SaaS Security
Onboard a Jamf Pro App to SSPM
Table of Contents
Expand All
|
Collapse All
SaaS Security Docs
Onboard a Jamf Pro App to SSPM
Connect a Jamf Pro instance to SSPM to detect posture risks.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
Or any of the following licenses that include the Data Security license:
|
For SSPM to detect posture risks in your Jamf Pro instance, you must onboard your
Jamf Pro instance to SSPM. Through the onboarding process, SSPM connects to the Jamf
Pro API and, through the API, scans yourJamf Pro instance for misconfigured settings
and account risks.
SSPM gets access to your Jamf Pro instance through an OAuth 2.0 client that you
create. During onboarding, you supply SSPM with the application credentials (Client
ID and Client Secret) for your OAuth 2.0 client. SSPM uses these credentials to
access the Jamf Pro API through the OAuth 2.0 client.
To access your Jamf Pro instance, SSPM requires the following information, which you
will specify during the onboarding process.
| Item | Description |
|---|---|
| Instance URL |
The unique URL for your Jamf Pro instance.
|
|
Client ID
|
SSPM will access the Jamf Pro API through an OAuth 2.0 client
that you create in Jamf Pro. Jamf Pro generates the Client ID to
uniquely identify this OAuth 2.0 client.
|
|
Client Secret
|
SSPM will access the Jamf Pro API through an OAuth 2.0 client
that you create in Jamf Pro. Jamf Pro generates the Client
Secret, which SSPM uses to authenticate to the API.
|
