SaaS Security
Onboard a Snowflake App to SSPM
Table of Contents
Expand All
|
Collapse All
SaaS Security Docs
Onboard a Snowflake App to SSPM
Connect a Snowflake App instance to SSPM to detect posture risks.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
Or any of the following licenses that include the Data Security license:
|
For SSPM to detect posture risks in your Snowflake instance, you must onboard your
Snowflake instance to SSPM. Through the onboarding process, SSPM connects to a
Snowflake API and, through the API, scans your Snowflake instance for misconfigured
settings. If there are misconfigured settings, SSPM suggests a remediation action
based on best practices.
SSPM gets access to your Snowflake instance through OAuth 2.0 authorization. To
enable OAuth 2.0 authorization, you first create an OAuth 2.0 security integration
in Snowflake. When creating this security integration, you will also create a custom
role that has the permissions that SSPM requires to run scans, and you will assign a
new user to this custom role.
During onboarding, you will provide SSPM with the following information.
| Item | Description |
|---|---|
| Account URL |
A URL for accessing your Snowflake account. This is the
account that you will use to create your OAuth 2.0 security
integration.
Required Permissions: The account that you will use
to create your OAuth 2.0 security integration must be
assigned to the ACCOUNTADMIN role.
|
| Client ID |
SSPM will access a Snowflake API through an OAuth 2.0
security integration that you create. Snowflake generates
the Client ID to uniquely identify this security
integration.
|
| Client Secret |
SSPM will access a Snowflake API through an OAuth 2.0
integration app that you create. Snowflake generates the
Client Secret, which SSPM uses to authenticate to this
security integration.
|
After you supply this information to SSPM, SSPM will redirect you to log in to
Snowflake. You will log in to Snowflake as the new user that you assigned to the
custom role. Snowflake will then prompt you to grant SSPM the access it needs to
your Snowflake instance.
As you complete the following steps, make note of the values of the items described
in the preceding table. You will need to enter these values during onboarding to
access your Snowflake instance from SSPM. You will also need to make note of the
user credientials for the new user that you assigned to the custom role.
- Create an OAuth 2.0 security integration.
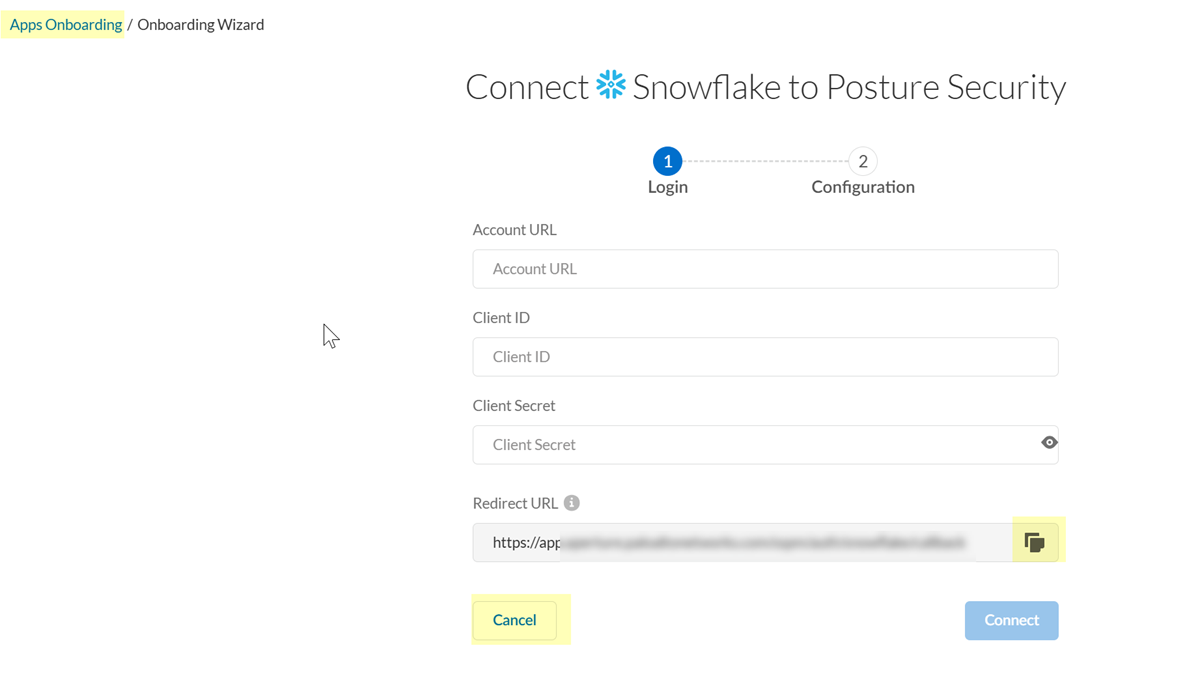
- From SSPM, get the redirect URL that you will need when you create your OAuth 2.0 security integration in Snowflake. To get this information, you will begin the onboarding process in SSPM, but you will not complete the process.
