Prisma Access Agent
Configure Third-Party Agent Coexistence with Bypass Rules
Table of Contents
Configure Third-Party Agent Coexistence with Bypass Rules
Configure bypass rules in forwarding profiles to enable Prisma Access Agent
coexistence with third-party remote access agents without routing conflicts.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
When you deploy Prisma® Access Agent in environments with existing remote access
solutions, you can configure bypass rules to enable both agents to coexist on an
endpoint. The bypass functionality enables Prisma Access Agent to ignore specific
traffic, enabling third-party agents to handle designated connections while Prisma
Access continues to secure other traffic according to your forwarding profile
rules.
Multiple remote access agents on the same endpoint typically create conflicts when
they attempt to control network routing and DNS resolution simultaneously. These
conflicts manifest as connectivity failures, DNS resolution issues, and routing
table conflicts that can disrupt employee productivity.
You configure bypass rules within Forwarding Profiles using the same interface where
you define tunnel, proxy, direct, and block actions for traffic. When you select
Bypass as the action for specific traffic, Prisma Access
Agent will not intercept or modify those connections, enabling other remote access
solutions to process the bypassed traffic according to their own routing
configurations.
Bypass rules support three traffic handling configurations: both network traffic and
DNS queries, DNS queries only, or network traffic only. When you configure traffic
for bypass, third-party agents process the connections if they are active and
configured to handle the designated traffic. If no third-party agent is present or
configured to handle the traffic, the system sends the traffic to the tunnel (if
present) or directly to its destination if the tunnel is not present. The bypass
functionality maintains consistent behavior regardless of which agent connects
first.
Before configuring bypass rules, ensure that you have:
- Administrative access to Strata Cloud Manager, Panorama, or your firewall management interface
- Configured appropriate rules in the third-party agent to intercept the traffic
- Identification of specific applications, destinations, or traffic types that should be handled by the third-party agent
Follow the instructions to configure bypass rules within Forwarding Profiles in Strata Cloud Manager Managed Prisma Access or Panorama Managed
Prisma Access or NGFW deployments.
Configure Third-Party Agent Coexistence with Bypass Rules (Strata Cloud Manager)
Configure bypass rules in forwarding profiles in Strata Cloud Manager Managed Prisma Access agents to enable
Prisma Access Agent coexistence with third-party remote access agents without routing
conflicts.
To configure bypass rules within Forwarding Profiles in Strata Cloud Manager Managed Prisma Access
deployments:
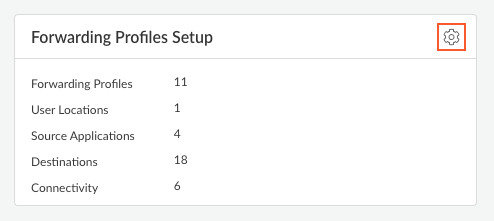
- Navigate to the forwarding profiles setup page:
- Strata Cloud Manager Managed Prisma Access deployments:
- Select ConfigurationNGFW and Prisma AccessConfiguration ScopeMobile Users Container.
- Edit the settings in the Forwarding Profiles Setup section.
![]()
- Panorama Managed
Prisma Access deployments:
- From the Cloud Services plugin in Panorama, select PanoramaCloud ServicesPrisma Access AgentLaunch Prisma Access Agent.
- Select ConfigurationForwarding Profiles
- Panorama Managed
NGFW deployments:
- Log in to Strata Cloud Manager as the administrator.
