Enterprise DLP
Enable Enterprise DLP on Strata Cloud Manager
Table of Contents
Expand All
|
Collapse All
Enterprise DLP Docs
Enable Enterprise DLP on Strata Cloud Manager
Enable Enterprise Data Loss Prevention (E-DLP) for Prisma Access (Managed by Strata Cloud Manager) and NGFW (Managed by Strata Cloud Manager).
- Activate the Enterprise DLP license.
- Activate a standalone Enterprise DLP license.
- Activate a Next-Generation CASB for Prisma Access and NGFW (CASB-X) license.The CASB-X license includes the Enterprise DLP license by default. To activate Enterprise DLP for your CASB-X tenants, you only need to activate CASB-X. There is no individual Enterprise DLP license you need to activate when using CASB-X.
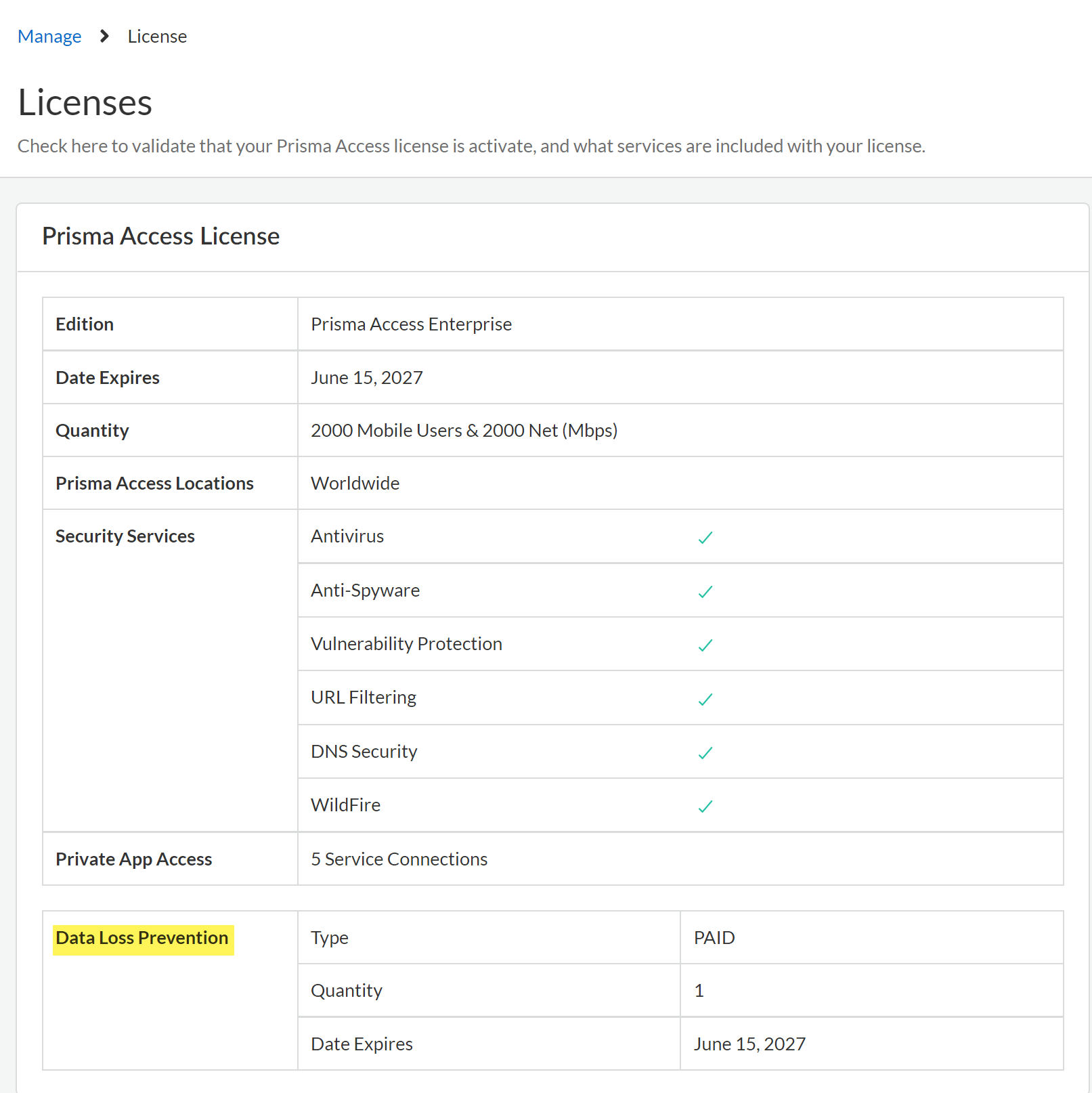
Review the Setup Prerequisites for Enterprise DLP and enable the required ports, Fully Qualified Domain Names (FQDN), and IP addresses on your network.This is required to forward traffic to Enterprise DLP for inspection and verdict rendering.Log in to Strata Cloud Manager.Verify that the Enterprise DLP license is active.- Select ConfigurationNGFW and Prisma AccessOverview and navigate to the Licenses widget.Click the license Quantity and confirm that the Data Loss Prevention license is active.Confirm the Data Loss Prevention license Type displays PAID and that an expiration date is displayed.
