Prisma Access
App-Based Office 365 Integration with Explicit Proxy (Strata Cloud Manager)
Table of Contents
Expand All
|
Collapse All
Prisma Access Docs
-
-
- Prisma Access China
- 4.0 & Later
- 3.2 Preferred and Innovation
- 3.1 Preferred and Innovation
- 3.0 Preferred and Innovation
- 2.2 Preferred
-
-
-
- 5.2 Preferred and Innovation
- 5.1 Preferred and Innovation
- 5.0 Preferred and Innovation
- 4.2 Preferred
- 4.1 Preferred
- 4.0 Preferred
- 3.2 Preferred and Innovation
- 3.1 Preferred and Innovation
- 3.0 Preferred and Innovation
- 2.2 Preferred
App-Based Office 365 Integration with Explicit Proxy (Strata Cloud Manager)
Prisma Access Explicit Proxy supports the
browser-based and app-based version of Office 365 (M365), including
Office Online (office.com). Web-based (browser-based)
Office 365 is supported with no additional configuration required
on Explicit Proxy; to use app-based version of Office 365, complete
the following steps.
- Visit the EDL Hosting Service and identify the Feed URL for your SaaS application.Review the Microsoft 365 documentation for more information which Feed URL is best for your use case. Additionally, consider the SaaS application and location of users accessing the SaaS application when identifying a Feed URL to use. For example, if you have a branch in Germany that only needs to access Exchange Online, select a Feed URL from the Service Area: Exchange Online for Germany.(Best Practices) Create a certificate profile to authenticate the EDL Hosting Service.
- Download the GlobalSign Root R1 certificate.Convert the GlobalSign Root R1 Certificate to PEM Format.Import the GlobalSign Root R1 certificate from Cloud Managed Prisma Access.
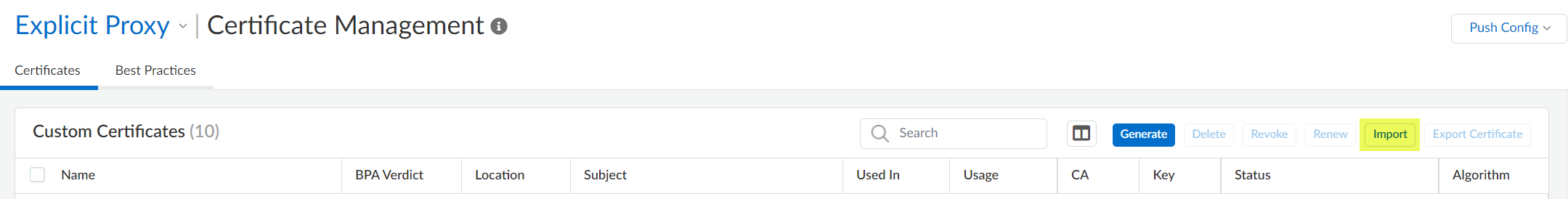
- In Prisma Access (Managed by Strata Cloud Manager), go to ManageConfigurationNGFW and Prisma AccessObjectsCertificate Management, set the configuration scope to Prisma AccessMobile Users ContainerExplicit Proxy, and Import a new certificate.