- Select ConfigurationForwarding Profiles
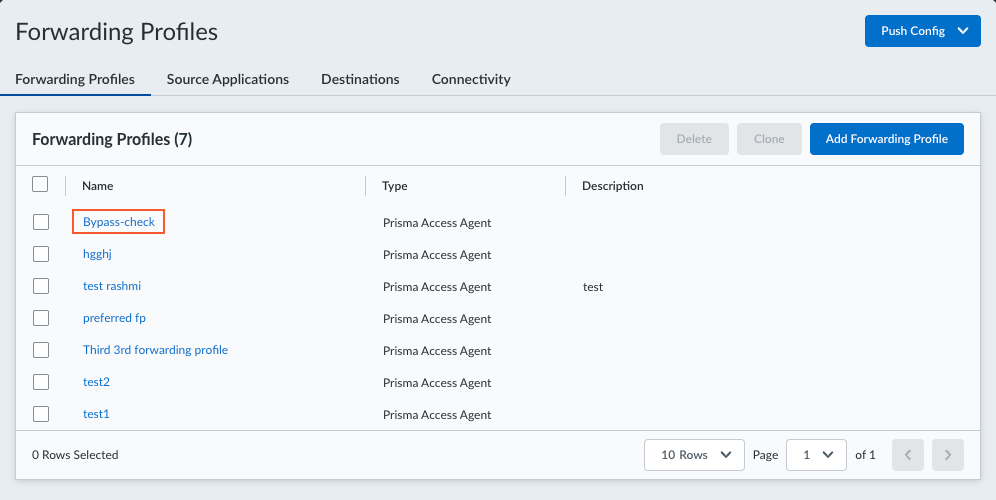
Set up the Source Applications or Destinations for which you need to bypass traffic.For example, you can specify a Destination for a domain you want to bypass, or specify the IP addresses for the applications you want to bypass. You can also set up specific Source Applications that you want to bypass.Configure a forwarding profile where you want to specify bypass rules.- Select an existing forwarding profile you want to modify or add a forwarding profile.For example:
![]() In the Forwarding Rules section, select an existing forwarding rule or Add a forwarding rule for the source application or destination you want to bypass.
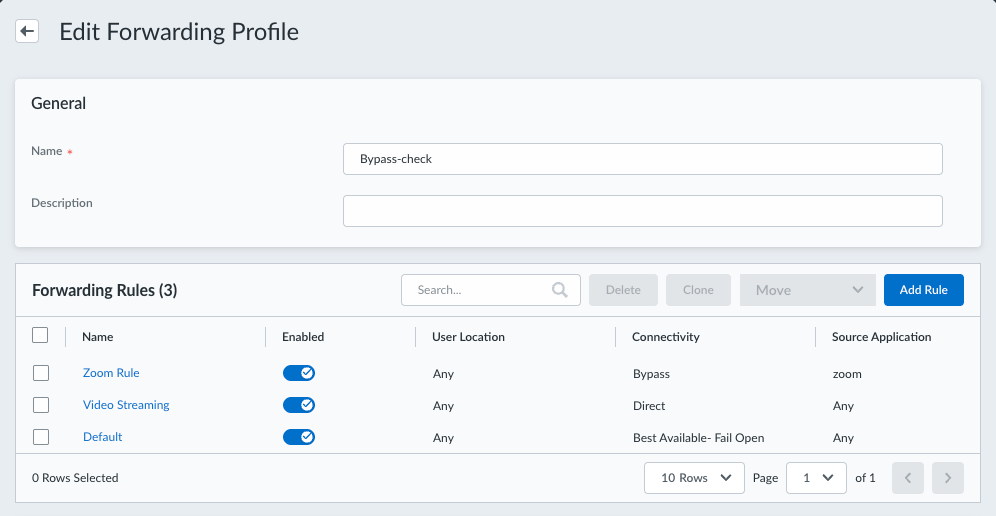
In the Forwarding Rules section, select an existing forwarding rule or Add a forwarding rule for the source application or destination you want to bypass.![]() Specify the properties for the forwarding rule:
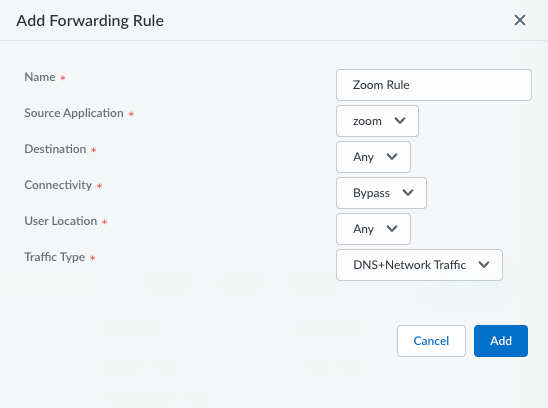
Specify the properties for the forwarding rule:- Enable the forwarding rule.
