Create a Custom Application Signature
Table of Contents
Expand all | Collapse all
-
- About Custom Application Signatures
- Create a Custom Application Signature
- Create a Custom L3 & L4 Vulnerability Signature
- Import a Custom Threat Signature from Snort and Suricata Rules
- Test a Custom Signature
- Custom Signature Pattern Requirements
- Testing Pattern Performance Impact
-
-
- dhcp-req-chaddr
- dhcp-req-ciaddr
- dhcp-rsp-chaddr
- dhcp-rsp-ciaddr
- dns-req-addition-section
- dns-req-answer-section
- dns-req-authority-section
- dns-req-header
- dns-req-protocol-payload
- dns-req-section
- dns-rsp-addition-section
- dns-rsp-answer-section
- dns-rsp-authority-section
- dns-rsp-header
- dns-rsp-protocol-payload
- dns-rsp-ptr-answer-data
- dns-rsp-queries-section
- email-headers
- file-data
- file-elf-body
- file-flv-body
- file-html-body
- file-java-body
- file-mov-body
- file-office-content
- file-pdf-body
- file-riff-body
- file-swf-body
- file-tiff-body
- file-unknown-body
- ftp-req-params
- ftp-req-protocol-payload
- ftp-rsp-protocol-payload
- ftp-rsp-banner
- ftp-rsp-message
- gdbremote-req-context
- gdbremote-rsp-context
- giop-req-message-body
- giop-rsp-message-body
- h225-payload
- http-req-cookie
- http-req-headers
- http-req-host-header
- http-req-host-ipv4-address-found
- http-req-host-ipv6-address-found
- http-req-message-body
- http-req-mime-form-data
- http-req-ms-subdomain
- http-req-origin-headers
- http-req-params
- http-req-uri
- http-req-uri-path
- http-req-user-agent-header
- http-rsp-headers
- http-rsp-non-2xx-response-body
- http-rsp-reason
- icmp-req-code
- icmp-req-data
- icmp-req-type
- icmp-req-protocol-payload
- icmp-rsp-data
- icmp-rsp-protocol-payload
- icmp-req-possible-custom-payload
- ike-req-headers
- ike-rsp-headers
- ike-req-payload-text
- ike-rsp-payload-text
- imap-req-cmd-line
- imap-req-first-param
- imap-req-params-after-first-param
- imap-req-protocol-payload
- imap-rsp-protocol-payload
- irc-req-params
- irc-req-prefix
- jpeg-file-scan-data
- jpeg-file-segment-data
- jpeg-file-segment-header
- ldap-req-searchrequest-baseobject
- ldap-rsp-searchresentry-objectname
- ms-ds-smb-req-share-name
- ms-ds-smb-req-v1-create-filename
- ms-ds-smb-req-v2-create-filename
- msrpc-req-bind-data
- mssql-db-req-body
- netbios-dg-req-protocol-payload
- netbios-dg-rsp-protocol-payload
- netbios-ns-req-protocol-payload
- netbios-ns-rsp-protocol-payload
- nettcp-req-context
- oracle-req-data-text
- pe-dos-headers
- pe-file-header
- pe-optional-header
- pe-section-header
- pe-body-data
- pop3-req-protocol-payload
- pop3-rsp-protocol-payload
- pre-app-req-data
- pre-app-rsp-data
- rtmp-req-message-body
- rtsp-req-headers
- rtsp-req-uri-path
- sip-req-headers
- snmp-req-community-text
- smtp-req-argument
- smtp-rsp-content
- smtp-req-protocol-payload
- smtp-rsp-protocol-payload
- ssh-req-banner
- ssh-rsp-banner
- ssl-req-certificate
- ssl-req-chello-sni
- ssl-req-client-hello
- ssl-req-protocol-payload
- ssl-req-random-bytes
- ssl-rsp-cert-subjectpublickey
- ssl-rsp-certificate
- ssl-rsp-protocol-payload
- ssl-rsp-server-hello
- tcp-context-free
- telnet-req-client-data
- telnet-rsp-server-data
- udp-context-free
- unknown-req-tcp-payload
- unknown-rsp-tcp-payload
- unknown-req-udp-payload
- unknown-rsp-udp-payload
-
- dnp3-req-func-code
- dnp3-req-object-type
- dns-rsp-tcp-over-dns
- dns-rsp-txt-found
- ftp-req-params-len
- http-req-connect-method
- http-req-content-length
- http-req-cookie-length
- http-req-dst-port
- http-req-header-length
- http-req-param-length
- http-req-no-host-header
- http-req-no-version-string-small-pkt
- http-req-simple-request
- http-req-uri-path-length
- http-req-uri-tilde-count-num
- http-rsp-code
- http-rsp-content-length
- http-rsp-total-headers-len
- iccp-req-func-code
- ike-req-payload-type
- ike-rsp-payload-type
- ike-req-payload-length
- ike-rsp-payload-length
- ike-version
- imap-req-cmd-param-len
- imap-req-first-param-len
- imap-req-param-len-from-second
- irc-req-protocol-payload
- irc-rsp-protocol-payload
- ntlm-req-auth-v1
- ntlm-req-auth-v2
- open-vpn-req-protocol-payload
- pfcp-req-msg-type
- pfcp-rsp-msg-type
- smtp-req-helo-argument-length
- smtp-req-mail-argument-length
- smtp-req-rcpt-argument-length
- sctp-req-ppid
- ssl-req-client-hello-ext-type
- ssl-req-client-hello-missing-sni
- ssl-rsp-version
- stun-req-attr-type
- panav-rsp-zip-compression-ratio
- Context Qualifiers
-
Create a Custom Application Signature
Follow these steps to build a custom application.
