Prisma Access
App-Based Office 365 Integration with Explicit Proxy (Panorama)
Table of Contents
Expand All
|
Collapse All
Prisma Access Docs
-
- 6.1 Preferred and Innovation
- 6.0 Preferred and Innovation
- 5.2 Preferred and Innovation
- 5.1 Preferred and Innovation
- 5.0 Preferred and Innovation
- 4.2 Preferred
- 4.1 Preferred
- 4.0 Preferred
- 3.2 Preferred and Innovation
- 3.1 Preferred and Innovation
- 3.0 Preferred and Innovation
- 2.2 Preferred
-
-
- 4.0 & Later
- Prisma Access China
-
-
App-Based Office 365 Integration with Explicit Proxy (Panorama)
Prisma Access Explicit Proxy supports the browser-based version of Office 365 (M365),
including Office Online (office.com). Follow these steps to integrate the browser-based version of
Office 365 with Explicit Proxy.
While Explicit Proxy does not support the app-based version of Office 365, you can
follow these guidelines to use Explicit Proxy with
Office 365 app-based policies.
Set up Browser-Based Office 365 Integration with Prisma Access Explicit Proxy
If you use the browser-based version of Office 365, complete the following task
to integrate Office 365 with Explicit Proxy.
- (Optional) if you want to use tenant-based restrictions (restrict access control to Office 365 for only a certain number of tenants), use HTTP header insertion with a Custom URL category to allow specific tenants access to Office 365.Add decryption policies for the URLs that are used for Office 365.
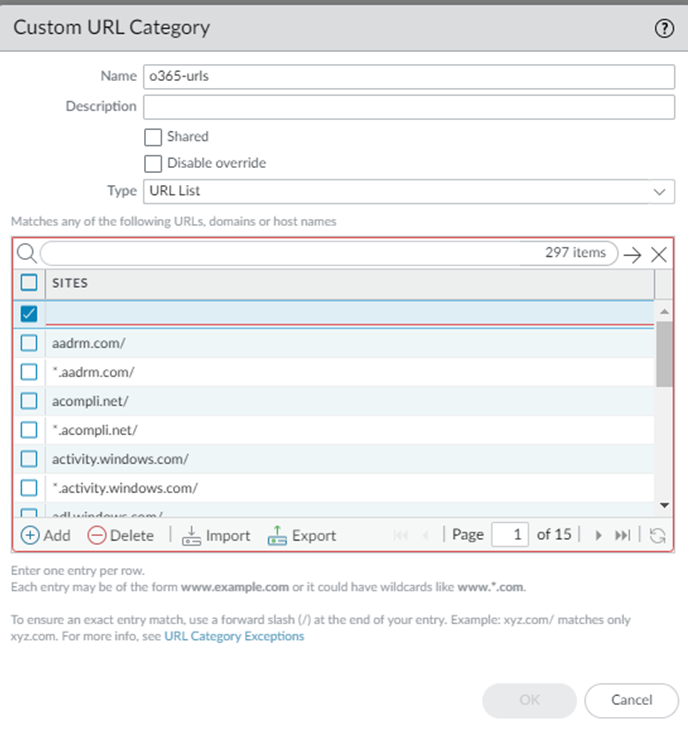
- Select ObjectsCustom ObjectsURL Category and Add a Custom URL Category.Be sure that you are in the Explicit_Proxy_Device_Group.Specify a Type of URL List.Add the list of sites to enable Office 365 integration.To simplify the uploading of the URLs, you can copy the list of Office 365 URLs at https://saasedl.paloaltonetworks.com/feeds/m365/worldwide/any/all/url, save those URLs to a file, and Import the file to the Custom URL category.