- Enter a meaningful Name for the rule.
- Select the Source Application and
Destination that you want to
bypass.For example, you can bypass Any applications in the lab destination.Prisma Access Agent cannot steer UDP traffic based on destination criteria on Windows endpoints. Any rule that uses the Destination object will not apply to UDP traffic on Windows endpoints.
- Select ConnectivityBypass.
- Select the Traffic Type to bypass (DNS, DNS + Network Traffic, or Network Traffic).
- Update the forwarding rule.
![]() Set the rule priority to ensure bypass rules are evaluated in the correct order relative to other forwarding rules. You can select a forwarding rule and move it up or down in the Forwarding Rules table.Select a Traffic Enforcement option if needed.Save your forwarding profile settings.Push the configuration to deploy the bypass rules to your Prisma Access Agent deployment.Verify that bypass rules are working correctly on an endpoint.
Set the rule priority to ensure bypass rules are evaluated in the correct order relative to other forwarding rules. You can select a forwarding rule and move it up or down in the Forwarding Rules table.Select a Traffic Enforcement option if needed.Save your forwarding profile settings.Push the configuration to deploy the bypass rules to your Prisma Access Agent deployment.Verify that bypass rules are working correctly on an endpoint.Configure Third-Party Agent Coexistence with Bypass Rules (Panorama)
Configure bypass rules in forwarding profiles in Panorama Managed deployments to enable Prisma Access Agent coexistence with third-party remote access agents without routing conflicts.To configure bypass rules within Forwarding Profiles in Panorama Managed deployments:- Navigate to the forwarding profiles setup page:
- Panorama Managed
Prisma Access deployments:
- From the Cloud Services plugin in Panorama, select PanoramaCloud ServicesPrisma Access AgentLaunch Prisma Access Agent.
- Select ConfigurationForwarding Profiles
- Panorama Managed NGFW deployments:
- Log in to Strata Cloud Manager as the administrator.
- Select ConfigurationForwarding Profiles
Set up the Source Applications or Destinations for which you need to bypass traffic.For example, you can specify a Destination for a domain you want to bypass, or specify the IP addresses for the applications you want to bypass. You can also set up specific Source Applications that you want to bypass.Configure a forwarding profile where you want to specify bypass rules.- Select an existing forwarding profile you want to modify or add a forwarding profile.For example:
![]() In the Forwarding Rules section, select an existing forwarding rule or Add a forwarding rule for the source application or destination you want to bypass.
In the Forwarding Rules section, select an existing forwarding rule or Add a forwarding rule for the source application or destination you want to bypass.![]() Specify the properties for the forwarding rule:
Specify the properties for the forwarding rule:- Enter a meaningful Name for the rule.
- Select the Source Application and
Destination that you want to
bypass.For example, you can bypass Any applications in the lab destination.Prisma Access Agent cannot steer UDP traffic based on destination criteria on Windows endpoints. Any rule that uses the Destination object will not apply to UDP traffic on Windows endpoints.
- Select ConnectivityBypass.
- Select the Traffic Type to bypass (DNS, DNS + Network Traffic, or Network Traffic).
- Add or Update the forwarding rule.
For example, the following image shows a forwarding rule with the Bypass connectivity:![]() Set the rule priority to ensure bypass rules are evaluated in the correct order relative to other forwarding rules. You can select a forwarding rule and move it up or down in the Forwarding Rules table.Select a Traffic Enforcement option if needed.Save your forwarding profile settings.Push the configuration to deploy the bypass rules to your Prisma Access Agent deployment.Verify that bypass rules are working correctly on an endpoint.
Set the rule priority to ensure bypass rules are evaluated in the correct order relative to other forwarding rules. You can select a forwarding rule and move it up or down in the Forwarding Rules table.Select a Traffic Enforcement option if needed.Save your forwarding profile settings.Push the configuration to deploy the bypass rules to your Prisma Access Agent deployment.Verify that bypass rules are working correctly on an endpoint.
- Panorama Managed
Prisma Access deployments:
- Strata Cloud Manager Managed Prisma Access deployments: