SaaS Security
Begin Scanning a GitHub App
Table of Contents
Expand All
|
Collapse All
SaaS Security Docs
Begin Scanning a GitHub App
Authorize Data Security to connect to GitHub to scan
all content shared within the app.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
Or any of the following licenses that include the Data Security license:
|
You can connect a GitHub to Data Security to scan for public exposure of repository folders or source
code files to ensure your company’s proprietary information is secure.
With GitHub, you can control if Data Security scans a collection
of owner accounts connected to an organization or a single owner account.
To
connect GitHub to Data Security and begin scanning assets, you
need to:
- Supported Content
- Onboard GitHub App to Data Security
- Troubleshooting Onboarding for GitHub App
- Start Scanning and Monitor Results
Support for automated remediation capabilities varies by SaaS application.
Supported Content
|
Support For
|
Details
|
|---|---|
|
Scan Content
| Files, Folders |
|
Backward Scan
|
Yes
Backward scanning is supported up to 1 year only.
|
|
Forward Scan
|
Yes
|
|
Rescan
|
Yes
|
|
Selective Scan
|
No
|
|
Exposure
|
Internal, Public
|
|
Remediation Actions
|
|
|
Post-Remediation Actions (Actions after Admin
Quarantine):
You can delete, restore, or download a quarantined file
after performing a remediation action (for example
quarantine or incident generation).
|
|
|
Notifications
|
|
|
User Activities
|
|
|
Snippet Support
|
Yes
|
|
Known License/Version restrictions
|
Supported Versions
|
|
Caveats/Notes
|
None
|
Onboard GitHub App to Data Security
For Data Security to scan assets, you must consent to specific permissions during adding
the GitHub App.
- Log in to Strata Cloud Manager.Select ConfigurationSaaS SecurityData SecurityApplicationsAdd ApplicationGitHub.
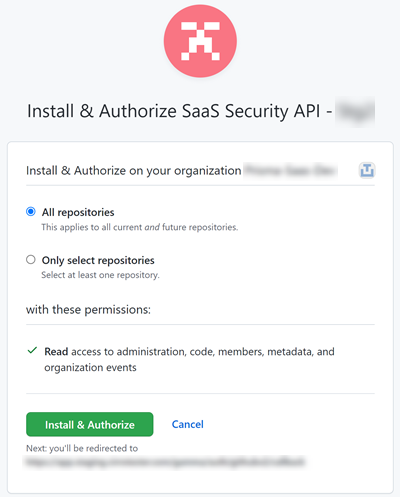
![]() Click Connect to GitHub Account, then sign in with a GitHub account that has Owner privileges.Choose which repositories you want Data Security to scan:
Click Connect to GitHub Account, then sign in with a GitHub account that has Owner privileges.Choose which repositories you want Data Security to scan:- (Recommended) If your GitHub account is part of an organization, Grant Data Security Organization access to scan your organization’s current and future repositories.
- Selectively choose which repositories you want Data Security to scan.
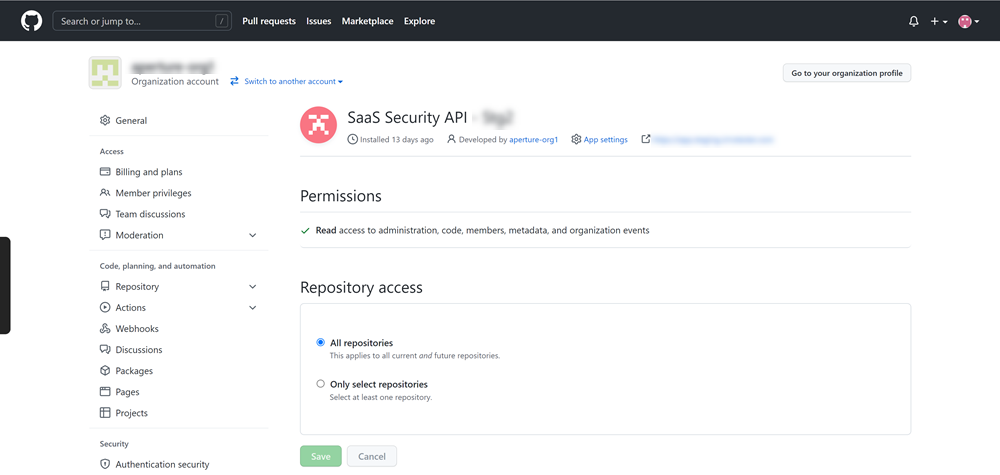
Authorize Data Security (listed as PAN ShieldArc) access to your GitHub account.![]() Verify that you successfully granted Third-Party application access policy to Data Security.
Verify that you successfully granted Third-Party application access policy to Data Security.![]()
Troubleshooting Onboarding for GitHub App
To ensure that your app has onboarded correctly without any issues in authentication or permissions, Data Security performs validation checks between the onboarding and scanning process. You can start scanning only after a successful validation. For GitHub, the following validations happen:- App Authentication
- Validating Permissions
After the validation is successful, Data Security displays the sample data assets.![]() If the App Authentication or Validating Permissions check fails, try the following:
If the App Authentication or Validating Permissions check fails, try the following:- Ensure you have administrator permissions.