- Log in to Strata Cloud Manager.
- Select ConfigurationSaaS SecurityPosture SecurityApplicationsAdd Application and click the Snowflake tile.
- On the Posture Security tab, Add New instance.
- Log in with Credentials.SSPM displays a page for onboarding a Snowflake instance. The Redirect URL field displays the redirect URL value.
- Copy the URL and paste it into a text file.
![]() Don't continue to the next step unless you have copied the redirect URL. You will need to specify this URL later when you're configuring your OAuth 2.0 security integration in Snowflake.
Don't continue to the next step unless you have copied the redirect URL. You will need to specify this URL later when you're configuring your OAuth 2.0 security integration in Snowflake. - Because you won't be completing the onboarding process until after you have gathered the necessary configuration information, Cancel the onboarding process and return to the Apps Onboarding page.
Identify the Snowflake administrator account that you will use to create your OAuth 2.0 security integration. Verify that the administrator is assigned to the ACCOUNTADMIN role.To verify that the account is assigned to the necessary roles, complete the following steps:- From the left navigation pane in Snowflake, select AdminUsers & Roles.
- Select the name of the user whose roles you want to verify.
- On the information page for the user, locate the Granted Roles section. Verify that the user is assigned to the ACCOUNTADMIN role. If the user isn’t assigned to this role, you can Grant Role.
Identify the account URL for the Snowflake administrator account.- Open a web browser to the Snowflake login page, and log in to the administrator account you identified earlier.
- From the Snowflake home page, select AdminAccounts.On the Accounts page, hover over the LOCATOR column and click the link icon to copy the Account URL.
- Paste the account URL into a text file.Don’t continue to the next step unless you have copied the account URL. You will provide this information to SSPM during the onboarding process.
Create an OAuth 2.0 security integration.When you later onboard Snowflake to SSPM, you will supply SSPM with the application credentials (Client ID and Client Secret) of your OAuth 2.0 security integration. SSPM will redirect you to log in to Snowflake to allow the requested permissions.In this step, you will create an SQL worksheet to run a series of SQL statements that will create the OAuth 2.0 security integration and also the user account that you will use to log in to Snowflake to allow the requested permissions. The new user will be assigned to a new custom role that will limit the user's permissions to only the permissions that SSPM requires.- Open a web browser to the Snowflake login page, and log in to the administrator account you identified earlier.
- From the Snowflake home page, select ProjectsWorksheets.
- On the Worksheets page, select + SQL Worksheet to create an SQL worksheet.
- In the new worksheet that you created, select the ACCOUNTADMIN role and a warehouse that the ACCOUNTADMIN role has privileges to use.
- Paste the following SQL statements into your worksheet, and
replace the following variables in the worksheet with
information specific to the OAuth 2.0 security integration that
you're creating.
- The SQL statements first create a warehouse and a custom role for the user who will grant SSPM permissions during onboarding. In the SQL statements that we provided, replace all occurrences of <warehouse_name> and <custom_role_name> with names for the new warehouse and custom role.