![]()
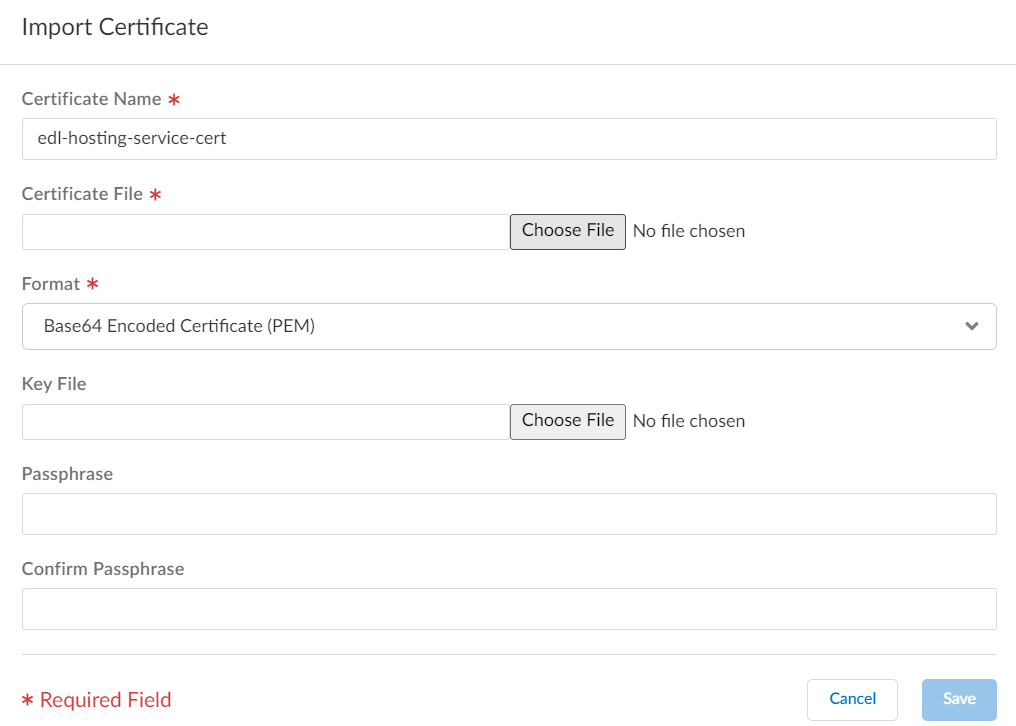
- Enter a descriptive Certificate Name.
- For the Certificate File, select Choose File and select the certificate you converted in the previous step.
- For the file Format, select Base64 Encoded Certificate (PEM).
