Enterprise DLP
Explore the Enterprise DLP Incident Management Dashboard
Table of Contents
Expand All
|
Collapse All
Enterprise DLP Docs
Explore the Enterprise DLP Incident Management Dashboard
Explore and learn more about the Enterprise Data Loss Prevention (E-DLP) Incident Management
dashboard and the available filters and widgets.
On May 7, 2025, Palo Alto Networks is introducing new Evidence Storage and Syslog Forwarding service IP
addresses to improve performance and expand availability for these services
globally.
You must allow these new service IP addresses on your network
to avoid disruptions for these services. Review the Enterprise DLP
Release Notes for more
information.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
Or any of the following licenses that include the Enterprise DLP license
|
Explore the Enterprise Data Loss Prevention (E-DLP) Incident Management dashboard and learn more
about the available filters and widgets that allow your data security administrators to
aggregate and correlate data security incidents across your various enforcement channels
to efficiently apply a consistent security posture.
To navigate to the Incident Management dashboard, select ConfigurationData Loss PreventionDLP Incidents.
Incident Management Dashboard Filters
The Incident Management filters allow you to quickly filter the Incidents list
displayed in the dashboard. You can apply any combination of the following
filters.
- Time Filter—Filter for incidents generated in the Past 60 Minutes, Past 3 Hours, Past 24 Hours, Past 7 Days, Past 30 Days, or Past 90 Days. You can apply only one filter at a time.
- Action—Filter for incidents based on the enforcement action taken. You can select Alert, Block, or Quarantine. Additionally, you can select any combination of the available action filters.
- Application—The type of app that generated a DLP incident. You can select GenAI Apps or Other Apps (non-GenAI).
- Assets—Enter the name of the Asset that generated the DLP incident. For file-based traffic, this is the file name. For non-file, the asset name is http-post-put. You can add multiple asset names.You can use the Violations widget to quickly find a list of available asset names that you can filter. Enterprise DLP updates the Violations widget based on any other applied filters.
- Assignee—Filter based on one or more case management assignee.
- Channels—Filter for incidents based on the security enforcement channel where that generated the incident. Email DLP, Endpoint DLP, NGFW, Prisma Access, Prisma Browser, or SaaS API. Additionally, you can select any combination of the available channel filters.
- Data Profile—Filter for incidents that match an Enterprise DLP data profile. The Incident Management dashboard displays all available data profiles and you can select any combination.
- Detection Types—Select the Enterprise DLP data pattern or advanced detection method that traffic matched against which generated a DLP incident. The Incident Management filters displays all available data patterns and advanced detection method and you can select any combination. The Incidents list displays all data profiles with which the selected detection types.
- Incident ID—Filter the list of DLP incidents based on one or more Incident ID.
- Priorities—Filter based the case management priority. You can select any combination of P1, P2, P3, P4, and P5.
- Regions—Filter based on the region where the DLP incident was generated.
- Report ID—Filter the Report ID assigned to the DLP incident. You can enter multiple Report IDs.
- Severities—Filter for incidents based on the incident severity level. You can select Critical, High, Medium, Low, or Lowest. Additionally, you can select any combination of the available severity filters.
- Source—Filter based on the User ID of the user that generated the DLP incident. You can enter multiple User IDs.You can also use the Violations widget to quickly find a list of available URL ID traffic source that you can filter. Enterprise DLP updates the Violations widget based on any other applied filters.
- Status—Filter incidents based on their current case management status. You can select any combination of Closed, New, Open, and Under Investigation.
- Tags—Filter incidents based on the assigned case management tag.
- URL Domain—Filter based on the URL domain of the Session URL in the DLP incident details. You can added multiple URL domains.You can also use the Violations widget to quickly find a list of available URL domains that you can filter. Enterprise DLP updates the Violations widget based on any other applied filters.
Incident Management Dashboard Search
Use the Incident Management search to find incident information specific to a single
Asset, URL Domain,
Report ID, or Source. The search
filter applies to all dashboard widgets as well as the Incidents list. You can apply
any of the dashboards filters after you search for a specific asset, URL domain,
report ID, or source to further investigate a specific incident.
Incident Management Dashboard Widgets
The Incident Management dashboard widgets enable your data security administrators to
view summary information for all your data security incidents across all your
security channels.
- Incident Summary WidgetShows a summary of all your data security incidents. You can filter
- Severity—All incidents based on the incident severity (Critical, High, Medium, Low, or Lowest).
