SaaS Security
Scan a Single Amazon S3 Account
Table of Contents
Expand All
|
Collapse All
SaaS Security Docs
Scan a Single Amazon S3 Account
Learn how Data Security scans S3 buckets for a single
AWS account.
To enable scanning of S3 buckets for a single AWS account, you must configure AWS IAM policy,
user, role, and CloudTrail logging before you can add the Amazon S3 app to Data Security.
- Log in to your AWS Console aws.amazon.com.Select ServicesSecurity, Identity & ComplianceIAM.Configure the Data Security policy used to connect to the Amazon S3 app.
- Select PoliciesCreate policy and then select Create Your Own Policy.In the Specify Permissions page, select JSON.Copy and paste the following configuration into the Policy editor section and click Next.
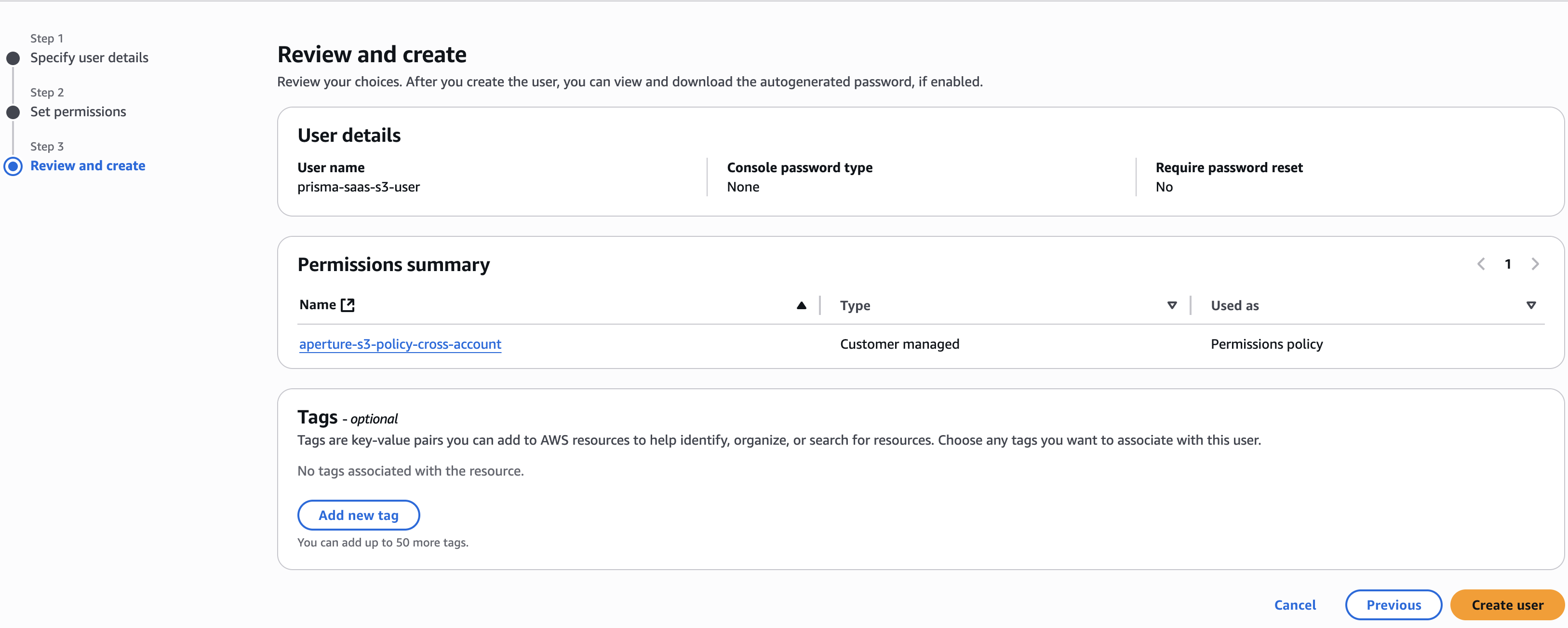
{ "Version": "2012-10-17", "Statement": [ { "Effect": "Allow", "Action": [ "s3:Get*", "s3:List*", "s3:Put*", "s3:Delete*", "s3:CreateBucket", "iam:GetUser", "iam:GetRole", "iam:GetUserPolicy", "iam:ListUsers", "cloudtrail:GetTrailStatus", "cloudtrail:DescribeTrails", "cloudtrail:LookupEvents", "cloudtrail:ListTags", "cloudtrail:ListPublicKeys", "cloudtrail:GetEventSelectors", "ec2:DescribeVpcEndpoints", "ec2:DescribeVpcs", "config:Get*", "config:Describe*", "config:Deliver*", "config:List*" ], "Resource": "*" } ]}Enter the Policy Name as prisma-saas-s3-policy and provide an optional description of the policy.Create Policy.Configure the account that Data Security will use to access the Amazon S3 logs:- Select Identity and Access Management (IAM)UsersCreate user.Enter the user name as prisma-saas-s3-user.Create an access key for an IAM user.Note your Access key ID and Secret access key.Select Next.Select Attach existing policies directly.Search for and select the check box next to the prisma-saas-s3-policy you created in the previous step.Select NextCreate User.
