IoT Security Policy Rule Recommendation Enhancements
Table of Contents
11.0 (EoL)
Expand all | Collapse all
End-of-Life (EoL)
IoT Security Policy Rule Recommendation Enhancements
PAN-OS® provides improved management and scaling
of policy rule recommendations from IoT Security.
One of the benefits of integrating IoT Security
with next-generation firewalls is the automatic creation of Security
policy rules to extend the framework of zero-trust and least-privilege
access to IoT devices. Instead of figuring out the types of traffic
that each IoT device generates and their destinations on your own,
you simply let IoT Security use AI and machine learning to do it
for you and create a set of policy rule recommendations based on
observed network behaviors. You can then keep the set of recommended
rules as is or change its name and add tags, security profiles,
and source and destination zones as you like. When done, activate
the policy rules set and let IoT Security automatically push it
to Panorama or directly to your firewalls. It’s then up to you to
select which rules you want to enforce and import them into your
policy rulebase. In this release, it’s easier than ever to manage
and scale policy rule recommendations from IoT Security thanks to
the following enhancements:
- IoT Security automatically pushes only rule recommendations that you’ve activated in IoT Security to Panorama and next-generation firewalls.
- Policy rule names are automatically generated through a concatenation of the policy set name and application name.
- You can import multiple rules from the policy recommendation database in Panorama to multiple device groups. From the Panorama web interface, you can also remove the mapping between multiple rules in the rulebase and the policy recommendation database.
- You can import multiple rules from the policy recommendation database on an individual firewall into your policy rulebase. From the PAN-OS® web interface, you can also remove the mapping between multiple rules in the rulebase and the policy recommendations database.
The
following section describes policy recommendation enhancements in
more detail.
- Activated Policy Rule Sets Get Pushed AutomaticallyAlthough IoT Security allows you to create multiple policy rule sets for a device profile, you can only activate one at a time. When you activate a policy set in IoT Security, IoT Security automatically pushes it to Panorama and all next-generation firewalls subscribed to the IoT Security service. Because Panorama and firewalls have only activated policy sets, the Activate Recommendation column no longer appears on PanoramaPolicy RecommendationIoT in Panorama nor on DevicePolicy RecommendationIoT in the PAN-OS web interface.Automatically Generated Rule NamesWhen you create a policy rule set in IoT Security, IoT Security assigns it a default name. You can either keep the default name or change it to something else.
![]() When you activate the policy set and IoT Security automatically pushes it to Panorama and your next-generation firewalls, it generates policy rule names by concatenating the policy set name with the name of the application in each rule. These names appear in the Policy Rule Name column on PanoramaPolicy RecommendationIoT in Panorama and on DevicePolicy RecommendationIoT in the PAN-OS web interface.Import Multiple Rules into Multiple Device GroupsThe ability to import policy rules into multiple firewall rulebases in multiple device groups can save you a lot of time. From this release, Panorama lets you do just that. You can now import one or more recommended policy rules—up to a maximum of ten at a time—into the rulebase of firewalls in one or more device groups.
When you activate the policy set and IoT Security automatically pushes it to Panorama and your next-generation firewalls, it generates policy rule names by concatenating the policy set name with the name of the application in each rule. These names appear in the Policy Rule Name column on PanoramaPolicy RecommendationIoT in Panorama and on DevicePolicy RecommendationIoT in the PAN-OS web interface.Import Multiple Rules into Multiple Device GroupsThe ability to import policy rules into multiple firewall rulebases in multiple device groups can save you a lot of time. From this release, Panorama lets you do just that. You can now import one or more recommended policy rules—up to a maximum of ten at a time—into the rulebase of firewalls in one or more device groups.- In Panorama, select PanoramaPolicy RecommendationIoT, select up to ten policy rules to import and then Import Policy Rule(s).
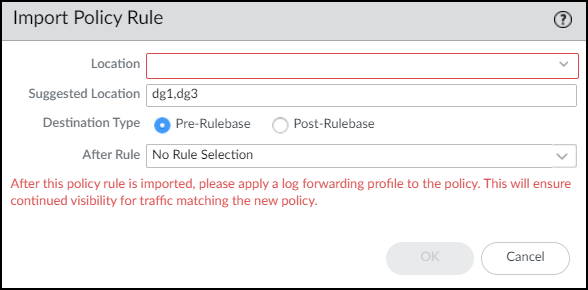
- In the Import Policy Rule dialog box that appears, enter the following, and then click OK:
- Location: Choose one or more device groups.
- Suggested Location: IoT Security learns about zones and device groups in the logs it receives from next-generation firewalls and suggests device groups for various policy rules accordingly. You can choose these suggested device groups among those available in the Location list or any other device groups if you prefer.
- Destination Type: Select either Pre-Rulebase to add the recommended policy rules before rules defined locally on a firewall or Post-Rulebase to add them after rules defined locally.
- After Rule: Choose a rule after which you want to add the imported rule or rules. If you choose No Rule Selection, the firewall imports the selected rules to the top. This is an optional setting. If you don’t choose a rule, the imported rules are added to the top of the rulebase.
