Network Security
Identify Untrusted CA Certificates
Table of Contents
Expand All
|
Collapse All
Network Security Docs
Identify Untrusted CA Certificates
Find sites that have untrusted CA certificates so you can make informed decisions
about allowed traffic.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
No separate license required for decryption when using NGFWs or
Prisma Access.
Note: The features and capabilities available to you in
Strata Cloud Manager depend on your active license(s).
|
Blocking access to sites with untrusted CA certificates and certificates
self-signed by an untrusted root CA is a best practice because sites with untrusted
CAs may indicate a man-in-the-middle attack, a replay attack, or other malicious
activity.
Identify Untrusted CA Certificates (Strata Cloud Manager)
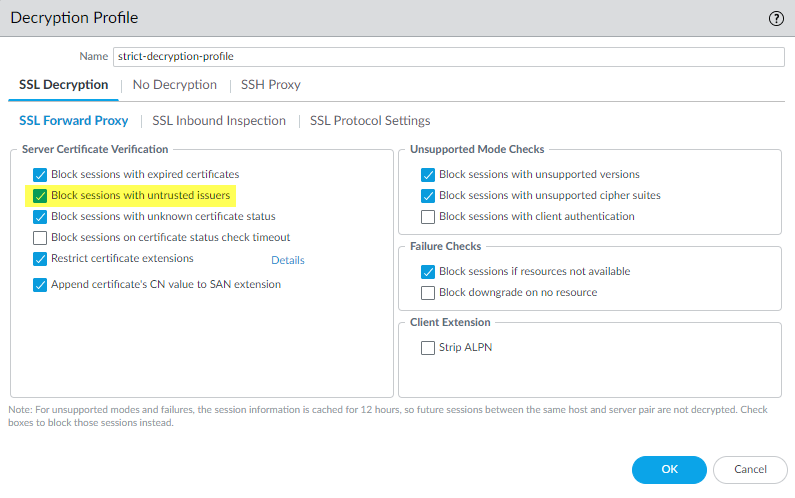
- Block sessions with untrusted issuers in the decryption profile for SSL Forward Proxy.When you block sessions with untrusted issuers in the decryption profile, the decryption log records the error.
- Select ConfigurationNGFW and Prisma Access Security ServicesDecryption.
- Under Decryption Profiles, select or Add a new profile, and then select the Block sessions with untrusted issuers option.
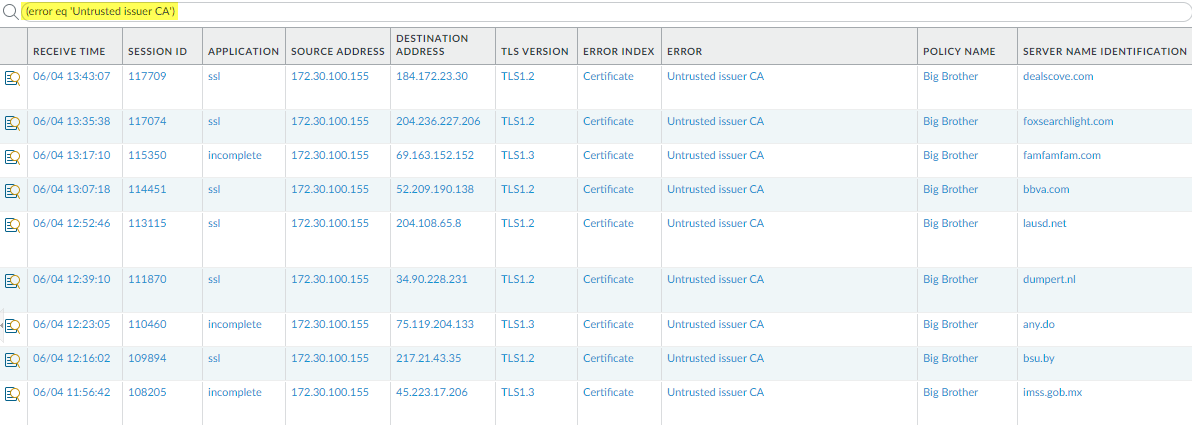
Filter decryption logs to identify sessions that failed due to revoked certificates.- Select Log ViewerFirewall/Decryption.
- Use the query Error Message = ‘Untrusted issuer CA’.
(Optional) Double-check the certificate expiration date at the Qualys SSL Labs site.Enter the hostname of the server (Server Name Identification column of the decryption log) in the Hostname field, and then Submit it to view certificate information for the host.
Identify Untrusted CA Certificates (PAN-OS)
- Block sessions with untrusted issuers in the Forward Proxy Decryption profile.When you block sessions with untrusted issuers in the Decryption profile, the Decryption logs log the error.Select ObjectsDecryptionDecryption Profiles. Then, select a profile to modify or create a new profile.
![]() Filter the log to identify sessions that failed due to revoked certificates using the query (error eq ‘Untrusted issuer CA’).
Filter the log to identify sessions that failed due to revoked certificates using the query (error eq ‘Untrusted issuer CA’).![]() (Optional) Double-check the certificate expiration date at the Qualys SSL Labs site.Enter the hostname of the server (Server Name Identification column of the Decryption log) in the Hostname field and Submit it to view certificate information for the host.
(Optional) Double-check the certificate expiration date at the Qualys SSL Labs site.Enter the hostname of the server (Server Name Identification column of the Decryption log) in the Hostname field and Submit it to view certificate information for the host.