- Save your changes.
![]()
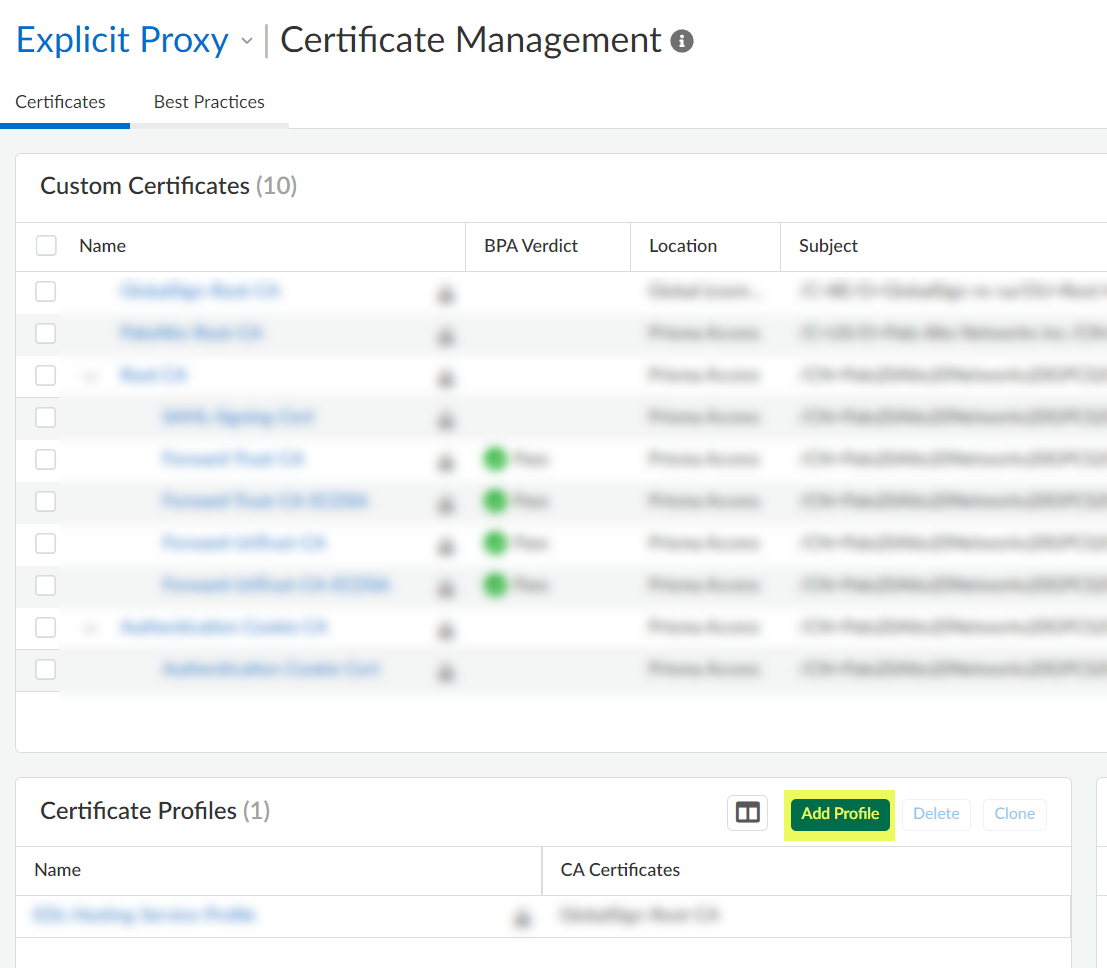
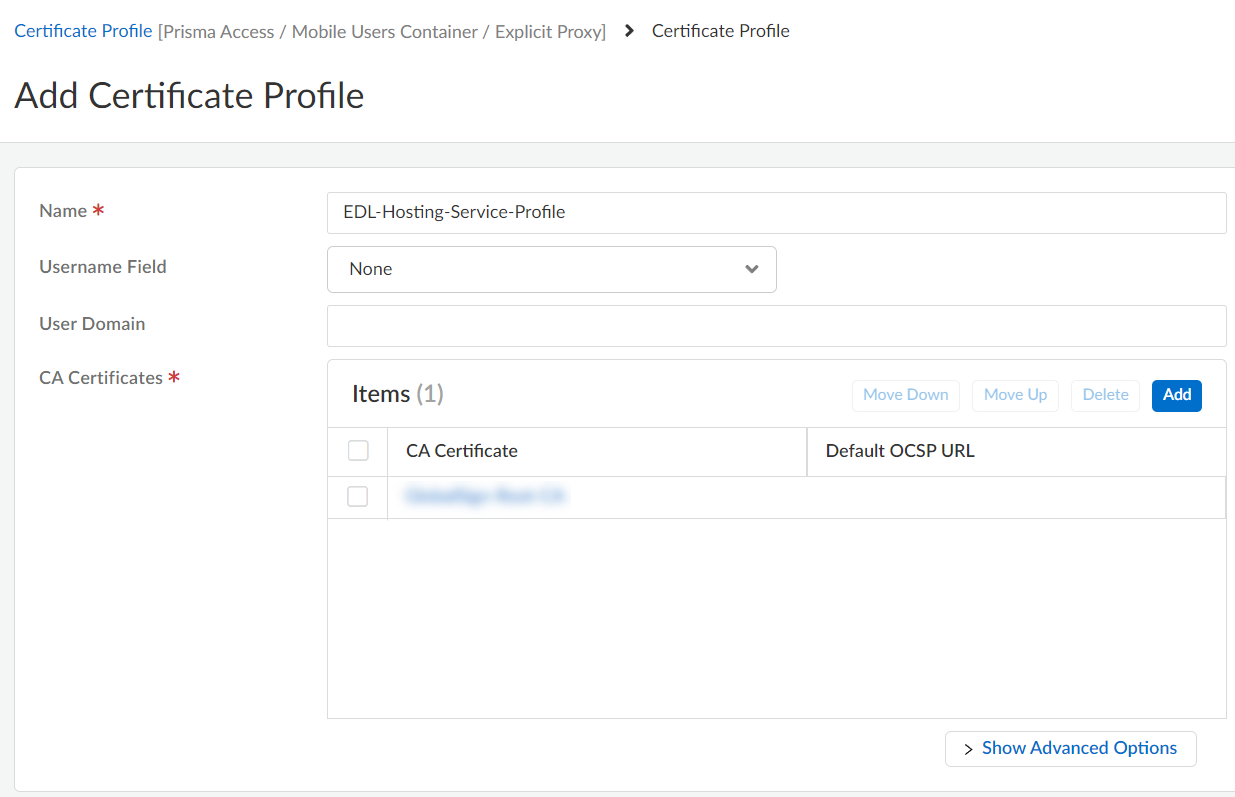
Create a certificate authority (CA) certificate profile.- Add Profile in the Certificate Profiles area.