To create a custom application signature,
you must do the following:
- Research the application using packet capture and analyzer tools
- Identify patterns in the packet captures
- Build your signature
- Validate your signature
Custom application
signatures require you to specify the Scope—how
your signature is applied to the traffic, Context—the
portion of the file or protocol where you expect to find your pattern,
the Pattern, and the Operator (Pattern
Match for string contexts and Greater Than, Less
Than, or Equal To for integer-based
contexts).
Refer to the Custom Signature Contexts, Defining Applications and Syntax for Regular Expression
Data Patterns while building your signature.
- Research the application using packet capture and/or analyzer tools.
- You should understand how you’d like to control the application before all else. Do you want to limit application functionality? Create a usage report? You’ll want to examine the contents of packet captures to gather context and identify unique characteristics of the application.Consider using a tool such as Wireshark or perform a packet capture on the firewall itself Take a Packet Capture for Unknown Applications.
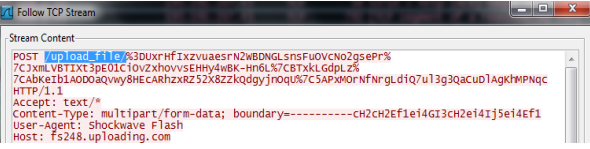
- Perform multiple packet captures between the client system and web server.Generate traffic for various application scenarios once you have launched the capture tool. For example, if you wanted to create a signature for ‘uploading’ on uploading.com, you would upload a file on that site.Multiple sessions might be created for the different actions performed in the application. You will need to locate and inspect each type of session in the resulting packet captures.Inspect packet captures for values or patterns that uniquely identify the application or application function.For example, after you uploaded a file to uploading.com, you would look for HTTP POST request packets in the sessions captured by your packet analyzer tool. Then, you would examine the packet contents for patterns.
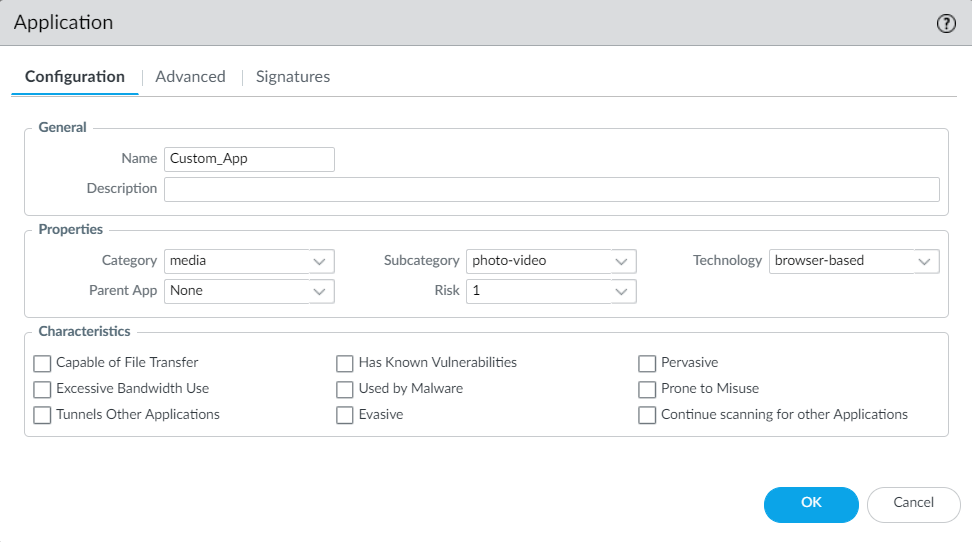
![]() Create the custom application.
Create the custom application.- Select ObjectsApplications and click Add.Under Configuration, enter a name and optional description for the application. Specify the application’s Properties and Characteristics.
- If your custom application has no Parent App that can be identified by regular App-ID or is used in an application override, the application cannot be scanned for threats.
- If the custom application has scanning options unchecked, the threat engine will stop inspecting the traffic as soon as the custom application is identified.
