Network Security
Configure Decryption Port Mirroring
Table of Contents
Expand All
|
Collapse All
Network Security Docs
Configure Decryption Port Mirroring
Where permitted by law, you can decrypt traffic and send unencrypted traffic to a
device that can archive and analyze the traffic.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
Before you can enable Decryption Port Mirroring, obtain and install the free Decryption Port
Mirror license. You can activate this license through the Customer Support Portal.
The license requirement ensures that this feature can only be used after approved
personnel purposefully activate the license. After obtaining, installing, and
activating the license, reboot the Next-Generation Firewall (NGFW),
then enable decryption mirroring.
Important Considerations
- Certain countries regulate the decryption, storage, inspection, or use of SSL traffic, and user consent may be required to mirror traffic
- Malicious users with administrative access to the NGFW could potentially harvest sensitive information (for example, usernames, passwords, social security numbers, and credit card numbers) submitted through encrypted channels.
- Consult with corporate counsel before activating and using this feature in a production environment.
- Request a license for each NGFW on which you want to enable decryption mirroring.
- Log in to the Palo Alto Networks Customer Support website and navigate to the Assets tab.Select the entry for the NGFW you want to license and select Actions.Select Decryption Port Mirror. A legal notice displays.Click I understand and wish to proceed when you are clear about the potential legal implications and requirements.Click Activate.
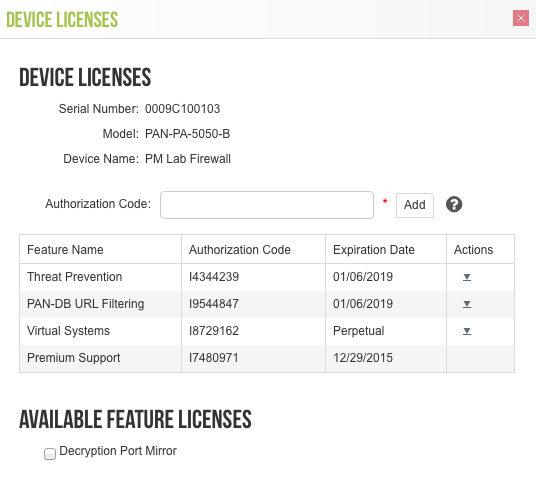
![]() Install the Decryption Port Mirror license.
Install the Decryption Port Mirror license.- On the NGFW, select DeviceLicenses.Click Retrieve license keys from license server.Verify that the license is active.
![]() Reboot the NGFW (DeviceSetupOperations). This feature is not available for configuration until PAN-OS reloads.Forward decrypted traffic. Superuser permission is required to perform this step.On an NGFW with a single virtual system:
Reboot the NGFW (DeviceSetupOperations). This feature is not available for configuration until PAN-OS reloads.Forward decrypted traffic. Superuser permission is required to perform this step.On an NGFW with a single virtual system:- Select DeviceSetupContent-ID.Select Allow forwarding of decrypted content.Click OK.On an NGFW with multiple virtual systems:
- Select DeviceVirtual System.Select a Virtual System, or create a new Virtual System by selecting Add.Select Allow forwarding of decrypted content.Click OK.Enable the Ethernet interface you want to use for decryption mirroring.
- Select NetworkInterfacesEthernet.Click an Ethernet interface. A dialog with various settings appears.For Interface Type, select Decrypt Mirror.This interface type appears only if you have installed the Decryption Port Mirror license.Click OK.Enable mirroring of decrypted traffic.
- Select ObjectsDecryption Profile.Select the Interface you will use for Decryption Mirroring.The Interface drop-down contains all Ethernet interfaces of Decrypt Mirror type.Specify whether to mirror decrypted traffic before or after policy enforcement.By default, the NGFW mirrors all decrypted traffic to the interface before the Security policy rule lookup, allowing you to replay events and analyze traffic that generates a threat or triggers a drop action.If you want to only mirror decrypted traffic after Security policy enforcement, select the Forwarded Only check box. With this option, only traffic forwarded through the NGFW is mirrored. This option is useful if you are forwarding the decrypted traffic to other threat detection devices, such as a DLP device or another intrusion prevention system (IPS).Click OK.Attach the decryption profile rule (with decryption port mirroring enabled) to a decryption policy rule. All traffic decrypted based on the policy rule is mirrored.
- Select PoliciesDecryption.Select an existing decryption policy rule, or Add a new rule.In the Options tab, select Decrypt and the Decryption Profile you created earlier.Click OK.Save the configuration.Click Commit.