Network Security
Test Security Rules
Table of Contents
Expand All
|
Collapse All
Network Security Docs
Test Security Rules
Test the traffic policy matches of your configuration.
Testing security rules helps ensure that the network's
security posture is robust and effective against potential threats. Security rules define how traffic is handled and controlled within the network. Testing these
rules ensures that your security rules appropriately allow and deny traffic and access
to applications and websites in compliance with your business needs and
requirements.
We provide tools that let you simulate traffic flow based on a specific set
of conditions defined in a security rule. By entering the necessary parameters such as
source and destination IP addresses, ports, and applications, you can simulate the
traffic flow and observe how your configuration would process it based on the
configured security rules. This provides valuable insights into the effectiveness of
the Security policy, which lets you verify if the security actions you intend, such
as allowing or denying traffic, are correctly applied as per the security rules. You
can also identify any misconfigurations or conflicts that might affect the policy's
behavior.
Regularly testing security rules is essential for maintaining an
efficient security posture. It enables you to adapt security rules to changing network
requirements and evolving threat landscapes. By conducting thorough tests and
fine-tuning security rules accordingly, you can ensure that your configuration
operates optimally, providing reliable protection against a variety of cyberthreats.
Test Security Rules (Strata Cloud Manager)
Test the traffic policy matches of your configuration.
Updates to your Security rules are often time-sensitive and
require you to act quickly. However, you want to ensure that any update you make to
your Security policy rulebase meets your requirements and does not introduce errors
or misconfigurations (such as changes that result in duplicate or conflicting
rules).
Policy Analyzer in
Strata Cloud Manager enables you to optimize time and resources when
implementing a change request. Policy Analyzer not only analyzes and provides
suggestions for possible consolidation or removal of specific rules to meet your
intent but also checks for anomalies, such as Shadows, Redundancies,
Generalizations, Correlations and Consolidations in your rulebase.
Use Policy Analyzer to analyze your Security rules both before and after you commit your changes.
- Pre-Change Policy Analysis—Enables you to evaluate the impact of a new rule so you can compare that to your intent for that rule and ensure that it does not duplicate or conflict with existing rules before you commit to avoid security rule inflation. You can also run a Security Policy Anomaly Analysis to check for shadows, redundancies, generalizations, correlations and consolidations.
- Post-Change Policy Analysis—Enables you to clean the existing rulebase by identifying shadows, redundancies, and other anomalies that have accumulated over time.
You can also use Policy Analyzer to add or optimize your Security policy rulebase.
- Before adding a new rule—Check to see if new rules need to be added. Policy Analyzer recommends how best to change your existing Security policy rules to meet your requirements without adding another rule, if possible.
- Streamline and optimize your existing rulebase—See where you can update your rules to minimize bloat and eliminate conflicts and also to ensure that traffic enforcement aligns with the intent of your Security policy rulebase.
Test Security Rules (PAN-OS & Panorama)
Test the traffic policy matches of the running firewall configuration.
Panorama customers with the Cloud Connector Plugin can use Policy Analyzer to analyze Security rules both before and after committing changes to their configuration.
Policy Analyzer not only analyzes and provides suggestions for possible consolidation
or removal of specific rules to meet your intent but also checks for anomalies, such
as Shadows, Redundancies, Generalizations, Correlations and Consolidations in your
rulebase.
- Policy Analyzer requires the Cloud Connector Plugin 1.1.0 on your Panorama appliance.
- Policy Analyzer requires Panorama to be updated to PAN-OS version 10.2.3 or a later version.
Both Panorama and PAN-OS customers can test and verify that security rules are allowing
and denying the correct traffic by executing policy match tests for firewalls
directly from the web interface.
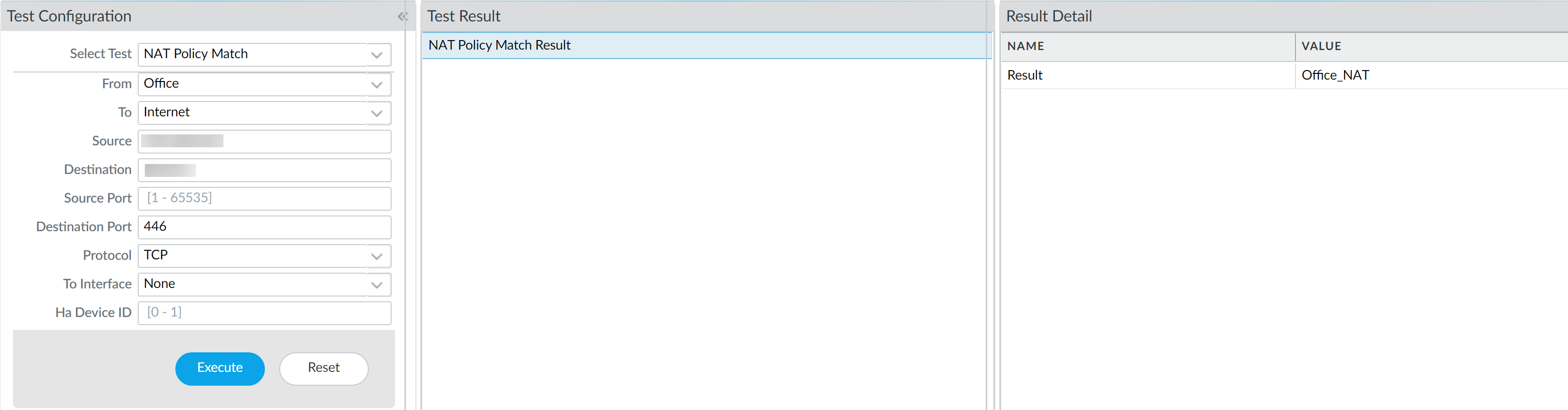
- Launch the firewall web interface.Select DeviceTroubleshooting to perform a policy match or connectivity test.Enter the required information to perform the policy match test. In this example, we run a NAT policy match test.
- Select Test—Select NAT Policy Match.From—Select the zone traffic is originating from.To—Select the target zone of the traffic.Source—Enter the IP address from which traffic originated.Destination—Enter the IP address of the target device for the traffic.Destination Port—Enter the port used for the traffic. This port varies depending on the IP protocol used in the following step.Protocol—Enter the IP protocol used for the traffic.If necessary, enter any additional information relevant for your NAT security rule testing.Execute the NAT policy match test.Review the NAT Policy Match Result to see the policy rules that match the test criteria.
![]()