
|
Collapse All
Prisma Access Docs
-
- 6.1 Preferred and Innovation
- 6.0 Preferred and Innovation
- 5.2 Preferred and Innovation
- 5.1 Preferred and Innovation
- 5.0 Preferred and Innovation
- 4.2 Preferred
- 4.1 Preferred
- 4.0 Preferred
- 3.2 Preferred and Innovation
- 3.1 Preferred and Innovation
- 3.0 Preferred and Innovation
- 2.2 Preferred
-
-
- 4.0 & Later
- Prisma Access China
-
-
Configure Secure Inbound Access for Remote Networks
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
To begin configuration, you choose how many public IP addresses you want to associate for
the applications. You can specify either 5 or 10 public IP addresses per remote network
site. Each public IP allocation takes bandwidth (units) from your Remote Networks
license, in addition to the bandwidth that you have allocated for the compute location associated to the
remote network. 5 IP addresses take 150 Mbps from your remote network license
allocation, and 10 IP addresses take 300 Mbps.
After you choose the number of public IP addresses, you then enter the application, along
with its associated private IP/port number/protocol combination, for which you want
secure inbound access.
You can decide how you want to map your application to the public IP addresses. By
default, Prisma Access assigns the public IP addresses to the applications you specify,
and multiple applications can be assigned to a single IP address. If you need to map a
single application to a single public IP address, you can select Dedicated
IP during system configuration. You can configure up to 100 inbound
applications for each group of provisioned public IP addresses (either 5 or 10).
Configure Secure Inbound Access for Remote Networks (Strata Cloud Manager)
Here’s how to make an application accessible from a remote network site to all
internet-connected users (not just Prisma Access users).
- If you haven’t already, review the inbound access remote network guidelines.Gather the application details you’ll need to get started.Make a list of the applications to which you want to provide access, and assign a private IP, port number, and protocol combination for each application. If you use the same IP address for multiple applications, the port/protocol combination must be unique for each application; if you use the same port/protocol combination for multiple applications, each IP address must be unique.In Strata Cloud Manager, go to ConfigurationNGFW and Prisma AccessConfiguration ScopePrisma AccessRemote NetworksInbound AccessAdd Inbound Access.Enter the required details.Choose the Number of Public IPs you want to use for the applications, either five or ten.Each public IP allocation takes bandwidth from your Remote Networks license, in addition to the license cost for the remote network. 5 IP addresses take 150 MB from your remote network license allocation, and 10 IP addresses take 300 MB.From Prisma Access version 4.1, if you have a resource that is in a remote network site that has inbound access enabled and you want users at non-inbound access sites to have access to that resource, you can Allow inbound flows to other Remote Networks over the Prisma Access backbone when you configure the non-inbound access remote network.From Prisma Access version 5.0, you can allow inbound flows to other remote networks over the Service Provider (SP) backbone when you configure the non-inbound access remote network.SP interconnect supports only the following:
- GCP Regions
- New Prisma Access deployments
- Explicit proxy egress traffic
Add the Inbound Access Applications for which you want to secure access.Add the associated private IP / port number / protocol combination for the application.Decide how you want to map applications to the public IP addresses.By default, Prisma Access assigns the public IP addresses to the applications you specify, and multiple applications can be assigned to a single IP address. If you need to map a single application to a single public IP address, you can Assign Dedicated IP during system configuration. You can configure up to 100 inbound applications for each group of provisioned public IP addresses (either 5 or 10).Finish setting up the inbound access remote network as you would a regular remote network site.Configure Secure Inbound Access for Remote Networks (Panorama)
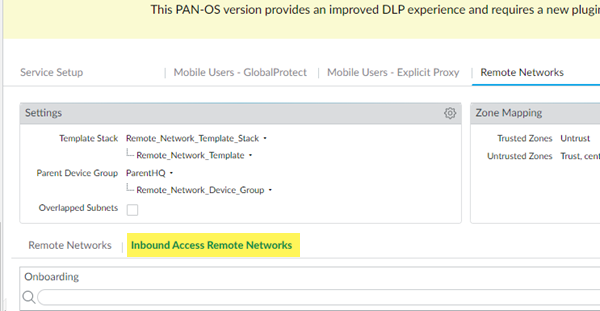
Describes the procedure you use to configure secure inbound access for a Prisma Access remote network connection.If you have a Prisma Access deployment that allocates remote network bandwidth by compute location, configure inbound access by completing the following steps.- Select PanoramaCloud ServicesConfigurationRemote Networks, and select Inbound Access Remote Networks.