![]()
- Enter a descriptive Name.
- For the CA Certificate, Add the certificate you imported in the previous step.
- Save your changes.
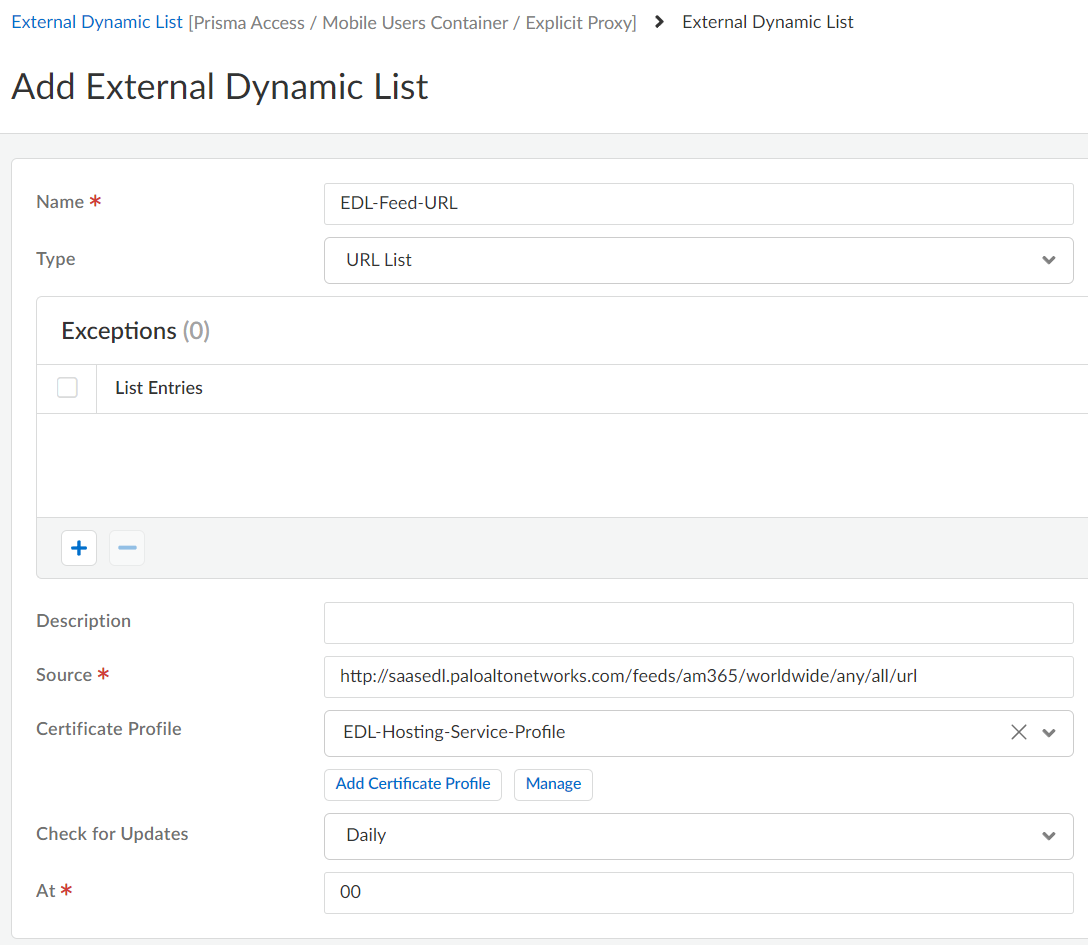
![]() Create an EDL using a Feed URL from the EDL Hosting Service.