- The SQL statements then create the user account that you
will use during onboarding to log in to Snowflake to
grant SSPM the permissions that it needs. Replace all
occurrences of <username> with the
name you want to give to this user. Also replace
<password> and
<email> with a user name and
password for the new user. Make note of the user name
and password.Don’t continue to the next step unless you have noted the user name and password. You will need this information to log in to Snowflake during the onboarding process.
- The SQL statements then grant the required permissions to the custom role and assign the user to the custom role. Double check that you have replaced all the variables in these sections.
- Finally, the SQL statements create the OAuth 2.0 security integration. Replace <integration_name> with a name for your OAuth 2.0 security integration. Replace <redirect_url_from_onboarding_page> with the redirect URL that you obtained from SSPM.
// Create minimum size warehouse and custom role CREATE OR REPLACE WAREHOUSE <warehouse_name> WITH WAREHOUSE_SIZE = XSMALL AUTO_SUSPEND = 30 AUTO_RESUME = TRUE INITIALLY_SUSPENDED = TRUE; CREATE OR REPLACE ROLE <custom_role_name>; // Create a new user CREATE OR REPLACE USER <username> PASSWORD='<password>' EMAIL='<email>' DEFAULT_ROLE=<custom_role_name> DEFAULT_WAREHOUSE=<warehouse_name>; // Give required permissions to the role GRANT OPERATE ON WAREHOUSE <warehouse_name> TO ROLE <custom_role_name>; -- To resume warehouse GRANT USAGE ON WAREHOUSE <warehouse_name> TO ROLE <custom_role_name>; -- To run SQL queries GRANT MONITOR ON ACCOUNT TO ROLE <custom_role_name>; -- Grants permission to approve OAuth integration GRANT APPLY PASSWORD POLICY ON ACCOUNT TO ROLE <custom_role_name>; -- To view password policy description GRANT APPLY AUTHENTICATION POLICY ON ACCOUNT TO ROLE <custom_role_name>; -- To view authentication policy description GRANT APPLY SESSION POLICY ON ACCOUNT TO ROLE <custom_role_name>; -- To view session policy description GRANT IMPORTED PRIVILEGES ON DATABASE SNOWFLAKE TO ROLE <custom_role_name>; -- To get all users // Assign the new user to the role GRANT ROLE <custom_role_name> TO USER <username>; // Create an OAuth security integration CREATE OR REPLACE SECURITY INTEGRATION <integration_name> TYPE = OAUTH OAUTH_CLIENT = CUSTOM OAUTH_CLIENT_TYPE = 'CONFIDENTIAL' OAUTH_REDIRECT_URI = '<redirect_url_from_onboarding_page>' OAUTH_ISSUE_REFRESH_TOKENS = TRUE OAUTH_REFRESH_TOKEN_VALIDITY = 7776000 ENABLED = TRUE; // Get Client ID and Client Secret SELECT SYSTEM$SHOW_OAUTH_CLIENT_SECRETS('<integration_name>'); - Click the run button in the upper-right corner of the worksheet page to execute the SQL statements.Snowflake will create the security integration, custom role, and user account. Snowflake displays the application credentials (Client ID and Client Secret) for the security integration in the Results area of the worksheet page.Copy the Client ID (OAUTH_CLIENT_ID) and Client Secret (OAUTH_CLIENT_SECRET) and paste them into a text file.Don't continue to the next step unless you have copied the Client ID and Client Secret. You must provide this information to SSPM during the onboarding process.Connect SSPM to your Snowflake instance.In SSPM, complete the following steps to enable SSPM to connect to your Snowflake instance.
- Log in to Strata Cloud Manager.Select ConfigurationSaaS SecurityPosture SecurityApplicationsAdd Application and click the Snowflake tile.On the Posture Security tab, Add New instance.Log in with Credentials.Enter the application credentials (Client ID and Client Secret) and the Account Locator and Connect.SSPM redirects you to the Snowflake login page.Log in to the new user account that you assigned to the new custom role.Snowflake displays a consent form that details the access permissions that SSPM requires.Review the consent form and allow the requested permissions.