Prisma Access
Configure Proxy Chaining on Prisma Access Explicit Proxy
Table of Contents
Expand All
|
Collapse All
Prisma Access Docs
-
- 6.1 Preferred and Innovation
- 6.0 Preferred and Innovation
- 5.2 Preferred and Innovation
- 5.1 Preferred and Innovation
- 5.0 Preferred and Innovation
- 4.2 Preferred
- 4.1 Preferred
- 4.0 Preferred
- 3.2 Preferred and Innovation
- 3.1 Preferred and Innovation
- 3.0 Preferred and Innovation
- 2.2 Preferred
-
-
- 4.0 & Later
- Prisma Access China
-
-
Configure Proxy Chaining on Prisma Access Explicit Proxy
Here's how you can configure downstream proxy chaining with third-party proxy using
Prisma Access explicit proxy.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
Prisma Access proxy chaining feature enables you to securely integrate your Prisma Access explicit proxy setup with another proxy in a seamless and
sequential manner. Enterprises utilize proxy chaining to integrate their current
proxy infrastructure or to meet compliance requirements. Here, the Prisma Access
explicit proxy functions as a downstream proxy to the other proxies. To configure
proxy chaining, you create profiles with the upstream proxy server’s IPv4 address or
FQDN that resolve to a IPv4 address and create rules to define the criteria to route
traffic through upstream proxy servers.
With proxy chaining feature you can route traffic to another proxy based on the users
source IP address, users or user-groups, and URL category. You can also share
X-Forwarded-For (XFF) and X-Authenticated-User (XAU) headers with upstream proxy
servers.
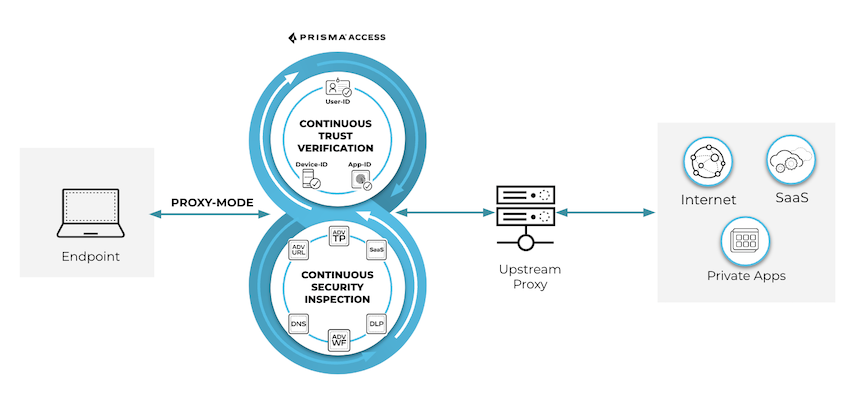
When you want to proxy chain the traffic from Prisma Access explicit proxy to
another proxy, Prisma Access explicit proxy authenticates users and passes the
username to another proxy using XAU header insertion (username in base64 format) and
the source IP address using the XFF header insertion. To chain to a proxy located
inside the data center, GlobalProtect agent and connectivity from Prisma Access
to the data center is needed.
Supported Methods to Connect
- GlobalProtect in proxy or tunnel and proxy mode with an upstream on-premises proxy or cloud proxy for proxy traffic.
- Prisma Browser with an upstream on-premises proxy or cloud proxy.
- IoT or server with remote networks and explicit proxy with skip authentication.
- Proxy auto-configuration (PAC): Kerberos to an upstream proxy cloud proxy only.
- Remote Network with explicit proxy to an upstream proxy cloud proxy only.
Prerequisites
Before you begin, you can enable Cloud Identity Engine (CIE) to learn about
the user and user-group.
Configure Proxy Chaining on Prisma Access Explicit Proxy (Strata Cloud Manager)
Here's how you can configure downstream proxy chaining with Prisma
Access explicit proxy on Strata Cloud Manager.
