5G Network Slice Security
Table of Contents
11.1 & Later
Expand all | Collapse all
-
- Intelligent Security and the UEIP Database
- Intelligent Security with PFCP for User Equipment to IP Address Correlation
- Configure Intelligent Security using PFCP for User Equipment to IP Address Correlation
- Configure Intelligent Security Using RADIUS for User Equipment to IP Address Correlation
- Configure Intelligent Security Using GTP for User Equipment to IP Address Correlation
5G Network Slice Security
Conceptual information about 5G network slice security.
Network slicing is about transforming
the system from a static, one-size-fits-all paradigm to a new paradigm
where logical networks and partitions are created with appropriate
isolation, resources, and optimized topology to serve a particular
purpose, service category, or individual customer.
From a mobile operator’s point of view, a network slice is an
independent, end-to-end, logical network that runs on a shared physical infrastructure,
capable of providing an agreed service quality. The technology enabling
network slicing is transparent to business customers for whom 5G
networks, in combination with network slicing, allow connectivity
and data processing tailored to the specific business requirements.
The customizable network capabilities include data speed, quality,
latency, reliability, security, and services. These capabilities
are always provided based on a Service Level Agreement (SLA) between
the mobile operator and the business customer. A network slice could
span multiple parts of the network (for example, access network,
core network, and transport network) and could be deployed across
multiple operators.
A network slice comprises dedicated and/or shared resources (for
example, processing power, storage, and bandwidth), and has isolation
from other network slices. Mobile network operators could deploy
a single network slice type that satisfies the needs of multiple verticals,
as well as multiple network slices of different types that are packaged
as a single product targeting business customers (a business bundle)
who have multiple, diverse requirements. For example, a vehicle
may simultaneously need a high bandwidth slice for infotainment
and an ultra-reliable slice for telemetry and assisted driving.
You can apply network security to an
enterprise or customer from a vertical industry that is using a fifth generation
cellular wireless (5G) network by creating Security policy rules based on network
Slice/Service Type (SST). 5G Control network functions communicate with each other using
the HTTP/2 protocol over service-based interfaces and with the User Plane Forwarding
Function (UPF) using packet forwarding control protocol (PFCP) over the N4 interface.
Traffic from User Equipment (UE) or IoT devices is carried in GTP-U tunnels in the 5G
network.
When the firewall is positioned at the N3 and N4 interfaces, the firewall monitors the
exchange of PFCP messages at the N4 interface. At the N3 interface, the firewall
decapsulates the GTP-U tunnels, which carry the user traffic. The firewall correlates
the Single Network Slice Selection Assistance Information (S-NSSAI) extracted from N4
interface with the IP traffic inside the GTP-U tunnels in a 5G network. The following
topology illustrates this deployment option in a 5G network.
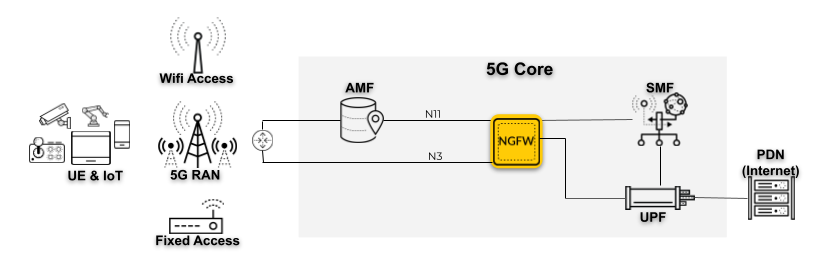
When the firewall is positioned at N3 and N11 interfaces, the firewall monitors the exchange of
control and signaling messages at the N11 interface, which uses HTTP/2 as the
application layer protocol. At the N3 interface, the firewall decapsulates the GTP-U
tunnels, which carry the user traffic. The firewall correlates the Single Network Slice
Selection Assistance Information (S-NSSAI) with the IP traffic inside the GTP-U tunnels
in a 5G network. The following topology illustrates a deployment option in a 5G
network.
PAN-OS® supports HTTP/2 control
messages on an N11 interface.
You can inspect HTTP/2 messages in a 3GPP 5G Service Based Architecture
(SBA) to extract S-NSSAI. An S-NSSAI consists of a Slice/Service
Type (SST) and optionally a Slice Differentiator (SD), which is
information that supplements the SST(s) to differentiate among multiple
network slices of the same SST.
You can also provide a way to secure dedicated network slices
for IoT customers. You configure Security policy rules for a 5G network
based on Network Slice/Service Type (SST) in two categories within
a single rule: standardized and operator-specific:
- Network Slice SST - Standardized—There are standardized
(predefined) slices, which are defined in 3GPP TS 23.501. PAN-OS® delivers
standardized values to you in dynamic Content Updates:
- eMBB (enhanced Mobile Broadband)—For faster speeds and high data rates, such as video streaming.
- URLLC (Ultra-Reliable Low-Latency Communications)—For mission-critical applications that are sensitive to latency, such as critical IoT (health care, wireless payments, home control, and vehicle communication).
- MIoT (Massive Internet of Things)—For smart metering, smart waste management, anti-theft, asset management, location tracking, and so on.
- Network Slice SST—Operator-specific—You name and specify the slice. The format of the slice name is text, followed by a comma (,) and a number in the range 128 to 255. For example, Enterprise Oil Company,145.
You can apply the following security per network slice or group
of network slices: application control, Antivirus, Anti-Spyware,
URL filtering, intrusion prevention, and advanced threat prevention
with WildFire®. You can log Network Slice ID SST and Network
Slice ID SD in traffic logs and GTP logs. In all other log types,
including URL Filtering, WildFire Submissions, Threat, Data Filtering,
and Unified logs, you can log Network Slice ID SST.
