Prisma SD-WAN
Configure and Integrate Prisma Access CloudBlade (Cloud Managed CloudBlade)
Table of Contents
Expand All
|
Collapse All
Prisma SD-WAN Docs
-
-
-
-
- AWS Transit Gateway
- Azure vWAN
- Azure vWAN with vION
- ChatBot for MS Teams
- ChatBot for Slack
- CloudBlades Integration with Prisma Access
- GCP NCC
- Service Now
- Zoom QSS
- Zscaler Internet Access
-
-
- ION 5.2
- ION 5.3
- ION 5.4
- ION 5.5
- ION 5.6
- ION 6.0
- ION 6.1
- ION 6.2
- ION 6.3
- ION 6.4
- New Features Guide
- On-Premises Controller
- Prisma Access CloudBlade Cloud Managed
- Prisma Access CloudBlade Panorama Managed
- Prisma SD-WAN CloudBlades
Configure and Integrate Prisma Access CloudBlade (Cloud Managed CloudBlade)
Configure and Integrate Prisma Access CloudBlade (Cloud Managed CloudBlade) by
entering all the parameters to enable remote networks in Prisma Acces.
- From the Prisma SD-WAN web interface, select CloudBlades.In CloudBlades, locate the Prisma Access for Networks (Cloud Managed) CloudBlade and click Configure. If this CloudBlade does not appear in the list, contact Palo Alto Networks Support.
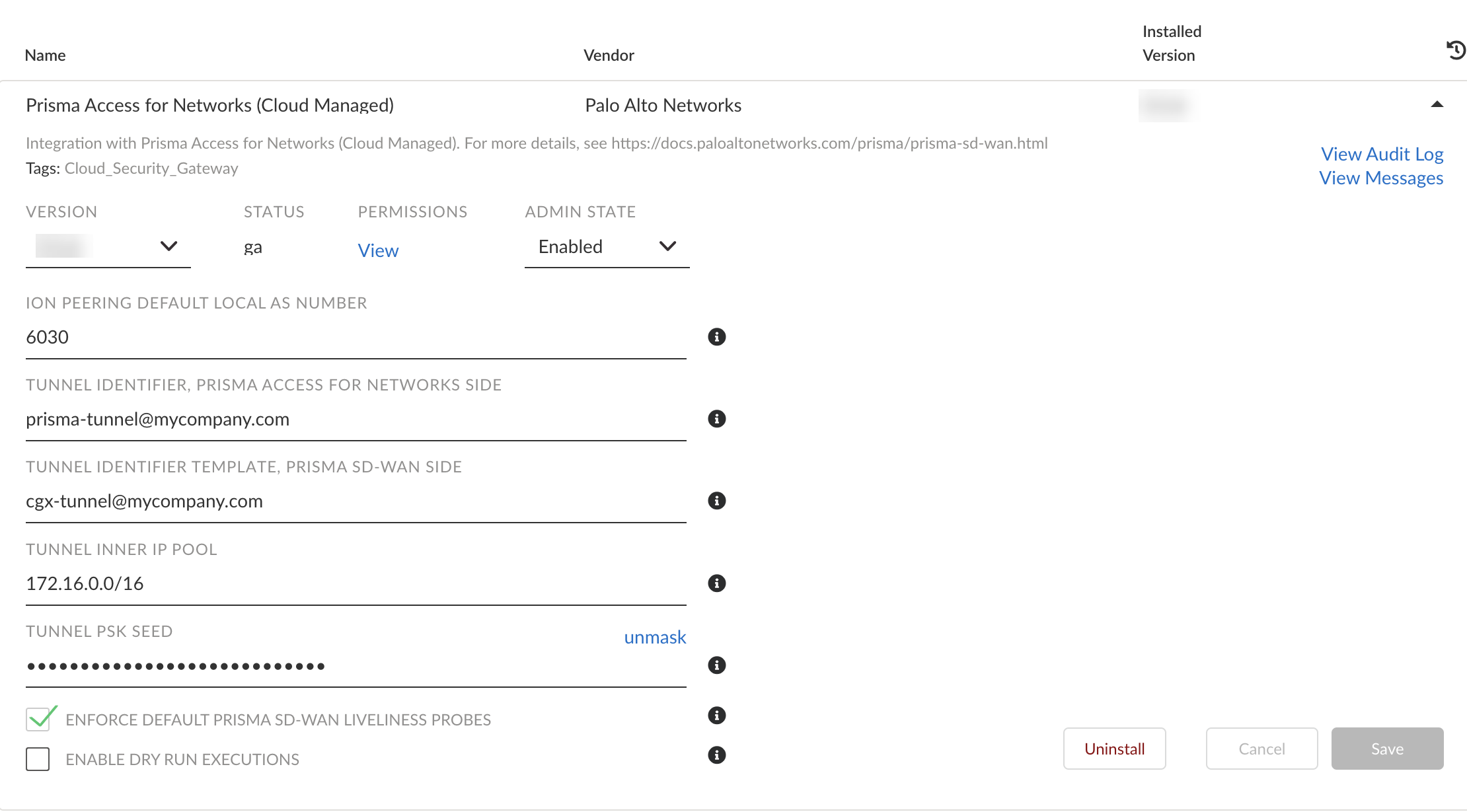
![]() Enter the following information in the fields shown below. Change where appropriate:
Enter the following information in the fields shown below. Change where appropriate:- VERSION: Select the version of the CloudBlade to use.
- ADMIN STATE: For the admin state, select or retain Enabled.
- ION PEERING DEFAULT LOCAL AS NUMBER: The BGP Local AS number is defined to quickly onboard ECMP sites. This can be any 16-bit AS number, but private BGP AS numbers are recommended.
- TUNNEL IDENTIFIER, PRISMA ACCESS FOR NETWORKS SIDE: Enter an FQDN IKE identifier in name@domain.com format. This identifier will be used by Prisma Access to identify remote tunnel connections.
- TUNNEL IDENTIFIER TEMPLATE, PRISMA SD-WAN SIDE: Enter an FQDN IKE identifier in name@domain.com format. This identifier should be different from the Prisma Access identifier. This identifier will serve as a template for generating a unique ID for each tunnel.
- TUNNEL INNER IP POOL: Specify an IP pool, using
IP address or Mask notation. This IP Pool should be unused or unique
across the entire network and should not be used by the Palo Alto
Service Infrastructure subnet.If you want to change the IP Prefix specified here, start by disabling the CloudBlade and ensuring all service links are updated. Now, change the IP CIDR to the required value and enable the CloudBlade to allocate Tunnels based on the new IP CIDR.The number of tunnels created in the Prisma SD-WAN Fabric to Prisma Access are directly limited by this configuration. Each tunnel will use a /31 subnet from this pool.
- TUNNEL PSK SEED: Specify a string of text, which will be used to derive the unique pre-shared keys (PSKs) used per tunnel.
- ENFORCE DEFAULT PRISMA SD-WAN LIVELINESS PROBES: For Prisma Access, the default is to leverage an ICMP probe to the last Prisma Access Infrastructure IP address. You can reconfigure this to probe non-default tunnel monitor IP addresses that were configured during Prisma Access integration.
- ENABLE DRY RUN EXECUTIONS: When enabled, the CloudBlade logs the changes made on Prisma SD-WAN and the CloudBlade in the Logs and Status Monitor. You can use this option to check the changes required by the CloudBlade.
Click Install after configuring the settings.![]()