- Home
- Prisma Access
- Prisma Access Administration
- Prisma Access Advanced Deployments
- Prisma Access Service Connection Advanced Deployments
- Use Traffic Steering to Forward Internet-Bound Traffic to Service Connections
- Configure Traffic Steering in Prisma Access
- Configure Traffic Steering in Prisma Access (Strata Cloud Manager)
Prisma Access
Configure Traffic Steering in Prisma Access (Strata Cloud Manager)
Table of Contents
Expand All
|
Collapse All
Prisma Access Docs
-
- 6.1 Preferred and Innovation
- 6.0 Preferred and Innovation
- 5.2 Preferred and Innovation
- 5.1 Preferred and Innovation
- 5.0 Preferred and Innovation
- 4.2 Preferred
- 4.1 Preferred
- 4.0 Preferred
- 3.2 Preferred and Innovation
- 3.1 Preferred and Innovation
- 3.0 Preferred and Innovation
- 2.2 Preferred
-
-
- 4.0 & Later
- Prisma Access China
-
-
Configure Traffic Steering in Prisma Access (Strata Cloud Manager)
Configure traffic steering in the Prisma Access deployment.
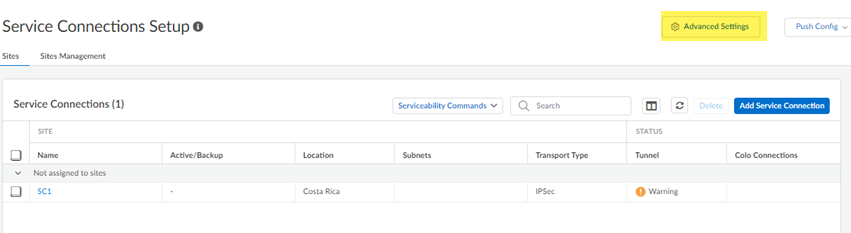
In Prisma Access deployments, a service connection provides access to internal
network resources, such as authentication services and private apps in your
headquarters or data center. Service connections process internal traffic, where no
internet access is required. In some cases, you might want to redirect
internet-bound traffic to the data center. Traffic steering allows you to redirect
mobile user or remote network traffic to a service connection before being sent to
the internet. Configure traffic steering for your Prisma Access deployment by
completing the following steps.
- Onboard your service connections, mobile users and remote networks, as applicable to your deployment.Go to ConfigurationNGFW and Prisma AccessConfiguration ScopePrisma AccessService ConnectionsAdvanced Settings.
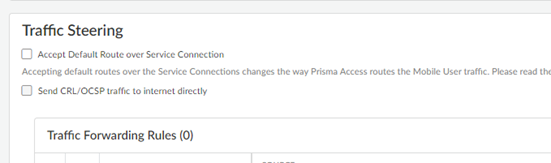
![]() Configure the Traffic Steering rules.
Configure the Traffic Steering rules.- (Optional, mobile user deployments only) Allow Prisma Access to accept and install the default route advertised over one or more service connections from the CPE by clicking the gear icon to open the Settings and selecting Accept Default Route over Service Connections.Default routes have guidelines that you must follow when using them; for example, default routes are supported for mobile user deployments only and have no effect on remote network deployments. Be sure to review these guidelines before implementing default routes with traffic steering.(Optional) Allow Prisma Access to send certificate revocation list (CRL) and Online Certificate Status Protocol (OCSP) traffic directly to the internet by selecting Send CRL/OCSP traffic to internet directly.Select this choice if you have an OCSP or CRP server in the public internet and you want to send that traffic directly to the internet using the untrust zone. If you do not select this choice, Prisma Access sends this traffic to the service connection.Be sure that you have upgraded your Prisma Access deployment to a minimum version of 5.1.1 before selecting Send CRL/OCSP traffic to internet directly.