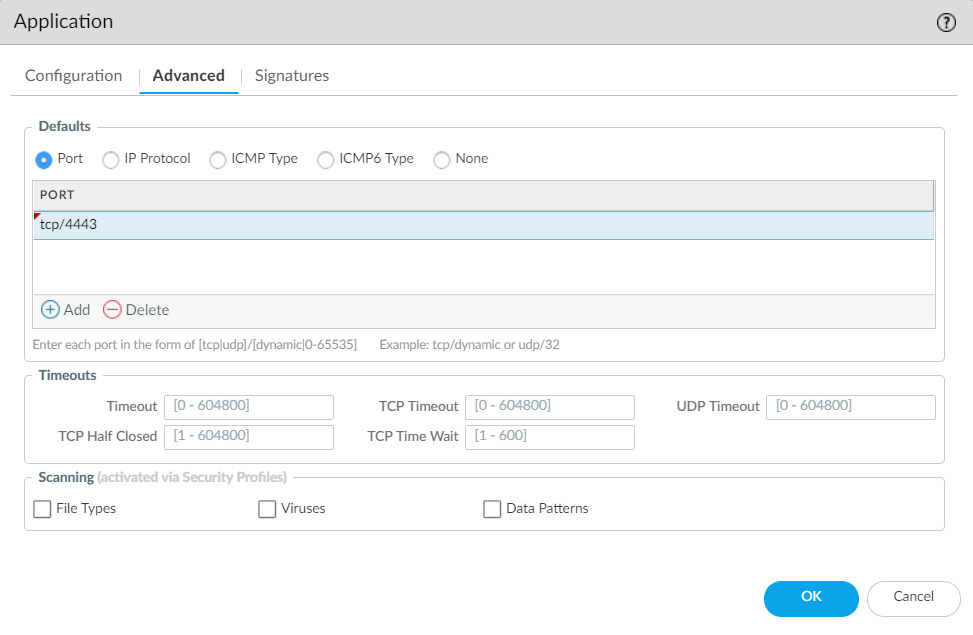
![]() Under Advanced, define settings that will allow the firewall to identify the application protocol:
Under Advanced, define settings that will allow the firewall to identify the application protocol:- Specify the default ports or protocol that the application uses. To specify signatures independent of protocol, select None.
- Specify the session timeout values. If you don’t specify timeout values, the default timeout values will be used.
- Indicate any type of additional scanning you plan to perform on the application traffic.
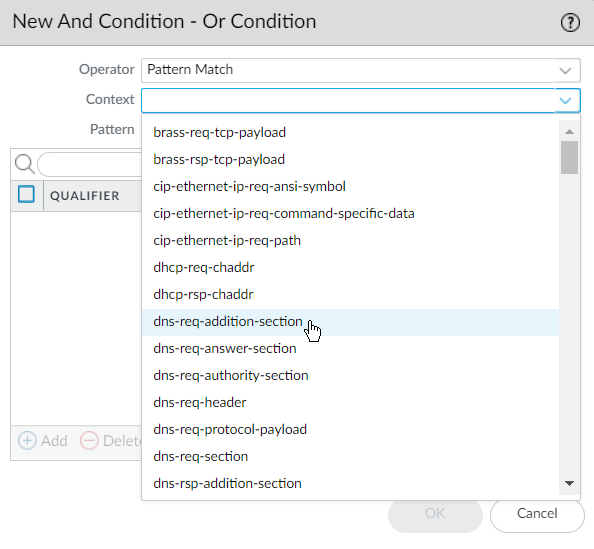
![]() Define your signature.Multiple signatures may be necessary to account for all traffic specific to the application.
Define your signature.Multiple signatures may be necessary to account for all traffic specific to the application.- Under Signatures, click Add and enter a Signature Name and optional description.Specify the Scope—Select between Transaction (e.g. HTTP request and response) or Session (e.g. a single POST request).Specify the matching conditions by clicking Add And Condition or Add Or Condition.Select an Operator to define the conditions that must be true for a signature to match traffic.
- If you select Pattern Match, select a Context and then use a regular expression to specify the Pattern. Optionally, Add a qualifier/value pair.
- Qualifiers are context-dependent and limit the match condition for the given context. For example, you might use the http-method qualifier to specify that a http-req-uri-path only matters if it is found inside an HTTP GET method.
![]()
- If you select Equal To, Less Than, or Greater Than, select an integer Context, and enter a Value.
Repeat sub-steps 3 and 4 for each matching condition.If you leave Ordered Condition Match selected, make sure the condition or group of conditions is in the desired order. The most specific conditions should come first. To order the conditions: Select a condition or a group and click Move Up or Move Down.You cannot move conditions from one group to another.Save the custom signature.- Click OK to save your signature definition.Commit your signature.