Network Security
View External Dynamic List Entries
Table of Contents
Expand All
|
Collapse All
Network Security Docs
View External Dynamic List Entries
View the contents of an external dynamic list to check if it contains certain IP
addresses, domains, or URLs.
It's a good idea to look at your external dynamic list (EDL) entries to
assess the information present in these lists. Viewing external dynamic list entries
gives you insights into the threat intelligence being used for Security policy
enforcement, and helps you maintain an up to date and robust security posture.
To access and view entries within an external dynamic list, navigate to the
Objects tab and select External Dynamic
Lists. Here, you can see a list of all configured external dynamic
lists. Select a specific external dynamic list to view the entries it contains.
External dynamic list entries typically comprise IP addresses, URLs, domain
names, or other indicators of compromise, depending on the type of external dynamic
list configured. Your configuration periodically fetches updates from the specified
URL associated with the external dynamic list, ensuring that the entries remain
current and reflect the latest threat intelligence.
To delve deeper into the entries within an external dynamic list, you can
review the contents directly from the external dynamic list configuration. This
might involve inspecting the external dynamic list's source file, which you can
access by clicking on the URL associated with the external dynamic list. The
contents of the external dynamic list source file provide a comprehensive view of
the listed indicators and their details.
Regular monitoring of these entries is vital to ensure the effectiveness of
your configuration's threat prevention capabilities. Review the entries
periodically, cross-reference them with known threat databases, and validate their
relevance to your organization's security posture.
Before you Enforce Policy on an External
Dynamic List, view the contents of an external dynamic list to check if
it contains certain IP addresses, domains, or URLs. The entries displayed are based
on the version of the external dynamic list that was most recently retrieved.
Follow these steps to view the contents of an external dynamic list to check if it
contains certain IP addresses, domains, or URLs.
View External Dynamic List Entries (Strata Cloud Manager)
View the contents of an external dynamic list to check if it contains certain IP