![]() Add a remote network to for inbound access.Specify settings for the inbound access remote network connection.
Add a remote network to for inbound access.Specify settings for the inbound access remote network connection.- Enter a Name for the inbound access connection.Enter a Location.Inbound access supports a subset of locations.Specify a Bandwidth to use for the inbound access connection.You allocate bandwidth for inbound access connections on a per-location basis.Specify the Number of Public IPs to use for the inbound access connection.Specify either 5 or 10 public IP addresses. Each public IP allocation takes bandwidth (units) from your Remote Networks license, in addition to the bandwidth that you have allocated for the compute location associated to the remote network.Select the IPSec tunnel to use with the inbound access connection.Select whether or not you want to Allow inbound flows to other Remote Networks over the Prisma Access Backbone.If you have a resource that is in a remote network site that has inbound access enabled and you want users at non-inbound access sites to have access to that resource, you can Allow Inbound Flows To Other Remote Networks over the Prisma Access Backbone when you configure the non-inbound access remote network. If you allow inbound flows from other remote networks, you must enable source NAT.(Optional) If you have a secondary WAN link at this location, select Enable Secondary WAN and provide an IPSec Tunnel that is different than the primary IPSec tunnel.Configure Static Routes, BGP, and QoS for your deployment.This configuration is the same as a non-inbound access remote network connection.Click the Inbound Access tab to configure inbound access options.
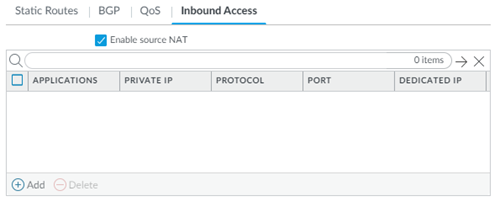
- (Optional) To disable source NAT, deselect Enable Source NAT.By default, source NAT is enabled. If the IPSec-capable device at your remote network site is capable of performing symmetric return (such as a Palo Alto Networks next-generation firewall), or if you have not selected Allow inbound flows to other Remote Networks over the Prisma Access backbone, deselect Enable source NAT.You must Enable source NAT in the Inbound Access tab if you select this check box. Source NAT is a requirement to allow inbound flows to other remote networks.
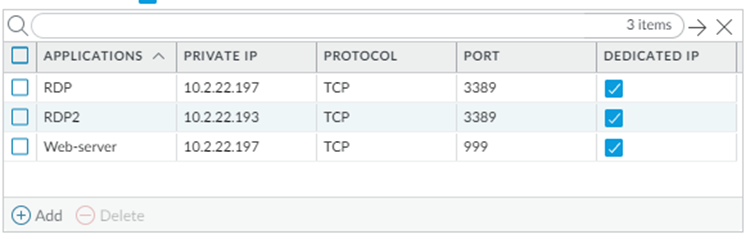
![]() Add the applications to provide secure inbound access.You can configure up to 100 inbound applications for each group of provisioned public IP addresses (either 5 or 10). Enter a unique Private IP address, Protocol, and Port combination for each application. It is acceptable to use duplicate private IP addresses and ports for two applications, as long as you select TCP for one application and UDP for another application.Provide the following values:
Add the applications to provide secure inbound access.You can configure up to 100 inbound applications for each group of provisioned public IP addresses (either 5 or 10). Enter a unique Private IP address, Protocol, and Port combination for each application. It is acceptable to use duplicate private IP addresses and ports for two applications, as long as you select TCP for one application and UDP for another application.Provide the following values:- Specify the name of the Application.
- Specify the Private IP address to use with this application.
- Specify the Protocol to use with the application (TCP or UDP).
- Specify the Port to use with the application.
- Choose whether you want to dedicate a single public IP address to a single application; to do so, select Dedicated IP.
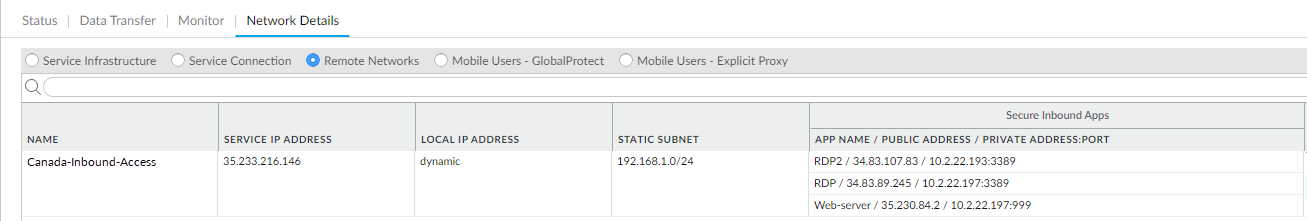
![]() Click OK to save your changes.Save and Commit your changes.Wait approximately 30 minutes for Prisma Access to generate the public IP addresses; then select PanoramaCloud ServicesStatusNetwork DetailsRemote Networks and make a note of the Public Address that is associated with the App Name for application you created.If you selected Dedicated IP, find the single application that is associated with the Public Address.
