About Roles and Permissions Through Common Services
Table of Contents
Expand all | Collapse all
- Get Started with Common Services: Identity & Access
-
- Add an Identity Federation
- Manually Configure a SAML Identity Provider
- Upload SAML Identity Provider Metadata
- Get the URL of a SAML Identity Provider
- Clone SAML Identity Provider Configuration
- Add or Delete an Identity Federation Owner
- Configure Palo Alto Networks as a Service Provider
- Delete an Identity Federation
- Map a Tenant for Authorization
- Update Tenant Mapping for Authorization
- PAN Resource Name Mapping Properties
- Manage Single Tenant Transition to Multitenant
- Release Updates
About Roles and Permissions Through Common Services
Learn about Common Services roles and permissions for role-based access control
(RBAC).
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
Common Services: Identity and Access supports role-based access control
(RBAC). Using Identity and Access, you can manage tenant users, service accounts, and
access to various resources within Common Services, Strata Multitenant Cloud Manager,
and enterprise apps. You're required to assign roles for users but roles are optional
for service accounts.
Roles work as a union. If you assign a role to a user for a specific app and another role
for All Apps & Services, the user will get the union of both
permissions. For example, consider a scenario where a user is assigned a role for the
Strata Logging Service app with a role that does not allow download or
share permissions. If that same user is also assigned the Superuser role for All Apps
& Services, the user is able to download and share. The behavior is to check the
specific app first and if the permission isn't available, then check All Apps &
Services. For more information about what each role can do, you can view the
permissions in the platform for each role.
If you have received information about the transition
of your app instance to a tenant or tenant service group (TSG), see
where are my roles? for a mapping of
previous roles to IAM roles.
Permissions
Permissions are actions that are allowed in the system. Permissions represent a specific set of
application programming interface (API) calls that you use to read, write, and
delete objects within the system. You can view the permissions in the
platform grouped into roles.
Multitenant Platform Roles
Multitenant platform roles are a predefined set of permissions for managing tenants
in a multitenant hierarchy. These roles include a collection of one or more system
permissions that are specific to the platform.
By default, every user automatically gets a
role that provides access to only the essential features required by Palo Alto
Networks web interface applications. This isn't the same as a “view only” role, as
it's necessary for the web interface. You can't assign or unassign this role.
The following table describes general roles and responsibilities. For more
information about what each role can do, you can view the permissions in the
platform for each role.
| Multitenant Platform Roles | Permissions | Supported Applications |
|---|---|---|
| Multitenant Superuser |
Read and write access to manage all apps, Strata Logging Service logs, and services within the
assigned level of the nested hierarchy. Includes all permissions
assigned to all roles, including Superuser. Includes access to
dashboards, create custom dashboards, and download, share, and
schedule reports. Includes the ability to activate product
licenses through an email activation link. Assign this role only
to users or service accounts that require unrestricted
access.
|
|
| Multitenant IAM Administrator |
Read and write access to identity and authentication functions
for all tenants in a multitenant hierarchy. Restricted to
read-only access for logs. No access to dashboards and Strata Logging Service logs.
|
|
| Multitenant Manage User | This role provides access to functions related to multitenant management and other common resources. |
|
| Multitenant Monitor User | This role provides access to functions related to multitenant monitoring and other common resources. |
|
| Business Administrator |
Read and write access to all subscription and license management
for the selected app. Includes read-only access to other
functions, such as access policies, service accounts, and tenant
Service Group operations. No access to dashboards and Strata Logging Service logs. Includes the ability to
activate product licenses through an email activation link.
Assign this role to administrators who manage devices, licenses,
and subscriptions.
|
|
When you add user access or add a service account,
you can assign a predefined
role to execute specific functions within the platform. You
can also assign a batch of
predefined roles to assign a role in bulk to multiple users
or service accounts at the same time.
