Prisma SD-WAN
Validate the Zscaler Configuration
Table of Contents
Expand All
|
Collapse All
Prisma SD-WAN Docs
-
-
- Prisma SD-WAN Controller
-
- CloudBlade Integrations
- CloudBlades Integration with Prisma Access
-
-
-
-
- 6.5
- 6.4
- 6.3
- 6.1
- 5.6
- Prisma SD-WAN Controller
- Prisma SD-WAN On-Premises Controller
- Prisma SD-WAN CloudBlades
- Prisma Access CloudBlade Cloud Managed
- Prisma Access CloudBlade Panorama Managed
Validate the Zscaler Configuration
Lets see how to validate the Zscaler configuration in Prisma SD-WAN.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
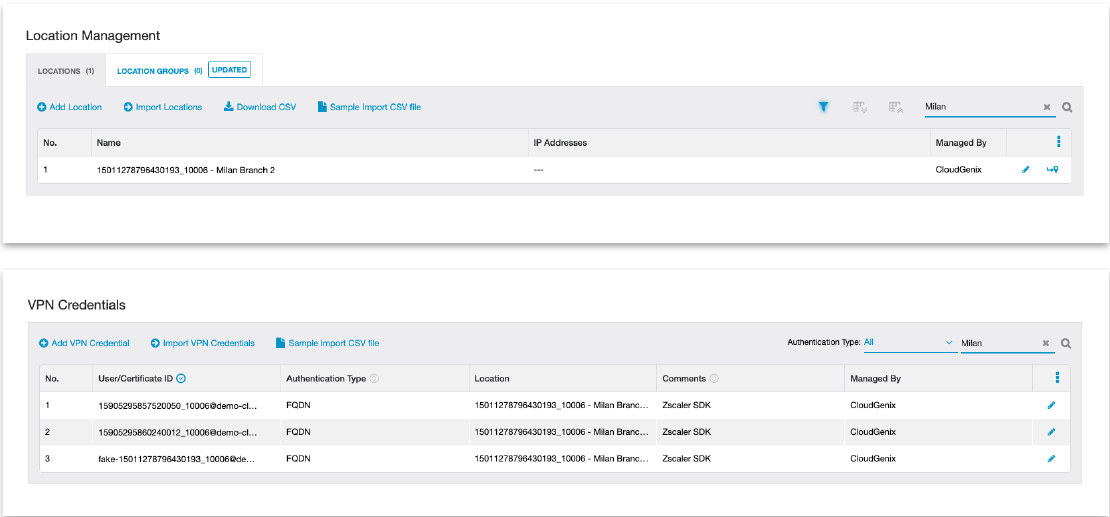
The Zscaler CloudBlade will provision locations and unique VPN credentials per tunnel
within Zscaler. Below is a sample output of the deployment for the Milan Branch 2
site from the Zscaler portal. This site has two circuits. Note that there is a third
fake VPN credential which is never used, but is part of the initial location
creation and onboarding process.
The status of the deployment and tunnels can be validated on the CloudBlades page as
follows:
- On the CloudBlades screen, click Monitor.
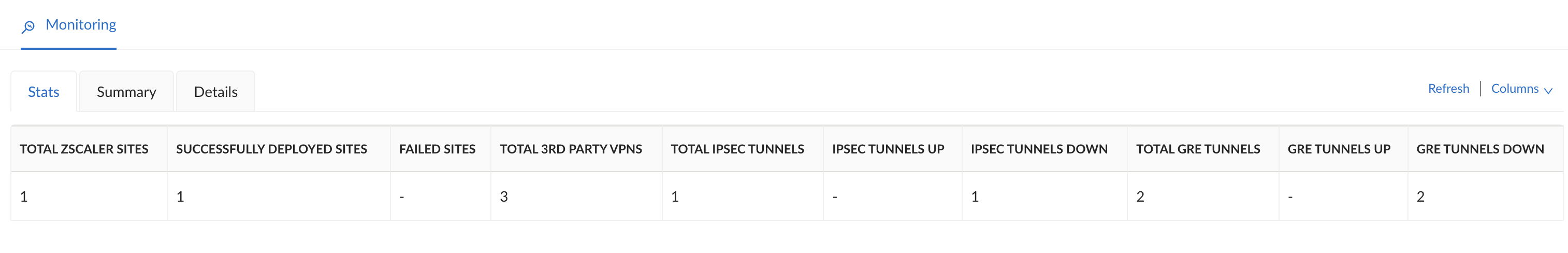
![]() Select the Stats tab to see information on the Zscaler sites and status of the IPSec and GRE tunnels.