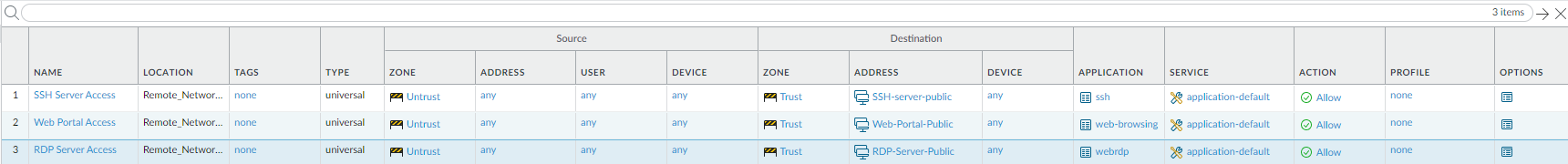
Click OK to save your changes.Save and Commit your changes.Wait approximately 30 minutes for Prisma Access to generate the public IP addresses; then select PanoramaCloud ServicesStatusNetwork DetailsRemote Networks and make a note of the Public Address that is associated with the App Name for application you created.If you selected Dedicated IP, find the single application that is associated with the Public Address.![]() Create security policies to allow traffic from the inbound internet users.Because Prisma Access’ default security policy only allows untrust-to-untrust traffic, you need to configure security polices to allow untrust-to-trust traffic for your inbound access applications. Palo Alto Networks recommends that you limit the type of access you permit to inbound applications. The following examples provide access to SSH servers, web portals, and RDP servers.
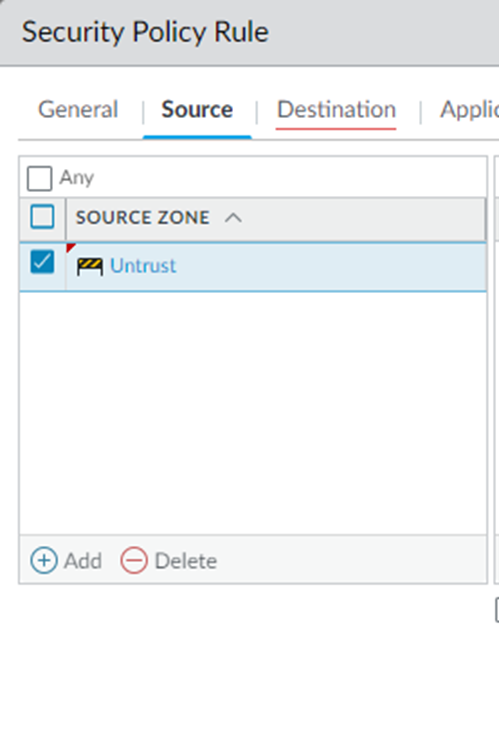
Create security policies to allow traffic from the inbound internet users.Because Prisma Access’ default security policy only allows untrust-to-untrust traffic, you need to configure security polices to allow untrust-to-trust traffic for your inbound access applications. Palo Alto Networks recommends that you limit the type of access you permit to inbound applications. The following examples provide access to SSH servers, web portals, and RDP servers.- Select PoliciesSecurity and Add a policy.Be sure to create this policy under the Remote_Network_Device_Group device group.Select the Source traffic as Untrust.
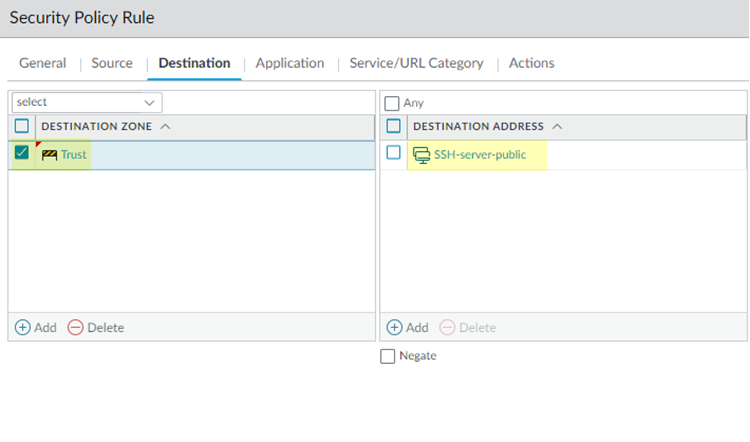
![]() Create a policy to allow SSH server traffic by selecting the Destination Zone for destination traffic as Trust and specifying a Destination Address of SSH-server-public. This is an Address or Address Group object you created that has a list of all the public IP addresses that are used for SSH login.