- Priority— All incidents based on the priority assigned during incident case management (P1, P2, P3, P4, P5.
- Action—All incidents based on the action the security enforcement took (Alert, Block, or Quarantine).
- Location—All regions where users generated incidents.
- Channel—All security enforcement points that generated incidents.
- Top Incident WidgetShows the top five incidents Alerted or Blocked by Enterprise DLP. You can filter the top incidents based on the following: the Data Profiles containing the data pattern match criteria or
- Data Profiles—Shows the top 5 predefined and custom data profiles that contained sensitive data match criteria that generated an incident.
- Data Patterns—Shows the top 5 predefined or custom data patterns that sensitive data matched against that generated an incident.
- Violations WidgetShows the top five violations. Additionally, the Incident Management dashboard includes a timestamp in Month, Day, HH:MM <AM or PM> <timezone> format describing the last time a user generated an incident.
- Source—Name of the user who generated.
- Asset—Name of the asset that contained sensitive data that generated an incident.
- URL Domain—URL domain name that a user uploaded sensitive data to or downloaded sensitive data from that generated an incident.
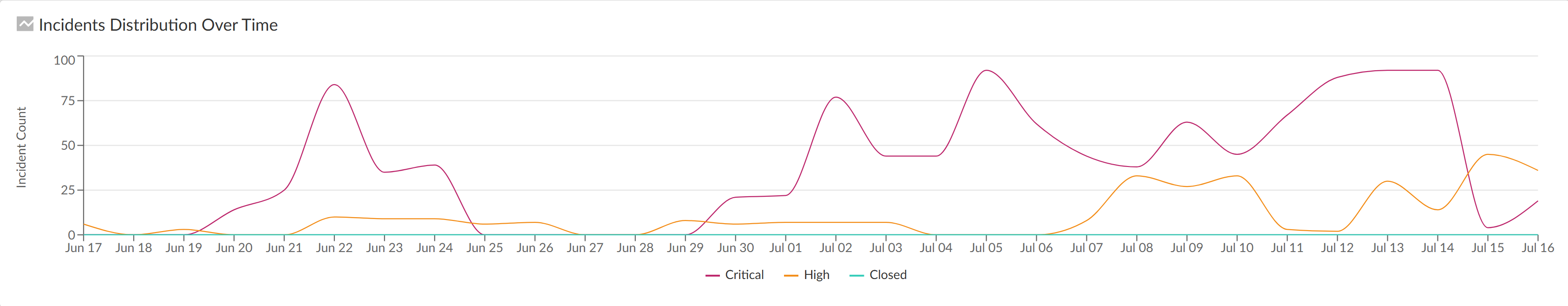
Incidents Distribution Over Time Graph
The Incidents Distribution Over Time line graph helps your security administrators by
creating a visual representation of Enterprise DLP incidents across all your
enforcement channels. This graph helps your data security administrators correlate
configuration changes and network activity with corresponding DLP incidents. This
helps data security administrators observe data security trends and helps them make
decisions to strengthen your organization's security posture and prevent
exfiltration of sensitive data. Enterprise DLP updates the graph based on the
Incident Management Dashboard Filters
you configure.
Incidents List
The Incidents list provides acts as a centralized repository for tracking and
managing all incidents that match the Incident Management filters you apply. It
plays a crucial role for maintaining an organized and effective approach to managing
your data security incidents.
For each incident, the DLP incidents list provides crucial information such as the
date and time the incident occurred, the Incident ID, the data profile containing
the sensitive match criteria, the asset name, the region where the incident
occurred, the user who generated the incident, the severity of the data security
incident, the security enforcement channel where the incident was generated, and
more. Additionally, you can configure the Incident list settings to hide or display
incident information as needed.
The Incident list updates in real time when new users generate new incidents to
ensure real-time visibility into incident management. Furthermore, all incidents
persist even after a data security administrator resolves the incident to maintain
an accurate historical record. This supports your data security administrators in
conducting postincident analysis and lessons learned activities.
Data security administrators can download (
![]() ) the full list of DLP incidents to their local device
in .csv format based on the currently applied filters.
This enables your data security administrators to create workflows based on the
types of DLP incidents that matter most to your organization.
) the full list of DLP incidents to their local device
in .csv format based on the currently applied filters.
This enables your data security administrators to create workflows based on the
types of DLP incidents that matter most to your organization.

Click the Incident ID to view incident details and snippets of matched
traffic, as well as to perform Incident Case Management.
