Next-Generation Firewall
New Features Through August 2023
Table of Contents
Expand All
|
Collapse All
Next-Generation Firewall Docs
-
-
-
-
-
-
-
- PAN-OS 12.1
- PAN-OS 11.2
- PAN-OS 11.1
- PAN-OS 11.0 (EoL)
- PAN-OS 10.2
- PAN-OS 10.1
- PAN-OS 10.0 (EoL)
- PAN-OS 9.1 (EoL)
- PAN-OS 9.0 (EoL)
- PAN-OS 8.1 (EoL)
-
- PAN-OS 12.1
- PAN-OS 11.2
- PAN-OS 11.1
- PAN-OS 10.2
- PAN-OS 10.1
New Features Through August 2023
These are the new features introduced from June through August 2023 for AIOps for
NGFW Free, and for AIOps for NGFW Premium.
These are the new features introduced from June through August 2023 for AIOps for NGFW
Free, and for AIOps for NGFW Premium. AIOps for NGFW Premium updates include new
features to support Cloud Management for NGFWs.
AIOps for NGFW on the Strata Cloud Manager Platform
AIOps for NGFW is now supported on the new Strata Cloud Manager platform. Starting
in June 2023, we'll be rolling out phased updates to provide you with the new
platform experience. We'll be updating your AIOps for NGFW app so that it is
on the Strata Cloud Manager platform, alongside your other Palo Alto Networks
products and subscriptions that are supported for unified management. This change
gives you a new navigation for your AIOps for NGFW features, introduces new
features, and means you can use common workflows and features across AIOps for NGFW
and your other products that are also updated for Strata Cloud Manager. Learn
more:
- What to expect when AIOps for NGFW is updated to give you the new management experience
- Where can I find my AIOps for NGFW features in Strata Cloud Manager?
- Take a First Look Strata Cloud Manager
- See the products and subscriptions are supported for unified management with Strata Cloud Manager
Palo Alto Networks Strata Cloud Manager
is the new AI-Powered network security management and operations platform. With Strata Cloud Manager, you can easily manage and monitor your Palo Alto Networks
network security infrastructure ━ your NGFWs and SASE environment ━ from a single,
streamlined user interface. This new cloud management experience gives you:
-
Shared policy for SASE and your NGFWs, and a unified view into security effectiveness.
-
AI-Powered ADEM for Prisma SASE; this new Prisma Access add-on license automates complex IT operations, to increase productivity and reduce time to resolution for issues.
-
Best practice recommendations and workflows to strengthen security posture and eliminate risk.
-
A common alerting framework that identifies network disruptions, so you can maintain optimal health and performance.
-
Enhanced user experience, with contextual and interactive use-case driven dashboards and license-aware data enrichment.
Learn more about Strata Cloud Manager
Cloud Management of NGFWs
Manage Palo Alto Networks Next-Generation firewalls from Strata Cloud Manager.
Manage your Palo Alto Networks Next-Generation firewalls from Strata Cloud Manager. Cloud Management of NGFW is a cloud-delivered
and AI-powered security solution to manage Palo Alto Networks' advanced ML-powered
firewalls alongside your Prisma Access deployments.
Cloud Management of NGFWs is done from a single streamlined user interface and leverages
Palo Alto Networks best-in-class cloud-delivered security services. To manage your
Next-Gen firewalls from Strata Cloud Manager, you must enable AIOps for NGFW Premium which also draws on PAN-OS device telemetry data to give
you an overview of the health and security of your cloud managed NGFWs. For logging, Strata Logging Service provides a secure, resilient, and fault tolerant
centralized log storage and aggregation.
VM Flex License Agreement for AIOps for NGFW
Now you can use Common Services to activate a VM Flex license agreement for
AIOps for NGFW.
Capacity Analyzer
Learn about what's new in Capacity Analyzer.
Sometimes, you can encounter a predicament where particular features on
your Next-Generation Firewalls (NGFW) approach their capacity thresholds, resulting
in diminished system performance and operational disruptions. Dealing with
capacity-related issues can be time-consuming, and unfortunately, these issues tend
to come to light only after the limits are breached.
The Capacity Analyzer feature allows
monitoring of device resource capacity by tracking metrics usage based on model
types. This feature includes a heatmap visualization to display resource consumption
rates and locations for each metric. It also enables planning for upgrading to
higher capacity firewalls based on specific needs. This proactive approach ensures
that you know about potential capacity constraints, allowing you to take preemptive
action to safeguard your business operations.

Compliance Summary Dashboard
View a history of changes to security checks.
Check the Compliance dashboard to view a history of
changes to the security checks made up to 12 months in the past, grouped together by
Center for Internet Security (CIS) and National Institute of Standards and Technology
(NIST) frameworks.