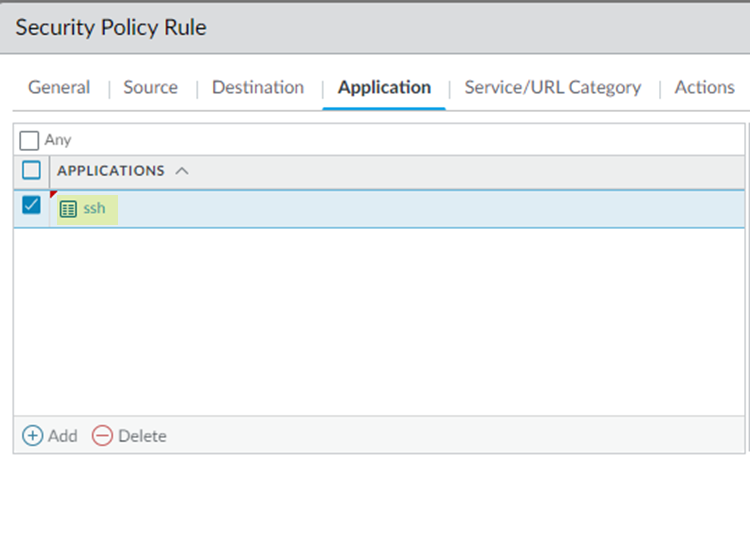
Create a policy to allow SSH server traffic by selecting the Destination Zone for destination traffic as Trust and specifying a Destination Address of SSH-server-public. This is an Address or Address Group object you created that has a list of all the public IP addresses that are used for SSH login.![]() Select an Application of ssh.
Select an Application of ssh.![]() Select a Service/URL Category of application-default to allow or deny applications based only their default ports as defined by Palo Alto Networks.In Actions, select Allow.Click OK to save the policy.Create a policy to allow web portal access by creating a policy in the previous steps but substituting the following settings in the Destination and Application tabs:
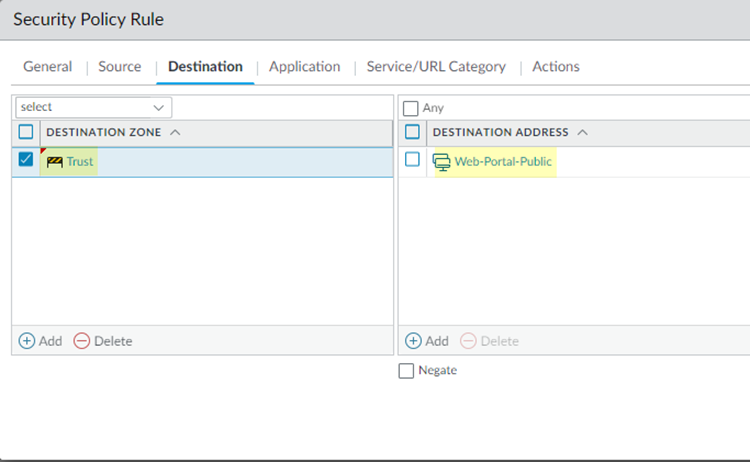
Select a Service/URL Category of application-default to allow or deny applications based only their default ports as defined by Palo Alto Networks.In Actions, select Allow.Click OK to save the policy.Create a policy to allow web portal access by creating a policy in the previous steps but substituting the following settings in the Destination and Application tabs:- Select a Destination Address of an Address or Address Group of Web-Portal-Public, which contains all the public IP addresses of the web portal.