Enterprise Roles
Enterprise roles are a predefined set of permissions for managing enterprise applications and
services. These roles include a collection of one or more system permissions for any
app to use. The following table describes general enterprise roles and
responsibilities. For more information about what each role can do, you can view the
permissions in the platform for each role.
| Enterprise Roles | Permissions | Supported Applications |
|---|---|---|
| ADEM Tier 1 Support |
For use with the Prisma Access app. Read-only access to
specific incident remediation workflows for only Prisma Access Autonomous Digital Experience Management
(ADEM). No access to other Prisma Access services. No
access to dashboards and Strata Logging Service
logs. Assign this role to third-party helpdesk employees, tier 2
and 3 support, or administrators who only need ADEM access.
|
|
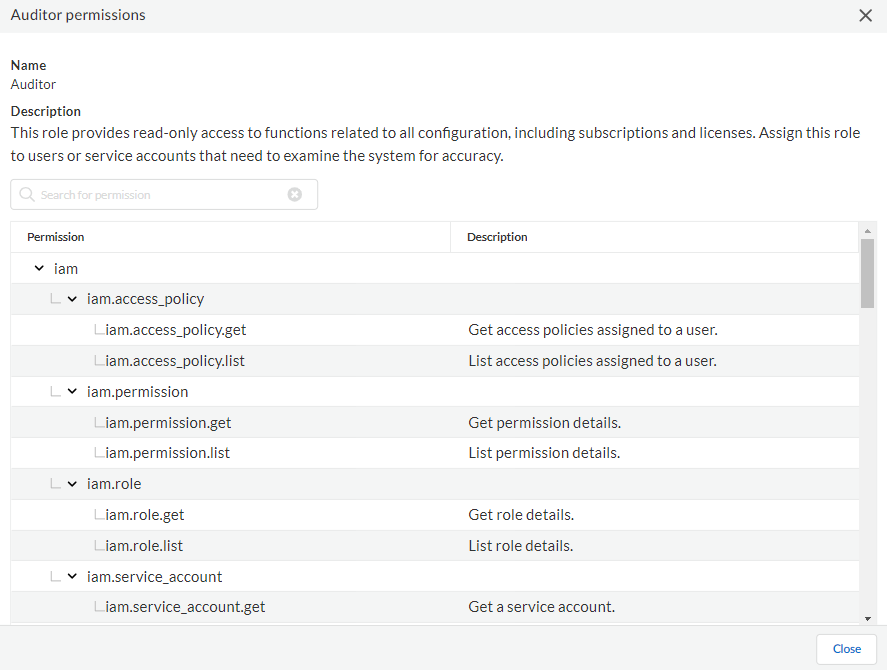
| Auditor |
Read-only access to functions related to all configurations,
including subscriptions and licenses for the selected app.
Includes access to view dashboards but can't download, share,
and schedule reports. Includes access to Strata Logging Service logs. Assign this role to
administrators who are tasked with examining the system for
accuracy.
|
|
| Data Security Administrator |
Read and write access to all data security functions for the
selected app. Includes access to Strata Logging Service logs, dashboards, create custom
dashboards, and download, share, and schedule reports. Includes
read-only access to logs. This role includes a small subset of
privileges included in the Security Admin role. Assign this role
to administrators who manage only decryption rule
configurations.
|
|
| Deployment Administrator |
Access to functions related to deployments. In addition, this
role provides read-only access to other functions.
|
|
| DLP Incident Administrator | This role provides access to functions related to DLP incidents and reports. This role also provides read-only access to other functions, including but not limited to: data profile, data filtering profile, data pattern, EDM, and OCR settings. |
|
| DLP Policy Administrator | This role provides access to functions related to DLP policy, including but not limited to: data profile, data filtering profile, data pattern, EDM, and OCR settings. |
|
| IAM Administrator |
Read and write access to identity and authentication functions
for the selected app. Includes read-only access to logs. No
access to dashboards and Strata Logging Service
logs. Assign this role to administrators who manage users.
