Intelligent Security with PFCP for User Equipment to IP Address Correlation
Table of Contents
11.1 & Later
Expand all | Collapse all
-
- Intelligent Security and the UEIP Database
- Intelligent Security with PFCP for User Equipment to IP Address Correlation
- Configure Intelligent Security using PFCP for User Equipment to IP Address Correlation
- Configure Intelligent Security Using RADIUS for User Equipment to IP Address Correlation
- Configure Intelligent Security Using GTP for User Equipment to IP Address Correlation
Intelligent Security with PFCP for User Equipment to IP Address Correlation
Learn about the deployment topologies that Intelligent Security supports.
As enterprises migrate their networks to 5G, this transition provides the potential for
vulnerability to some of the security risks associated with 5G. As an unprecedented
number of devices connect to enterprise and government networks, this increases the
potential for attacks and other threats.
To address these concerns, networks need to provide simplified and holistic network
security that employs zero-trust policies that cover each user, device, application, and
piece of data.
Intelligent Security with PFCP supports multiple sources for PFCP and RADIUS for 5G/4G
mobile network identifier-based security with N6 or SGI-based firewalls.
Intelligent Security provides threat identification and policy enforcement capabilities
for:
- Subscribers (5G and 4G)
- Users (5G and 4G)
- Equipment (5G and 4G)
- Devices (5G and 4G)
- Network slices (5G)
This enables network administrators to extend zero-trust policies for their 5G and 4G
networks by consistently verifying all subscribers, equipment, applications, and data
based on content and subscriber activity.
To deploy a Palo Alto Networks firewall that supports Intelligent Security with PFCP,
first determine the optimal deployment topology for your firewall from the following
supported topologies.
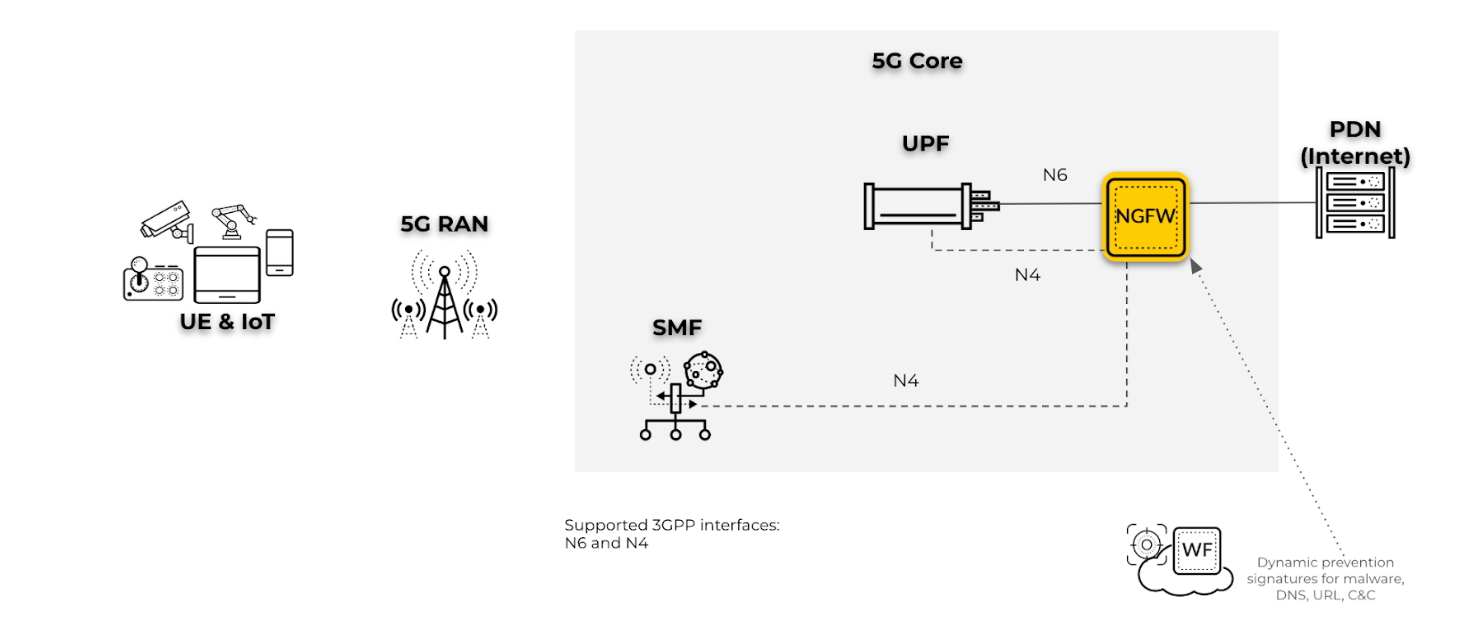
- Perimeter security for N6 interfaces with PFCP on N4 interfaces for a 5G network
: For this use case, deploy the firewall for perimeter security and to map user
equipment (UE) to IP addresses for UE subscriber and equipment traffic on the N6
interface. The firewall inspects the PFCP protocol traffic on the N4 interface.