![]()
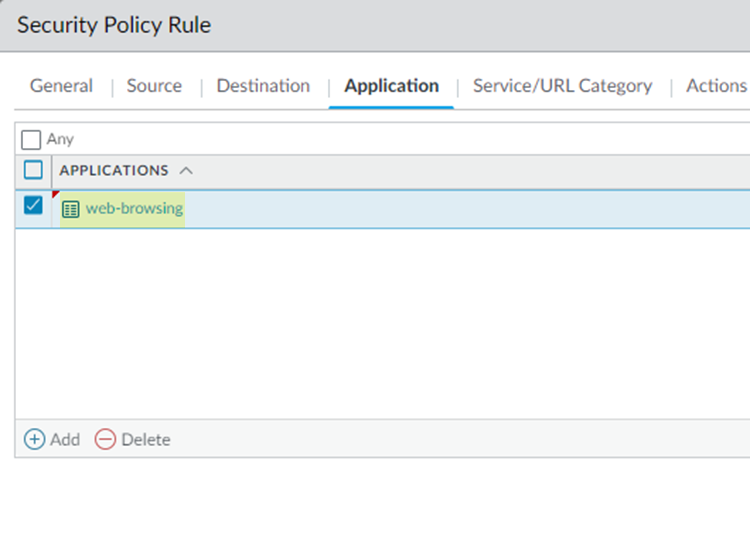
- Select an Application of web-browsing.
![]()
Create a security policy for RDP server access, using the same settings as you did for the other policies but creating an Address or Address Group object called RDP-Server-Public, which contains the public IP addresses for the RDP server, as the Destination Address and webrdp as the Application.When complete, you have three different policies to allow SSH server access, web portal access, and RDP server access.![]() Save and Commit your changes.Check that the remote network connection is operational and correctly processing inbound traffic.
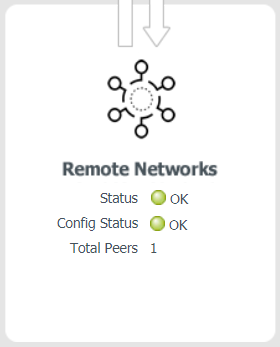
Save and Commit your changes.Check that the remote network connection is operational and correctly processing inbound traffic.- Select PanoramaCloud Services StatusStatusRemote Networks and hover over the Status and Config Status areas to see the tunnel’s status.
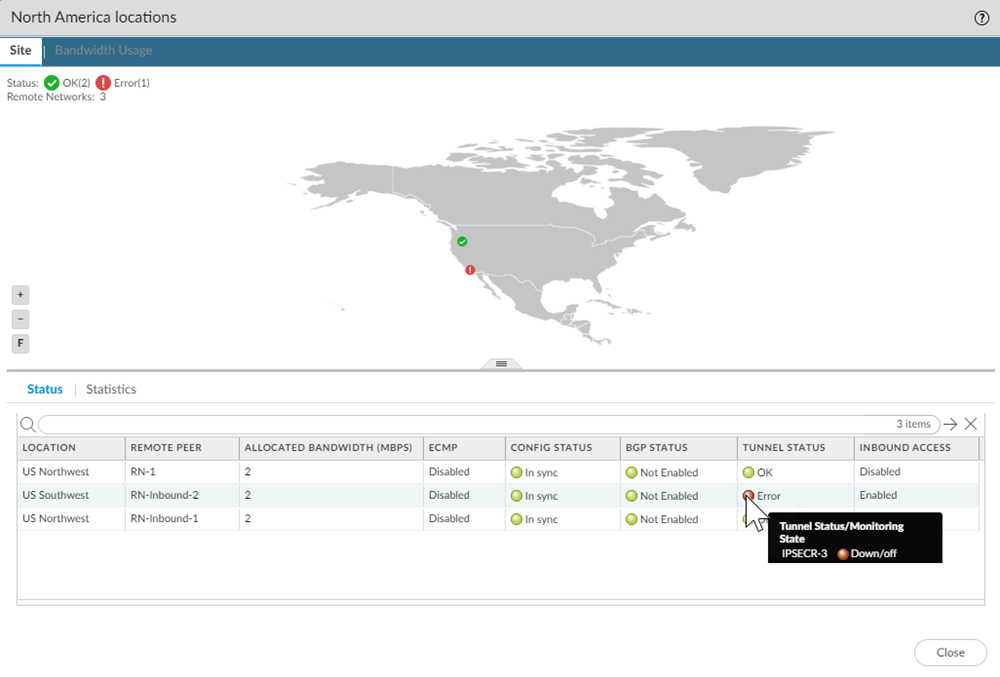
![]() If you find issues, select PanoramaCloud Services StatusMonitorRemote Networks, select the location of the remote network tunnel in the map, and hover over the Tunnel Status area to determine the cause of the error.
If you find issues, select PanoramaCloud Services StatusMonitorRemote Networks, select the location of the remote network tunnel in the map, and hover over the Tunnel Status area to determine the cause of the error.![]()