![]() Select Configuration and verify that Data Loss Prevention is displayed.Create a Security policy rule to drop the Quick UDP Internet Connection (QUIC) protocol.Many supported web applications, such as Gmail, require that you disable the QUIC protocol for Enterprise DLP to function correctly.
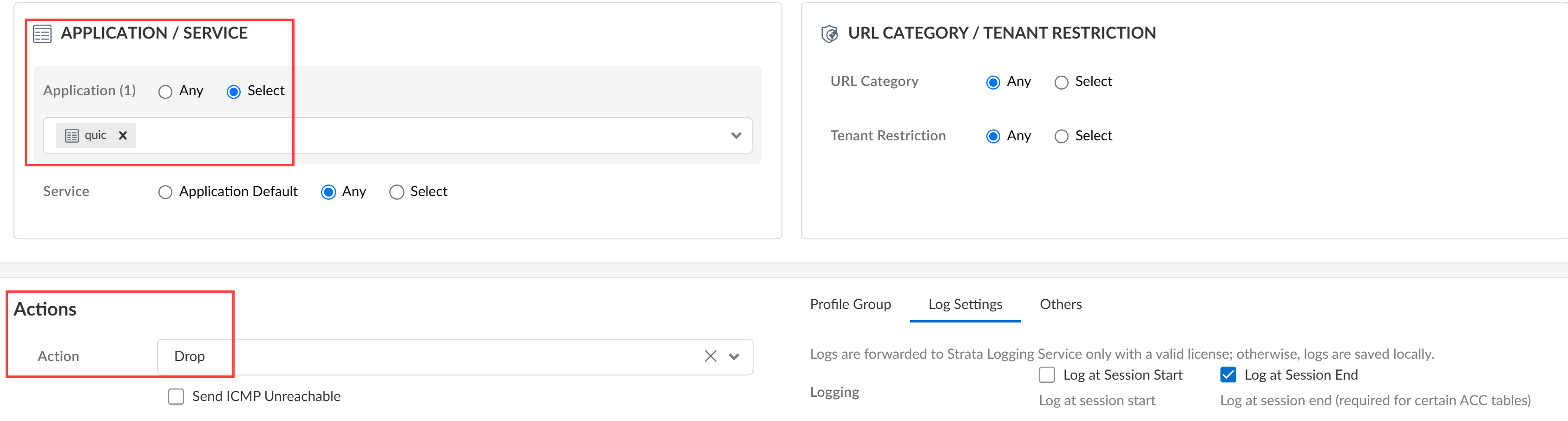
Select Configuration and verify that Data Loss Prevention is displayed.Create a Security policy rule to drop the Quick UDP Internet Connection (QUIC) protocol.Many supported web applications, such as Gmail, require that you disable the QUIC protocol for Enterprise DLP to function correctly.- Select ConfigurationNGFW and Prisma AccessSecurity ServicesSecurity Policy.Select the Configuration Scope where you want to create the Security policy rule.Select Add RulePre Rule Security Rule.This Security policy rule should precede all Security policy rules that forward traffic to Enterprise DLP.Enter a descriptive Name for the Security policy rule.Configure the Source and Destination match criteria as needed.Configure the Security policy rule to drop the QUIC protocol.