To onboard your Jamf Pro instance, you complete the following actions:
- Identify your instance URL, which appears in the browser's address bar.Jamf Pro typically creates your instance URL during the initial setup of your Jamf Pro environment, at which time you specify an instance name. Your full instance URL has the format https:// <instance-name>.jamfcloud.com.Before you continue to the next step, make note of this instance URL. You will provide this URL to SSPM during the onboarding process.Create the OAuth 2.0 client that SSPM will use to access the Jamf Pro API to scan your Jamf Pro instance.An OAuth 2.0 client in Jamf Pro consists of one or more API roles and an API client. An API role is a custom privilege set designed for non-human API access. An API client is the non-human identity that an external application, in this case SSPM, will use to authenticate to your Jamf Pro instance.
- Identify the Jamf Pro account that you will use to create the OAuth 2.0 client.Required Permissions: To create an API role and an API client, use an administrator account (an account assigned to the Administrator Privilege Set) with Full Access.Open a web browser to your Jamf Pro login page and log in to the administrator account that you identified.Create an API role to assign to your API client.An API role defines a set of permissions for an API client. In this case, you will create an API role that allows access to the scopes that SSPM will need to complete its scans.
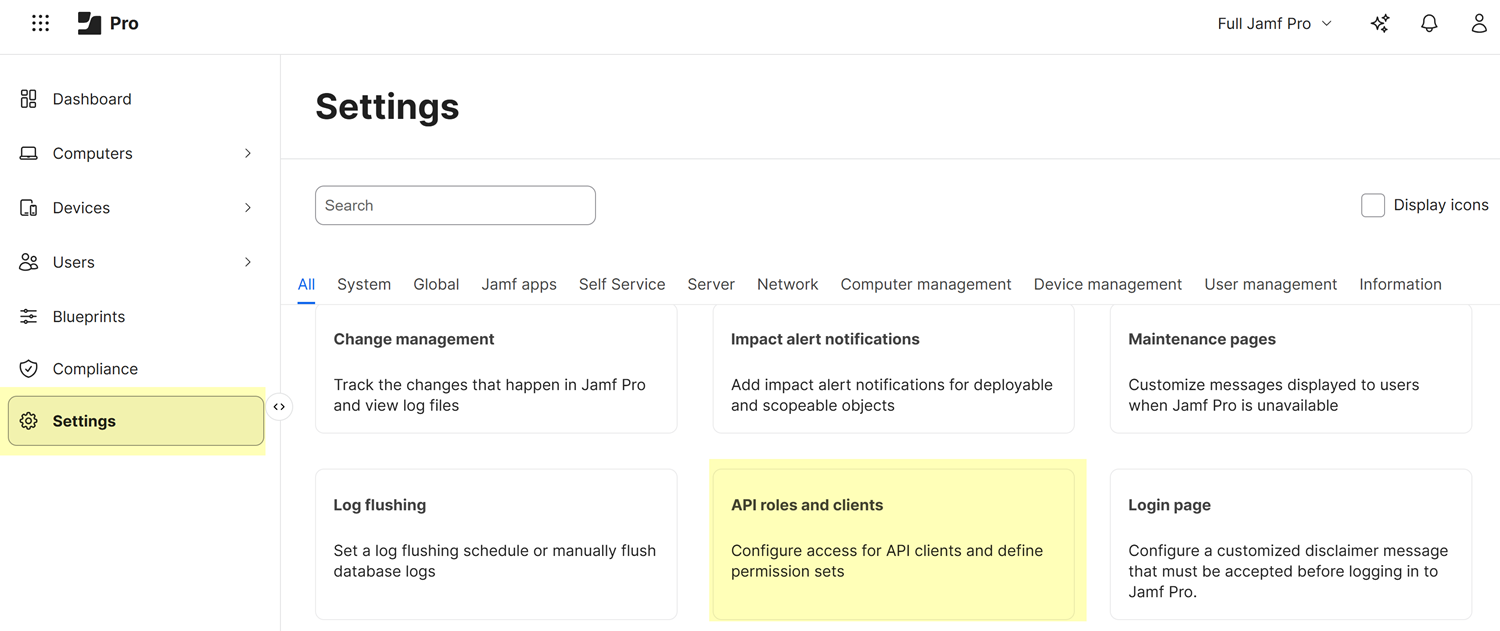
