URL Filtering Inline ML
Table of Contents
10.0 (EoL)
Expand all | Collapse all
-
- Automatic Content Updates Through Offline Panorama
- Enhanced Authentication for Dedicated Log Collectors and WildFire Appliances
- Syslog Forwarding Using Ethernet Interfaces
- Increased Configuration Size for Panorama
- Access Domain Enhancements for Multi-Tenancy
- Enhanced Performance for Panorama Query and Reporting
- Log Query Debugging
- Configurable Key Limits in Scheduled Reports
- Multiple Plugin Support for Panorama
End-of-Life (EoL)
URL Filtering Inline ML
URL Filtering inline ML prevents malicious content in
real-time using machine learning on the firewall.
You can now prevent malicious variants of
JavaScript exploits and phishing attacks embedded in webpages from
entering your network using machine learning (ML) on the firewall
dataplane. URL filtering inline ML dynamically
analyzes and detects malicious contents by evaluating various webpage
details to formulate a high probability classification of a file.
This protection extends to currently unknown as well as future variants
of threats that match characteristics that Palo Alto Networks identified
as malicious.You configure the URL filtering inline ML models through
your URL Filtering profile but this requires a PAN-DB URL Filtering license.
Additionally, you can specify URL exceptions to exclude any false-positives
you encounter, which enables you to create more granular rules in
your profiles to support your specific security needs.
URL
filtering inline ML is not supported on the VM-50 or VM50L virtual
appliance.
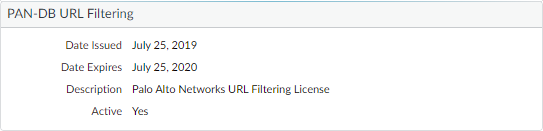
- To take advantage of URL filtering inline ML, you must have an active PAN-DB URL Filtering subscription to analyze webpages for JavaScript and phishing threats.Verify that you have a URL Filtering subscription. To verify subscriptions for which you have currently-active licenses, select DeviceLicenses and verify that the appropriate licenses display and are not expired.
![]() Create a new or update your existing URL Filtering Security profiles to use URL Filtering inline ML.
Create a new or update your existing URL Filtering Security profiles to use URL Filtering inline ML.- Select an existing URL Filtering Profile or Add a new one (ObjectsSecurity ProfilesURL Filtering).
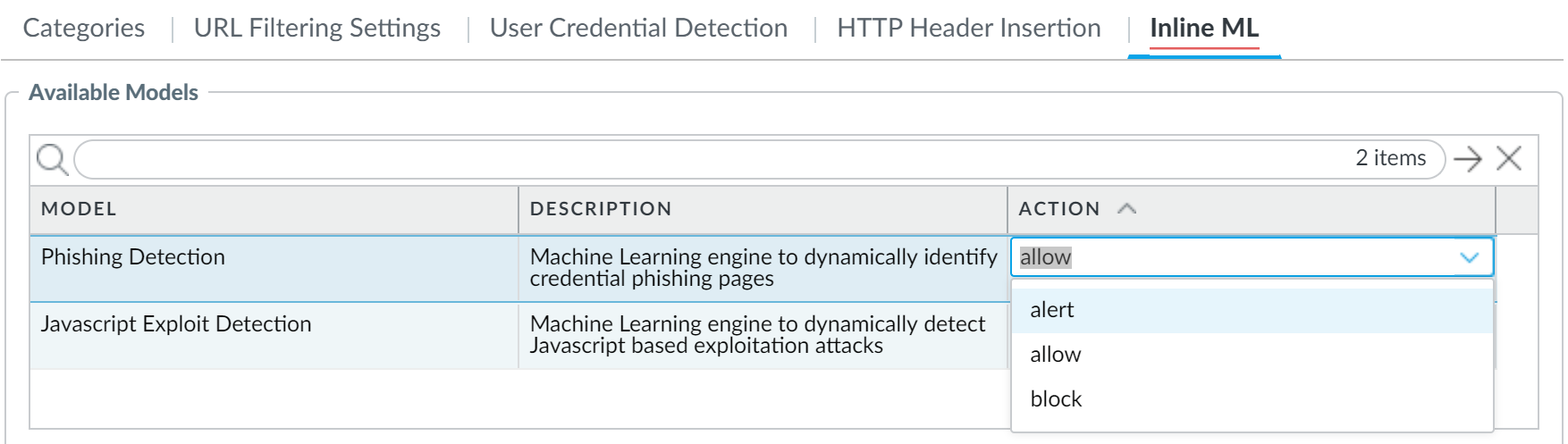
- Select your URL Filtering profile and then go to Inline ML and define a policy Action for each URL Filtering model. There are two URL classification engines: Phishing and JavaScript Exploit, one for each type of malicious webpage content.
- Block—The firewall blocks the website and the user will not be able to continue to the website. The firewall also generates a URL Filtering log entry.
- Alert—The firewall allows access to the website but also generates a URL Filtering log entry.
- Allow—The firewall allows access to the website does not generate a URL Filtering log entry.
![]()
- Click OK to exit the URL Filtering Profile configuration dialog and Commit your changes.
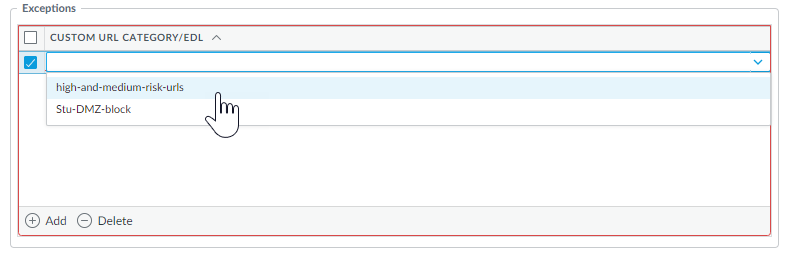
(Optional) Add URL exceptions to your URL Filtering Security profile if you encounter false-positives.- Select Objects > Security Profiles > URL Filtering.
- Add or modify an existing URL Filtering profile from which you want to exclude specific URLs and then select Inline ML.
- Add a pre-existing URL-based external dynamic list. If none are available, create a new external dynamic list.
![]()
- Click OK to save the URL Filtering profile and Commit your changes.
(Optional) See Configure URL Filtering Inline ML for information about testing your firewall’s connection to the inline ML cloud service and viewing related logs.