- In the Application/Service section, click Select for the Application field. Search for and select quic.
- In the Actions section, select Drop for the Action field.
- (Best Practices) Click Log Settings and configure logging for impacted traffic.
![]() Save the Security policy rule.Create the decryption profile required for Enterprise DLP to inspect traffic.
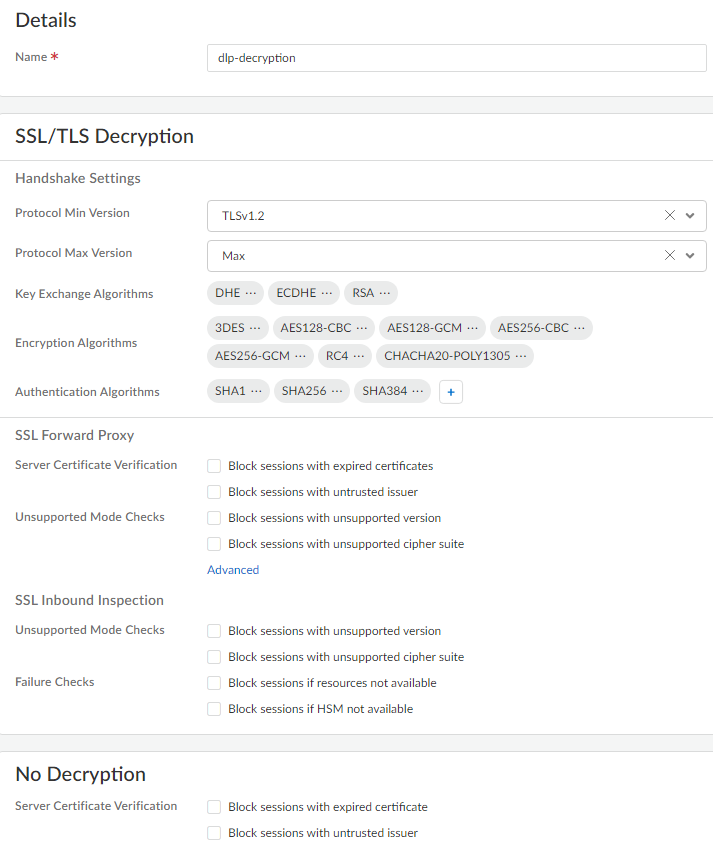
Save the Security policy rule.Create the decryption profile required for Enterprise DLP to inspect traffic.- Select ConfigurationNGFW and Prisma AccessSecurity ServicesDecryption and Add Profile.Enter a descriptive Name for the decryption profile.Review the predefined decryption profile settings.The predefined decryption profile settings enable Enterprise DLP to inspect traffic. Modifying the predefined decryption profile settings isn’t required unless you need to enable Strip ALPN.
![]() (Software Version 10.2.2 or earlier versions) Configure the decryption profile to remove Application-Layer Protocol Negotiation (ALPN) headers from uploaded files.Remove the ALPN headers from files if any Strata Cloud Manager deployment is running software version 10.2.2 or earlier version. If your entire Strata Cloud Manager deployment is running software version 10.2.3 or later version, stripping ALPN headers isn’t required.A Security admin can also strip ALPN headers in the Internet Security decryption settings. Security admins don’t need to create a decryption policy rule and can push the setting to Remote Networks and Mobile Users.
(Software Version 10.2.2 or earlier versions) Configure the decryption profile to remove Application-Layer Protocol Negotiation (ALPN) headers from uploaded files.Remove the ALPN headers from files if any Strata Cloud Manager deployment is running software version 10.2.2 or earlier version. If your entire Strata Cloud Manager deployment is running software version 10.2.3 or later version, stripping ALPN headers isn’t required.A Security admin can also strip ALPN headers in the Internet Security decryption settings. Security admins don’t need to create a decryption policy rule and can push the setting to Remote Networks and Mobile Users.- In the SSL Forward Proxy, click Advanced.