- In Jamf Pro, navigate to the Settings page. To do this, from the left navigation pane select Settings.
- On the Settings page, locate the System settings. In the
System settings, select API roles and
clients.
![]()
- On the API roles and clients page, select the API Roles tab and click + New.
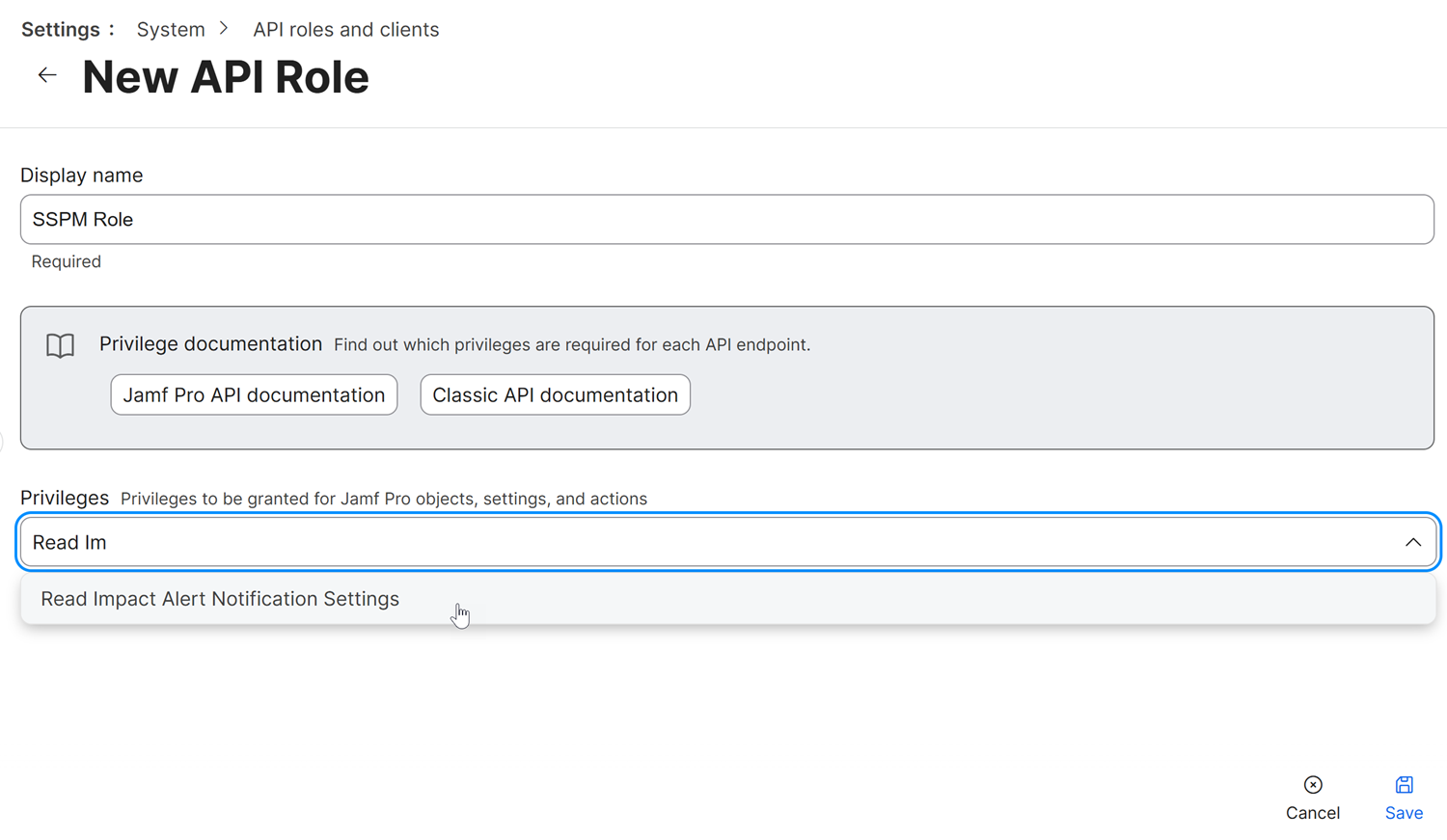
- On the New API Role page, complete the following actions:
- Specify a Display name for the API role. This name will appear in the list of API roles on the API Roles and Clients page. When you're creating the API client, this name will also appear in a selection list for assigning a role to the API client. For these reasons, specify a meaningful name, such as SSPM Role.
- In the Privileges field, add
the following privileges. These are the privileges
that SSPM requires to complete posture and identity
scans.
Privileges Scan Type - Read Impact Alert Notification Settings
- Read App Request Settings
- Read Automatically Renew MDM Profile Settings
- Read Policies
- Read Re-enrollment
- Read Computer Check-In
- Read User-Initiated Enrollment
Posture - Read API Integrations
- Read API Roles
- Read Accounts
- Read Webhooks
Identity ![]()
- Save the API role.
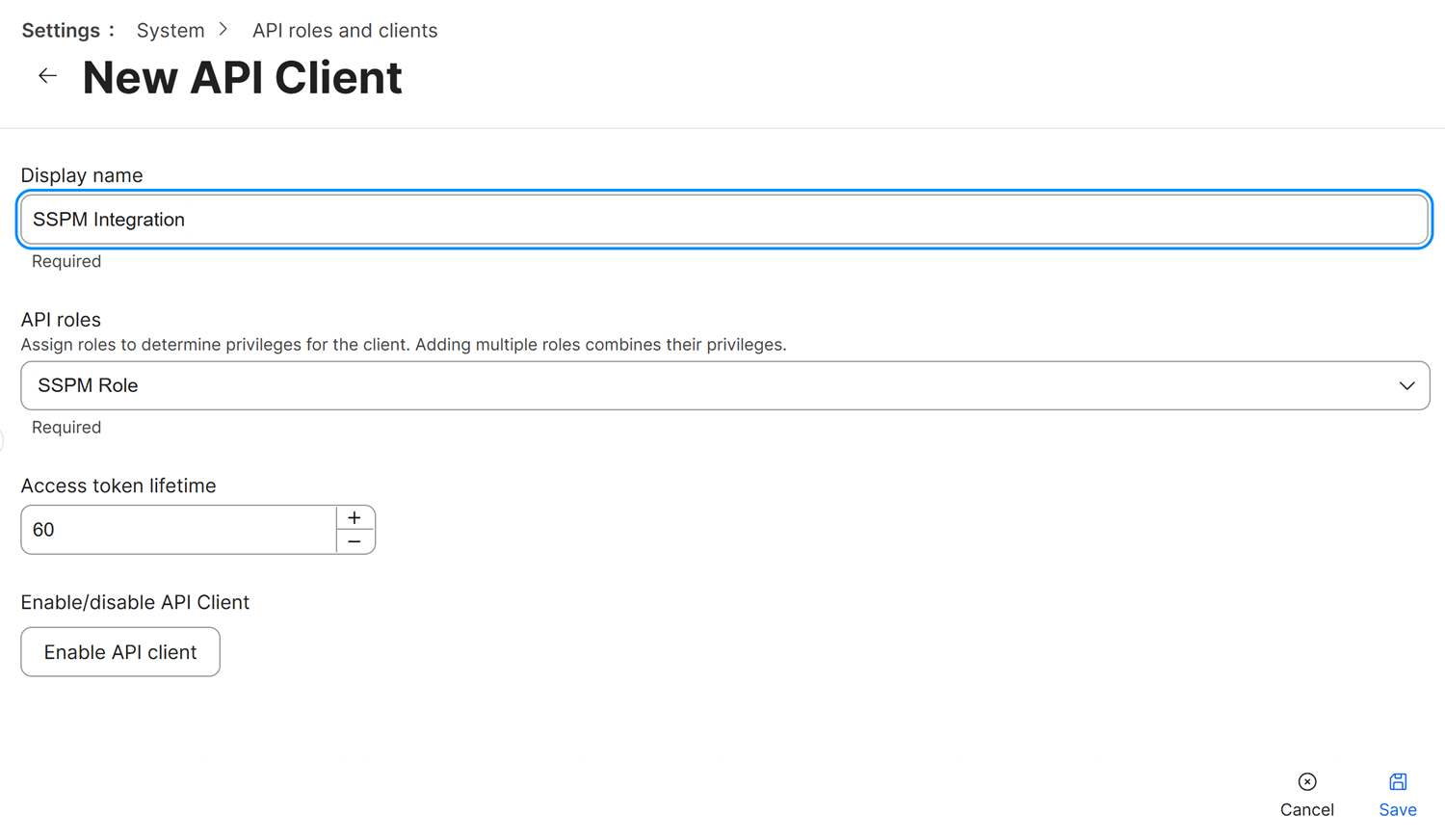
Create the API client.The API client is the Jamf Pro non-human identity that SSPM will use to authenticate with Jamf Pro. You will assign the API role you created to this API client to limit the client's permissions. Creating the API client generates the Client ID and Client Secret necessary for the integration with SSPM.- On the API roles and clients page, select the API Clients tab and click + New.
- On the New API Client page, complete the following actions:
- Specify a Display name for the API role. This name will appear in the list of API clients on the API Roles and Clients page. To distinguish it for other API clients in the list, specify a meaningful name. For example, SSPM Integration.
- In the API Roles field, add the API role that you created.
- Enable API client.
- Save the API client.
![]() Jamf Pro saves the API client and displays its configuration details.
Jamf Pro saves the API client and displays its configuration details.
- On the configuration details page for the API client, click
Generate client secret. After you confirm that you want to create the secret, Jamf Pro generates and displays the application credentials (Client ID and Client Secret) for your API client.
- Copy the credentials and paste them into a text file.Don’t continue to the next step unless you have copied both the Client ID and Client Secret. You must provide these credentials to SSPM during the onboarding process.
Connect SSPM to your Jamf Pro instance.In SSPM, complete the following steps to enable SSPM to connect to your Jamf Pro instance.- Log in to Strata Cloud Manager.Select ConfigurationSaaS SecurityPosture SecurityApplicationsAdd Application and click the Jamf Pro tile.On the Posture Security tab, Add New instance.Log in with Credentials.Enter your instance URL and the application credentials (Client ID and Client Secret).Connect.