SaaS Security
View Identity Threats for SaaS Apps
Table of Contents
Expand All
|
Collapse All
SaaS Security Docs
View Identity Threats for SaaS Apps
Navigate to the Identity page in SSPM to view threats by individual SaaS app
accounts.
The Identity page provides an overview of identity-related threats across SaaS apps
used in your organization. Details about the threats are listed in tables on the
following tabs:
- The Identity Threats tab, which provides details for each individual threat that SSPM detected. Each entry in this tab's table is a separate threat detected for a single SaaS application account.
- The Unique Identities tab. On this tab, SSPM attempts to resolve a user's various identities across SaaS apps into a single unified identity. The best results are realized if you have onboarded an instance of either the Microsoft Azure or the Okta identity provider. In this case, SSPM can determine the various SaaS apps that you're accessing through single sign-on (SSO). If you have not onboarded an identity provider, then SSPM uses email login addresses to determine unique identities across SaaS apps. If multiple SaaS app accounts are using the same email address for login, SSPM consolidates those accounts into a unique identity.
- To navigate to the Identity page, select ConfigurationSaaS SecurityPosture SecurityIdentity.
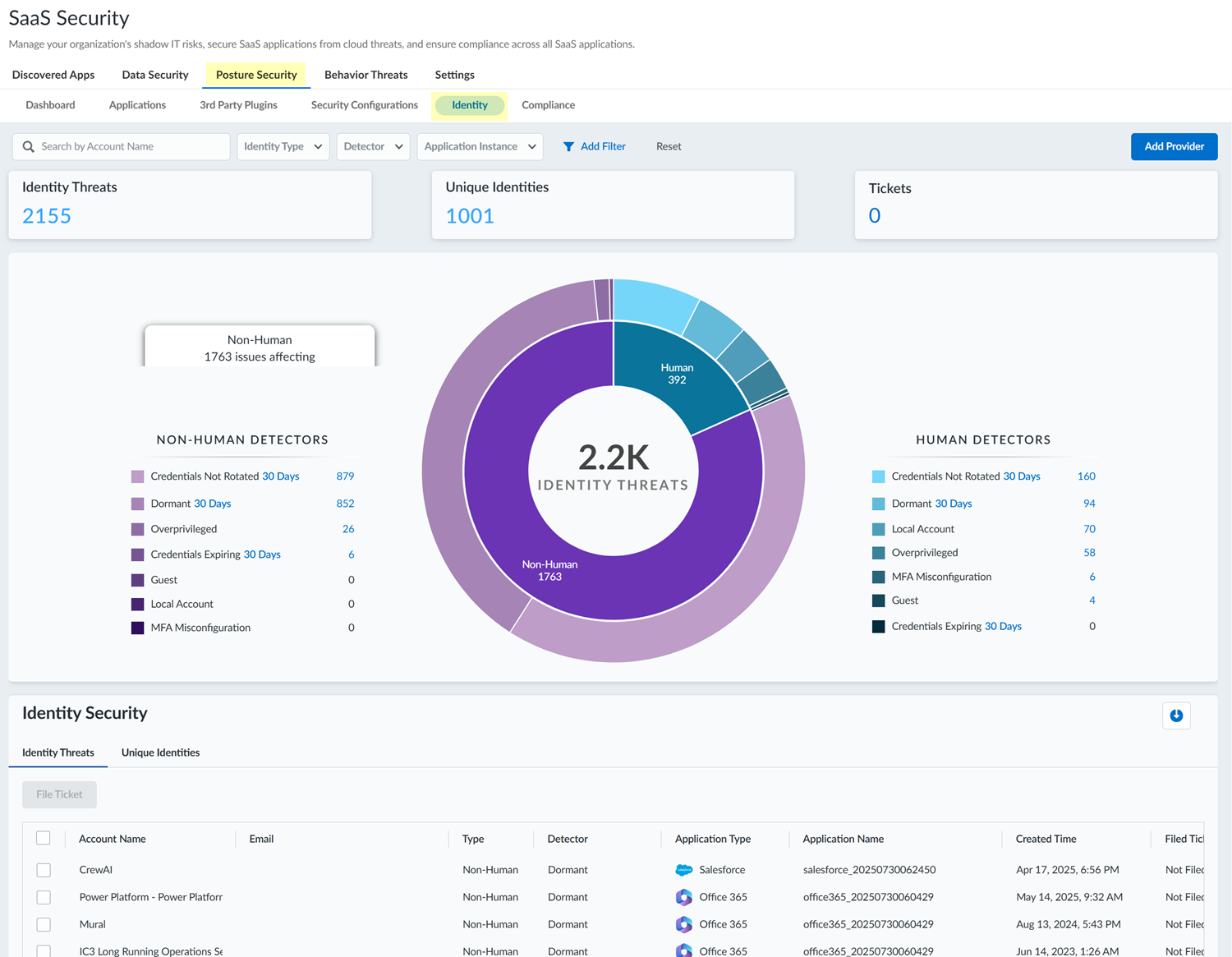
![]() SSPM supports identity scans for certain SaaS apps. If one or more of those SaaS apps were scanned, SSPM displays identity threats for those SaaS app instances. You can view a list of the SaaS app instances in the Application Instance filter list. To view a list of the SaaS apps that SSPM supports for identity scans, and to onboard instances of those apps, Add Provider.In the upper section of the Identity page, examine the overview of the identity threats that SSPM detected across all instances of the supported SaaS apps.This overview divides the threats into the threats detected for non-human identities (such as services that authenticate to an API by using a token or an API key) and human identities (accounts tied to individual people). For the non-human and human identities, the threats are further categorized by the types of threats (as indicated by the threats discovered by the different threat detectors).A donut chart represents all the detected identity threats, with slices of the chart representing threats for non-human and human identities relative to the whole. Additional slices of the donut chart show the percentage of different threat types detected relative to the whole. You can hover over the slices in the donut chart to display more details.In the lower section of the Identity page, view the information shown in the Identity Threats table, which lists the individual threats that SSPM detected.The table lists each threat that was detected for SaaS accounts. The table shows information about the account where the threat was detected. The account information shows the type of account (human or non-human) and the application. The Detector column shows the type of threat, as indicated by the detector name. Each entry in the table is a single threat, even if multiple threats were detected for the account. To view all the threats for a particular account, use the Search by Account Name filter in the upper-left corner of the Identity page.