- Check (enable) Strip ALPN and Save.
![]()
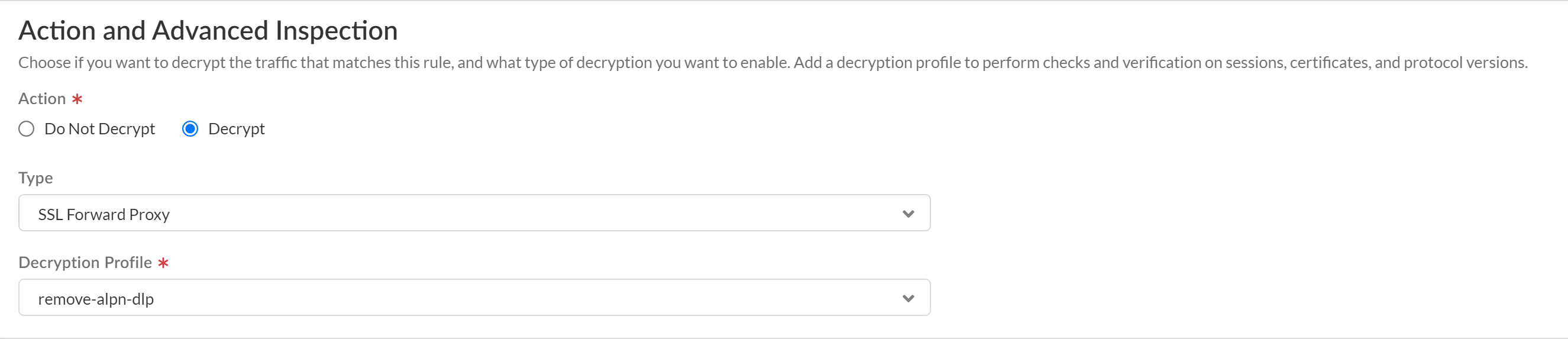
Save the decryption profile group.Create a decryption policy rule to decrypt traffic for Enterprise DLP inspection.Strata Cloud Manager includes the predefined Exclude Microsoft O365 Optimized Endpoints - IPs and Exclude Microsoft O365 Optimized Endpoints - URLs decryption rules that exclude Microsoft Office 365 from decryption.For Enterprise DLP to successfully inspect traffic for Microsoft Office 365, you must position this new decryption rule before the predefined decryption exclusion rules. Alternatively, you can Disable these rules or Delete them.- Select ConfigurationNGFW and Prisma AccessSecurity ServicesDecryption and Add Rule.Enter a descriptive Name and configure the decryption policy rule as needed.In the Action and Advanced Inspection section, configure the policy rule to Decrypt traffic that matches this rule.For the Type, select SSL Forward Proxy.Select the Decryption Profile you created to strip ALPN headers.
![]() Save the decryption policy rule.Create a decryption policy rule to exclude decrypting traffic for apps that use pinned certificates and mutual authentication.Decrypting app traffic when the app uses pinned certificates or mutual authentication causes user connectivity and app functionality issues. Create this decryption policy rule to exclude these apps from decryption.Order the decryption policy rule after the decryption policy rule to decrypt traffic for Enterprise DLP inspection. This ensures that app traffic that can be decrypted is decrypted before being forwarded to Enterprise DLP while excluding apps where decrypting its traffic causes access or usage issues.
Save the decryption policy rule.Create a decryption policy rule to exclude decrypting traffic for apps that use pinned certificates and mutual authentication.Decrypting app traffic when the app uses pinned certificates or mutual authentication causes user connectivity and app functionality issues. Create this decryption policy rule to exclude these apps from decryption.Order the decryption policy rule after the decryption policy rule to decrypt traffic for Enterprise DLP inspection. This ensures that app traffic that can be decrypted is decrypted before being forwarded to Enterprise DLP while excluding apps where decrypting its traffic causes access or usage issues.