addresses, domains, or URLs.
- Select ConfigurationNGFW and Prisma AccessObjectsExternal Dynamic Lists.Select the external dynamic list you want to view.Check the List Entries and Exceptions and view the objects that were retrieved from the list.
![]() The list might be empty if:
The list might be empty if:- The EDL has not yet been applied to a Security rule. To apply an EDL to a Security rule and populate the EDL, see Enforce Policy on an External Dynamic List.
- The external dynamic list has not yet been retrieved. To force the retrieval of an external dynamic list immediately, Retrieve an External Dynamic List from the Web Server.
Enter an IP address, domain, or URL (depending on the type of list) in the search field to check if it’s in the list. Exclude entries from an external dynamic list based on which IP addresses, domains, and URLs you need to block or allow.Exclude Entries from an External Dynamic List
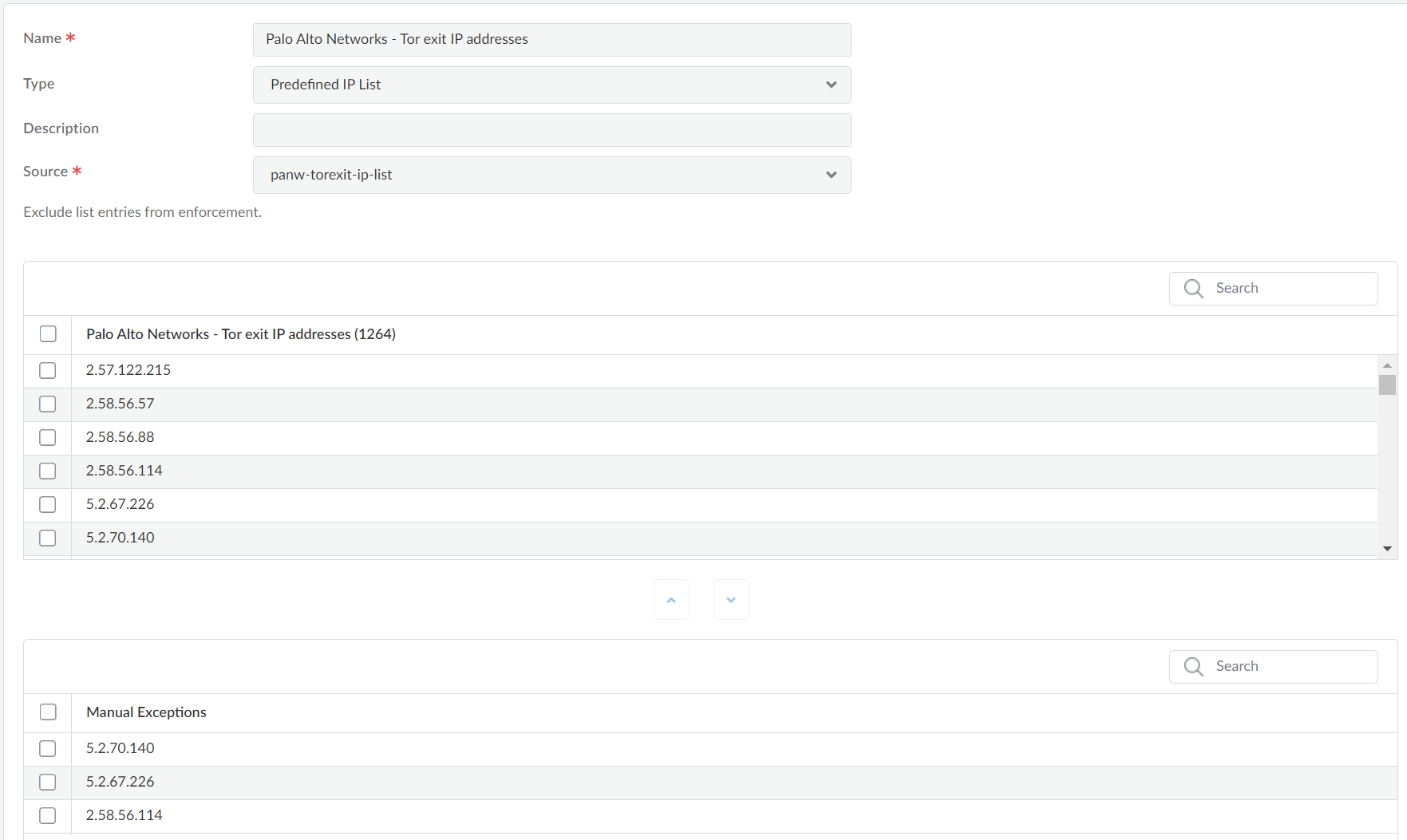
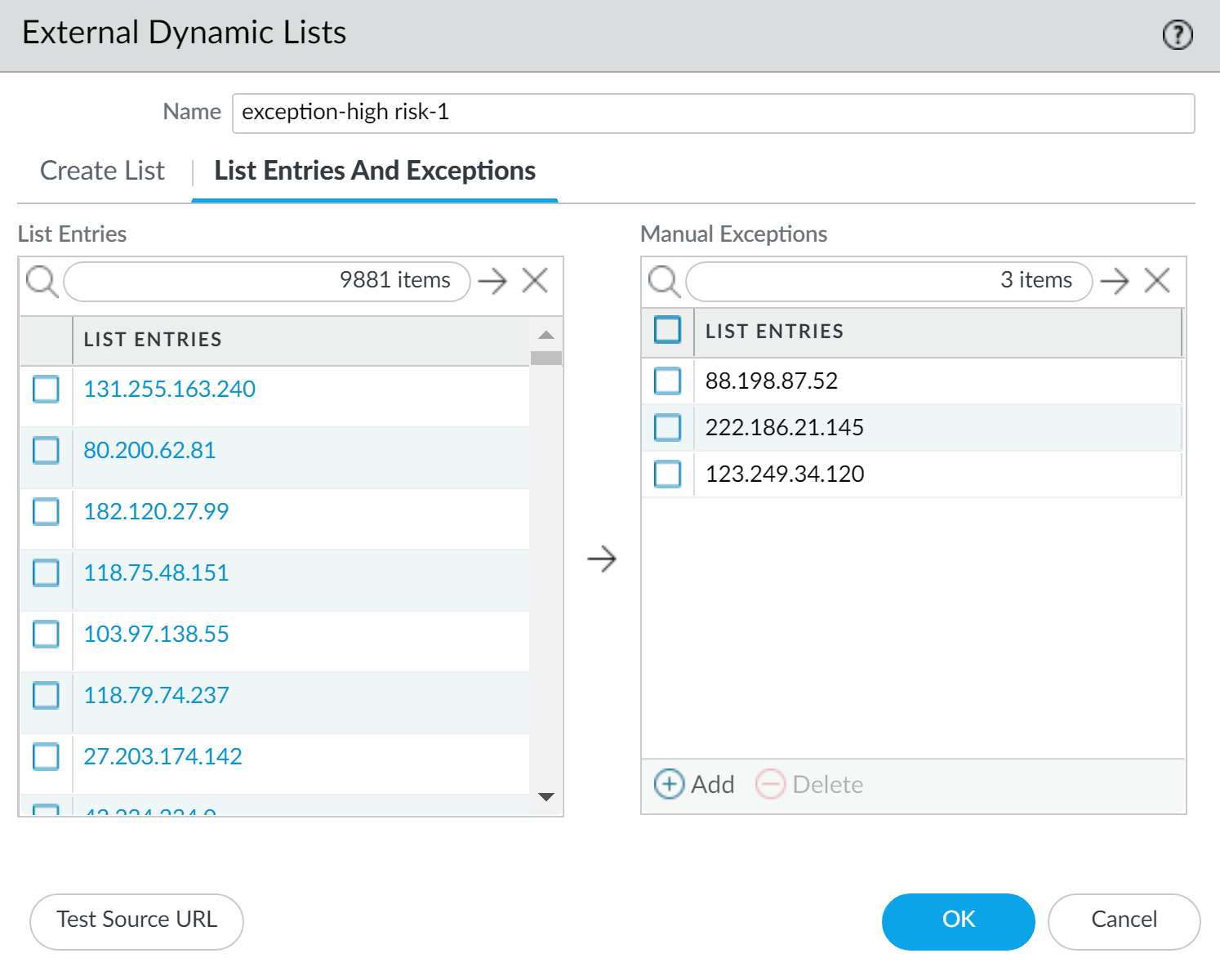
As you view the entries of an external dynamic list, you can exclude up to 100 entries from the list. The ability to exclude entries from an external dynamic list gives you the option to enforce policy on some (but not all) of the entries in a list. This is helpful if you cannot edit the contents of an external dynamic list (such as the Palo Alto Networks High-Risk IP Addresses feed) because it comes from a third-party source.Follow these steps to exclude entries from an external dynamic list to enforce policy on some (but not all) of the entries in a list.- View External Dynamic List Entries.Select up to 100 entries to manually exclude from the list or manually add a list exception.
- You cannot save your changes to the external dynamic list if you have duplicate entries in the Manual Exceptions list. To identify duplicate entries, look for entries with a red underline.
- A manual exception must match a list entry exactly. Additionally, you cannot exclude a specific IP address from within an IP address range. To exclude a specific IP address from an IP address range, you must add each IP address in the range as a list entry and then exclude the desired IP address.Exclusion of an individual IP address from an IP address range is not supported.
Save your changes.(Optional) Enforce Policy on an External Dynamic List.
View External Dynamic List Entries (PAN-OS & Panorama)