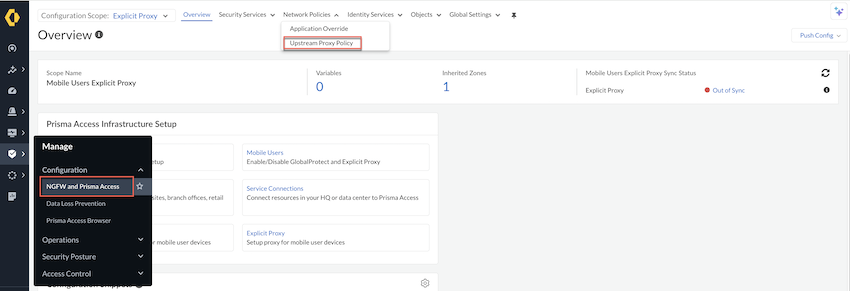
- Set up an explicit proxy.Go to ConfigurationNGFW and Prisma AccessNetwork PoliciesUpstream Proxy Policy. Set the Configuration Scope to Explicit Proxy.
![]() Create an Upstream Proxy Profile.
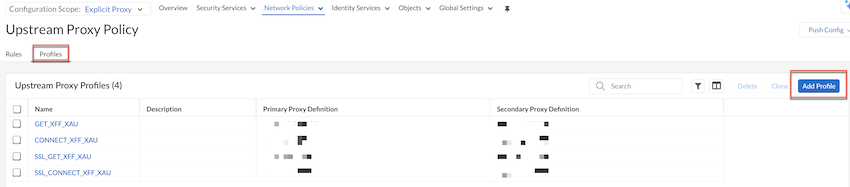
Create an Upstream Proxy Profile.- Under Upstream Proxy Policy, select Profiles and Add Profile.
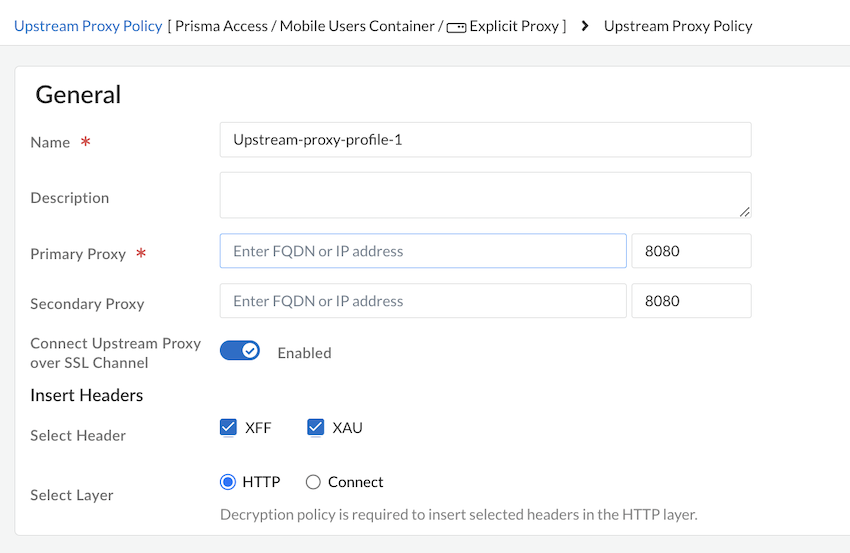
![]() Add a Name, Description, a Primary Proxy, and optionally a Secondary Proxy. By default, the port is set as 8080. You can add the port as per your requirement.The FQDN should be resolvable to an IPv4 address or IP address should be IPv4 and reachable.
Add a Name, Description, a Primary Proxy, and optionally a Secondary Proxy. By default, the port is set as 8080. You can add the port as per your requirement.The FQDN should be resolvable to an IPv4 address or IP address should be IPv4 and reachable.![]() (Optional) Select the headers XFF or XAU, select layer as HTTP or Connect to send information to an upstream proxy.If you add XFF and XAU headers and select the Connect layer, we recommend to enable Connect Upstream Proxy over SSL Channel to securely connect Prisma Access explicit proxy to another proxy.If you select HTTP and add XAU or XFF headers, we recommend having decryption on PAN-OS.Save your changes.Configure proxy policy rules. Rules must be Enabled for the configuration to be saved.
