Network Security
Test Security Rules (PAN-OS & Panorama)
Table of Contents
Expand All
|
Collapse All
Network Security Docs
Test Security Rules (PAN-OS & Panorama)
Test the traffic policy matches of the running firewall configuration.
Panorama customers with the Cloud Connector Plugin can use Policy Analyzer to analyze Security rules both before and after committing changes to their configuration.
Policy Analyzer not only analyzes and provides suggestions for possible consolidation
or removal of specific rules to meet your intent but also checks for anomalies, such
as Shadows, Redundancies, Generalizations, Correlations and Consolidations in your
rulebase.
- Policy Analyzer requires the Cloud Connector Plugin 1.1.0 on your Panorama appliance.
- Policy Analyzer requires Panorama to be updated to PAN-OS version 10.2.3 or a later version.
Both Panorama and PAN-OS customers can test and verify that security rules are allowing
and denying the correct traffic by executing policy match tests for firewalls
directly from the web interface.
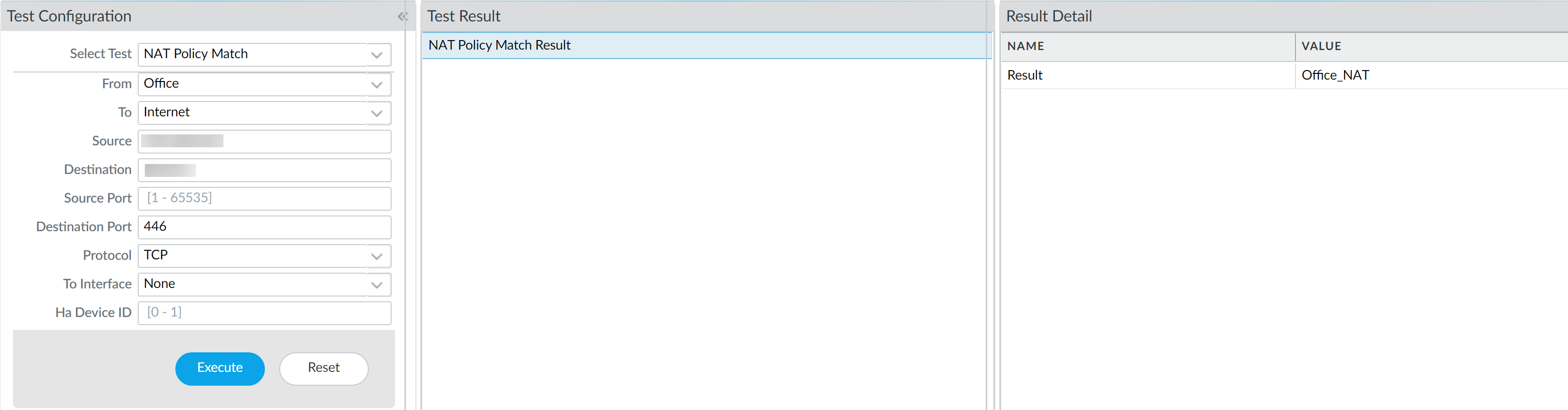
- Launch the firewall web interface.Select DeviceTroubleshooting to perform a policy match or connectivity test.Enter the required information to perform the policy match test. In this example, we run a NAT policy match test.
- Select Test—Select NAT Policy Match.From—Select the zone traffic is originating from.To—Select the target zone of the traffic.Source—Enter the IP address from which traffic originated.Destination—Enter the IP address of the target device for the traffic.Destination Port—Enter the port used for the traffic. This port varies depending on the IP protocol used in the following step.Protocol—Enter the IP protocol used for the traffic.If necessary, enter any additional information relevant for your NAT security rule testing.Execute the NAT policy match test.Review the NAT Policy Match Result to see the policy rules that match the test criteria.
![]()