Best Practices Dashboard
The best practices dashboard and reports measure your security posture against Palo
Alto Networks’ best practice guidance.
Check the Best Practices dashboard for daily best
practices reports, and their mapping to Center for Internet Security’s Critical Security
Controls (CSC) checks, to help you identify areas where you can make changes to improve
your best practices compliance. Share the best practice report as a PDF and schedule it
to be regularly delivered to your inbox. This release introduces the following new
features:
- Ability to export BPA reports in .csv format for use in third-party applications such as Microsoft Excel
- Ability to download CLI remediations in .txt format. CLI remediations are generated using TSF data you upload when generating an On-Demand BPA report. (PAN-OS 9.1 and above TSFs)
- Ability to view historical trend charts for BPA checks

Security Posture Insights Dashboard
Get visibility into the security status and trend of your deployment based on the
security postures of the onboarded NGFW devices.
Get visibility into the security status and trend of your deployment based on
the security postures of the onboarded NGFWs with Security Posture Insights. Use this dashboard
to:
-
Know the trend of issues that impact the security posture of your deployment.
-
Understand the security improvements that you have made in your deployment by looking at the historical security score data.
-
Narrow down devices where there is an opportunity to improve the security posture and prioritize the issues to resolve them.

On-Demand BPA & Adoption Summary
Generate a BPA Report with Feature Adoption Summary on demand.
Run the Best Practice Assessment (BPA) and Feature Adoption summary directly
from Strata Cloud Manager. Just upload a Tech Support File (TSF) to generate the on-demand BPA report for devices
that are not sending telemetry data or onboarded to AIOps for NGFW (PAN-OS devices
running versions 9.1 and above).
The BPA evaluates your security posture against Palo Alto Networks best practices and
prioritizes improvements for devices. Security best practices prevent known and unknown
threats, reduce the attack surface, and provide visibility into traffic, so you can know
and control which applications, users, and content are on your network.
Custom Dashboard
Create and customize dashboards to get visibility into areas of interest in your
network.
Apart from the default dashboards, you can now build a custom dashboard based on your network and
security visibility requirements. You can use various types of customizable widgets from
the widget library to create the dashboard. The
widgets available to you depend on the services supported with your licenses. You can
add up to 10 widgets in a custom dashboard and create 10 custom dashboards per user. The
custom dashboard can be customized at any time. These are some of the customizations
available in the custom dashboard:
-
Customize dashboard settings such as layout, dashboard name, and descriptions
-
Edit widget title, description, and show or hide filters
-
Filter and sort data
-
Look at the Sample Data view to know how your widget looks in the dashboard

Device Health Dashboard
The Device Health dashboard provides an overall view of the health and performance of
your NGFW devices.
The Device health dashboard shows you the
cumulative health status and performance of your onboarded NGFW devices. The device
health is determined by the severity of the health score (0-100) and its corresponding
health grade (good, fair, poor, critical). The health score is calculated based on the
priority, quantity, type, and status of the open alerts.
This dashboard helps you:
-
Understand the deployment improvements that you have made over a period by looking at the historical health score data.
-
Narrow down devices that require attention in your deployment and prioritize the issues to resolve them.
- Review the device statistics and fix the critical alerts on the device to improve the health score and deployment health.
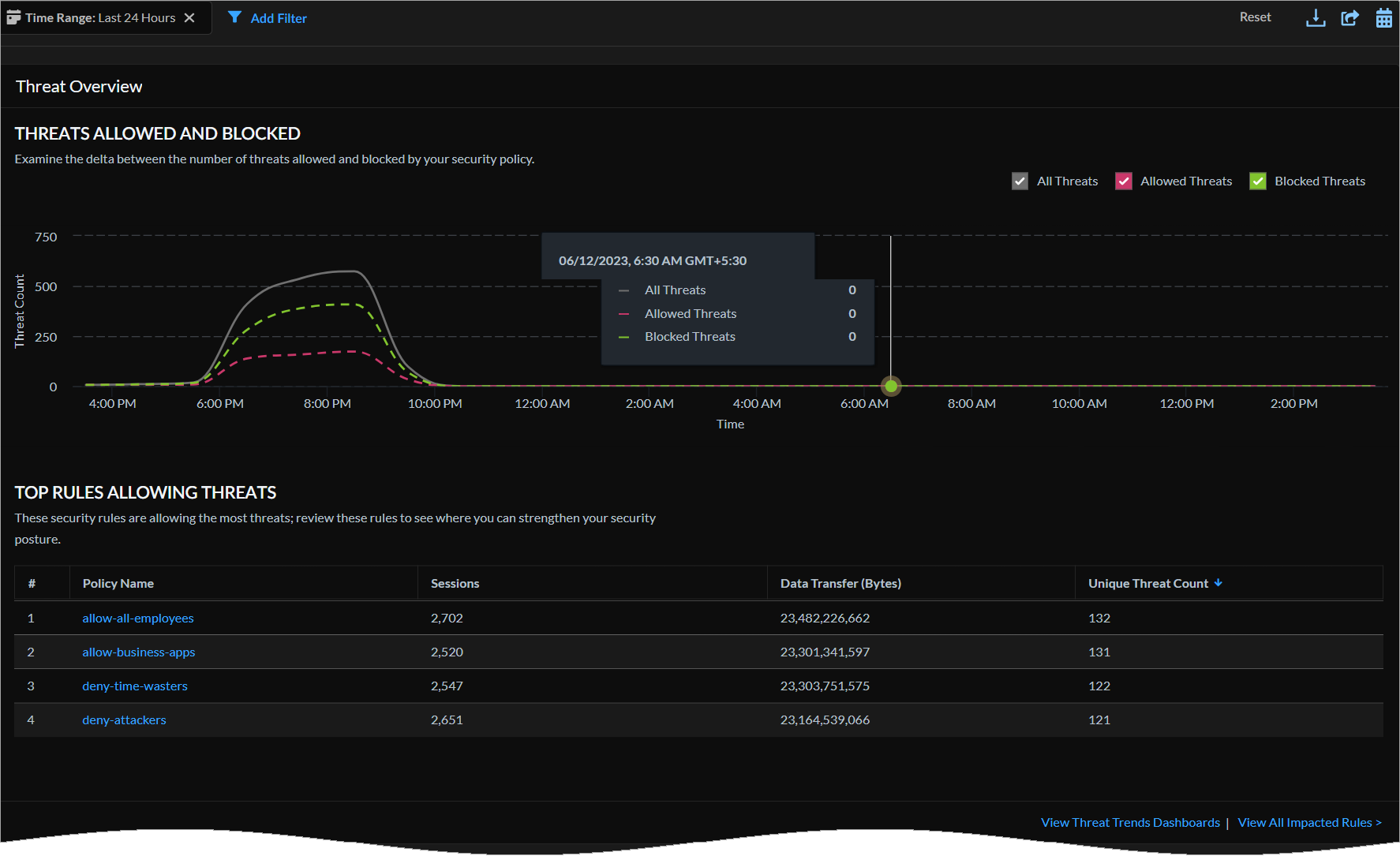
Advanced Threat Prevention Dashboard
Identify opportunities to strengthen your security posture with the threat prevention
dashboard.
The Advanced Threat Prevention dashboard gives
insight into unknown malware, command and control (C2), and vulnerability exploit
attempts in your network. The dashboard gives visibility into the real-time threat
detection data by inline cloud analysis along with threats
detected based on the threat signatures generated from malicious
traffic data collected from various Palo Alto Networks services.
This dashboard provides:
- a time line view of threats allowed and blocked, list of source IPs and users responsible for generating command and control (C2) traffic, and hosts targeted by cloud-detected exploits.
- contextual links to Log Viewer to get context around the threat.
- IOC search result to learn about the usage patterns related to host generating traffic and host targeted by vulnerability exploits.
- cloud report and packet capture from the logs to get additional context and use Palo Alto Networks threat analytics data and threat intelligence to improve your incident response processes.
The dashboard helps to understand the security effectiveness of the Advanced Threat Prevention service. Use the data along
with the analysis data from your other Palo Alto Networks security services to prevent
security infringement on your network infrastructure.
Enhancements to CDSS Dashboard
Learn about the enhancements in the CDSS dashboard.
In order to enhance the security of your enterprise by identifying and
addressing potential security vulnerabilities, AIOps for NGFW offers a streamlined
workflow that enables you to monitor the implementation of CDSS features using the CDSS dashboard. This allows you to easily
track the progress of CDSS feature activation, configuration, and adherence to best
practices. Moreover, you have the option to override recommendations at the firewall
level, saving time by avoiding the need to override them for each role-pair
individually.

Feature Adoption Dashboard
Monitor the security features you’re using.
Monitor Feature Adoption and stay abreast of which
security features you’re using in your deployment and potential gaps in coverage. This
release introduces the following new features:
- TSF upload-generated CLI remediations (PAN-OS 9.1 and above TSFs)
- Historical adoption trend charts
- Per-device views of adoption (including for Panorama-managed devices)
- Ability to export adoption data as .csv file

NGFW SDWAN Dashboard
Learn about what's new in the NGFW SDWAN dashboard.
The NGFW SD-WAN dashboard provides performance
metrics for cloud-managed firewalls with SD-WAN, allowing visibility into application
and link performance. It helps troubleshoot issues across VPN clusters, isolates
problems to affected sites, applications, and links, and generates actionable alerts for
poor links and applications. These alerts are based on data-driven thresholds and offer
insights into trends with machine learning-powered detection and forecasting.

