Next-Generation Firewall
Prepare to Deploy App-ID Cloud Engine
Table of Contents
Expand All
|
Collapse All
Next-Generation Firewall Docs
-
-
-
-
-
-
-
- PAN-OS 12.1
- PAN-OS 11.2
- PAN-OS 11.1
- PAN-OS 11.0 (EoL)
- PAN-OS 10.2
- PAN-OS 10.1
- PAN-OS 10.0 (EoL)
- PAN-OS 9.1 (EoL)
- PAN-OS 9.0 (EoL)
- PAN-OS 8.1 (EoL)
-
- PAN-OS 12.1
- PAN-OS 11.2
- PAN-OS 11.1
- PAN-OS 10.2
- PAN-OS 10.1
Prepare to Deploy App-ID Cloud Engine
Prerequisites to setting up and deploying the App-ID
Cloud Engine (ACE).
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
There are several prerequisite onboarding
tasks to do before the firewall can use the App-ID Cloud Engine
(ACE). You can deploy ACE on standalone firewalls or use Panorama
to deploy ACE on managed firewalls.
Before a firewall can
use ACE to provide specific App-IDs for traffic previously identified
as ssl or web-browsing traffic, the PAN-OS administrator and the
SaaS Security administrator must work together to:
- Install a valid device certificate on each appliance that will use ACE, including Panorama appliances that manage ACE firewalls. (PAN-OS administrator.)
- (Explicit Proxy Deployments [requires PAN-OS 11.2.3 and later or PAN-OS 11.1.5 and later]) Enable firewalls using a proxy server to access servers that facilitate requests generated by various features using inline cloud services.
- Activate SaaS Security Inline on each firewall that will use ACE. Panorama doesn’t require a license. (SaaS Security administrator.)
- Configure a service route for communication between the firewall and ACE. (PAN-OS administrator.)
- Enable ACE on Panorama appliances which manage firewalls that will use ACE. (PAN-OS administrator.)On firewalls, ACE is enabled by default after activating SaaS Security Inline.
- Create Security policy rule that allows ACE traffic. (PAN-OS administrator.)
- Configure Log Forwarding from the firewall to the Strata Logging Service. (PAN-OS administrator.)
At
the appropriate step in the following procedure, the PAN-OS administrator
should notify the SaaS Security administrator that the deployment
is ready for SaaS Security Inline activation. After activating SaaS
Security Inline, the SaaS Security Inline administrator should notify the
PAN-OS administrator that the deployment is ready to complete on
the PAN-OS devices. Communication between the administrators is
essential to achieving a smooth deployment.
Requirements:
- Standalone firewalls, Panorama appliances, and managed firewalls must run PAN-OS 11.1 or later.
- All ACE firewalls must have purchased a SaaS Security Inline license. Panorama does not require a license to manage ACE firewalls or push ACE configurations to managed firewalls.
- All ACE appliances must be able to connect to the US, APAC, or EU GCP region, depending on your location (the region is selected automatically based on your Strata Logging Service region).Verify that the firewall uses the correct Content Cloud FQDN (DeviceSetupContent-IDContent Cloud Setting) for your region and change the FQDN if necessary:
- US—hawkeye.services-edge.paloaltonetworks.com
- EU—eu.hawkeye.services-edge.paloaltonetworks.com
- APAC—apac.hawkeye.services-edge.paloaltonetworks.com
ACE data, including traffic payloads, is sent to the servers in the selected region. If you specify a Content Cloud FQDN that is outside of your region (for example, if you are in the EU region but you specify the APAC region FQDN), you may violate your country’s or your organization’s privacy and legal regulations.
The
PAN-OS administrator completes the first two steps of the procedure
and then hands it off to the SaaS Security Inline administrator
for activation (Step 3). After
activation, the SaaS Security Inline administrator hands the rest
of the procedure back to the PAN-OS administrator to complete on
the PAN-OS devices.
- Bring the firewall and Panorama (if using) online. (PAN-OS administrator.)Install device certificates on Panorama (if you use Panorama) and on individual firewalls so that they can use cloud services. (PAN-OS administrator.)