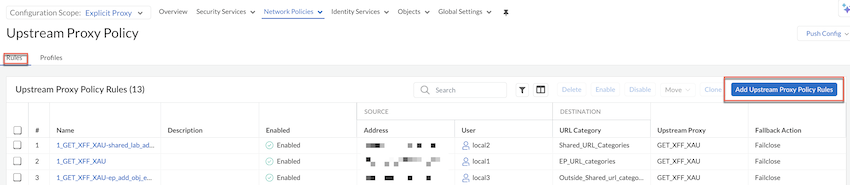
(Optional) Select the headers XFF or XAU, select layer as HTTP or Connect to send information to an upstream proxy.If you add XFF and XAU headers and select the Connect layer, we recommend to enable Connect Upstream Proxy over SSL Channel to securely connect Prisma Access explicit proxy to another proxy.If you select HTTP and add XAU or XFF headers, we recommend having decryption on PAN-OS.Save your changes.Configure proxy policy rules. Rules must be Enabled for the configuration to be saved.- Go to Rules and select Add Upstream Proxy Policy Rules and build your rule by configuring the following rule components. Components marked with an asterisk(*) are mandatory.
![]()
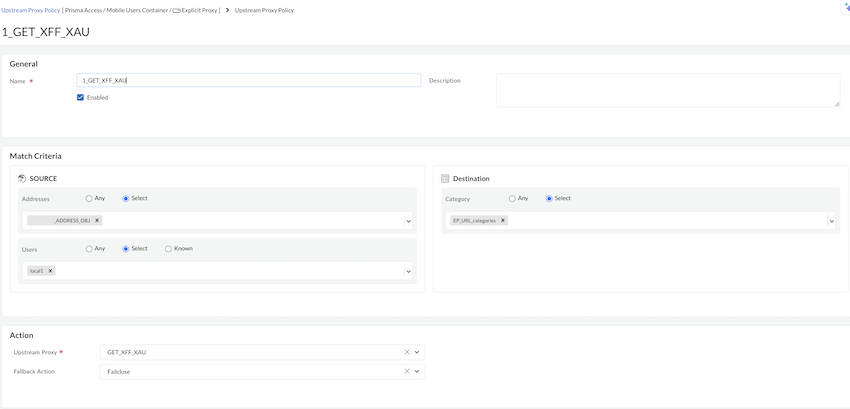
Section Element Details General *Name Give your rule a unique name the tells other administrators what it does. Optionally provide a detailed description of the rule's intent. Match Criteria Source Define the matching criteria for the source fields for the traffic. - Specify the source IP *Addresses, or add an Address Groups or leave the value set to Any.
- Specify source *Users or leave the value set to Any. You can select Users to enforce the policy for individual users or a group of users.
Destination Define the destination address for the traffic. Specify a URL category as match criteria for the proxy chaining rule. Select URL Category to specify it as a match criteria in the proxy chaining rule or leave the value set to Any.Action *Upstream Proxy Define what Action you want to take for the traffic that matches the rule. Select an upstream proxy or select Direct. When you select Direct, the traffic egresses using Prisma Access explicit proxy to an upstream web or application server.Fallback Action Specifies a Failclose or Failopen action to apply when the selected upstream proxy isn't reachable. - Failclose: Either resets the connection or silently drops packets.
- Failopen: Allows the traffic based on your matching criteria using Prisma Access explicit proxy.
![]() Save your proxy rule and Push Config.In Prisma Access, security rules are evaluated from top to bottom, where traffic matches the conditions of the first rule it meets, that rule is applied, and the evaluation process stops there; therefore, you should consider placing the most specific rules at the top of the list.You can delete, enable, disable, move, or clone an upstream proxy rule. To perform any of these actions, select the rule and then select the action.