![]()
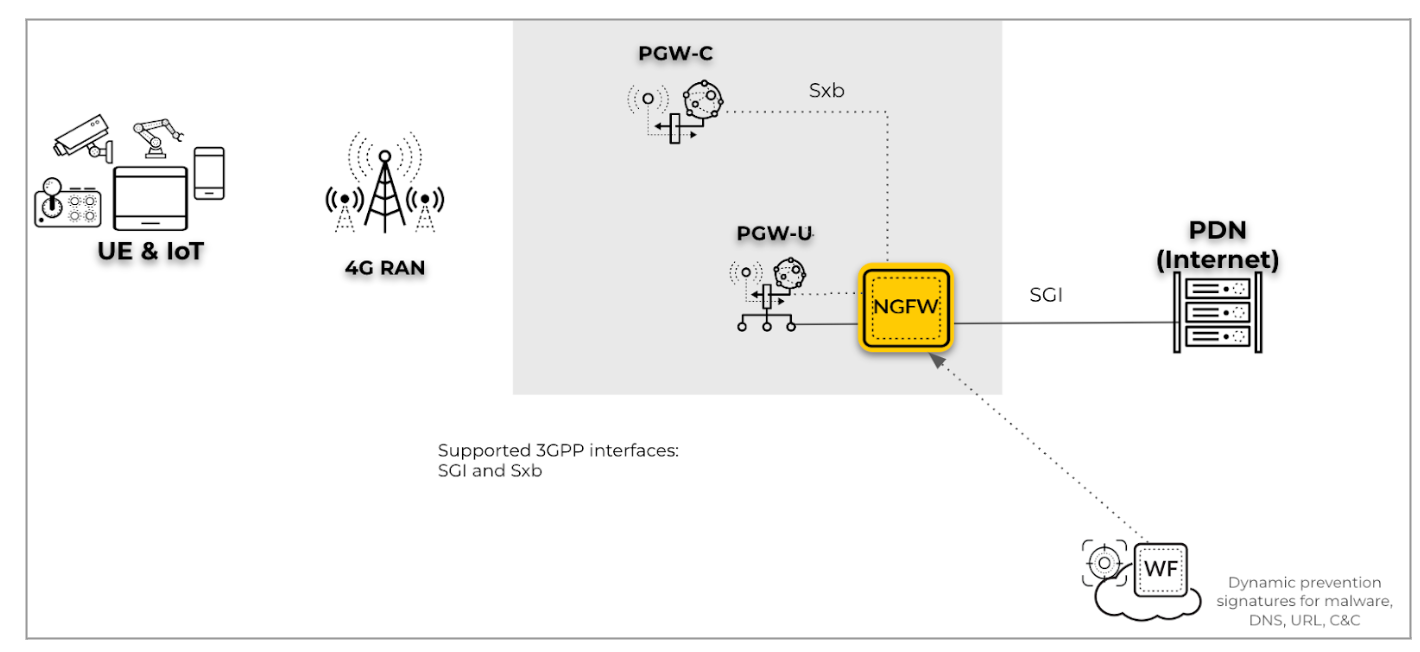
- Perimeter security for SGi interfaces with PFCP on Sxb interfaces for a 4G
Network: For this scenario, deploy the firewall for perimeter security and
to provide the UE-to-IP mapping for the UE subscriber and equipment traffic on the
SGi interface by inspecting the PFCP protocol traffic on the Sxb interface.
