Network Security
Find External Dynamic Lists That Failed Authentication
Table of Contents
Expand All
|
Collapse All
Network Security Docs
Find External Dynamic Lists That Failed Authentication
View authentication failures related to external dynamic lists so you can take
resolve them.
An External Dynamic List (EDL) used for policy enforcement can be hosted either
internally or externally. Your configuration checks your EDLs at your configured
intervals to enable dynamic policy enforcement.
EDLs play a vital role in enriching the threat intelligence of your
configuration by keeping threat data up to date. However, authentication failures
with these lists can disrupt this critical process and potentially impact your
configuration's ability to stay updated with the latest threat intelligence.
Identifying and addressing external dynamic lists (EDLs) that have failed
authentication is necessary for maintaining a reliable and secure network
infrastructure.
Once you’ve identified the EDLs with authentication failures using the
steps below, you’ll be able to take appropriate action to rectify the situation.
This might involve updating the authentication credentials, verifying connectivity
to the authentication server, or addressing any changes in the authentication
mechanism.
Regularly reviewing and addressing authentication failures for EDLs is
crucial for maintaining an effective threat intelligence update mechanism. By
ensuring that the authentication process for EDLs functions smoothly, you can
maximize the potential of your configuration to detect and mitigate emerging
cyberthreats in a timely and proactive manner.
Follow these steps to find external dynamic lists that have failed
authentication.
Find External Dynamic Lists That Failed Authentication (Strata Cloud Manager)
View authentication failures related to external dynamic lists.
When an external dynamic list that requires SSL fails client or server
authentication, you'll see the authentication failure in the EDL Distribution
Status. Typically, if your environment is unable to connect or otherwise fetch the
most current EDL from the server, your configuration retains the last successfully
retrieved list and continues operating with the most recent EDL information until
the connection is restored with the web server hosting the EDL. However, in cases
where authentication to the EDL fails, the Security policy stops enforcing the EDL.
Use the following process to view authentication failures related to external
dynamic lists. Troubleshoot EDLs
Troubleshoot EDLs
Get the status and latest details for the External Dynamic Lists (EDLs) that
you’re using with Prisma Access, and:
- Search across EDLs to see if they include a specific IP address, subnet, or URL
- Force an EDL to refresh
To get started, go to ConfigurationNGFW and Prisma AccessObjectsExternal Dynamic Lists, set the scope to Remote Networks or
Mobile Users - GlobalProtect, and check the
EDL Status.
Troubleshooting is available only for custom EDLs and not for predefined,
built-in EDLs.

Troubleshoot Site Connections
For troubleshooting purposes, you can now view the routing table for a remote
network site or service connection site. Find the Routing
Information button on the remote networks or service connection
dashboard.
Go to ConfigurationNGFW and Prisma AccessOverview, set the Configuration Scope to
Prisma Access, select either
Remote Networks or Service
Connections, and then select Routing InformationShow.

Find External Dynamic Lists That Failed Authentication (PAN-OS & Panorama)
View authentication failures related to external dynamic lists.
When an external dynamic list that requires SSL fails client or server
authentication, the firewall generates a system log of critical severity. The log is
critical because the firewall continues to enforce policy based on the last
successful external dynamic list after it fails authentication, instead of using the
latest version. Use the following process to view critical system log messages
notifying you of authentication failure related to external dynamic lists.
The following warning is displayed when your environment is unable to connect or
otherwise fetch the most current EDL information from the server.
Unable to fetch external list. Using old copy for refresh.
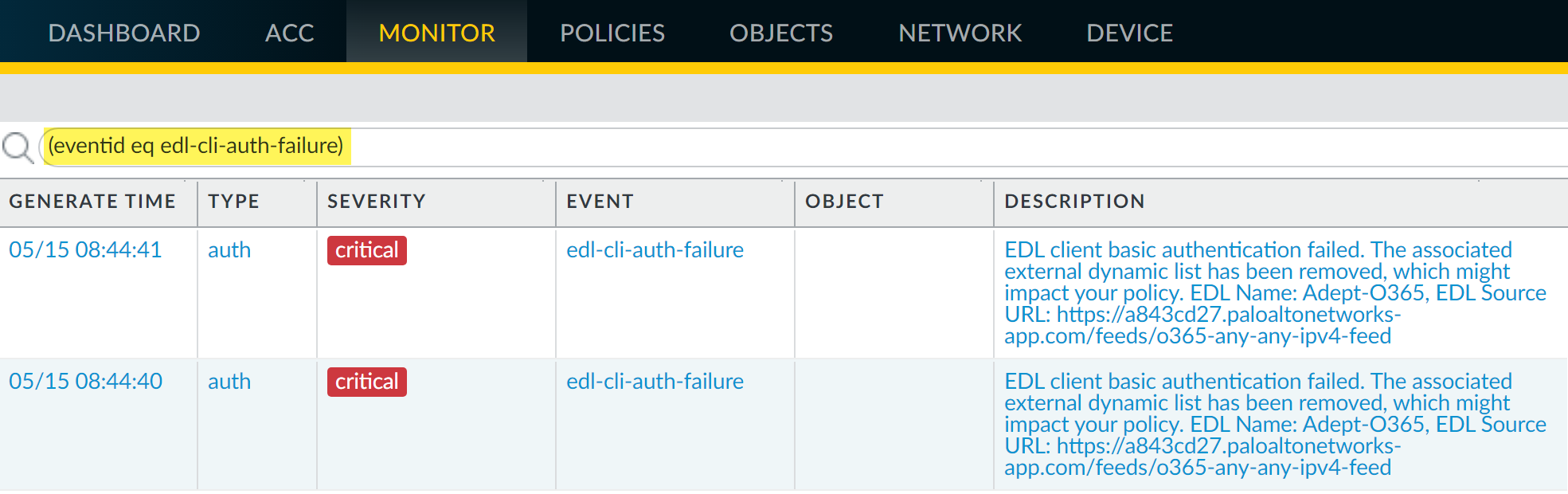
- Select MonitorLogsSystem.Construct the following filters to view all messages related to authentication failure, and apply the filters. For more information, review the complete workflow to Filter Logs.
- Server authentication failure—(eventid eq tls-edl-auth-failure)
- Client authentication failure—(eventid eq edl-cli-auth-failure)
![]() Review the system log messages. The message description includes the name of the external dynamic list, the source URL for the list, and the reason for the authentication failure.The server that hosts the external dynamic list fails authentication if the certificate is expired. If you have configured the certificate profile to check certificate revocation status via Certificate Revocation List (CRL) or Online Certificate Status Protocol (OCSP), the server may also fail authentication if:
Review the system log messages. The message description includes the name of the external dynamic list, the source URL for the list, and the reason for the authentication failure.The server that hosts the external dynamic list fails authentication if the certificate is expired. If you have configured the certificate profile to check certificate revocation status via Certificate Revocation List (CRL) or Online Certificate Status Protocol (OCSP), the server may also fail authentication if:- The certificate is revoked.
- The revocation status of the certificate is unknown.
- The connection times out as the firewall is attempting to connect to the CRL/OCSP service.
For more information on certificate profile settings, refer to the steps to Configure a Certificate Profile.Verify that you added the root CA and intermediate CA of the server to the certificate profile configured with the external dynamic list. Otherwise, the firewall will not authenticate the list properly.Client authentication fails if you have entered the incorrect username and password combination for the external dynamic list.(Optional) Disable Authentication for an External Dynamic List that failed authentication as a stop-gap measure until the list owner renews the certificate(s) of the server that hosts the list.