SSPM supports identity scans for certain SaaS apps. If one or more of those SaaS apps were scanned, SSPM displays identity threats for those SaaS app instances. You can view a list of the SaaS app instances in the Application Instance filter list. To view a list of the SaaS apps that SSPM supports for identity scans, and to onboard instances of those apps, Add Provider.In the upper section of the Identity page, examine the overview of the identity threats that SSPM detected across all instances of the supported SaaS apps.This overview divides the threats into the threats detected for non-human identities (such as services that authenticate to an API by using a token or an API key) and human identities (accounts tied to individual people). For the non-human and human identities, the threats are further categorized by the types of threats (as indicated by the threats discovered by the different threat detectors).A donut chart represents all the detected identity threats, with slices of the chart representing threats for non-human and human identities relative to the whole. Additional slices of the donut chart show the percentage of different threat types detected relative to the whole. You can hover over the slices in the donut chart to display more details.In the lower section of the Identity page, view the information shown in the Identity Threats table, which lists the individual threats that SSPM detected.The table lists each threat that was detected for SaaS accounts. The table shows information about the account where the threat was detected. The account information shows the type of account (human or non-human) and the application. The Detector column shows the type of threat, as indicated by the detector name. Each entry in the table is a single threat, even if multiple threats were detected for the account. To view all the threats for a particular account, use the Search by Account Name filter in the upper-left corner of the Identity page.- To investigate a threat in more detail, click the View More link for the threat.If the Account Name in the table appears as a hyperlink, click the link to open an access graph, which shows the different SaaS apps that the identity can access. The access graph shows information, such as the SaaS apps that the user accesses through the identity provider versus direct login to local accounts. The access graph also shows SaaS apps that are accessed through non-human accounts that the unique identity created.In the lower section of the Identity page, view the information shown in the Unique Identities table.The table lists each unique identity that SSPM was able to discern from your identity provider or other sources. The Detector column shows the types of threats that SSPM detected for the unique identity across SaaS apps that the identity can access.When viewing either the Identity Threats or the Unique Identities tab, you can click the download icon to export a CSV file that contains the table information.Optionally, filter the information on the Identity page to show only the information that you're interested in.For example, you can filter the information by identity type (human or non-human), detector, or application instance. You can apply these filters using the Add Filter control, or by clicking on the relevant slices in the donut chart. To return to the full unfiltered view, Reset the filters.Investigate the accounts further and take action to resolve threats.For example, you might investigate dormant accounts to determine if you can delete them, or you might investigate guest accounts to ensure that their access to your resources is properly restricted. If SSPM is linked to an issue tracking system, you can create a ticket to resolve account threats. To do this, select one or more accounts names in the table and File Ticket.