Save your proxy rule and Push Config.In Prisma Access, security rules are evaluated from top to bottom, where traffic matches the conditions of the first rule it meets, that rule is applied, and the evaluation process stops there; therefore, you should consider placing the most specific rules at the top of the list.You can delete, enable, disable, move, or clone an upstream proxy rule. To perform any of these actions, select the rule and then select the action.
Configure Proxy Chaining on Prisma Access Explicit Proxy (Panorama)
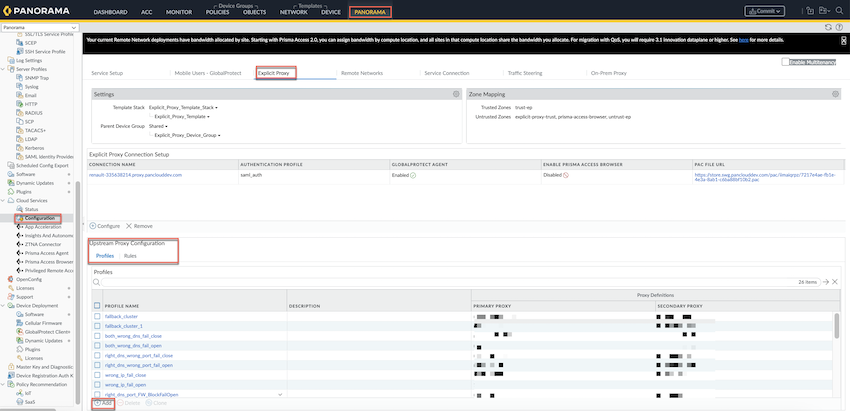
Here's how you configure downstream proxy chaining with Prisma Access explicit proxy on Panorama.- Set up an explicit proxy.Go to PanoramaCloud ServicesConfigurationExplicit ProxyUpstream Proxy Configuration.
![]() Create a Profile.
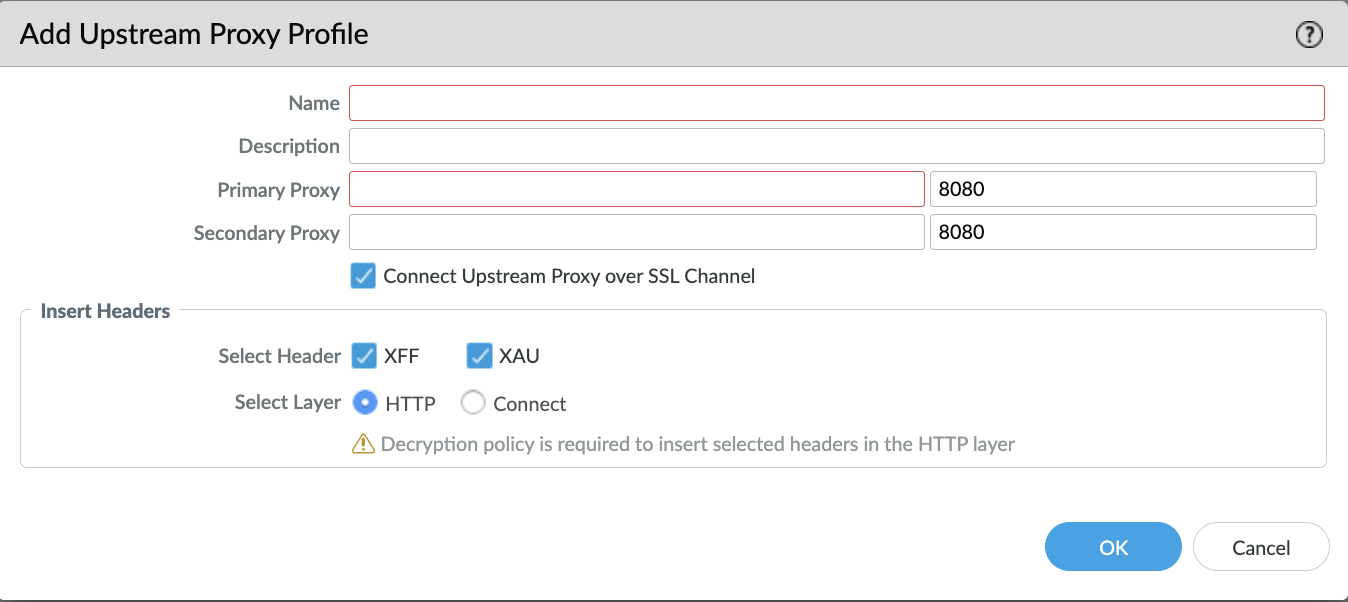
Create a Profile.- Under Profiles, Add to create a proxy profile.Add a Name, Description, a Primary Proxy, and optionally a Secondary Proxy. By default, the port is set as 8080. You can add the port as per your requirement.The FQDN should be resolvable to an IPv4 address or IP address should be IPv4 and reachable.(Optional) Select the headers XFF or XAU, select layer as HTTP or Connect to send information to an upstream proxy.If you add XFF and XAU headers and select the Connect layer, we recommend to enable Connect Upstream Proxy over SSL Channel to securely connect Prisma Access explicit proxy to another proxy.If you select HTTP and add XAU or XFF headers, we recommend having decryption on PAN-OS.