![]()
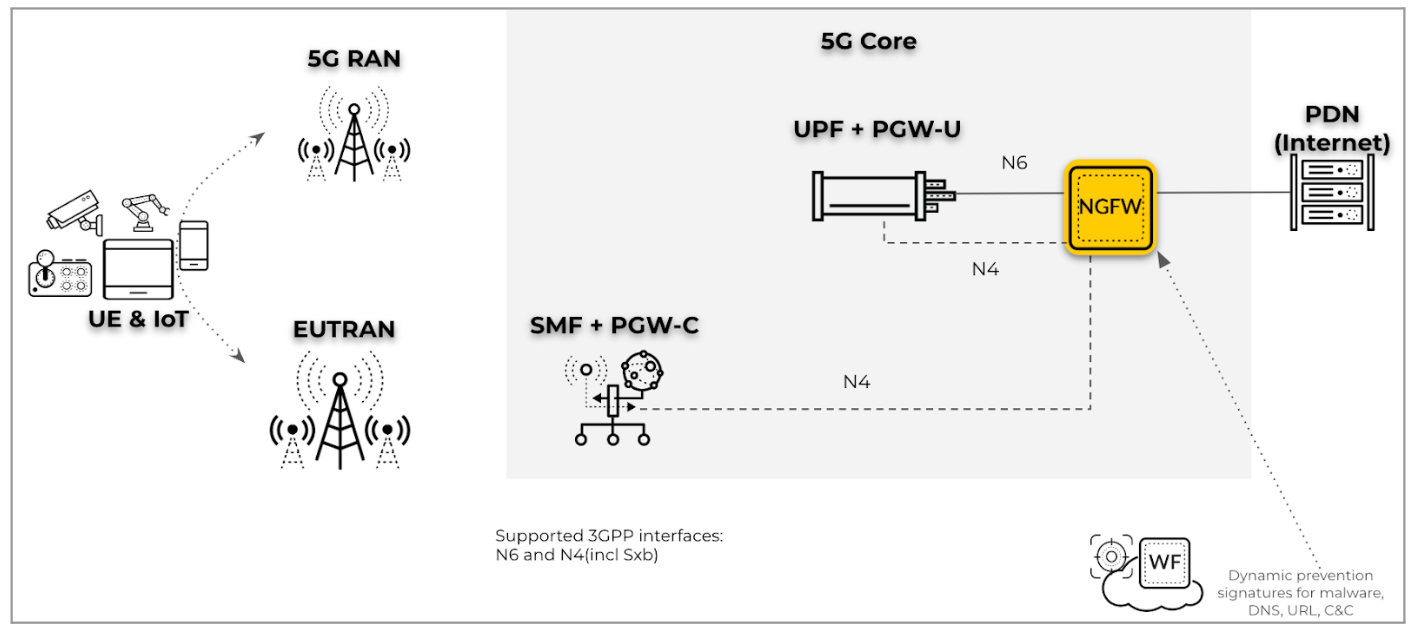
- Perimeter security on an N6 interface with PFCP on an N4 interface in a hybrid
(5G and 4G) network (including mobility): For this deployment type, deploy
the firewall for perimeter security for UE that transitions between 5G and 4G
networks. The firewall also provides the UE-to-IP mapping for UE subscriber and
equipment traffic on the N6 and SGi interfaces by inspecting the PFCP protocol
traffic on the N4 interface.
