GlobalProtect
Use Connect Before Logon
Table of Contents
Use Connect Before Logon
To use Connect Before Logon, choose the authentication method.
The Pre-logon and Pre-logon then On-demand
connection methods are not supported simultaneously with Connect Before
Logon.
Connect Before Logon is not supported for internal
gateway configurations.
To simplify the login process
and improve your experience, GlobalProtect offers Connect Before
Logon to allow you to establish the VPN connection to the corporate network
before logging in to the Windows 10 endpoint using a Smart card,
authentication service such as LDAP, RADIUS, or Security Assertion
Markup Language (SAML), username/password-based authentication,
or one-time password (OTP) authentication. Administrators can benefit
from enabling Connect Before Logon when they onboard new GlobalProtect
users on the endpoint that is not set up with a local profile or
account for the user. Connect Before Logon is disabled by default. When
the administrator enables Connect Before Logon, you can launch the
GlobalProtect app credential provider and connect to the corporate
network before logging in to Windows endpoint. After Connect Before
Logon establishes a VPN connection, you can use the Windows logon
screen to log in to the Windows endpoint. GlobalProtect can act
as a Pre-Login Access Provider (PLAP) credential provider to provide access
to your organization before logging in to Windows.
Because
Connect Before Logon prompts you to authenticate twice on the portal
and gateway when logging in to the Windows endpoint for the first
time, the Authentication Override cookie is not working as expected.
To use Connect Before Logon, the administrator must deploy the settings in the Windows
registry and you choose the authentication method:
Connect Before Logon Using Smart Card Authentication
Connect Before Logon supports smart card authentication. The
administrator must import the Root CA certificate that issued the
certificates contained on the smart card onto the portal and gateway.
The administrator can apply the certificate profile and that Root
CA to your portal or gateway configuration to enable use of the
smart card in the authentication process. You can authenticate to
GlobalProtect prior to logging into the Windows endpoint using a
smart card. When prompted, insert your smart card to verify that
smart card authentication is successful. If smart card authentication
is successful, GlobalProtect will connect to the portal or gateway
specified in the configuration.
- Before you can use Connect Before Logon, the administrator
must have completed the following tasks:
- Deploy Connect Before Logon Settings in the Windows Registry.
- Set up the smart card for two-factor authentication.
- Assign the certificate profile to the GlobalProtect portal.
- Configure the gateway to authenticate end users based on a smart card.
- Log in to the Windows endpoint using Connect Before Logon.
- Click the Network Sign-In () button at the lower right corner of the Windows logon screen.If the VPN connection is successful, the Disconnect () button appears next to the Network Sign-In button of the Windows logon screen. You are logged out of the VPN if you have not yet logged in to your endpoint within the configured time period. This causes the VPN tunnel to disconnect.
- (Optional) If you are logging in to the endpoint
for the first time and the portals have not been predefined by the
administrator, enter the FQDN or IP address of the GlobalProtect
portal, and Submit.
![]()
- (Optional) If you are logging in to the endpoint
for the first time and the portals have been predefined by the administrator,
select a portal from the Portal drop-down,
and click the arrow to submit.
![]()
- Select the client certificate from a list of valid
certificates on the endpoint to authenticate with the portal or
gateway, and click the arrow to submit.
![]()
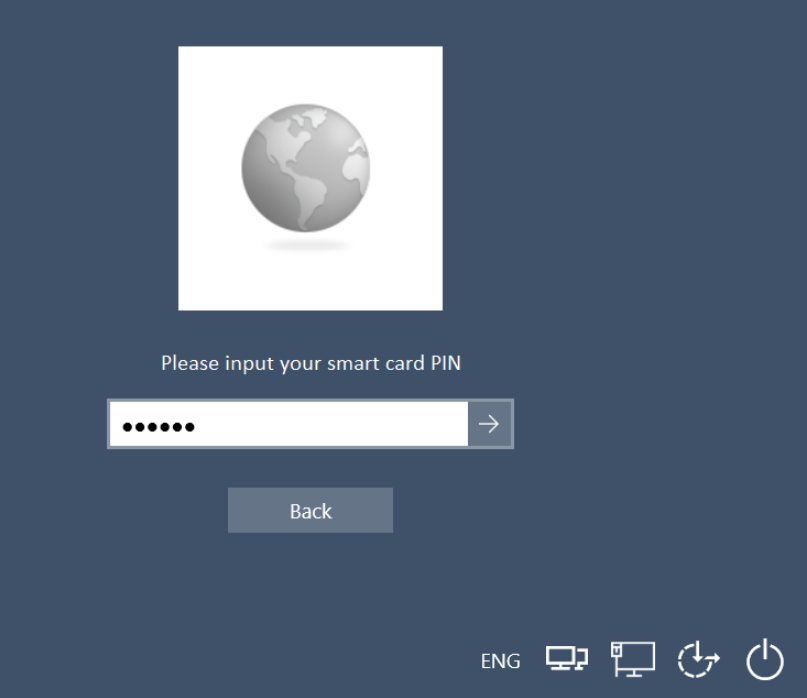
- Enter the Personal Identification Number (PIN) of
the smart card, and click the arrow to submit.
