Network Security
Migrating Web Security Policy Rules to Internet Access Rules
Table of Contents
Expand All
|
Collapse All
Network Security Docs
Migrating Web Security Policy Rules to Internet Access Rules
This section outlines the changes to Web Security policy rules in the latest Strata Cloud
Manager February 2025 Release and provides various troubleshooting scenarios.
The Strata Cloud Manager February 2025 release changes how we handle Web Security in
your environment. We addressed the rigidity of current Web Access policy rules based
on user feedback. Users reported challenges with rule ordering and cross-referencing
of objects and profiles, which caused operational inefficiencies from unusable
rulebases or object duplication.
We moved to a single rulebase to enhance flexibility and user control. This
change streamlines policy management and improves operational efficiency.
The Internet Access rule replaces the existing Web Access policy rules with
improved capabilities. The Internet access rule is a new policy type within the
security rulebase in Strata Cloud Manager that optimizes the management of internet
access use cases.
Changes to Web Security in Strata Cloud Manager
|
Old Navigation Path
| New Navigation Path |
|---|---|
ManageConfigurationNGFW and Prisma AccessSecurity ServicesWeb SecurityWeb Access PolicyPolicies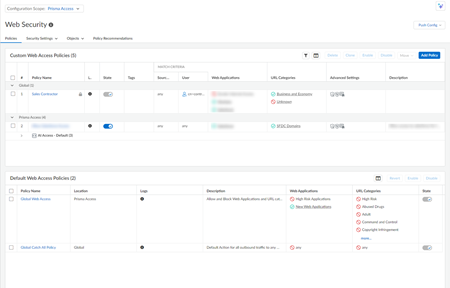
| ConfigurationNGFW and Prisma AccessSecurity ServicesSecurity PolicySecurity Policy RulesAdd Rule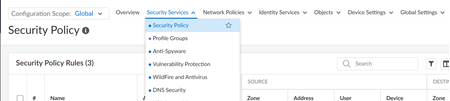
|
ManageConfigurationNGFW and Prisma AccessSecurity ServicesWeb SecuritySecurity Settings 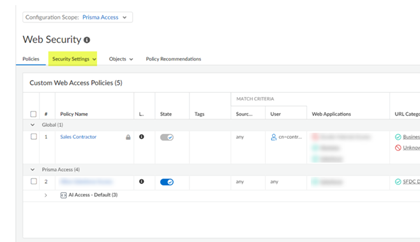
| ConfigurationNGFW and Prisma AccessSecurity ServicesInternet SecuritySecurity Settings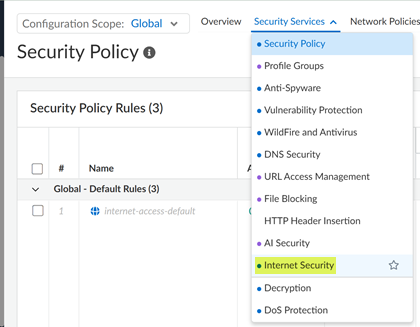
|
| ManageConfigurationNGFW and Prisma AccessSecurity ServicesWeb SecuritySecurity Settings Threat Management | ConfigurationNGFW and Prisma AccessSecurity ServicesInternet SecuritySecurity SettingsThreat Management
|
| ManageConfigurationNGFW and Prisma AccessSecurity ServicesWeb SecuritySecurity Settings DNS Security | ConfigurationNGFW and Prisma AccessSecurity ServicesInternet SecuritySecurity SettingsDNS Security |
| ManageConfigurationNGFW and Prisma AccessSecurity ServicesWeb SecuritySecurity Settings Decryption | ConfigurationNGFW and Prisma AccessSecurity ServicesInternet SecuritySecurity SettingsDecryption |
| ManageConfigurationNGFW and Prisma AccessSecurity ServicesWeb SecuritySecurity Settings File Control | ConfigurationNGFW and Prisma AccessSecurity ServicesInternet SecuritySecurity SettingsFile Control |
| ManageConfigurationNGFW and Prisma AccessSecurity ServicesWeb SecuritySecurity Settings General | ConfigurationNGFW and Prisma AccessSecurity ServicesInternet SecuritySecurity SettingsGeneral |
| ManageConfigurationNGFW and Prisma AccessSecurity ServicesWeb SecurityObjects | ConfigurationNGFW and Prisma AccessSecurity ServicesInternet SecurityObjects
|
| ManageConfigurationNGFW and Prisma AccessSecurity ServicesWeb SecurityObjectsDevice Posture | ConfigurationNGFW and Prisma AccessSecurity ServicesInternet SecurityObjects Device Posture |
| ManageConfigurationNGFW and Prisma AccessSecurity ServicesWeb SecurityObjectsDevice Posture |
ConfigurationNGFW and Prisma AccessSecurity ServicesInternet SecurityObjects App Group with Control
|
| ManageConfigurationNGFW and Prisma AccessSecurity ServicesWeb SecurityPolicy Recommendations |
ConfigurationNGFW and Prisma AccessConfiguration ScopeSnippetsSAAS-Inline-Pol-Recommendation
|
Troubleshooting Scenarios for Environments Without Web Security Enabled at Any Node
| Case | Issue | How to Mitigate |
|---|---|---|
|
Unintended Country Block Policy Rules (for Prisma
Access only)
|
If you have any Country Block configuration in the
Source or Destination region block under Security Services >
Web Security > Security Settings > Threat Management, it
will generate a source-region and destination-region block
policies respectively.