![]()
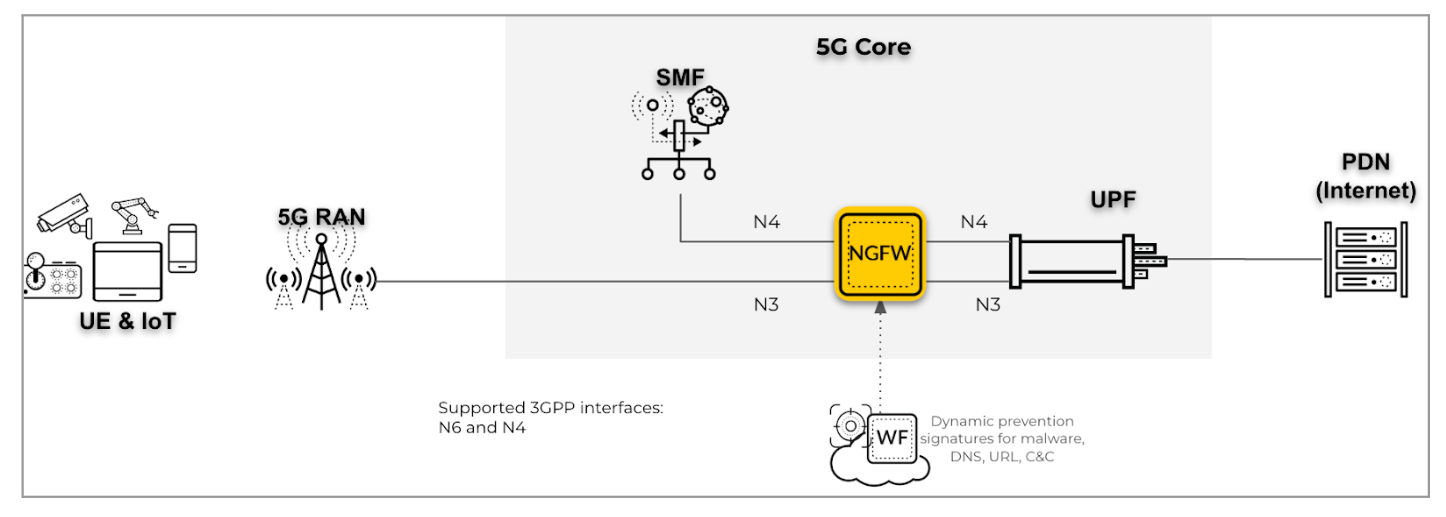
- RAN Security on an N3 interface with PFCP on an N4 interface in a 5G network:
For the deployment type, deploy the firewall for RAN security and to provide the
UE-to-IP mapping for UE subscriber and equipment traffic on the N3 interface by
inspecting the PFCP protocol traffic on the N4 interface. On the N3 interface, the
firewall decapsulates GTP-U packets for inspection and correlation.
![]()
- RAN security on an S1-U or N3 interface with PFCP on the N4 interface in a hybrid
(5G and 4G) network (including mobility): For this use case, deploy the
firewall for RAN security for UE that transition between your 5G and 4G networks.
The firewall also provides the UE-to-IP mapping for UE subscriber and equipment
traffic on the N3 and S1-U interfaces by inspecting the PFCP protocol traffic on the
N4 interface. On the N3 and S1-U interfaces, the firewall decapsulates GTP-U packets
for inspection and correlation.
![]()
- RAN security on S1-U PFCP on Sxb in 4G CUPS Network : For this scenario,
deploy the firewall for RAN security and to provide the UE-to-IP mapping for UE
subscriber and equipment traffic on the S1U interface in 4G CUPS-based networks by
inspecting the PFCP protocol traffic on the N4 interface. On the S1-U interface, the
firewall decapsulates GTP-U packets for inspection and correlation.
![]()