![]()
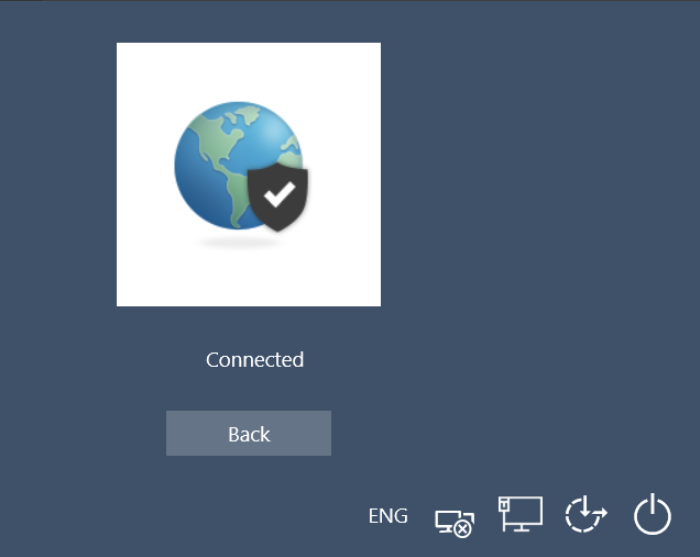
- If authentication is successful, the connection status
displays Connected upon successful VPN connection.
Click Back to display the Windows logon screen.
![]()
- Click the Network Sign-In (
- Verify that you are connected to the GlobalProtect gateway.
- Log in to the Windows endpoint again. Click
the Network Sign-In () button at the lower right corner of the Windows logon screen.
- The status panel opens. By default, you are automatically connected to the Best Available gateway.
- Log in to the Windows endpoint again. Click
the Network Sign-In (
Connect Before Logon Using SAML Authentication
Connect Before Logon supports SAML authentication
for user login. You can authenticate to GlobalProtect prior to logging
into the Windows endpoint using the configured SAML identity providers
(ldPs) such as Onelogin or Okta. If SAML authentication is successful,
GlobalProtect will connect to the portal or gateway specified in
the configuration.
- Before you can use Connect Before Logon, the administrator
must have completed the following tasks:
- Deploy Connect Before Logon Settings in the Windows registry.
- Set up SAML authentication to
authenticate end users.
- Create a server profile with settings to the SAML authentication service.
- Create an authentication profile that refers to the SAML server profile.
- Specify SAML authentication for the GlobalProtect gateway.
- Specify a SAML authentication for the client (see Define the GlobalProtect Client Authentication Configurations).
- Log in to the Windows endpoint using Connect Before Logon.
- Click the Network Sign-In () button at the lower right corner of the Windows logon screen.If the VPN connection is successful, the Disconnect () button appears next to the Network Sign-In button of the Windows logon screen. You are logged out of the VPN if you have not yet logged in to your endpoint within the configured time period. This causes the VPN tunnel to disconnect.
- (Optional) If you are logging in to the endpoint
for the first time and the portals have not been predefined by the
administrator, enter the FQDN or IP address of the GlobalProtect
portal, and click the arrow to submit.
![]()
- (Optional) If you are logging in to the endpoint
for the first time and the portals have been predefined by the administrator,
select a portal from the Portal drop-down,
and click the arrow to submit.
