Network Security
Enforce Security Rule Description, Tag, and Audit Comment
Table of Contents
Expand All
|
Collapse All
Network Security Docs
Enforce Security Rule Description, Tag, and Audit Comment
Require that a description, tag, or audit comment be entered when creating or editing
a security rule.
Enforcing a security rule description, tag, and audit comment policy isn’t
only important for staying compliant with security best practices, but also for
maintaining clarity, organization, and accountability within the Security policy.
These elements provide essential context and information about each rule, aiding in
policy management, troubleshooting, and compliance adherence.
For each policy rule, administrators can add a descriptive rule name
and a detailed description. Rule descriptions are essential for conveying the
purpose and intent of the rule, ensuring that other administrators can quickly
comprehend its function. A well-written description should succinctly articulate the
rule's role and relevance in the Security policy.
Administrators can tag security rules with relevant labels or categories,
making it easier to classify and search for rules based on specific criteria. Tags
help organize the rulebase efficiently, providing a structured approach to rule
management and policy organization.
Enforcing an audit comment for each security rule allows administrators to
document any additional notes, rationale, or comments related to the rule. These
comments can include information about the reasoning behind the rule, compliance
requirements, or any specific considerations that influenced its creation.
Regularly enforcing and updating rule descriptions, tags, and audit
comments is crucial for maintaining a well-organized and documented Security policy.
It enhances collaboration among administrators, streamlines policy management, and
simplifies auditing processes. Additionally, it aids in compliance audits and
demonstrates a disciplined approach to network security and policy enforcement.
For uniformity, you can set specific requirements for what the audit comment can
include.
Enforce Security Rule Description, Tag, and Audit Comment (Strata Cloud Manager)
Require that a description, tag or audit comment be entered when creating or editing
a security rule.
A comprehensive set of Security
checks that are used to evaluate your configuration. Your configuration is
compared against these checks to assess the security posture of your devices and to
generate security alerts automatically when a rule doesn't adhere to best practices.
In addition to the predefined best practice checks, you can create your own custom
checks to cover any special requirements you may have. You can:
- Set the severity level for your custom checks to identify the checks that are the most critical to your deployment.
- Create and delete your own custom checks, clone existing checks and edit them to create new ones, and make special exceptions for checks you don't want applied to portions of your deployment.
- Set the response when a check fails.
- Alert (default)—Raises an alert for the failed check.
- Block—Stop potential misconfigurations before they enter your deployment. Here's what block means for your deployment depending on how you manage it:
- Inline Checks on Cloud Manager—Prevents you from committing or pushing a noncompliant configuration, but won't prevent you from saving your configuration locally.
- Real-Time Inline Checks on Cloud Manager—Prevents you from even saving a noncompliant configuration.
- Panorama Managed—Prevents you from committing a noncompliant configuration to Panorama, but won't prevent you from saving it to the Panorama candidate configuration.
- PAN-OS web interface, API, or CLI management—Block has no enforcement effect on configurations that are not either Cloud managed or Panorama managed.
Enforce Security Rule Description, Tag, and Audit Comment (PAN-OS & Panorama)
Require that a description, tag, or audit comment be entered when creating or editing
a security rule.
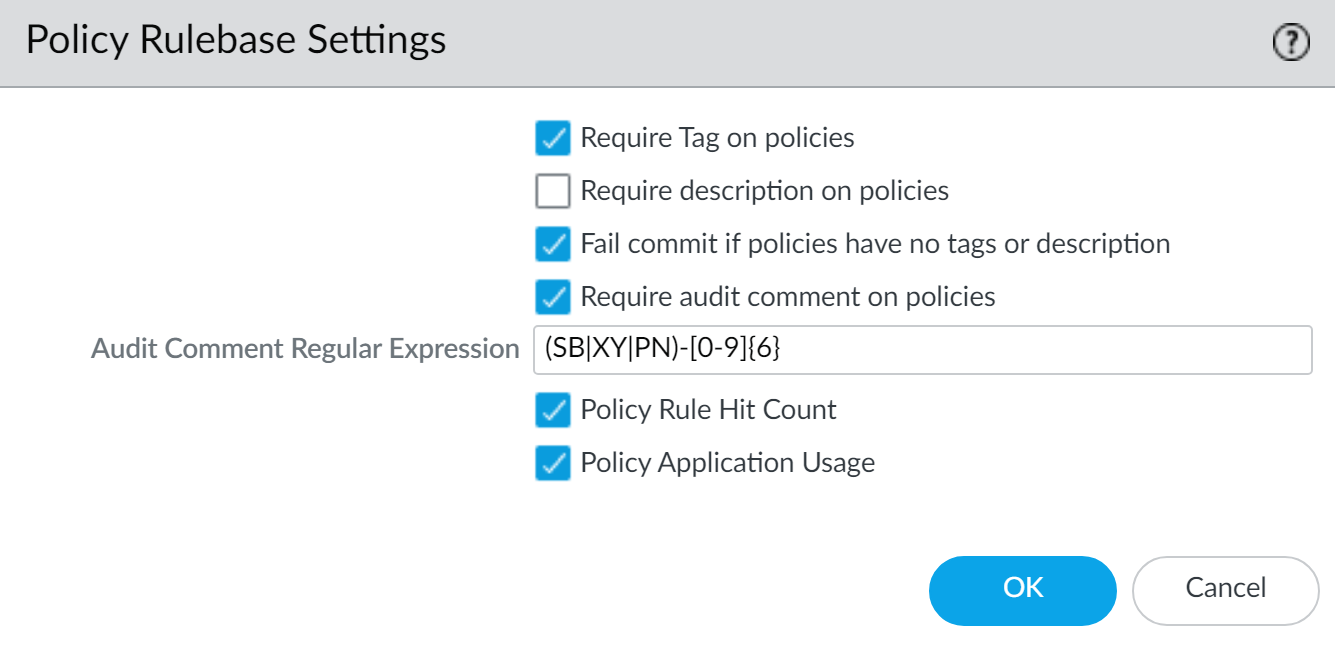
By default, enforcement of a description, tag, and audit comment isn't enabled. You
can specify whether a description, tag, audit comment, or any combination of these
three is required to successfully add or modify a rule. The audit comment archive
allows you to view the audit comments entered for a selected rule, review the
configuration log history, and compare rule configuration versions.