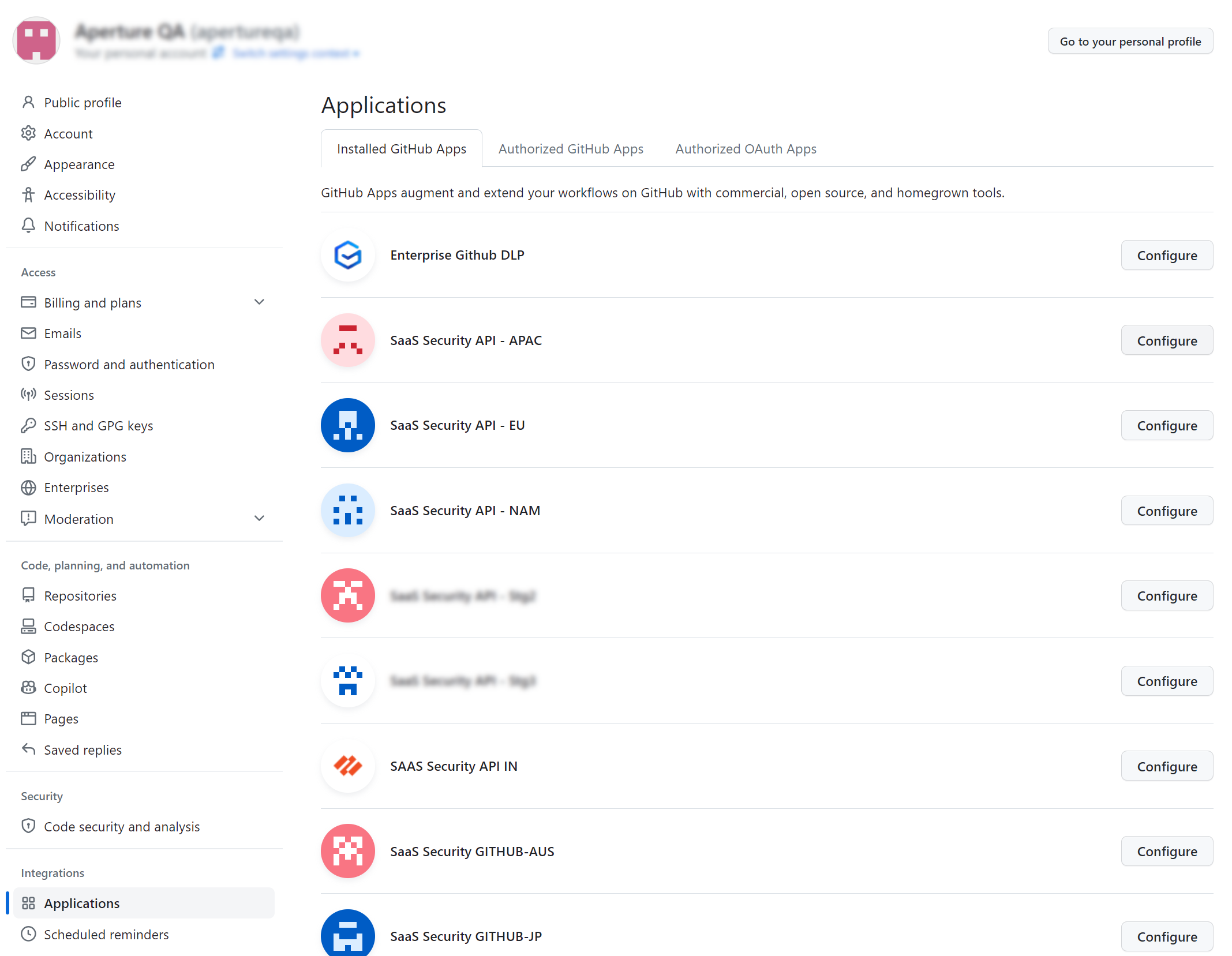
- Go to your GitHub app directory and check if your Palo
Alto Networks application is listed in the list of Installed
Apps. Following are the app names for specific regions:
- India region: SAAS Security API IN
- Australia region: SaaS Security GITHUB-AUS
- Japan region: SaaS Security GITHUB-JP
- UK region: SaaS Security GITHUB-UK
- EU region: SaaS Security API - EU
- APAC region: SaaS Security API - APAC
- US region: SaaS Security API - NAM
![]()
Handling ErrorsTo understand your error messages and ways to resolve them, see:The other most common issues related to onboarding a GitHub App are as follows:SymptomExplanationSolutionData Security does not create assets during forward scanning.Existing Data Security account will not create asset during forward scan due to a mismatch in installation ID. Thus, assets are created only during backward scanning.For assets to be created during forward scanning also, uninstall the existing Data Security app from your GitHub account/organization manually and perform a fresh onboarding to install Data Security again.Data Security web interface does not display assets that are associated with new branches.For performance reasons, Data Security only scans the default branch of the repository, not all branches of the repository.This is expected behavior.Data Security web interface does not display assets for a newly created repository.You likely did not grant Organization access as outlined in Onboard GitHub App to Data Security.Reauthenticate and authorize access to the new repository or grant Organization access.If the issue persists, contact SaaS Security Technical Support.Start Scanning and Monitor Results
When you add a new cloud app, then enable scanning, Data Security automatically scans the cloud app against the default data patterns and displays the match occurrences. You can take action now to improve your scan results and identify risks.- To start scanning the new GitHub app for risks, select ConfigurationSaaS SecurityData SecurityApplicationsGitHubView Settings...Start Scanning.Monitor the scan results.During the discovery phase, as Data Security scans files and matches them against enabled policy rules:
- Verify that SaaS Security web interface displays assets.
- Verify that your default policy rules are effective. If the results don’t capture all the risks or you see false positives, proceed to next step to improve your results.
(Optional) Modify match criteria for existing policy rules.(Optional) Add new policy rules.Consider the business use of your cloud app, then identify risks unique to your enterprise. As necessary, add new:(Optional) Configure or edit a data pattern.You can Configure Data Patterns to identify specific strings of text, characters, words, or patterns to make it possible to find all instances of text that match a data pattern you specify.