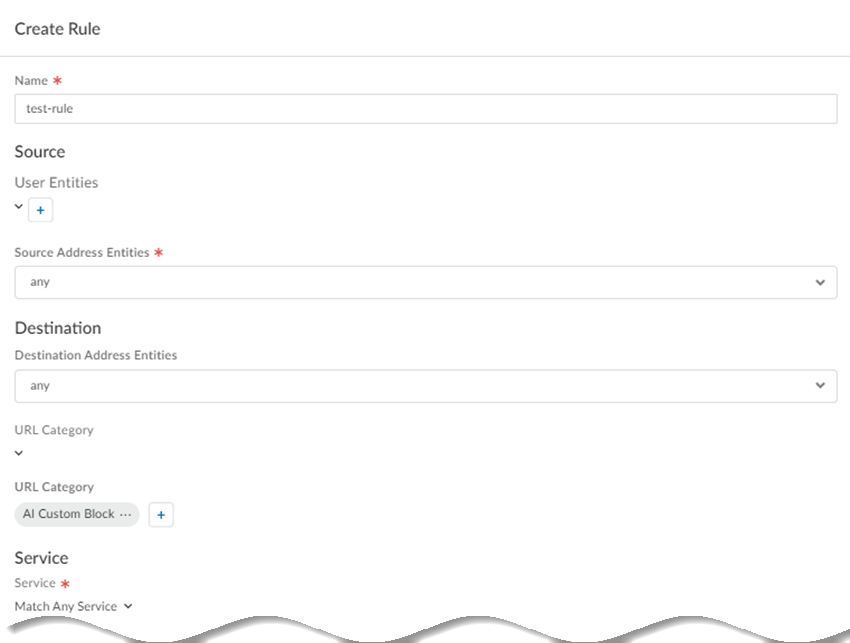
![]() Create rules for the target you created and apply them to the target.
Create rules for the target you created and apply them to the target.- Add Rule.Enter a unique Name for the rule.In the Source area:
- Specify the list of users to match. You can Match Any User, Match Pre-logon, Match known-user, Match unknown, or Add Users and select the user or users to match.
- Select Source Address Entities. You can
select one or more of the following objects:
- An IP address
- An address group
- An External Dynamic List (EDL) using IP addresses or URLs
In the Destination area specify one of the following Destination Address Entities, or select Any to have traffic processed by the rules in the URL Category field:- An IP address
- An address group
- An External Dynamic List (EDL) using IP addresses or URLs
Specify a URL Category.If you create a custom URL category, enter URLs in all lower case. Traffic steering supports custom URL and predefined URL categories.You can use wildcards with the URLs in URL categories. The following wildcard formats are supported:- *.example.com
- *.fqdn.example.com
The following formats are not supported:- *
- *.*
- *example.com
- example.com/ (trailing slashes in URLs are not supported in URL categories that are used with Traffic Steering)
- example.com/path (only domain names are supported)
- *fqdn.example.com
- fqdn.example.*
Use the following guidelines when configuring destination options:- If you specify a URL category, Prisma Access only matches HTTP and HTTPS traffic, even when service is set to Any.
- Do not create a custom URL category with a type of Category Match.
Specify a Service type and Add Service.Specify service-http to forward HTTP traffic and specify service-https to specify HTTPS traffic. Select Match Any Service to forward traffic of any service type.![]() Create a service connection group and specify an Action.