![]() Configure CloudTrail logging, if you have not already done so.CloudTrail logging enables the Amazon S3 app to log management and data events to the CloudTrail buckets of your choice.
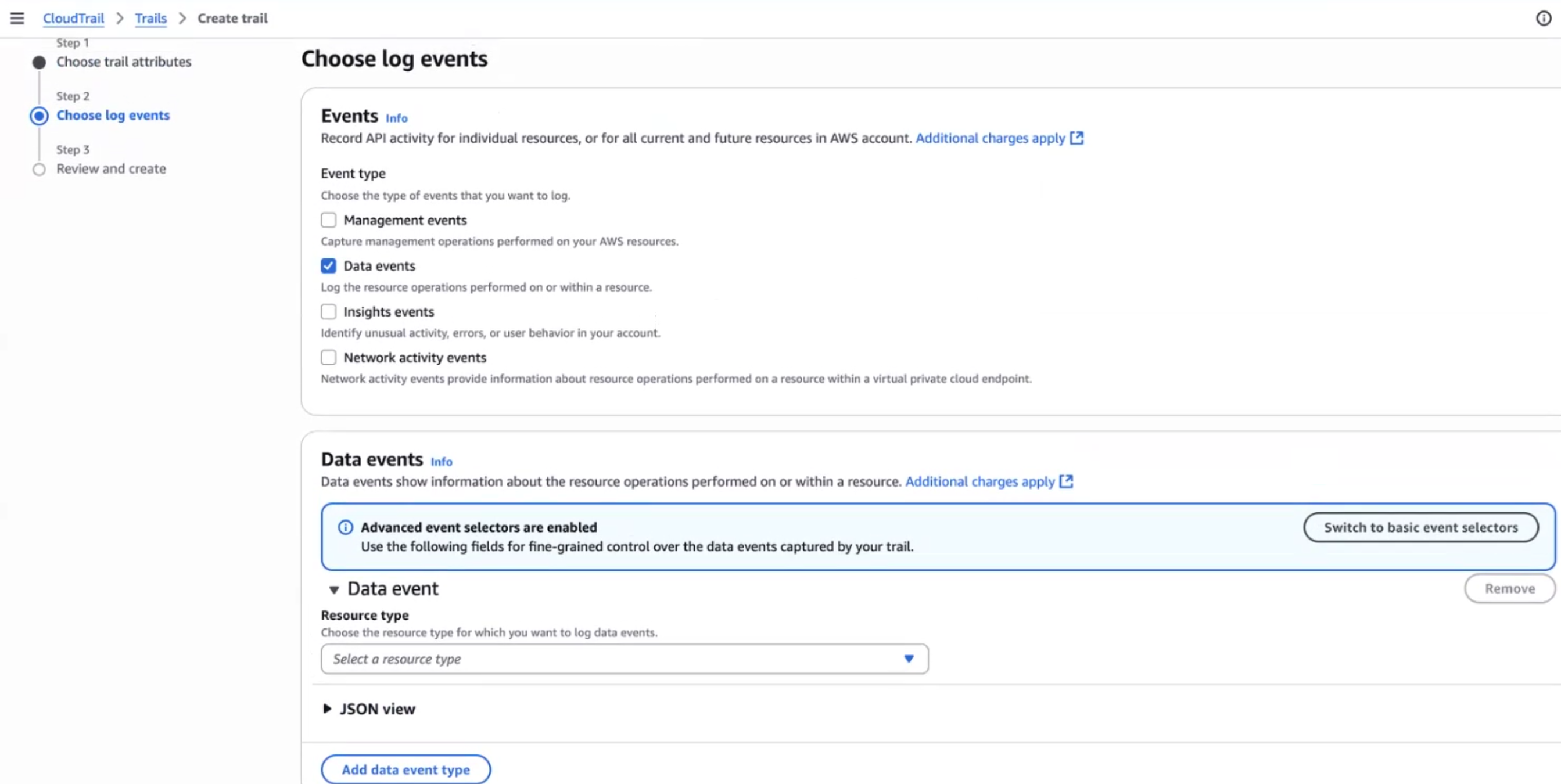
Configure CloudTrail logging, if you have not already done so.CloudTrail logging enables the Amazon S3 app to log management and data events to the CloudTrail buckets of your choice.- Copy your AWS account ID into memory by clicking on your username at the top right and copy the account number.You will need your account number later in this procedure.Select ServicesManagement ToolsCloudTrailTrailsCreate trail.Enter the Trail name prisma-saas-s3-trail.Deselect Log file SSE-KMS encryption.To create a bucket in which CloudTrail will store management and data event logs, enter the S3 bucket name as prisma-saas-s3-<AWS account ID> in the Storage location area.Take note of the S3 bucket (CloudTrail bucket name) and region.Select Next.In the Choose log events page, deselect Management Events and select Data events.In the Data events pane, select Switch to basic event selectorsContinue.
![]() Ensure you select S3 in the Data event source drop-down.You can choose to log read and/or write events for all buckets or choose individual buckets.
Ensure you select S3 in the Data event source drop-down.You can choose to log read and/or write events for all buckets or choose individual buckets.- Individual buckets—Operates as an allow list and requires ongoing maintenance.
Click Next, review the details and Create trail.Next Step: Proceed to adding the Amazon S3 app to .