- Install a device certificate on individual firewalls (if not managed by Panorama)
Hand off the next step to the SaaS Security administrator.Activate SaaS Security Inline on every firewall that will use ACE. Activation enables ACE on the firewalls. (SaaS Security administrator.)Panorama does not require a SaaS Security Inline license to manage firewalls that use ACE. Only managed firewalls need licenses, which you must retrieve manually as shown in the next step.Hand off the rest of the steps to the PAN-OS administrator.Retrieve the SaaS Security Inline license on each firewall—Panorama doesn’t need a license—and verify that it is activated. (PAN-OS administrator.)The SaaS Security administrator’s activation sets up the licenses for the firewall, so you don’t have to go to the Customer Support Portal or obtain Auth Codes.- Go to DeviceLicensesLicense Management and select Retrieve license keys from license server to retrieve the license.Check DeviceLicenses to ensure that the SaaS Security Inline license is active.(Required when the firewall is deployed with an explicit proxy server) Configure the proxy server used to access the servers that facilitate requests generated by various features using inline cloud services. A single proxy server can be specified and applies to all Palo Alto Networks inline cloud services, including all configured inline cloud analysis and logging services.
- (PAN-OS 11.2.3 and later) Configure the proxy server through PAN-OS.
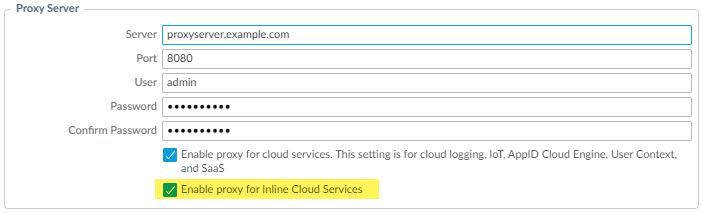
- Select Device Setup Services and edit the Services details.
- Specify the Proxy Server settings and Enable proxy for Inline Cloud Services. You can provide either an IP address or FQDN in the Server field.The proxy server password must contain a minimum of seven characters.
![]()
- Click OK.
(PAN-OS 11.1.5 and later) Configure the proxy server through the firewall CLI.- Configure the base proxy server settings using the following CLI commands:
set deviceconfig system secure-proxy-server <FQDN_or_IP> set deviceconfig system secure-proxy-port <1-65535> set deviceconfig system secure-proxy-user <value> set deviceconfig system secure-proxy-password <value>
The proxy server password must contain a minimum of seven characters. - Enable the proxy server to send requests to the inline cloud service servers using the following CLI command:
debug dataplane mica set inline-cloud-proxy enable
- View the current operational status of proxy support for inline cloud services using the following CLI command:
debug dataplane mica show inline-cloud-proxy
For example:debug dataplane mica show inline-cloud-proxy Proxy for Advanced Services is Disabled
Configure a data services (dataplane) service route so that the firewall can communicate with the App-ID Cloud Engine. (PAN-OS administrator.)You can push this configuration to managed firewalls from Panorama. Both Panorama and the managed firewalls must run PAN-OS 11.1 or later.By default, the firewall uses the management interface as the source interface for the data services service route, but it is recommended that you configure a dataplane interface that has connectivity to cloud services as the Source Interface and Source Address for data services, as shown later in this step.The issue on firewalls is that if an explicit proxy is configured on the management interface and you use it for the data services service route, then the management interface can only connect to the Knowledge Cloud Service (KCS), which manages the cloud application and signatures. When an explicit proxy is configured on the management interface, it cannot connect to the Detection Cloud Service (DCS), which checks the application payload against existing ACE App-IDs and provides verdicts. KCS and DCS are services in the ACE cloud. If the management interface has an explicit proxy configured, you can’t use it for the data services service route for ACE because it can’t connect to all of the services. In this case, you must use a dataplane interface on the firewall to connect to the data services.Panorama uses the management port by default to connect to the KCS and does not connect to the DCS.To configure the service route on a data plane interface instead of using the default management interface:- Select DeviceSetupServices then in Service