![]()
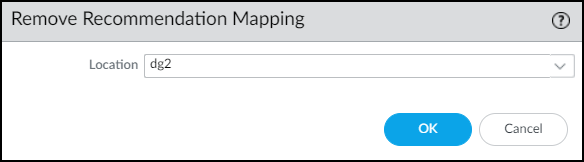
- To remove the mapping between rules in the policy rulebase and their counterparts in the policy recommendation database, select PanoramaPolicy RecommendationIoT, select up to ten rules that have already been imported, and then Remove Policy Mapping.
- Indicate a device group from which you want to remove the policy mapping and then confirm the removal. Repeat this if you want to remove the mapping from any other device groups.
![]()
- After confirming the policy mapping removal, you can then manually delete up to ten rules at a time from the rulebase in each device group on PoliciesDevice Group <name>.
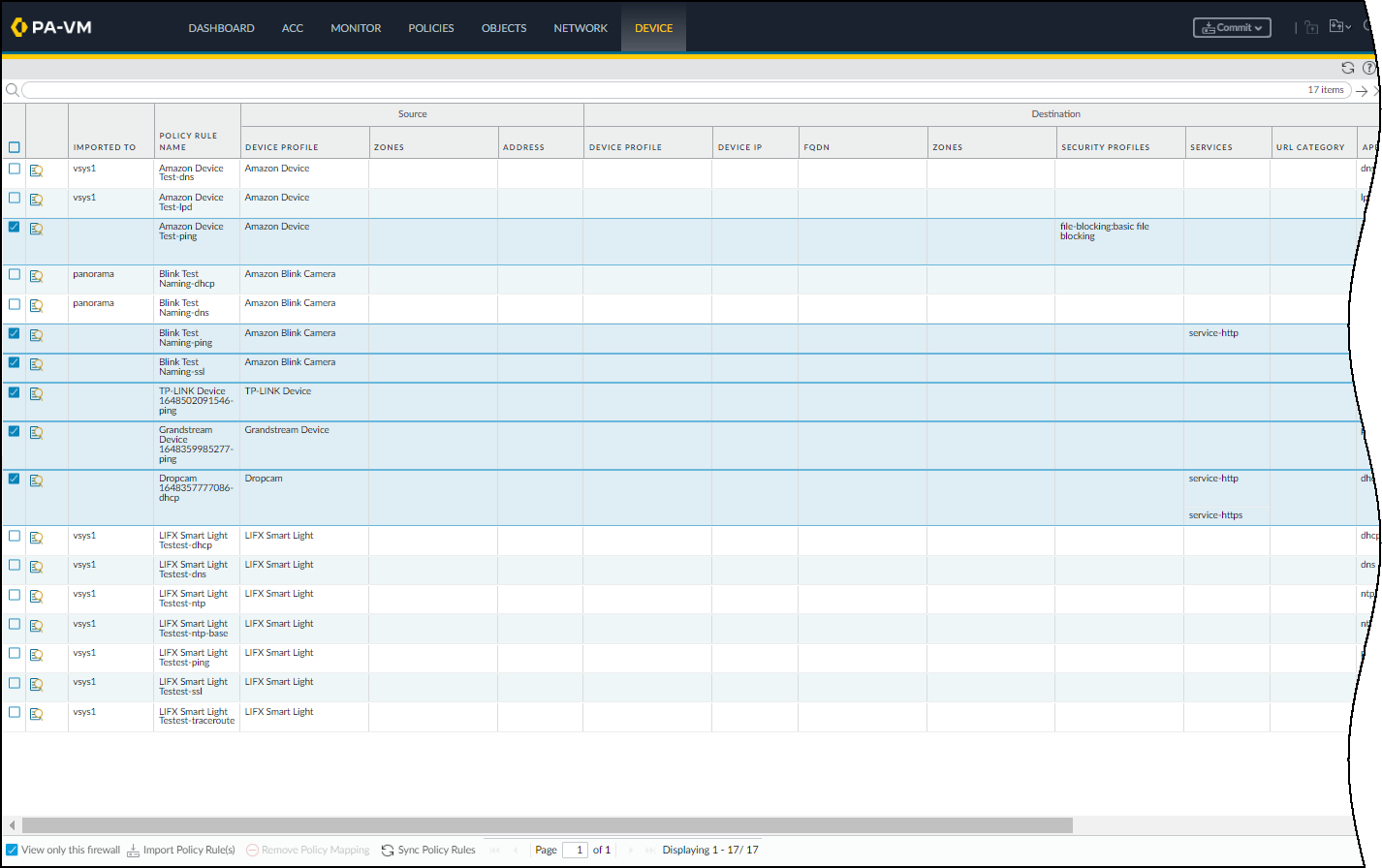
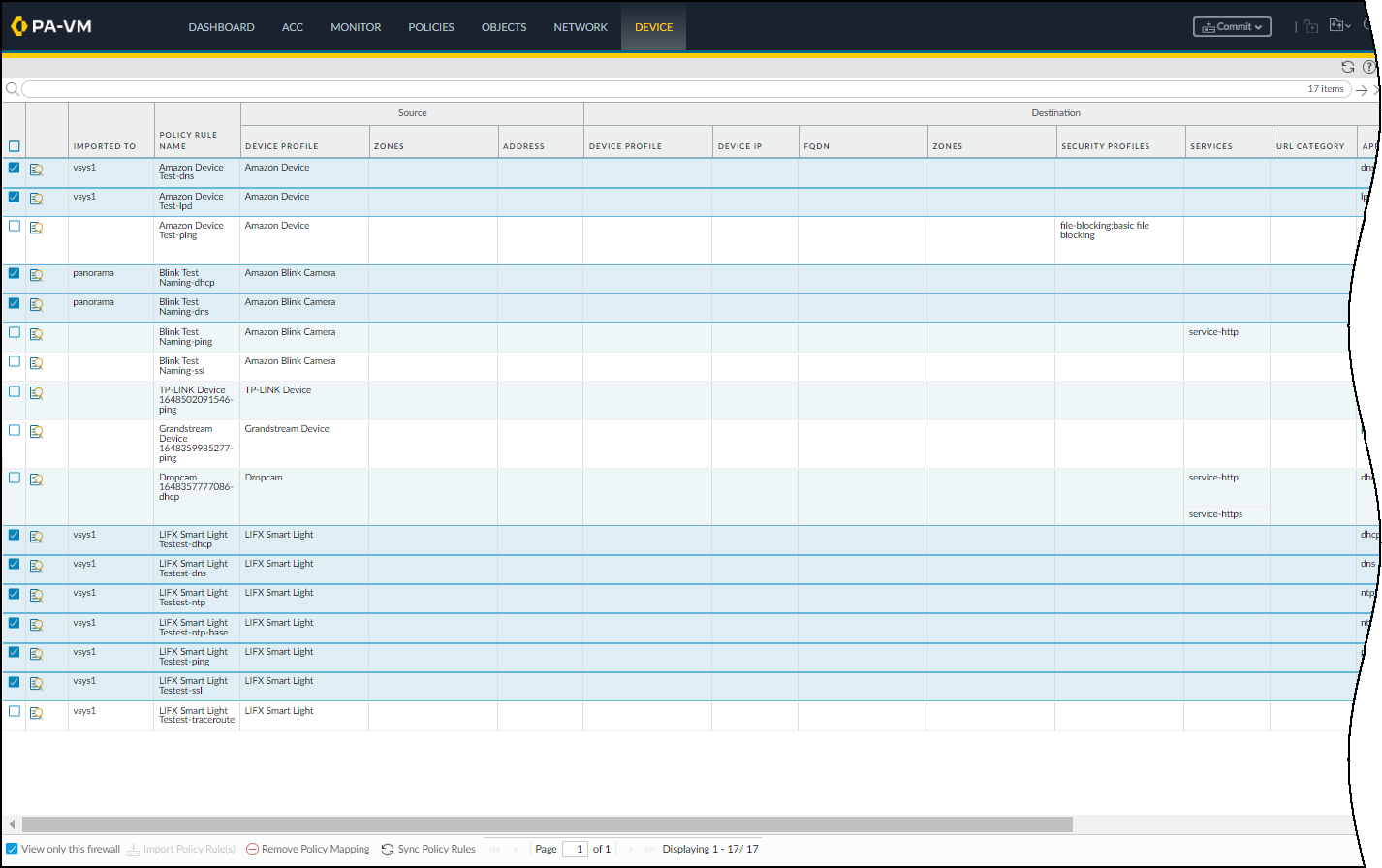
Import Multiple Rules in Individual Firewalls- To import multiple rules at a time into the policy rulebase in the PAN-OS web interface on a single next-generation firewall, select DevicePolicy RecommendationIoT, select up to ten rules that have not already been imported, and then Import Policy Rule(s).
![]()
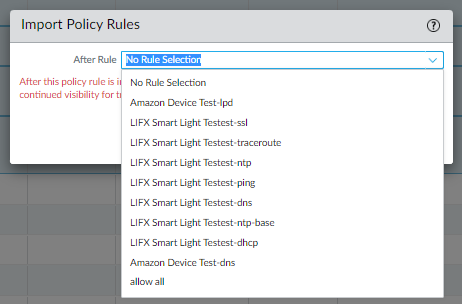
- Choose the name of a rule in the rulebase after which you want PAN-OS to place the imported rules. If you choose No Rule Selection, the firewall imports the selected rules to the top.
![]()
Remove Mappings between Imported Rules and Recommendations- To remove the mapping between rules in the policy rulebase and their counterparts in the policy recommendation database, select DevicePolicy RecommendationIoT, select up to ten rules that have already been imported, and then Remove Policy Mapping.
![]()
- After confirming the policy mapping removal, you can then manually delete the rules from the rulebase.