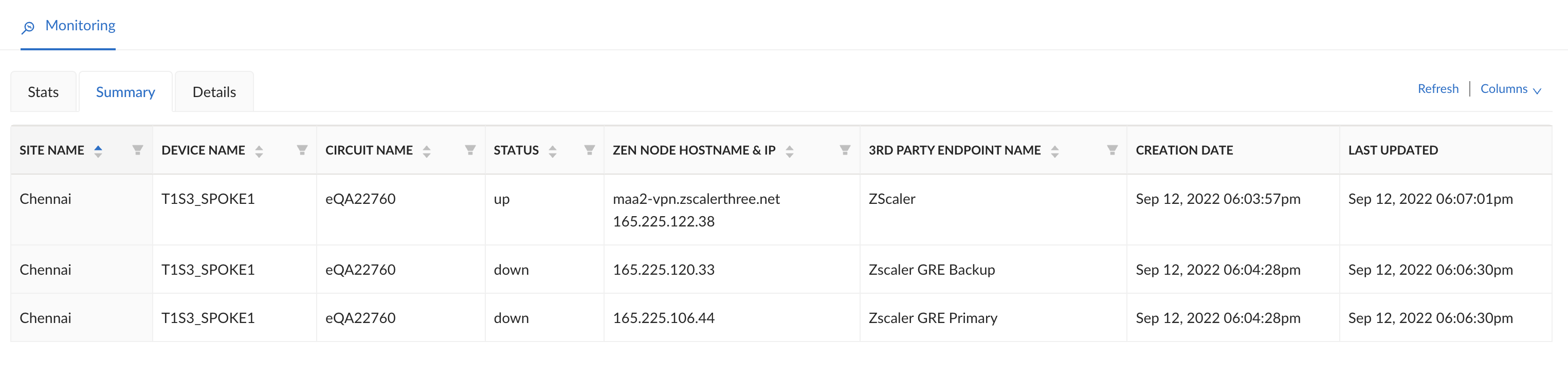
Select the Stats tab to see information on the Zscaler sites and status of the IPSec and GRE tunnels.![]() Select the Summary tab to see an overview of all the connected sites, ZEN node endpoints, and name of the third-party endpoints.
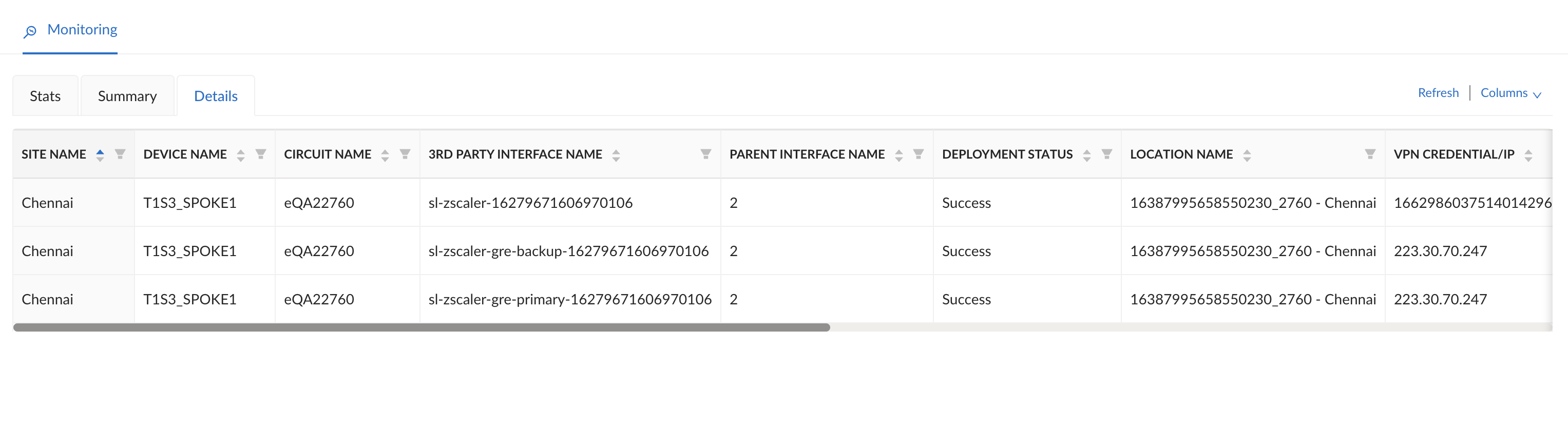
Select the Summary tab to see an overview of all the connected sites, ZEN node endpoints, and name of the third-party endpoints.![]() Select the Details tab to view the deployment status and the configuration details. These details are helpful for troubleshooting.
Select the Details tab to view the deployment status and the configuration details. These details are helpful for troubleshooting.![]()
Edit Application Network Policy Rules
Once the CloudBlade configures the appropriate Standard VPN objects within Prisma SD-WAN and Zscaler, the administrator can reference the path (Standard VPN) and service group (Zscaler) within application network policies. The ION devices will make intelligent per-app path selections using the network policies to chain multiple path options together in Active-Active and Active-Backup modes.Example:- Application A: Take Standard VPN direct to Zscaler.
- Application B: Take Standard VPN direct to Zscaler; Backup to Direct Internet.
- Application C: Go to Internet through Prisma SD-WAN; Backup to Standard VPN direct to Zscaler.
- Application D: Use only Direct Internet.
The Prisma SD-WAN Secure Application Fabric (AppFabric) enables granular controls for virtually unlimited number of policy permutations down to the sub-application level. Here are some of the most common examples of how traffic policy can be configured per application:- Send all internet-bound traffic from a set of branches to a Zscaler datacenter. (Blanket Greylist)
- Send all internet-bound traffic from a set of branches to a Zscaler datacenter with the exception of specific known applications. (Greylist-Whitelist)
- Send all internet traffic direct to the internet except for certain applications needing additional inspection or security. (Whitelist-Greylist)