Create an EDL using a Feed URL from the EDL Hosting Service.- Go to ManageConfigurationNGFW and Prisma AccessObjectsExternal Dynamic Lists and Add External Dynamic List. Set the configuration scope to Prisma AccessMobile Users ContainerExplicit Proxy.Enter a descriptive Name for the EDL.Select a Type of URL List.(Optional) Enter a Description for the EDLEnter the Feed URL as the EDL Source.Enforce all endpoints within a specific Feed URL. Adding an excluding a specific endpoint from a Feed URL can cause connectivity issues to the SaaS application.(Best Practices) Select the Certificate Profile you created in the previous step.Specify the frequency the firewall should Check for updates to match the update frequency of the Feed URL.For example, if the Feed URL is updated daily by Palo Alto Networks then configure the EDL to check for updates Daily.Palo Alto Networks displays the update frequency for each Feed URL in the EDL Hosting Service. Feed URLs are automatically updated with any new endpoints.Save your changes.
![]() Add a decryption policy to prevent decryption for the EDL Feed URLs.
Add a decryption policy to prevent decryption for the EDL Feed URLs.- Select go to ManageConfigurationNGFW and Prisma AccessSecurity ServicesDecryption and Add Rule. Set the configuration scope to Prisma AccessMobile Users ContainerExplicit Proxy.