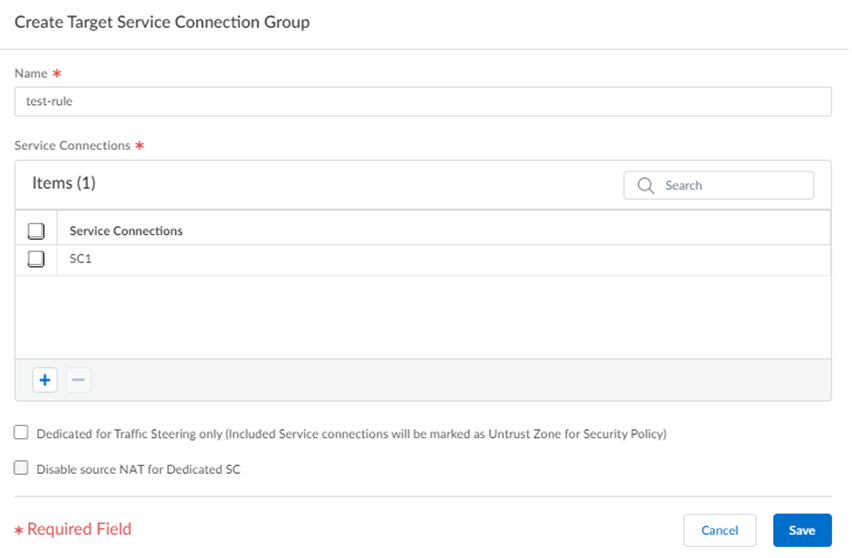
Create a service connection group and specify an Action.- Create New or Manage a group and give it a unique Name.
- Specify the Service Connection or service
connections to use with the target.Palo Alto Networks does not recommend using multiple service connections (whether dedicated or non-dedicated) in a target service connection group that is referenced in a traffic steering rule. In addition, a given service connection can only exist in one target and you cannot add a single service connection to two different targets.
- (Optional) Use a dedicated service connection to steer traffic to a third-party security stack or cloud that is not on your premises and does not need to participate in routing. To set a service connection to be used as a dedicated service connection, select Dedicated for Traffic Steering Only.Dedicated service connections change their zones and are marked as an Untrust Zone for security policy rules.Deselect Dedicated for Traffic Steering Only if you will send both normal service connection-related and traffic steering traffic through the service connection; with this choice, the zone for the service connection remains as Trust.
- Disable source NAT for Dedicated service connections by
selecting, select Disable Source NAT for Dedicated
SC. Source NAT is enabled by default (the
checkbox is deselected). If you disable source NAT, Prisma Access uses your organization’s source IP addresses for the dedicated service connection. If you enable source NAT, Prisma Access uses the EBGP Router address of the service connection (PanoramaCloud ServicesStatusNetwork DetailsService ConnectionEBGP Router) as the source IP address, even after the traffic egresses from the dedicated service connection.
- Save your changes.
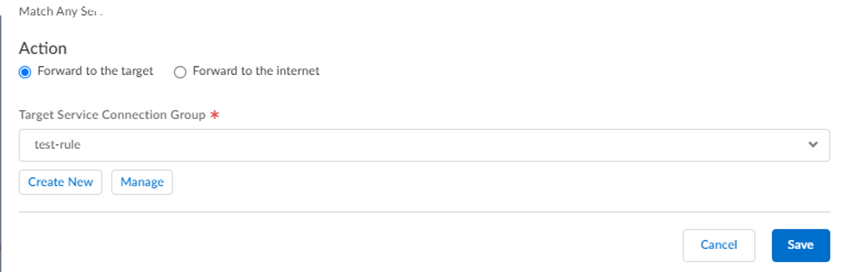
![]() Forward traffic to the specified service connection target, or send the traffic directly to the internet without going through the service connection.
Forward traffic to the specified service connection target, or send the traffic directly to the internet without going through the service connection.- To have Prisma Access forward traffic to a service connection target, select Forward to the target; then select the Target Service Connection Group.Specify this choice if you have traffic you need to send to your existing or legacy environment because of SaaS application allow list limitations, or if you want to create a traffic flow to direct specified internet traffic back to your on-premises network.
- To have Prisma Access forward traffic directly to the internet without first sending it to a service connection, select Forward to the internet.Specify this choice if you are sending a default route to Prisma Access and you want to steer some traffic directly to the internet.
![]() Push Config to save your changes.
Push Config to save your changes.