Download PDF
Prisma Access
New Features in Prisma Access 5.2, 5.2.1, and 5.2.2
Table of Contents
Expand All
|
Collapse All
Prisma Access Docs
-
- 6.1 Preferred and Innovation
- 6.0 Preferred and Innovation
- 5.2 Preferred and Innovation
- 5.1 Preferred and Innovation
- 5.0 Preferred and Innovation
- 4.2 Preferred
- 4.1 Preferred
- 4.0 Preferred
- 3.2 Preferred and Innovation
- 3.1 Preferred and Innovation
- 3.0 Preferred and Innovation
- 2.2 Preferred
-
-
- 4.0 & Later
- Prisma Access China
-
-
New Features in Prisma Access 5.2, 5.2.1, and 5.2.2
| Where Can I Use This? | What Do I Need? |
|---|---|
|
|
This section provides you with a list of new features in Prisma Access 5.2 and
5.2.1 Preferred and Innovation, along with the recommended and required software
versions you need to use.
This document contains roadmap information and is being shared for INFORMATIONAL
AND PLANNING PURPOSES ONLY. It is not a binding commitment and is subject to
change.
- Recommended Software Versions for Prisma Access 5.2.2 Preferred and Innovation
- Recommended Software Versions for Prisma Access 5.2.1 Preferred and Innovation
- Infrastructure, Plugin, and Dataplane Dependencies for Prisma Access 5.2.2 Preferred and Innovation Features
- Infrastructure, Plugin, and Dataplane Dependencies for Prisma Access 5.2.1 Preferred and Innovation Features
- Infrastructure, Plugin, and Dataplane Dependencies for Prisma Access 5.2 Preferred and Innovation Features
- Prisma Access 5.2.2 Features
- Prisma Access 5.2.1 Features
- Prisma Access 5.2 Features
Recommended Software Versions for Prisma Access 5.2.2 Preferred and Innovation
There are two Prisma Access 5.2.2 versions:
- 5.2.2 Preferred runs a PAN-OS 10.2.4 dataplane. If your deployment is running a lower dataplane version, you should upgrade your dataplane to PAN-OS 10.2.4 to implement 5.2.2 Preferred features.
- 5.2.2 Innovation runs on a PAN-OS 11.2.6 dataplane.
For Prisma Access 5.2.2 features, Palo Alto Networks recommends
that you upgrade your Prisma Access to the following versions
before installing the plugin.
| Prisma Access Version | Cloud Services Plugin Version | Required Dataplane Version for 5.2.2 | Recommended GlobalProtect Version | Recommended Panorama Version |
|---|---|---|---|---|
| 5.2.2 | 5.2.0 hotfix | PAN-OS 10.2.4 (required for 5.2.2 Preferred) PAN-OS 11.2.6
(required for 5.2.2 Innovation) |
6.0.7+
6.1.3+
6.2.1+
Minimum required versions for IPv6 Support for Public Apps for IP
Optimization:
|
10.2.4+
11.0.1+
11.1.0+
11.2.6+
|
Recommended Software Versions for Prisma Access 5.2.1 Preferred and Innovation
There are two Prisma Access 5.2.1 versions:
- 5.2.1 Preferred runs a PAN-OS 10.2.4 dataplane. If your deployment is running a lower dataplane version, a dataplane upgrade to PAN-OS 10.2.4 might be required to implement 5.2.1 Preferred features.
- 5.2.1 Innovation runs a PAN-OS 11.2.4 dataplane. An upgrade to PAN-OS 11.2.4 is required to implement 5.2 Innovation features.
For new Prisma Access 5.2.1 Innovation features, Prisma Access
recommends that you upgrade your Prisma Access to the following
versions before installing the plugin.
| Prisma Access Version | Cloud Services Plugin Version | Required Dataplane Version for 5.2.1 | Recommended GlobalProtect Version | Recommended Panorama Version |
|---|---|---|---|---|
| 5.2.1 | 5.2.0 hotfix | PAN-OS 10.2.4 (required for 5.2.1 Preferred) PAN-OS 11.2.4
(required for 5.2.1 Innovation) |
6.0.7+
6.1.3+
6.2.1+
|
10.2.4+
11.0.1+
11.1.0+
11.2.4+
|
Recommended Software Versions for Prisma Access 5.2 Preferred and Innovation
There are two Prisma Access 5.2 versions:
- 5.2 Preferred runs a PAN-OS 10.2.4 dataplane. If your deployment is running a lower dataplane version, a dataplane upgrade to PAN-OS 10.2.4 might be required to implement 5.2 Preferred features. If you're an existing customer, see Infrastructure, Plugin, and Dataplane Dependencies for Prisma Access 5.2.1 Preferred and Innovation Features to see if a dataplane upgrade is required for a Prisma Access 5.2 feature.
- 5.2 Innovation runs a PAN-OS dataplane of 11.2.3. An upgrade to PAN-OS 11.2.3 is required to implement 5.2 Innovation features.
For new Prisma Access 5.2 Innovation features, Prisma Access
recommends that you upgrade your Prisma Access to the following
versions before installing the plugin.
| Prisma Access Version | Cloud Services Plugin Version | Required Dataplane Version for 5.2 | Recommended GlobalProtect Version | Recommended Panorama Version |
|---|---|---|---|---|
| 5.2 | 5.2 | PAN-OS 10.2.4 (required for 5.2 Preferred) PAN-OS 11.2.3
(required for 5.2 Innovation) |
6.0.7+
6.1.3+
6.2.1+
|
10.2.4+
11.0.1+
11.1.0 +
11.2.3+
|
Infrastructure, Plugin, and Dataplane Dependencies for Prisma Access 5.2.2 Preferred and Innovation Features
Prisma Access 5.2.2 features require one of more of the following components
to function:
- Infrastructure Upgrade—The infrastructure includes the underlying
service backend, orchestration, and monitoring infrastructure. Prisma Access upgrades the infrastructure before the general
availability (GA) date of a Prisma Access release. Features that require only an infrastructure upgrade to be unlocked take effect for all Prisma Access deployments, regardless of version, at the time of the infrastructure upgrade.