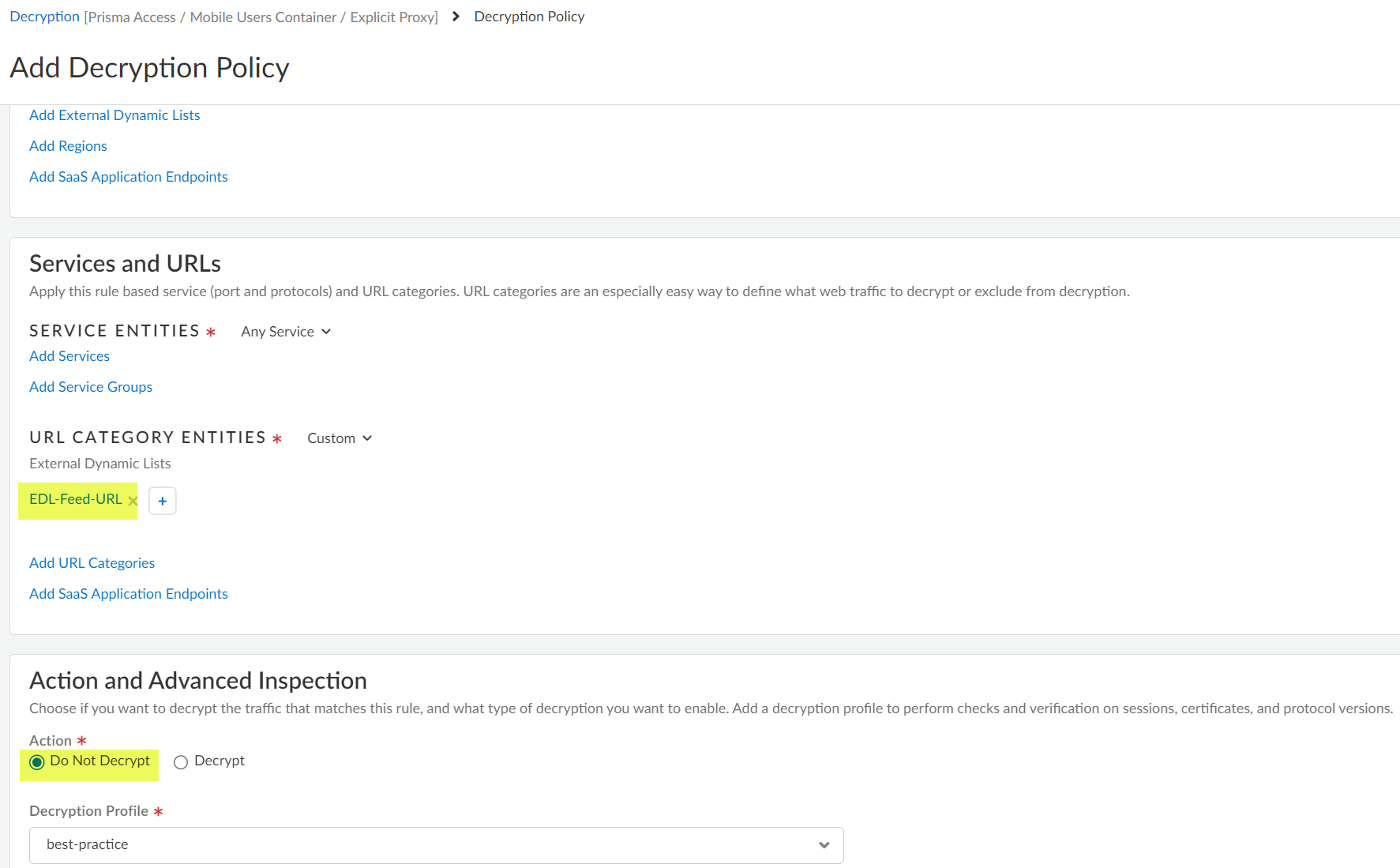
![]() Enter a descriptive Name for the policy.In the Services and URLs area, Add External Dynamic Lists and specify the EDL you created in an earlier step.Select an Action and Advanced Inspection of Do Not Decrypt.
Enter a descriptive Name for the policy.In the Services and URLs area, Add External Dynamic Lists and specify the EDL you created in an earlier step.Select an Action and Advanced Inspection of Do Not Decrypt.![]() Add a security policy rule to allow traffic from the EDL Feed URLs.
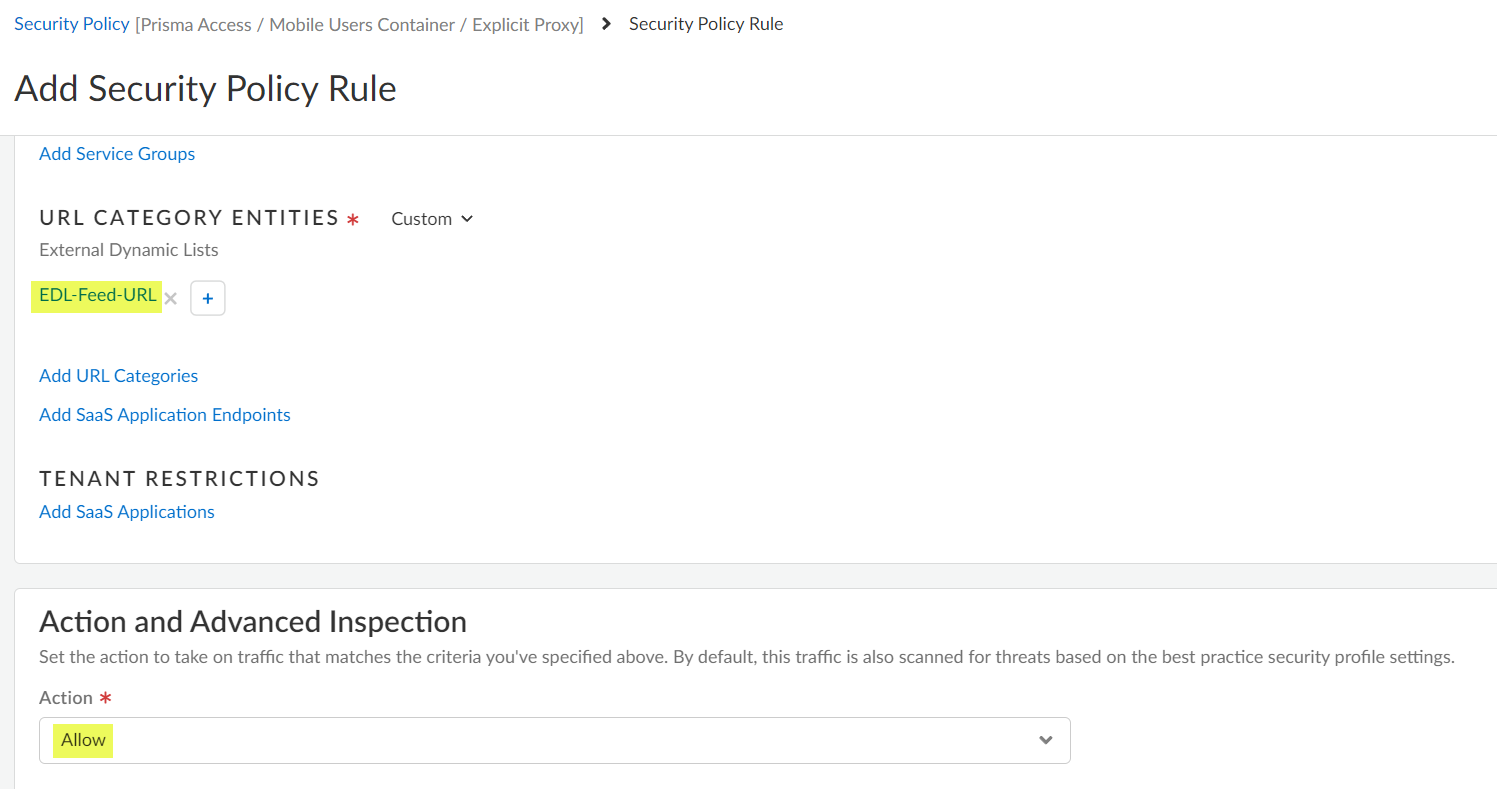
Add a security policy rule to allow traffic from the EDL Feed URLs.- Select ManageConfigurationNGFW and Prisma AccessSecurity ServicesDecryption and Add Rule. Set the configuration scope to Prisma AccessMobile Users ContainerExplicit ProxyEnter a descriptive Name for the policy.In the URL Category Entities area, Add External Dynamic Lists and specify the EDL you created in an earlier step.Select an Action and Advanced Inspection of Allow.
![]() Push Config to save your changes to Prisma Access.
Push Config to save your changes to Prisma Access.List of URLs to Enable Office 365 Integration with Prisma Access Explicit Proxy
One option you can use to integrate non-browser Office 365 apps with Explicit Proxy is to specify the Office 365-related URLs and bypass those URLs in the Explicit Proxy PAC file. Use one of the following methods to obtain the list of URLs to bypass:- Use the EDL URL from the Palo Alto Networks EDL Hosting Service for Microsoft 365 apps.Using the hosting service eases the operational burden of securing traffic to your SaaS applications by utilizing a Feed URL as the EDL source. When a SaaS provider adds a new endpoint for a SaaS application, the corresponding Feed URL is updated.For worldwide Microsoft 365 URLs, use the https://saasedl.paloaltonetworks.com/feeds/m365/worldwide/any/all/url URL. Other URLs are provided for IPv4 and IPv6 and for country-specific and governmental applications.
- Retrieve the list of Office 365 IP addresses and URLs provided by Microsoft at https://learn.microsoft.com/en-us/microsoft-365/enterprise/urls-and-ip-address-ranges. Microsoft also provides an Office 365 IP address and URL web service at https://learn.microsoft.com/en-us/microsoft-365/enterprise/microsoft-365-ip-web-service.