- Launch the Web Interface.Select DeviceSetupManagement and edit the Policy Rulebase Settings.Configure the settings you want to enforce. In this example, tags and audit comments are required for all policies.Enforce audit comments for security rules to capture the reason an administrator creates or modifies a rule. Requiring audit comments on security rules helps maintain an accurate rule history for auditing purposes.Configure the Audit Comment Regular Expression to specify the audit comment format.When administrators create or modify a rule, you can require they enter a comment those audit comments adhere to a specific format that fits your business and auditing needs by specifying letter and number expressions. For example, you can use this setting to specify regular expressions that match your ticketing number formats:
- [0-9]{<Number of digits>}—Requires the audit comment to contain a minimum number of digits that range from 0 to 9. For example, [0-9]{6} requires a minimum of six digits in a numerical expression with numbers 0 to 9.
- <Letter Expression>—Requires the audit comment to contain a letter expression. For example, Reason for Change- requires that the administrator begin the audit comment with this letter expression.
- <Letter Expression>-[0-9]{<Number of digits>}—Requires the audit comment to contain a predetermined character followed by a minimum number of digits that range from 0 to 9. For example, SB-[0-9]{6} requires the audit comment format to begin with SB-, followed by a minimum six digits in a numerical expression with values from 0 to 9. For example, SB-012345.
- (<Letter Expression>)|(<Letter Expression>)|(<Letter Expression>)|-[0-9]{<Number of digits>}—Requires the audit comment to contain a prefix using any one of the predetermined letter expressions with a minimum number of digits that range from 0 to 9. For example, (SB|XY|PN)-[0-9]{6} requires the audit comment format to begin with SB-, XY-, or PN- followed by a minimum of six digits in a numerical expression with values from 0 to 9. For example, SB-012345, XY-654321, or PN-012543.
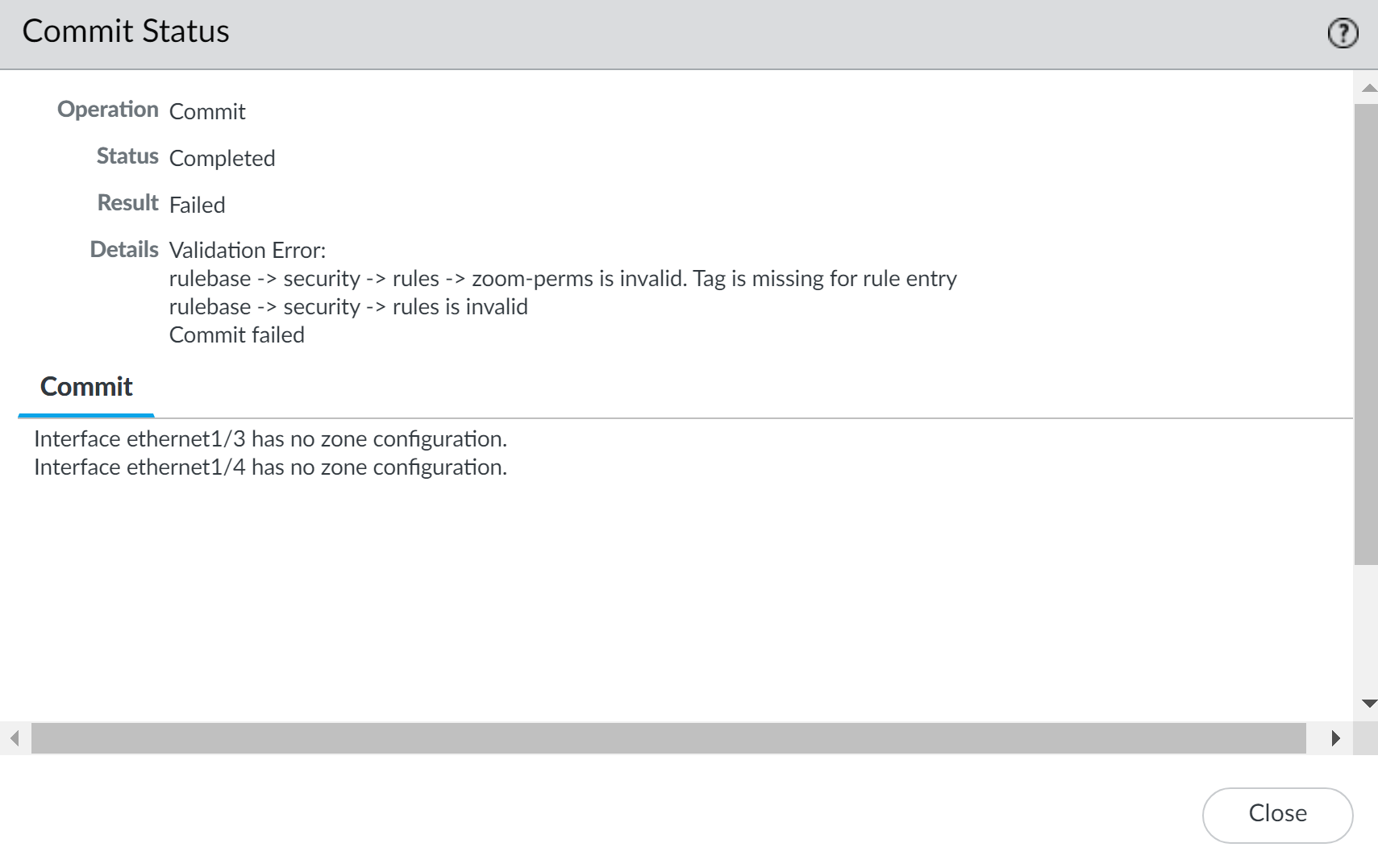
Click OK to apply the new policy rulebase settings.![]() Commit the changes.After you commit the policy rulebase settings changes, modify the existing security rule based on the rulebase settings you decided to enforce.
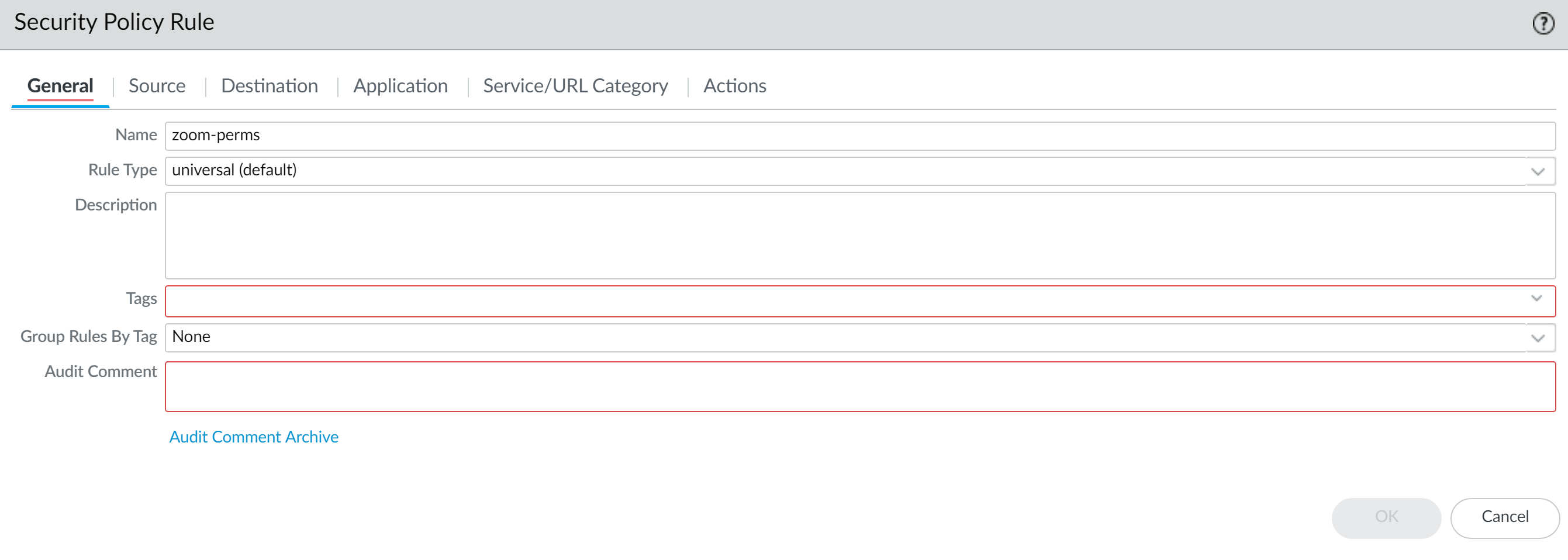
Commit the changes.After you commit the policy rulebase settings changes, modify the existing security rule based on the rulebase settings you decided to enforce.![]() Verify that the firewall is enforcing the new policy rulebase settings.
Verify that the firewall is enforcing the new policy rulebase settings.- Select Policies and Add a new rule.Confirm that you must add a tag and enter an audit comment click OK.
![]()