- Plugin Upgrade (Prisma Access Panorama Managed Deployments
Only)—Installing the plugin activates the features that are
available with that release. You download and install the plugin on the
Panorama that manages Prisma Access.Prisma Access 5.2.2 uses a hotfix version of the 5.2 Cloud Services plugin.
- Dataplane Upgrade—The dataplane enables traffic inspection and
Security policy enforcement on your network and user traffic.
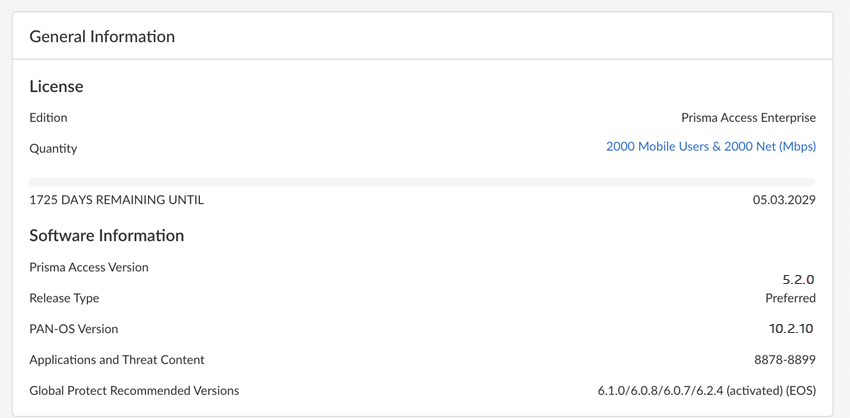
- For Prisma Access (Managed by Strata Cloud Manager), go to ManageConfigurationNGFW and Prisma AccessOverview.'
![]()
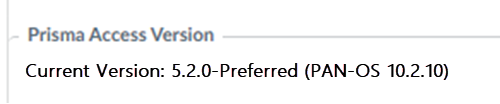
- For Prisma Access (Managed by Panorama) deployments, you can view your dataplane version by going to PanoramaCloud ServicesConfigurationService Setup and viewing the Prisma Access Version. Prisma Access 5.2.2 Preferred runs PAN-OS 10.2.4 and Prisma Access Innovation runs PAN-OS 11.2.6.
![]()
- For Prisma Access (Managed by Strata Cloud Manager), go to ManageConfigurationNGFW and Prisma AccessOverview.'
A dataplane upgrade to 5.2.2 Innovation is optional, and is
only required if you want to take advantage of the features that require a dataplane
upgrade.
These features are activated with the infrastructure upgrade only for Prisma Access:
- None
These 5.2.2 features require an infrastructure and plugin upgrade but don't
require a dataplane upgrade to 10.2.10. A minimum dataplane version of 10.2.4 is
required for these features:
- IoT Device-ID Based Policies Support for Mobile Users
These 5.2.2 features require an infrastructure and plugin upgrade and require
a minimum dataplane version of PAN-OS 10.2.4, making them Prisma Access
5.2.2 Preferred features:
- IPv6 Support for Public Apps for IP Optimization
These 5.2.2 features require an infrastructure, plugin, and dataplane upgrade
to PAN-OS 11.2.6, making them Prisma Access 5.2.2 Innovation features:
- Proxy Chaining from Prisma Access Explicit Proxy to Third-Party Proxy
- Prisma SASE 5G
Infrastructure, Plugin, and Dataplane Dependencies for Prisma Access 5.2.1 Preferred and Innovation Features
Prisma Access 5.2.1 features require one of more of the following components
to function:
- Infrastructure Upgrade—The infrastructure includes the underlying
service backend, orchestration, and monitoring infrastructure. Prisma Access upgrades the infrastructure before the general
availability (GA) date of a Prisma Access release. Features that require only an infrastructure upgrade to be unlocked take effect for all Prisma Access deployments, regardless of version, at the time of the infrastructure upgrade.
- Plugin Upgrade (Prisma Access Panorama Managed Deployments
Only)—Installing the plugin activates the features that are
available with that release. You download and install the plugin on the
Panorama that manages Prisma Access.Prisma Access (Managed by Panorama) releases 5.2 and 5.2.1 use the Cloud Services Plugin 5.2 Cloud Services plugin. Prisma Access 5.2.1 is activated using a hotfix version of the 5.2 plugin.
- Dataplane Upgrade—The dataplane enables traffic inspection and
security policy enforcement on your network and user traffic.
- For Prisma Access (Managed by Strata Cloud Manager), go to ManageConfigurationNGFW and Prisma AccessOverview.'
![]()
- For Prisma Access (Managed by Panorama) deployments, you can view your dataplane version by going to PanoramaCloud ServicesConfigurationService Setup and viewing the Prisma Access Version. Prisma Access 5.2.1 Preferred runs PAN-OS 10.2.4 and Prisma Access Innovation runs PAN-OS 11.2.4.
![]()
- For Prisma Access (Managed by Strata Cloud Manager), go to ManageConfigurationNGFW and Prisma AccessOverview.'
A dataplane upgrade to 5.2.1 Innovation is optional, and is
only required if you want to take advantage of the features that require a dataplane
upgrade.