|
|
|
Web Security Default Snippet
Reattachment
|
During the upgrade, the Web Security default
snippet (Internet-Security-Default) is automatically
reattached to Global, even if previously removed or
detached. This reattachment may fail if the snippet is
attached to child nodes. The snippet is required and not
having it will cause reference errors, as other snippets may
reference profiles and objects within this default
snippet.
|
|
|
Web Security and Internet Access Changes
| After the upgrade, review the Internet Security settings to ensure correct behavior. |
Expected Upgrade Behavior:
|
Troubleshooting Scenarios for Partial Web Security Enablement on Nodes
| Case | Issue | How to Mitigate |
|---|---|---|
|
Resolving Unintended Policy Inheritance in Child
Scopes
|
When policies are created on a parent folder, but
one or more child folders/scopes do not have Web Security
enabled, all parent policies will be inherited by all child
scopes and get enforced, once pushed.
|
|
|
Internet Access Default post-rule in Global is
enabled
| When the Internet Access default post-rule in Global is enabled, it impacts traffic on all child nodes, as it gets enforced as a Global post-rule. If you want different treatment for different child nodes, then mitigation is required. |
|
|
Implicit DNS allow policy is moved to a snippet
|
When Internet Access migrates to a single rulebase, the
implicit DNS allow policy is no longer implemented. This is
managed via a snippet instead and in user control.
|
|
Troubleshooting Scenarios For Hybrid (Prisma Access + NGFW tenant)
| Case | Issue | How to Mitigate |
|---|---|---|
| Security Zone Mismatch in Internet Access Policies | The security zones used by Internet Access policy rules are defaulted to Inbound Zone = any and Outbound zone = internet, push time validations / commits fail if these zones do not exist on the NGFW. |
|
|
Snippet Attachment Issues with Device Scope and Web
Security Settings.
|
When device scope is disabled but Web Security is
enabled for specific Next-Generation Firewalls (NGFWs), you
may encounter issues with attaching snippets directly to
nodes. In particular, the Internet Access best practice
snippet, which contains default policies for Internet and
Gen AI access, cannot be attached and policies will get
removed during the push process for affected devices.
|
|
Troubleshooting Scenarios: Web Security is Enabled and Snippet with Web Security Policy Rules is attached
| Case | Issue | How to Mitigate |
|---|---|---|
|
Web Access Policy Placement After
Upgrade
|
Following an upgrade, web access policies are
relocated to the security rulebase of the snippet. These
snippets are attached in order within the security rulebase
of folders. Consequently, web access policies are positioned
just above the security policies of that particular snippet.
This differs from the pre-upgrade behavior, where they were
placed at the top of the rulebase, above all security rules.
This change in ordering can potentially impact your security
posture and policy enforcement.
|
|
Troubleshooting Scenario: Rule Name Collision Between Web Access Policy Rules and Security Rules
| Case | Issue | How to Mitigate |
|---|---|---|
|
Rule Name Conflicts During Web Access and
Security Policy Migration
|
When migrating to a single rulebase, identical rule
names in Web Access policies can cause name conflicts. This
situation arises because the unified rulebase requires
unique identifiers for each rule. The conflict can lead to
unexpected behavior, policy application errors, or potential
security gaps if not addressed properly.
|
|