![]()
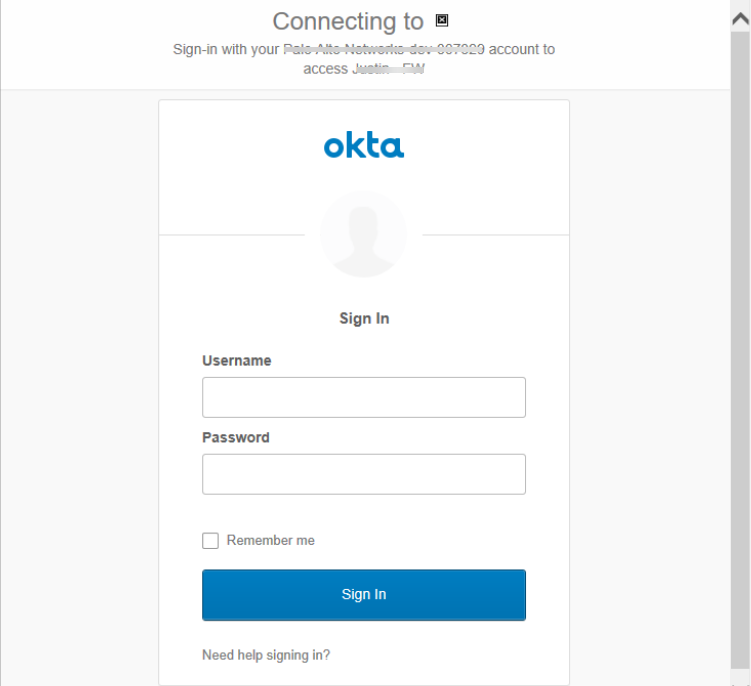
- Enter the username and password to authenticate to
the ldP, and then click Sign In.
![]()
- If authentication is successful, the connection status
displays Connected upon successful VPN connection.
Click Back to display the Windows logon screen.
![]()
- Click the Network Sign-In (
- Verify that you are connected to the GlobalProtect gateway.
- Log in to the Windows endpoint again. Click
the Network Sign-In () button at the lower right corner of the Windows logon screen.
- The status panel opens. By default, you are automatically connected to the Best Available gateway.
- Log in to the Windows endpoint again. Click
the Network Sign-In (
Connect Before Logon Using Username/Password-Based Authentication
Connect Before Logon supports username/password-based
authentication for user login using an authentication service such
as LDAP, RADIUS, or OTP. You can authenticate to GlobalProtect prior
to logging into the Windows endpoint using the username and password
credentials. If username/password-based authentication is successful,
GlobalProtect will connect to the portal or gateway specified in
the configuration.
- Before you can use Connect Before Logon, the administrator
must have completed the following tasks:
- Deploy Connect Before Logon Settings in the Windows registry.
- Set up access to the GlobalProtect portal to authenticate end users to the portal using their credentials.
- Configure a GlobalProtect gateway to authenticate end users to the gateway using their credentials.
Connect Before Logon does not support a custom authentication message. - Log in to the Windows endpoint using Connect Before Logon.
- Click the Network Sign-In () button at the lower right corner of the Windows logon screen.If the VPN connection is successful, the Disconnect () button appears next to the Network Sign-In button of the Windows logon screen. You are logged out of the VPN if you have not yet logged in to your endpoint within the configured time period. This causes the VPN tunnel to disconnect.
- (Optional) If you are logging in to the endpoint
for the first time and the portals have not been predefined by the
administrator, enter the FQDN or IP address of the GlobalProtect
portal, and click the arrow to submit.
![]()
- (Optional) If you are logging in to the endpoint
for the first time and the portals have been predefined by the administrator,
select a portal from the Portal drop-down,
and click the arrow to submit.
![]()
- Enter the username and password, and click the arrow
to submit.
![]()
- If authentication is successful, the connection status
displays Connected upon successful VPN connection.
Click Back to display the Windows logon screen.
![]()
- Click the Network Sign-In (
- Verify that you are connected to the GlobalProtect gateway.
- Log in to the Windows endpoint again. Click
the Network Sign-In () button at the lower right corner of the Windows logon screen.
- The status panel opens. By default, you are automatically connected to the Best Available gateway.
- Log in to the Windows endpoint again. Click
the Network Sign-In (