View the contents of an external dynamic list directly on the firewall to check if it contains certain IP addresses, domains, or URLs.- Select ObjectsExternal Dynamic Lists.Click the external dynamic list you want to view.Click List Entries and Exceptions and view the objects that the firewall retrieved from the list.
![]() The list might be empty if:
The list might be empty if:- The EDL has not yet been applied to a Security rule. To apply an EDL to a Security rule and populate the EDL, see Enforce Policy on an External Dynamic List.
- The firewall has not yet retrieved the external dynamic list. To force the firewall to retrieve an external dynamic list immediately, Retrieve an External Dynamic List from the Web Server.
- The firewall is unable to access the server that hosts the external dynamic list. Click Test Source URL to verify that the firewall can connect to the server.
Enter an IP address, domain, or URL (depending on the type of list) in the filter field and Apply Filter () to check if it’s in the list. Exclude entries from an external dynamic list based on which IP addresses, domains, and URLs you need to block or allow.![]()
Exclude Entries from an External Dynamic List
As you view the entries of an external dynamic list, you can exclude up to 100 entries from the list. The ability to exclude entries from an external dynamic list gives you the option to enforce policy on some (but not all) of the entries in a list. This is helpful if you cannot edit the contents of an external dynamic list (such as the Palo Alto Networks High-Risk IP Addresses feed) because it comes from a third-party source.Follow these steps to exclude entries from an external dynamic list to enforce policy on some (but not all) of the entries in a list.- View External Dynamic List Entries.Select up to 100 entries to manually exclude from the list or manually add a list exception.
- You cannot save your changes to the external dynamic list if you have duplicate entries in the Manual Exceptions list. To identify duplicate entries, look for entries with a red underline.
- A manual exception must match a list entry exactly. Additionally, you cannot exclude a specific IP address from within an IP address range. To exclude a specific IP address from an IP address range, you must add each IP address in the range as a list entry and then exclude the desired IP address.Exclusion of an individual IP address from an IP address range is not supported.
Save your changes.(Optional) Enforce Policy on an External Dynamic List.