Network Security
View External Dynamic List Entries (Strata Cloud Manager)
Table of Contents
Expand All
|
Collapse All
Network Security Docs
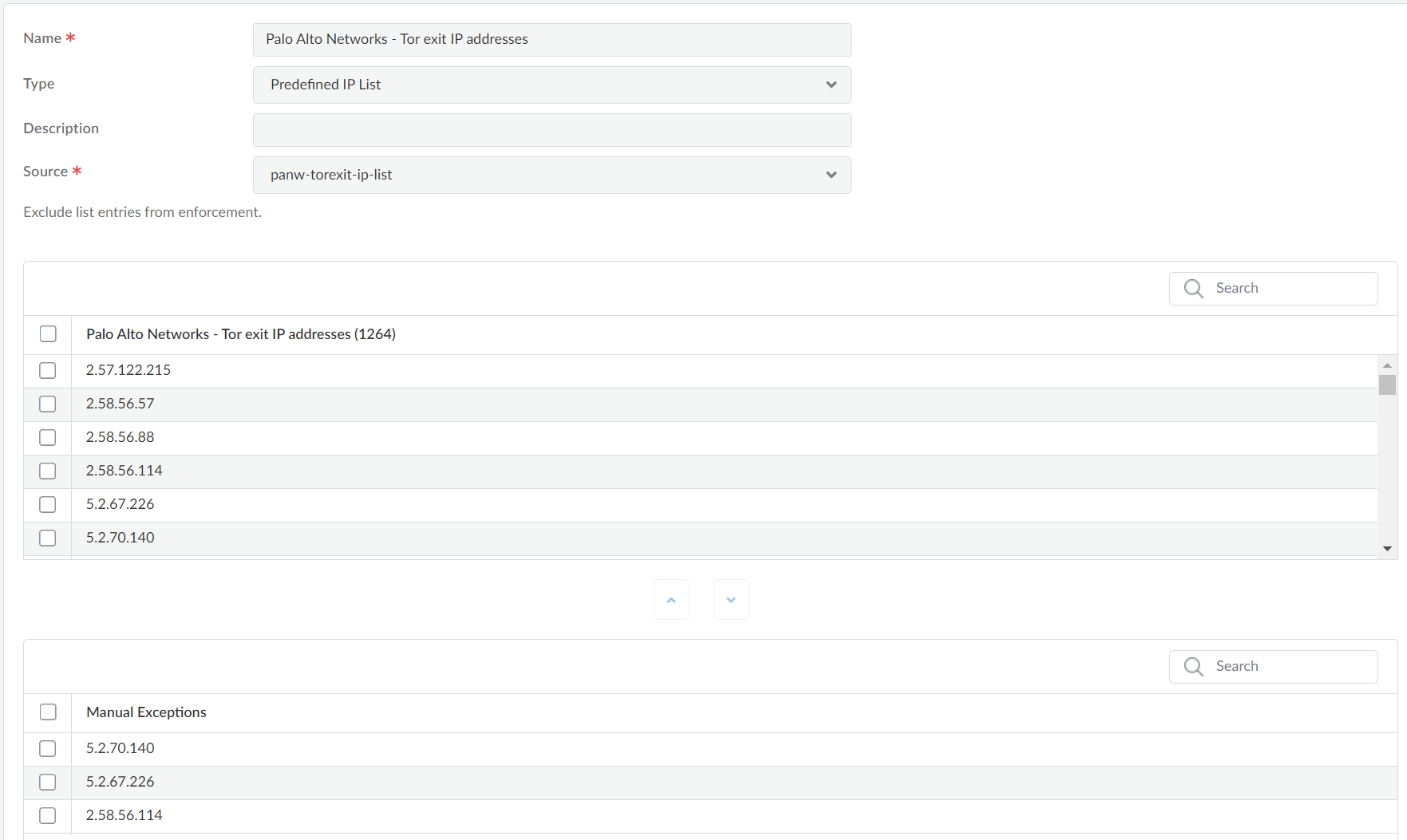
View External Dynamic List Entries (Strata Cloud Manager)
View the contents of an external dynamic list to check if it contains certain IP
addresses, domains, or URLs.
- Select ConfigurationNGFW and Prisma AccessObjectsExternal Dynamic Lists.Select the external dynamic list you want to view.Check the List Entries and Exceptions and view the objects that were retrieved from the list.
![]() The list might be empty if:
The list might be empty if:- The EDL has not yet been applied to a Security rule. To apply an EDL to a Security rule and populate the EDL, see Enforce Policy on an External Dynamic List.
- The external dynamic list has not yet been retrieved. To force the retrieval of an external dynamic list immediately, Retrieve an External Dynamic List from the Web Server.
Enter an IP address, domain, or URL (depending on the type of list) in the search field to check if it’s in the list. Exclude entries from an external dynamic list based on which IP addresses, domains, and URLs you need to block or allow.Exclude Entries from an External Dynamic List
As you view the entries of an external dynamic list, you can exclude up to 100 entries from the list. The ability to exclude entries from an external dynamic list gives you the option to enforce policy on some (but not all) of the entries in a list. This is helpful if you cannot edit the contents of an external dynamic list (such as the Palo Alto Networks High-Risk IP Addresses feed) because it comes from a third-party source.Follow these steps to exclude entries from an external dynamic list to enforce policy on some (but not all) of the entries in a list.- View External Dynamic List Entries.Select up to 100 entries to manually exclude from the list or manually add a list exception.
- You cannot save your changes to the external dynamic list if you have duplicate entries in the Manual Exceptions list. To identify duplicate entries, look for entries with a red underline.
- A manual exception must match a list entry exactly. Additionally, you cannot exclude a specific IP address from within an IP address range. To exclude a specific IP address from an IP address range, you must add each IP address in the range as a list entry and then exclude the desired IP address.Exclusion of an individual IP address from an IP address range is not supported.
Save your changes.(Optional) Enforce Policy on an External Dynamic List.