Features, select Service Route Configuration.Customize a service route.Select the IPv4 protocol.Click Data Services in the Service column to open the Service Route Source dialog box.Select a Source Interface and Source Address (these cannot be the management interface).The source interface must have internet connectivity. The best practice is to use a dataplane interface that has connectivity to cloud services. See Configure Interfaces and Create an Address Object for more information about creating source interfaces and addresses.Click OK to set the source interface and address.Click OK to set the Service Route Configuration.Select PoliciesSecurity and add a Security policy rule that allows traffic from the source interface you specified earlier in this procedure to the FQDN addresses for the KCS and DCS services, which are kcs.ace.tpcloud.paloaltonetworks (KCS service for all regions) and hawkeye.services-edge.paloaltonetworks.com (US region DCS service), eu.hawkeye.services-edge.paloaltonetworks.com (EU region DCS service), or apac.hawkeye.services-edge.paloaltonetworks.com (APAC region DCS service).Also add and allow the following two FQDNs in a new or existing Security policy rule: ocsp.paloaltonetworks.com and crl.paloaltonetworks.com for certificate verification.Finally, add or modify a Security policy rule to allow ACE traffic by allowing the following three applications: paloalto-ace, paloalto-ace-kcs, and paloalto-dlp-service.Make sure that hawkeye.services-edge.paloaltonetworks.com and kcs.ace.tpcloud.paloaltonetworks are reachable on firewalls and that kcs.ace.tpcloud.paloaltonetworks is reachable on Panorama devices. (PAN-OS administrator.)Run the operational command admin@fw1> show cloud-appid connection-to-cloud. The output informs you whether the connection is working and if the license is installed.(Panorama only) Enable ACE on any Panorama appliance that manages ACE-enabled firewalls. (PAN-OS administrator.)ACE is disabled by default on Panorama.If you push ACE configurations to managed groups that do not have ACE-enabled firewalls (some or all firewalls in the group do not have ACE enabled), the push fails.
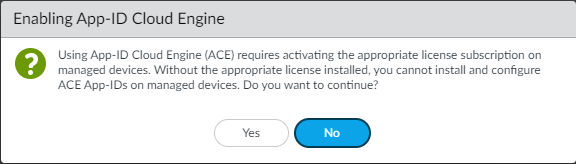
- Navigate to PanoramaSetupACESettings.Click edit () and then de-select Disable App-ID Cloud Engine.
![]() Click OK.The Enable App-ID Cloud Engine dialog appears.
Click OK.The Enable App-ID Cloud Engine dialog appears.![]() Click Yes to enable ACE.Commit the change.Wait for the App-ID catalog to download. (PAN-OS administrator.)There are fewer than four thousand content-provided App-IDs. After you download the ACE catalog, you see many thousands more applications on the firewall and can confirm by checking ObjectsApplications or by using the operational CLI command show cloud-appid cloud-app-data application all to see the new App-IDs.(Panorama only) Push the desired configuration to the managed firewall(s). (PAN-OS administrator.)Configure Log Forwarding to Strata Logging Service and enable Log Forwarding with the correct Log Forwarding profile in Security policy rules. (PAN-OS administrator.)A SaaS Security Inline connection to Strata Logging Service is required for SaaS visibility and to support SaaS App-ID Policy Recommendation. At a minimum, you must forward Traffic logs and URL logs to Strata Logging Service for SaaS Security Inline to work properly.
Click Yes to enable ACE.Commit the change.Wait for the App-ID catalog to download. (PAN-OS administrator.)There are fewer than four thousand content-provided App-IDs. After you download the ACE catalog, you see many thousands more applications on the firewall and can confirm by checking ObjectsApplications or by using the operational CLI command show cloud-appid cloud-app-data application all to see the new App-IDs.(Panorama only) Push the desired configuration to the managed firewall(s). (PAN-OS administrator.)Configure Log Forwarding to Strata Logging Service and enable Log Forwarding with the correct Log Forwarding profile in Security policy rules. (PAN-OS administrator.)A SaaS Security Inline connection to Strata Logging Service is required for SaaS visibility and to support SaaS App-ID Policy Recommendation. At a minimum, you must forward Traffic logs and URL logs to Strata Logging Service for SaaS Security Inline to work properly.