![]() Select OK to save the configuration changes.Configure proxy policy rules. You must Enable the rules for the configuration to get saved.
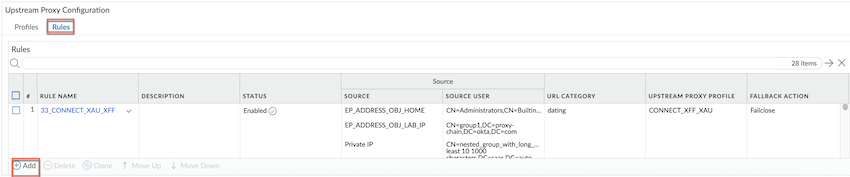
Select OK to save the configuration changes.Configure proxy policy rules. You must Enable the rules for the configuration to get saved.- Go to Rules and Add a proxy rule. Build your rule by configuring the following rule components. Components marked with an asterisk(*) are mandatory.
![]()
Section Element Details General *Name Give your rule a unique name that tells the other administrators what it does. Optionally provide a detailed description of the rule's intent and Enable. Match Criteria Source Define the matching criteria for the source fields for the traffic. - Specify the source IP *Addresses, or add an Address Groups or leave the value set to Any.
- Specify source *Users or leave the value set to Any. You can select Users to enforce the policy for individual users or a group of users.
Destination Define the destination address for the traffic. Specify a URL category as match criteria for the proxy chaining rule. Select URL Category to specify it as a match criteria in the proxy chaining rule or leave the value set to Any.Action *Upstream Proxy Define what Action you want to take for the traffic that matches the rule. Select an upstream proxy or select Direct. When you select Direct, the traffic egresses using Prisma Access explicit proxy to an upstream web or application server.Fallback Action Specifies a Failclose or Failopen action to apply when the selected upstream proxy isn't reachable. - Failclose: Either resets the connection or silently drops packets.
- Failopen: Allows the traffic based on your matching criteria using Prisma Access explicit proxy.
![]() Select OK to save the security rule, and Commit and push configurations to the Explicit_Proxy_Device_Group.In Prisma Access, security rules are evaluated from top to bottom, where traffic matches the conditions of the first rule it meets, that rule is applied, and the evaluation process stops there; therefore, you should consider placing the most specific rules at the top of the list.You can delete, enable, disable, move up, move down, or clone an upstream proxy rule. To perform any of these actions, select the rule and then select the action.
Select OK to save the security rule, and Commit and push configurations to the Explicit_Proxy_Device_Group.In Prisma Access, security rules are evaluated from top to bottom, where traffic matches the conditions of the first rule it meets, that rule is applied, and the evaluation process stops there; therefore, you should consider placing the most specific rules at the top of the list.You can delete, enable, disable, move up, move down, or clone an upstream proxy rule. To perform any of these actions, select the rule and then select the action.