These features are activated with the infrastructure upgrade only for Prisma Access:
- High-Performance Branch Sites Visibility
- RFC6598 Mobile Users Address Pool for New Prisma Access (Managed by Strata Cloud Manager) Deployments
- Route Table Visibility at Branch Sites and Service Connections
- Israel and Saudi Arabia Strata Logging Service Region Support
- Native IPv6 Support for Existing Prisma Access Deployments
- View Access Agent in All Users
These features require an infrastructure and plugin upgrade but don't require
a dataplane upgrade. A minimum dataplane version of 10.2.4 is required for these
features:
- Explicit Proxy Support for Colo-Connect
- Explicit Proxy Third-Party Enterprise Browser Integration
The following 5.2.1 features require an infrastructure and plugin upgrade and
require a minimum dataplane version of PAN-OS 10.2.4, making them Prisma Access 5.2.1 Preferred features:
- None
The following 5.2 features require an infrastructure, plugin, and dataplane
upgrade to PAN-OS 11.2.4, making them Prisma Access 5.2.1 Innovation features:
- Remote Network—High Performance Private App Access Support
- Static IP Address Enhancements for Mobile Users
Infrastructure, Plugin, and Dataplane Dependencies for Prisma Access 5.2 Preferred and Innovation Features
Prisma Access 5.2 features require one of more of the following components
to function:
- Infrastructure Upgrade—The infrastructure includes the underlying
service backend, orchestration, and monitoring infrastructure. Prisma Access upgrades the infrastructure before the general
availability (GA) date of a Prisma Access release. Features that require only an infrastructure upgrade to be unlocked take effect for all Prisma Access deployments, regardless of version, at the time of the infrastructure upgrade.
- Plugin Upgrade (Prisma Access Panorama Managed Deployments Only)—Installing the plugin activates the features that are available with that release. You download and install the plugin on the Panorama that manages Prisma Access.
- Dataplane Upgrade—The dataplane enables traffic inspection and
security policy enforcement on your network and user traffic.
- For Prisma Access (Managed by Strata Cloud Manager), go to ManageConfigurationNGFW and Prisma AccessOverview.
![]()
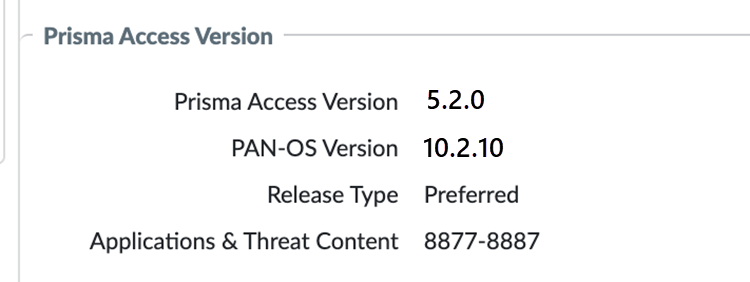
- For Prisma Access (Managed by Panorama) deployments, you can view your dataplane version by going to PanoramaCloud ServicesConfigurationService Setup and viewing the Prisma Access Version. Prisma Access 5.2 Preferred runs PAN-OS 10.2.4 and Prisma Access Innovation runs PAN-OS 11.2.3.
![]()
- For Prisma Access (Managed by Strata Cloud Manager), go to ManageConfigurationNGFW and Prisma AccessOverview.
A dataplane upgrade to 5.2 Innovation is optional, and is
only required if you want to take advantage of the features that require a dataplane
upgrade.
These features are activated with the infrastructure upgrade only for Prisma Access:
- Simplify Prisma Access SaaS Connectivity with IP Optimization for Mobile Users and Explicit Proxy Deployments
- TLS 1.3 and PubSub Support for Traffic Replication (PubSub support is added in Prisma Access 5.2.1)
- View and Monitor Colo-Connect
These features require an infrastructure and plugin upgrade but don't require
a dataplane upgrade:
- 25,000 Remote Network and 50,000 IKE Gateway Support
- Private IP Address Visibility and Enforcement for Agent Based Proxy Traffic
- IP Address Optimization for Explicit Proxy Users- Proxy Deployments
- Simplified Prisma Access Private App Connectivity
- View Prisma Access, Dataplane, and Application and Threats Content Versions in Strata Cloud Manager
The following 5.2 features require an infrastructure and plugin upgrade and
require a minimum dataplane version of PAN-OS 10.2.4, making them Prisma Access 5.2
Preferred features:
- Remote Networks—High Performance
The following 5.2 features require an infrastructure, plugin, and dataplane
upgrade to Prisma Access 11.2.3, making them Prisma Access 5.2 Innovation features:
- SC-NAT Support for Dynamic Privilege Access with CIAM
- ZTNA Connector Support for Commitless App Onboarding
Prisma Access 5.2.2 Features
The following table describes the new features that will be generally available with
Prisma Access 5.2.2.
IoT Device-ID Based Policies Support for Mobile Users
|
Supported in:
Prisma Access (Managed by Panorama) deployments in Prisma Access 5.2.2
|
Prisma Access extends the use of third-party Device-ID to include mobile
users. You can create new Device-ID based Security policies specific to
mobile users, or extend existing Device-ID based Security policies for
remote networks to include mobile users. Use the Cloud Identity Engine along with
Prisma Access to learn about IoT devices from third-party IoT detection sources
or from Device Security. You can create Device-ID objects from the
information you learn, and apply those Device-ID objects to Security
policy rules for access and control for mobile users in the same way you can for
remote networks.
IPv6 Support for Public Apps for IP Optimization
|
Supported in:
Prisma Access 5.2.2 Preferred and Innovation
|
Prisma Access supports IPv6 for public (internet) apps as well as
internal apps for existing deployments that use IP Optimization. This public app support
expands the use cases for IP Optimization deployments.
Prisma SASE 5G
|
Supported in:
Prisma Access 5.2.2 Innovation
|
Prisma SASE 5G extends comprehensive
zero-trust security to enterprise 5G deployments.
Prisma SASE 5G feature integrates zero-trust security with 5G networks,
enabling service providers to offer comprehensive SASE services for 5G-connected
devices without the complexity of agents or inline hardware. This innovative
approach combines Palo Alto Networks' proven Prisma Access with your 5G
infrastructure, providing agentless authentication, flexible traffic routing, and
intuitive multi-tenant management. By bridging the gap between 5G authentication and
SASE policy rules, Prisma Access lets enterprises embrace 5G technology securely
and at scale. With support for all SASE use cases, robust monitoring, and
integration with existing Prisma Access capabilities, Prisma SASE 5G is the key to
unlocking the full potential of enterprise mobility in the 5G era.
Proxy Chaining from Prisma Access Explicit Proxy to Third-Party Proxy
|
Supported in:
Prisma Access 5.2.2 Innovation
|
To allow secure upstream proxy integration from Prisma Access explicit proxy deployments to a cloud-based or
on-premises proxy solution, you can use proxy chaining. This functionality
establishes a sequential pathway by routing the traffic through multiple proxy
servers sequentially by utilizing the existing network infrastructure, thereby
enhancing security and compliance. To configure proxy chaining, you create profiles
with the upstream proxy server’s IP address or FQDN and port number, and create
rules to define the criteria to route traffic through upstream proxy servers.
With this enhancement, you can:
- Route traffic to the cloud or on-premises upstream proxy servers based on source IP address, URL category, usernames, and user groups.
- Connect Prisma Access explicit proxy infrastructure to a third-party cloud-based or on-prem proxies without extensive reconfiguration.
- Connect to upstream proxy over TLS to secure plain text data between proxies.
- Share X-Forwarded-For (XFF) and X-Authenticated-User (XAU) headers with upstream proxy servers.
Third Party NDR integration with Prisma Access
|
Supported in:
|
Prisma Access Traffic Replication adds full visibility
into forensic and postmortem analysis involving SASE architectures by making a copy
available of the traffic that is traversing Prisma Access. Some common use cases
where Traffic Replication is instrumental are:
- Forensic and Threat Hunting analysis where packet captures provide irrefutable evidence of the attack and the approach that was used
- Meeting specific regulatory compliance where packet captures need to be stored for a certain amount of time
- Packet-level network and application performance debugging
- Continuing to use any preferred third-party tools that your organization has invested in
Here are the supported third-party Network
Detection and Response (NDR) solutions.
Prisma Access 5.2.1 Features
This section describes the new features that are available with Prisma Access 5.2.1.
All Users in Prisma Access
|
Supported in:
Prisma Access 5.2.1 Innovation
|
Managing security across a hybrid workforce requires administrators to track user
connection status, location, and access mode across Next-Generation Firewalls
(NGFWs) and cloud services. The new All Users page provides comprehensive,
centralized visibility to address this complexity
In the All Users page, you can view:
- The total number of unique users currently connected to Palo Alto Networks security solutions and whether users are connected to NGFW and Prisma® Access.
- The number of users connected during a certain time range, broken down by users connected through NGFW and Prisma Access.
- Agent-based users connected through NGFW and Prisma Access.
- Agent-based or browser-based Explicit Proxy users connected to NGFW and Prisma Access.
- A list of unmanaged device users accessing Prisma Access.
- A list of users connecting from branch locations to Prisma Access.
- A list of users connecting their data centers using specific service connections.
Explicit Proxy Support for Colo-Connect
|
Supported in:
Prisma Access 5.2.1 Preferred and Innovation
|
For organizations operating large data centers with direct connectivity to colocation facilities, achieving
high-speed, simplified access to private applications previously involved complex,
manual routing configurations. This manual overhead often led to suboptimal
performance and inconsistent latency. This advanced explicit proxy capability, built
into the Prisma® Access platform, resolves those
challenges by enabling users to connect via Explicit Proxy. Customers now receive up
to 20 Gbps of dedicated throughput per region, ensuring robust performance and
exceptional scale for their largest environments
This simplified integration offers critical operational advantages:
- Explicit Proxy automatically connects to the nearest Prisma Access compute location, offering you the best possible latency.
- Eliminates network and routing dependencies, offering automated secure tunnel management and routing for private applications.
- Colo-Connect supports retrieving private applications in overlapped networks, ensuring flexibility and accessibility.
Explicit Proxy Support for DNS Proxy
|
Supported in:
Prisma Access (Managed by Strata Cloud Manager) 5.2.1 Preferred and Innovation
|
Organizations using Explicit Proxy often face challenges integrating their cloud
security with specialized internal network infrastructure, particularly regarding
custom Domain Name Service (DNS) resolution. This limitation can interrupt seamless
access to both public internet applications and critical internal private resources.
Explicit Proxy now expands its capabilities to include comprehensive DNS Proxy customization, solving this
hybrid networking challenge. This feature allows you to seamlessly integrate
regional DNS, custom third-party resolvers, or existing on-premises DNS
infrastructure. By supporting FQDN-based resolution, the solution guarantees that
all applications—whether public or privately hosted—are resolved correctly and
securely. This optimization is supported on Panorama Managed Prisma ®
Access, delivering a more robust and flexible security posture for hybrid
environments and optimizing the user experience.
Secure Integration of Third-Party Enterprise Browsers with Explicit Proxy
|
Supported in:
Prisma Access 5.2.1 Preferred and Innovation
|
For organizations using Explicit Proxy, integrating third-party Enterprise Browsers
previously required complex configurations to ensure secure policy enforcement,
often forcing end-users to re-authenticate unnecessarily. This feature, integrated into the
Prisma Access now enables secure and transparent exchange of
user information between the browser and the proxy. This robust exchange allows
security teams to enforce granular User-ID based policy rules directly within Prisma Access for private application access. This feature
eliminates the need for end users to re-authenticate if they have already logged
into the third-party Enterprise Browser, providing a true single sign-on experience
and simplifying administrative overhead.
Explicit Proxy Integration With ZTNA Connector
|
Supported in:
Prisma Access 5.2.1 Preferred and Innovation
|
Previously, integrating ZTNA Connector with explicit proxy often
involved complex manual routing and network dependencies, leading to management
overhead and suboptimal performance. This new integration, built into the Prisma® Access platform, resolves those challenges.
It enables users connecting to private applications through ZTNA Connector to
establish a high-capacity connection via Explicit Proxy, supporting ZTNA Connectors
with a capacity of up to 10 Gbps for Prisma® Access
Browser and Agent Proxy traffic. This feature ensures robust performance
and seamless connectivity.
Additional benefits of this simplified integration include:
- Explicit Proxy automatically connects to the nearest Prisma Access compute location with Explicit Proxy, ensuring optimal latency.
- Eliminates network and routing dependencies, ensuring automated secure tunnel management and routing for private applications.
- ZTNA Connector supports Cloud Identity Engine (CIE), which enables the automatic discovery of private applications.
- ZTNA Connector supports retrieval of private applications in overlapping networks, ensuring flexibility and accessibility.
High-Performance Branch Sites Visibility
|
Supported in:
Prisma Access 5.2.1 Innovation (new Prisma Access deployments only)
|
When scaling a distributed business, ensuring high-bandwidth branch sites have
secure, consolidated access to both the internet and private applications requires
complex, separate infrastructure management. To onboard a branch site with a high
bandwidth, Prisma® Access provides you with a Remote Network—High
Performance. The high-performance remote network provides you with a high
bandwidth for each service IP address, which reduces the complexity in configuring
and managing multiple IPSec devices at every remote location.
The Prisma Access Remote Network—High Performance adds
private app access support, in addition to its existing support for egress to the
internet. This support means that you can retrieve private apps from a branch
connected by a high-performance remote network, communicate with another branch
(branch-to-branch traffic), and communicate with mobile users (mobile user-to-branch
traffic) using service connections.
You can now view data for High-Performance branch sites in Strata
Cloud Manager to view the health and connectivity of your branch sites.
Israel and Saudi Arabia Strata Logging Service Region Support
|
Supported in:
Prisma Access 5.2.1 Preferred and Innovation
|
Organizations operating in regulated regions often face strict data residency
mandates, requiring that network security logs and audit trails remain stored within
specific national borders. To help customers seamlessly meet these regulatory
demands, Prisma® Access now enables localized log storage options for the Strata
Logging Service.
This enhancement introduces dedicated Strata Logging Service regions for both
Israel and Saudi Arabia. When you activate Strata Logging Service for your Prisma
Access deployment and select the local region, you ensure that log data is
physically stored within the respective region's bounds. This capability supports
stringent data locality compliance and can provide superior performance for regional
log querying and analysis.
Native IPv6 Support for Existing Prisma Access Deployments
|
Supported in:
Prisma Access 5.2.1 Preferred and Innovation for
all deployments (IPv6 support for new deployments is
supported starting Prisma Access
5.1.1; support for
existing deployments added in Prisma Access
5.2.1)
|
Organizations adopting IPv6 endpoints require seamless, end-to-end IPv6 access across
their Secure Access Service Edge (SASE) environment. Previously, IPv6 support in
Prisma® Access was limited to private applications. This feature now encompasses
comprehensive end-to-end IPv6 support for Mobile Users,
Remote Networks, and Service Connections, and adds native IPv6 support for existing
deployments. One key benefit of native IPv6 support is the ability for Mobile Users
utilizing IPv6-only endpoints to establish connections with Prisma Access via IPv6
connections using GlobalProtect®. Additionally, this support enables secure access
to public SaaS applications over the internet, even when those destinations
necessitate IPv6 connections. This enhancement, leveraging the significantly larger
IPv6 address space, ensures compatibility with both IPv6 and dual-stack connections,
accelerating your organization's migration to modern, cloud-based, and IPv6-enabled
networks.
Privileged Remote Access
|
Supported in:
Prisma Access 5.2.1 Innovation
|
Privileged Remote Access (PRA) is a
capability for Prisma Access that enables secure, clientless access to nonweb
applications like RDP, SSH, and VNC. With PRA, you can provide contractors, vendors,
and other third parties with browser-based access to internal resources without
requiring them to install additional software. This feature addresses use cases such
as unmanaged device access, vendor consolidation, and enterprise browser controls
for nonweb apps.
PRA allows you to retire legacy solutions while centralizing visibility and
management with Prisma Access. You can define access policies and monitor and
terminate connections as needed, all from a centralized console. The cloud-delivered
service takes advantage of your existing Prisma Access infrastructure and integrates
with the Cloud Identity Engine for authentication.
By implementing PRA, you can simplify your IT stack, improve security, and enable
productivity for your extended workforce. Whether you need to provide access for
contractors or enable just-in-time privileged access for OT environments, PRA offers
a solution that aligns with Zero Trust principles.
Remote Networks—High Performance Private App Access Support
|
Supported in:
Prisma Access 5.2.1 Innovation (new Prisma Access deployments only)
|
When scaling a distributed business, ensuring high-bandwidth branch sites have
secure, consolidated access to both the internet and private applications requires
complex, separate infrastructure management. To onboard a branch site with a high
bandwidth, Prisma® Access provides you with a Remote Network—High
Performance. The high-performance remote network provides you with a high
bandwidth for each service IP address, which reduces the complexity in configuring
and managing multiple IPSec devices at every remote location.
The Prisma Access Remote Network—High Performance adds
private app access support, in addition to its existing support for egress to the
internet. This support means that you can retrieve private apps from a branch
connected by a high-performance remote network, communicate with another branch
(branch-to-branch traffic), and communicate with mobile users (mobile user-to-branch
traffic) using service connections.
Route Table Visibility at Branch Sites and Service Connections
|
Supported in:
Prisma Access 5.2.1 Preferred and Innovation
|
Prisma Access customers face challenges when troubleshooting application
reachability issues because they lack visibility into the routing information
learned at Service Connections and Branch Sites. When your remote and
branch users need access to applications hosted in your data centers, proper routing
configuration is essential. Service connections facilitate the necessary
connectivity between your data centers and The
Route Table Visibility feature addresses this need by providing a
comprehensive view of routing tables at each service connection and remote network
site, allowing you to verify that routing information propagates correctly through
your Prisma® Access infrastructure With this visibility, you can search and
analyze the data to quickly identify routing-related issues without escalating to
technical support. This allows you to remediate connectivity problems faster,
ensuring successful application access for your distributed workforce.
Static IP Address Enhancements for Mobile Users
|
Supported in:
Prisma Access 5.2.1 Innovation
|
Managing mobile user access on networks that rely on IP address-based
authorization is challenging because dynamic IP assignment from Prisma® Access can
break access policies. The Static IP Allocation feature allows you to assign a fixed IP address to Prisma Access mobile
users to address this challenge. This feature is useful if your network deployments
restrict user access to resources using IP addresses as part of their network and
application design. This functionality simplifies deployment and provides critical
benefits:
You can assign static IP addresses for mobile
users based on the Prisma Access theater or User-ID™
You can now use location groups and user groups to improve your IP address assignment
for mobile users, in addition to theater and User-ID.
The supported number of IP address pool profiles is significantly increased,
simplifying the management and scaling of large mobile user deployments.
RFC 6598 Mobile Users Address Pool for New Prisma Access (Managed by Strata Cloud Manager) Deployments
|
Supported in:
Prisma Access (Managed by Strata Cloud Manager) 5.2.1 Preferred and Innovation
|
Manually defining and configuring RFC-compliant IP address pools for mobile users adds
time and complexity to new SASE deployments. To simplify the onboarding of
GlobalProtect® mobile users, new Prisma® Access (Managed by Strata Cloud Manager)
deployments now automatically include a default RFC6598 Mobile User address IP pool.
This pre-configured pool is immediately assigned to devices connecting via
GlobalProtect, significantly reducing setup time and the risk of misconfiguration
during initial deployment. While a compliant default is provided, you retain full
flexibility to customize this pool or define your own IP address ranges as your
specific networking requirements evolve.
View Access Agent in All Users
|
Supported in:
Prisma Access 5.2.1 Preferred and Innovation
|
View All Usersconnected to Palo Alto Networks'
security solutions Next-Generation Firewall (NGFW) and Prisma Access. You can easily
determine a user's connection status to NGFW or Prisma Access, including the
specific mode used and the user's location, whether at a branch site, service
connection, or remote location. View users' connection methods, such as Access
Agent, which could be Prisma Access Agent or GlobalProtect.
View Agent-Based Explicit Proxy
|
Supported in:
Prisma Access 5.2.1 Innovation
|
All Users provides an overview of all
users connected to Palo Alto Networks' security solutions Next-Generation Firewall
(NGFW) and Prisma Access. You can easily determine a user's connection status to
NGFW or Prisma Access, including the specific mode used and the user's location,
whether at a branch site, service connection, or remote location. You can view
agent-based or browser-based Explicit Proxy users connected to NGFW and Prisma
Access.
View Static IP Address Allocation for Mobile Users
|
Supported in:
Prisma Access 5.2.1 Innovation
|
Wildcard FQDN Configuration for Security Policies in ZTNA Connector
|
Supported in:
Prisma Access 5.2.1 Preferred and Innovation
|
Previously, security policy configuration for ZTNA Connector was protocol-dependent.
Although we supported wildcard Fully Qualified Domain Names (FQDNs), policies were
restricted strictly to the HTTP and HTTPS protocols. This limitation created
unnecessary complexity and administrative overhead for security teams managing
large, diverse application portfolios across Prisma®
Access platform.
This enhancement significantly improves operational agility by removing those
protocol constraints. By configuring a single, unified security policy based on a
wildcard application FQDN, that policy is automatically applied to all matching
discovered applications. This reduces the need for numerous individual policy
definitions. Crucially, when new applications matching wildcard FQDN are discovered, traffic can
pass securely without requiring the time-consuming process of committing
changes.
With this capability:
- You can configure a security policy based on the wildcard application FQDN.
- The same security policy is applied to all the discovered applications that share the same wildcard FQDN.
- When new applications that match the wildcard FQDN are discovered, traffic can pass without requiring a new commit.
ZTNA Connector for Onboarding Applications
|
Supported in:
Prisma Access 5.2.1 Preferred and Innovation
|
For enterprises utilizing Zero Trust Network Access (ZTNA) to secure access to
internal private applications, infrastructure scalability is critical. Organizations
with vast environments often find application counts quickly exceed previous limits,
constraining growth and increasing operational overhead. This feature, integrated
into the Prisma® Access platform, improves how you
manage high volumes of applications and resources. It specifically targets
organizations that previously encountered scalability issues when their private
applications exceeded 10,000.
The ZTNA Connector enhancement supports
significant enterprise growth while simplifying tenant management and reducing the
operational need to deploy excessive connector infrastructure. You gain improved
resource utilization and ensure your ZTNA Connector deployment remains stable and
highly performant, solidifying your Zero Trust architecture.
This enhancement provides dramatically increased capacity limits, allowing you to
onboard:
- 10,000 application targets per tenant
- 1,000 applications per connector group
- 200 connectors per tenant
Prisma Access 5.2 Features
This section describes the new features that are available with Prisma Access 5.2.
25,000 Remote Network and 50,000 IKE Gateway Support
|
Supported in:
Prisma Access 5.2 Preferred and Innovation
|
To implement this feature, reach out to your Palo Alto Networks account team, who
will open an SRE case to accommodate the request.
As enterprise networks expand, the ability to onboard and manage large-scale remote
networks and IKE gateways becomes critical for maintaining performance and security.
To accommodate the capacity increase for Prisma® Access deployments, the Strata Cloud Manager web interface now
provides enhanced tools for navigating and managing large lists of remote
networks and IKE gateways. These improvements, including advanced filtering,
sorting, and grouping options, ensure administrators can quickly find, manage, and
monitor remote networks, IPSec tunnels, and QoS settings, which significantly
improves operational efficiency at scale.
The interface now provides pagination, allowing you to choose how many rows to
display on a given page. A search ability is added, allowing you to find the desired
remote network in the list by typing its Name in the text box. You can also group by
compute locations. All groups display in a collapsed view and the page size you
selected applies to the groups. When you select a compute location to expand it, the
view displays based on the page size you selected.
Prisma Access Agent Observability
|
Supported in:
Prisma Access 5.2 Preferred and Innovation
|
The Prisma Access Agent is a next-generation mobile access
agent that allows you to use Prisma Access to secure your mobile workforce. Built
for today's hybrid workforce, the Prisma Access Agent delivers secure and convenient
access to both enterprise apps and the internet, and also simplifies network, IT and
security operations for an organization.
Private IP Address Visibility and Enforcement for Agent Based Proxy Traffic
|
Supported in:
Prisma Access 5.2 Preferred and Innovation
|
Visibility and enforcement based on an endpoint's private IP address was previously
unavailable for users connecting via
GlobalProtect® agent to the Explicit Proxy. This new feature
solves that challenge by allowing you to now leverage the private IP addresses of
endpoints for logging and to apply IP address-based enforcement. This enhancement
ensures consistent policy application and granular monitoring for users who connect
to Prisma® Access Explicit Proxy through the GlobalProtect agent from the branches.
IP Address Optimization for Explicit Proxy Users- Proxy Deployments
|
Supported in:
Prisma Access 5.2 Preferred and Innovation
|
IP Address Stickiness
With
IP address stickiness, you can secure the SaaS apps and websites that require user
sessions to maintain the same egress IP address of Prisma Access
throughout the user session.Simplify SaaS Applications Onboarding
Adding a
Prisma Access location or experiencing a scaling event at an existing Prisma Access location could lead to new IP addresses being allocated to your
Explicit Proxy deployments. It's a best practice to retrieve the new egress and gateway IP
addresses and add them to an allow list of the SaaS applications. IP address
optimization reduces the number of IP addresses that you have to manage in large
deployments.Explicit Proxy China Support
|
Supported in:
Prisma Access 5.2 Preferred and Innovation
|
Multinational organizations operating in China face unique challenges in securing
internet access for users and headless devices where VPN agents cannot be installed
due to compliance reasons or network restrictions. Prisma
® Access
explicit proxy support in China addresses
this critical need by providing a secure internet gateway that works without
requiring default route changes to the infrastructure, while coexisting with VPN
agents.
This solution also acts as a reliable proxy solution that complies with local
regulations while effectively managing internet access and safeguarding sensitive
information across endpoints. The explicit proxy support in China leverages AWS
infrastructure with a 1:1 architecture where each Envoy proxy is paired with a proxy
firewall virtual machine (VM). This architecture enables secure traffic handling
while accommodating the unique networking constraints.
When you implement this solution, users connecting from branch locations can
access the internet securely through the explicit proxy without having GlobalProtect
® clients installed. Additionally, headless devices such as IoT systems
or servers can route traffic through the proxy for security inspection. The
service integrates with your existing authentication methods, including SAML and
Kerberos, and supports the same Security policy rules you configure for your global
deployment. Palo Alto Networks NGFW capabilities securely inspect traffic,
with logs and telemetry available through the same management interface you use for
your global deployment. The architecture also supports routing specific domains to
Service Connection when needed, providing flexibility for accessing both internet
and private resources.
Remote Networks—High Performance
|
Supported in:
Prisma Access 5.2 Innovation (new Prisma Access deployments only)
|
Scaling distributed businesses requires secure, high-bandwidth connectivity, but
achieving reliable IPSec termination for large remote sites often involves managing
complex configurations and manual load balancing. Prisma® Access provides a
comprehensive solution for high-bandwidth IPSec termination that enhances the
scalability, performance, and reliability of remote site connectivity. You can
quickly onboard a branch site with high bandwidth using a Prisma Access remote
network, also known as a Remote Network—High Performance, which
offers these benefits:
- Supports high aggregate bandwidth per service IP address or service endpoint address, reducing the number of IP addresses or FQDNs required for IPSec tunnel termination.
- Includes regional redundancy to improve availability and fault tolerance.
- Uses network address translation (NAT) to reduce public egress IP addresses.
- Simplifies onboarding with in-product recommendations for choosing locations based on geographic availability.
- Includes support for Link Quality Metrics (LQM) that provide constant measurement of network performance metrics (such as jitter, latency, and packet loss) to inform traffic forwarding decisions.
Route Summarization for Dynamic Privilege Access
|
Supported in:
Prisma Access (Managed by Strata Cloud Manager) 5.2 Innovation
|
On Dynamic Privilege Access enabled Prisma
Access tenants, you can summarize routes when advertising the Mobile User (MU)
routes to your on-premises network. Route summarization is beneficial for
enterprises that have on-premises equipment that has limited capacity such as basic
cloud routers. By reducing the demand on these devices, route summarization ensures
that the devices won't exceed their route capacity when communicating with the data
center.
To enable route summarization, configure
global summary pools that consist of lists of large IP pools that can be used across
multiple projects. Then, enable route summarization in the Prisma Access service
connection. When a user uses the Prisma Access Agent to connect to a project that
has an IP address within the range of the configured global summary pools, the
service connection will advertise the global summary pool instead of the smaller
project-level route. This helps reduce the number of routes that are sent to the
network.
SC-NAT Support for Dynamic Privilege Access with CIAM
|
Supported in:
Prisma Access 5.2 Innovation
|
Prisma Access uses SC-NAT support with Dynamic Privilege Access
(DPA) to enforce service connections for access to private applications
in your data center or headquarters. When you have multiple projects in your DPA
environment, your network can experience IP address exhaustion when IP addresses in
your infrastructure subnet overlap. SC-NAT support enables Prisma Access to
implement source NAT (SNAT) for IP addresses to provide the following benefits:
- Map a single IP address for private application access through a service connection.
- Use SNAT for simplified routing.
- Eliminate IPv4 address pool overlap.
- Eliminate IPv4 address pool exhaustion between Prisma Access and your data center or headquarters.
Simplified Prisma Access Private App Connectivity
|
Supported in:
Prisma Access 5.2 Preferred and Innovation
|
One way for Prisma® Access to access a private app is by using a service connection, also known as a
Service Connection-Corporate Access Node (SC-CAN). It can be difficult to connect to
private apps using service connections because:
- Indeterministic throughput of the private app due to SC-CAN bottlenecks.
- Latency due to incorrect transit hops.
- Operational complexity in deploying SC-CANs.
Prisma Access has enhanced its routing infrastructure, orchestrating additional
routes to your onboarded SC-CANs in the Prisma® Access internal network when
required, eliminating SC-CAN bottlenecks and preventing incorrect transit hops and
inefficient routing.
This design offers the following benefits:
- Routing setup that is easier to deploy.
- Easy initial setup.
- Deterministic high bandwidth from a given SC-CAN to the data center or headquarters location where the private app is located.
Simplify Prisma Access SaaS Connectivity with IP Optimization for Mobile Users and Explicit Proxy Deployments
|
Supported in:
Prisma Access 5.2 Preferred and Innovation
|
Managing large SaaS allow lists, especially during Prisma® Access autoscaling events,
creates significant administrative overhead. Prisma Access expands the existing IP
Optimization functionality to address this challenge, offering support for both
Mobile Users—GlobalProtect® and Explicit
Proxy deployments.
For Mobile Users—GlobalProtect deployments, when a large number of users access a
GlobalProtect gateway from a location, Prisma Access autoscales the location and
adds another GlobalProtect gateway. IP Optimization uses a NAT layer so that the
autoscaled gateway uses the same IP address as the previously allocated IP address,
thus eliminating the need to add extra IP addresses to your organization's allow
lists.
Prisma Access expands this NAT layer to Explicit Proxy connections, thereby providing
consistent, low-management IP addresses for all supported mobile and proxy use
cases. This Explicit Proxy NAT layer is beneficial if you're setting up a Mobile
Users and Explicit Proxy deployment in Proxy Mode or Tunnel and Proxy Mode.
TLS 1.3 and PubSub Support for Traffic Replication
|
Supported in:
Prisma Access 5.2 Preferred and Innovation
PubSub support is added in Prisma Access 5.2.1
Preferred and Innovation.
|
If you use Traffic Replication, Prisma® Access can
minimize the challenges you encounter when you deploy third-party tools to deploy
and use it:
- Tools that consume the packet capture (PCAP) files require frequent queries of the buckets to cope with a large number of PCAP files. The tools might create overhead on the buckets and their use might be limited by the cloud providers.
- When using the PCAP files for forensic analysis, accessing SSL decrypted traffic provides better efficacy. A significant amount of the traffic is TLS 1.3 encrypted and requires decryption.
To solve these challenges, Prisma Access offers these enhancements for efficiency and
scalability:
- Pub/Sub Notifications—Prisma Access proactively sends a publisher and subscriber (Pub/Sub) notification when the storage bucket receives a new PCAP file. Using Pub/Sub notifications for new PCAP files eliminates the need to develop tools that notify you when there are new files in the buckets.
- TLS 1.3 Decryption Support—Prisma Access uses TLSv1.3 to decrypt PCAP files, which provides deeper visibility into your network traffic. However, this support applies only to remote network deployments where you have enabled the use of SSL/TLS decryption policy rules on PCAP files.

View and Monitor Colo-Connect
|
Supported in:
Prisma Access 5.2 Preferred and Innovation
|
Monitor data on your Colo-Connect service connections to provide a comprehensive view
of the health and connectivity of your deployment. To monitor your private
connectivity to hybrid cloud and on-premises data centers over cloud interconnects,
access the Monitor Colo-Connect feature.
Prisma Access Colo-Connect uses GCP interconnect technology to offer high-bandwidth
service connections to your private applications. Colo-Connect can work alongside
existing IPSec tunnel-based connections, allowing for private app access to smaller
data centers with lower bandwidth requirements. Gain insight into your Colo-Connect
deployment by checking metrics like the number of links and their status, throughput
patterns, and details of individual tunnels, connections, and links.
View Prisma Access, Dataplane, and Application and Threats Content Versions in Strata Cloud Manager and Panorama
|
Supported in:
Prisma Access (Managed by Strata Cloud Manager) 5.2 Preferred and Innovation
|
Managing component versions and tracking End-of-Support (EoS) dates across Prisma®
Access, Dataplane, and content releases typically requires checking multiple
locations. Prisma Access now lets you view the status of these components in a
single page for Prisma Access deployments managed by Strata Cloud
Manager and Panorama® and includes notifications that show you when your
current running Panorama version and plugin versions will be EoS.
Prisma® Access consists of components you manage such as Panorama and
the Cloud Services plugin, components that Prisma Access manages such as the
dataplane version, and components that Prisma Access manages but whose version you
can control (such as the GlobalProtect® version hosted on the Prisma Access portal).
Prisma Access lets you view the status of these components in a single page and
provides you with this information:
- Prisma Access version
- PAN-OS dataplane version
- Release Type (Preferred or Innovation)
- Applications and Threats content version


ZTNA Connector Support for Commitless App Onboarding
|
Supported in:
Prisma Access 5.2 Innovation
|
For security operations teams using ZTNA Connector within the Prisma® Access platform, application lifecycle management
previously involved significant delays. Onboarding, modifying, or removing
applications required a commitment process that introduced an operational delay of 5
to 10 minutes. This new capability eliminates that bottleneck, resulting in
dramatically improved operational efficiency. Your application onboarding time now takes
less than one minute, accelerating management tasks significantly.
Furthermore, this enhancement provides the necessary scalability to serve large
enterprises managing over 10,000 applications. This allows security teams to rapidly
deploy and modify application access policies without workflow interruptions,
ensuring greater flexibility and efficiency in enterprise security operations.