|
|
| Network Administrator |
Read and write access to logs and network policy configurations
for the selected app. Includes read-only access to other
functions: alerts, license quotas, devices, and tenant Service
Group operations. Includes access to dashboards, create custom
dashboards, and download, share, and schedule reports. Assign
this role to administrators who need to maintain authentication,
certificates, and decryption rules.
|
|
| Posture Security Administrator |
This role provides full SSPM functionality, but only for the SaaS
applications that the administrators onboard themselves. It is
intended to give IT/SaaS administrators visibility and full SSPM
read and write access to the SaaS apps they are responsible
for.
|
|
| Security Administrator |
Read and write access to logs and security policy configurations
for the selected app. This includes read-only access to other
functions, such as alerts, license quotas, devices, and tenant
Service Group operations. Includes access to dashboards, create
custom dashboards, and download, share, and schedule reports.
Assign this role to administrators who need to maintain
authentication, certificates, and decryption rules.
|
|
| SOC Analyst |
Access to functions related to logs, reports, events, alerts, and
all configurations for the selected app. Assign this role to
administrators who need to view and investigate threats and
trends.
|
|
| Superuser |
Read and write access to all available system-wide functions for
the selected app. This includes all permissions assigned to all
other roles, including MSP Superuser. This includes the ability
to activate product licenses through an email activation link.
Assign this role only to users or service accounts that require
unrestricted access.
|
|
| Tier 1 Support |
Read and write access to remediation workflows that update
network, security, and device configurations for the selected
app. This includes read-only access for alerts, access policies,
configurations, license quotas, devices, and tenant Service
Group operations. Full access to view dashboards, create custom
dashboards, download, share, and schedule reports, and Strata Logging Service logs.
|
|
| Tier 2 Support |
Read and write access to remediation workflows that update
network, security, and device configurations for the selected
app. This includes read-only access for alerts, access policies,
configurations, license quotas, devices, and tenant Service
Group operations. Full access to view dashboards, create custom
dashboards, download, share, and schedule reports, andStrata Logging Service logs.
|
|
| View Only Administrator |
Read-only access to all available system-wide functions for the
selected app and logs (except DNS logs). Includes access to view
dashboards except DNS dashboard. No access to download, share,
and schedule dashboards.
|
|
| Web Security Admin | This role provides access to functions related to web security for Prisma Access. |
|
When you add user access or add a service account,
you can assign a predefined
role to execute specific functions within a network. You
can also assign a batch of
predefined roles to assign a role in bulk to multiple users
or service accounts at the same time.
View Role Permissions
For more granular information about what each role can do, you can view the
permissions.
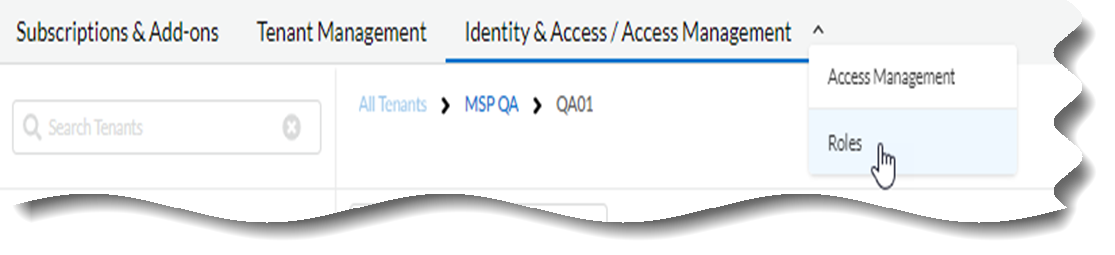
- Use one of the various ways to access Common ServicesIdentity & Access.
- Select Common ServicesIdentity & Access/Access ManagementRoles to view role permissions.
![]()
- Select a role, such as Auditor to view the
permissions.
![]()