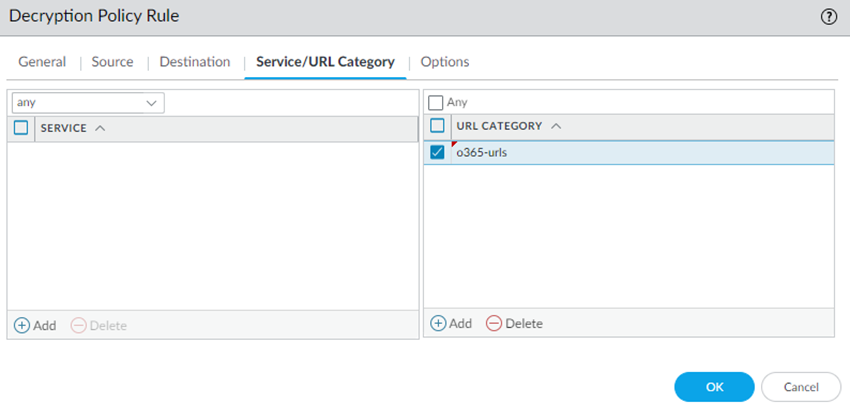
![]() Select PoliciesDecryptionPre Rules and Add a decryption policy rule.Specify the URL Category you created.
Select PoliciesDecryptionPre Rules and Add a decryption policy rule.Specify the URL Category you created.![]() Add decryption policies for Data and Threat Protection capabilities such as Enterprise Data Loss Prevention (Enterprise DLP), WildFire, Threat Prevention, or SaaS Security.
Add decryption policies for Data and Threat Protection capabilities such as Enterprise Data Loss Prevention (Enterprise DLP), WildFire, Threat Prevention, or SaaS Security.Set up App-Based Office 365 Integration with Explicit Proxy
Explicit Proxy does not support the full client-based (app) version of Office 365, because Office 365 uses non-web ports and protocols and pinned certificates, which prevents the use of decryption. If you need to secure traffic from Office 365 client apps, you can use one of the following Prisma Access capabilities to do so:- Deploy a Mobile Users—GlobalProtect deployment with Explicit Proxy and use GlobalProtect split tunnel options to route traffic from the Office 365 apps to the GlobalProtect tunnel, while specifying other internet traffic to be sent to the GlobalProtect tunnel, direct to the internet, or to Explicit Proxy, based on your PAC file and GlobalProtect tunnel include and exclude options.
- If your organization requires that internet-bound traffic go through an Explicit Proxy, or if your network does not have a default route, you can deploy a Remote Network deployment with Explicit ProxyRemote Network deployment with Explicit Proxy. In this deployment, Explicit Proxy provides you with a list of Anycast and unicast addresses, and you configure your CPE to route traffic through those addresses to the remote network and, from there, to Explicit Proxy and to the internet.To use Office 365 with this deployment type, specify PAC file rules to bypass the non-web Office 365 directly to the internet.
- If you are not able to deploy GlobalProtect or a Prisma Access Remote Network in your environment, you can configure the Explicit Proxy PAC file to bypass Office 365 traffic. Use the URL list to bypass.
List of URLs to Enable Office 365 Integration with Prisma Access Explicit Proxy
One option you can use to integrate non-browser Office 365 apps with Explicit Proxy is to specify the Office 365-related URLs and bypass those URLs in the Explicit Proxy PAC file. Use one of the following methods to obtain the list of URLs to bypass:- Use the EDL URL from the Palo Alto Networks EDL Hosting Service for Microsoft 365 apps.Using the hosting service eases the operational burden of securing traffic to your SaaS applications by utilizing a Feed URL as the EDL source. When a SaaS provider adds a new endpoint for a SaaS application, the corresponding Feed URL is updated.For worldwide Microsoft 365 URLs, use the https://saasedl.paloaltonetworks.com/feeds/m365/worldwide/any/all/url URL. Other URLs are provided for IPv4 and IPv6 and for country-specific and governmental applications.
- Retrieve the list of Office 365 IP addresses and URLs provided by Microsoft at https://learn.microsoft.com/en-us/microsoft-365/enterprise/urls-and-ip-address-ranges. Microsoft also provides an Office 365 IP address and URL web service at https://learn.microsoft.com/en-us/microsoft-365/enterprise/microsoft-365-ip-web-service.