X-Forwarded-For HTTP Header Data Support in Policy
Table of Contents
10.0 (EoL)
Expand all | Collapse all
-
- Automatic Content Updates Through Offline Panorama
- Enhanced Authentication for Dedicated Log Collectors and WildFire Appliances
- Syslog Forwarding Using Ethernet Interfaces
- Increased Configuration Size for Panorama
- Access Domain Enhancements for Multi-Tenancy
- Enhanced Performance for Panorama Query and Reporting
- Log Query Debugging
- Configurable Key Limits in Scheduled Reports
- Multiple Plugin Support for Panorama
End-of-Life (EoL)
X-Forwarded-For HTTP Header Data Support in Policy
Learn more about how to use X-Forwarded-For IP addresses
in security policy.
The Palo Alto Networks NGFW can now read the
XFF field and use the XFF IP address when enforcing security policy. Additionally,
you can configure various logs and reports to display the XFF IP
address along with the source IP address.
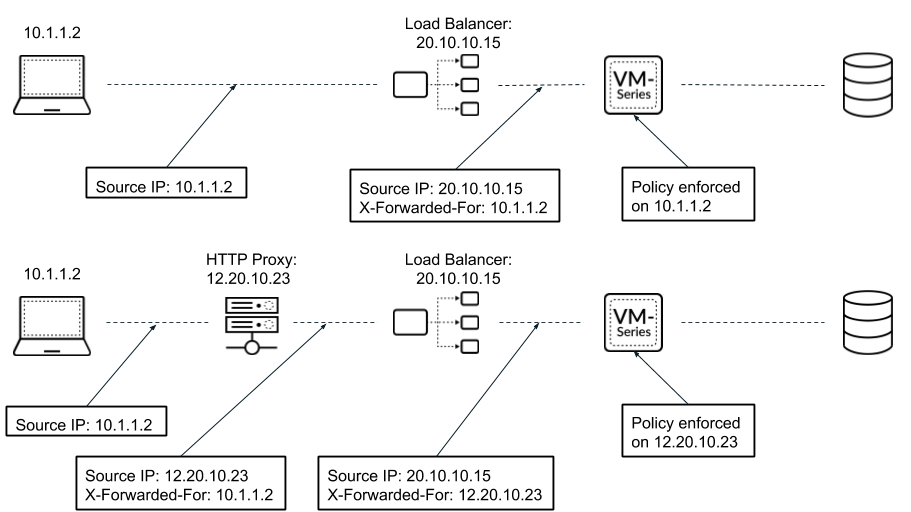
When a endpoint
attempts to access a network resource, if the packet passes through
an upstream device like an explicit HTTP proxy or load balancer,
the endpoint’s IP address is masked and replaced with the IP address
of the upstream device. When an IP address is replaced by a proxy’s
IP address, the IP address of the previous device is placed in the X-Forwarded-For
(XFF) field of the HTTP header. If the packet passes through a single
proxy server before reaching the firewall, the XFF field contains
the IP address of the originating endpoint and the firewall can
use that IP address to enforce security policy. However, if the
packet passes through multiple upstream devices, the firewall uses
the most-recently added IP address to enforce policy or use other
features that rely on IP information.