SaaS Security
Begin Scanning a Google Chat App
Table of Contents
Expand All
|
Collapse All
SaaS Security Docs
Begin Scanning a Google Chat App
Add your Google Chat app to Data Security to begin scanning and monitoring
assets for possible security risks.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
Or any of the following licenses that include the Data Security license:
|
To connect a Google Chat app to Data Security and begin scanning assets, you
need to:
- Ensure that you have a Google Chat admin account with Super admin role.
- Add the Google Chat admin account to Data Security and assign a Super admin role.
- Ensure that you have authorized the provided OAuth scopes via Domain Wide Delegation in the Google Admin Console.
Ensure that the Super Admin account
added to the Strata Cloud Manager for onboarding Google Chat app has logged in at
least once into the Strata Cloud Manager. Only then will the account be enabled.
Onboarding will fail if this account has never logged into the Strata Cloud Manager.
Supported Content
|
Support For
|
Details
|
|---|---|
|
Scan Content
| Messages, Files uploaded from device |
|
Backward Scan
|
Yes
|
|
Forward Scan
|
Yes
|
|
Rescan
|
No
|
|
Selective Scan
|
No
|
|
Exposure
|
Internal, External
|
|
Remediation Actions
|
|
|
Post-Remediation Actions (Actions after Admin
Quarantine):
You can delete, restore, or download a quarantined file
after performing a remediation action (for example
quarantine or incident generation).
|
|
|
Notifications
|
|
|
User Activities
|
|
|
Snippet Support
|
Yes
|
|
Known License and Version restrictions
|
Supported Versions
|
|
Caveats and Notes
|
Due to Google Chat app constraints, remediation for
Direct Messages with external users isn’t supported.
|
Prepare to Add Google Chat App
Google’s default Super admin role provides the necessary communication between
Data Security and the Google Chat app.
- Read, write, delete (for remediation) messages in the app.
- API access. API access provides visibility into the assets in Google Chat and enables Data Security to monitor the sharing of assets.
- Verify that your Google Chat administrator account is assigned a Super admin role.
![]() Ensure that the Google Chat administrator account’s domain matches the existing domain on Data Security.(Recommended) Add your Google Chat domain as an internal domain.Log in to Google Admin console.
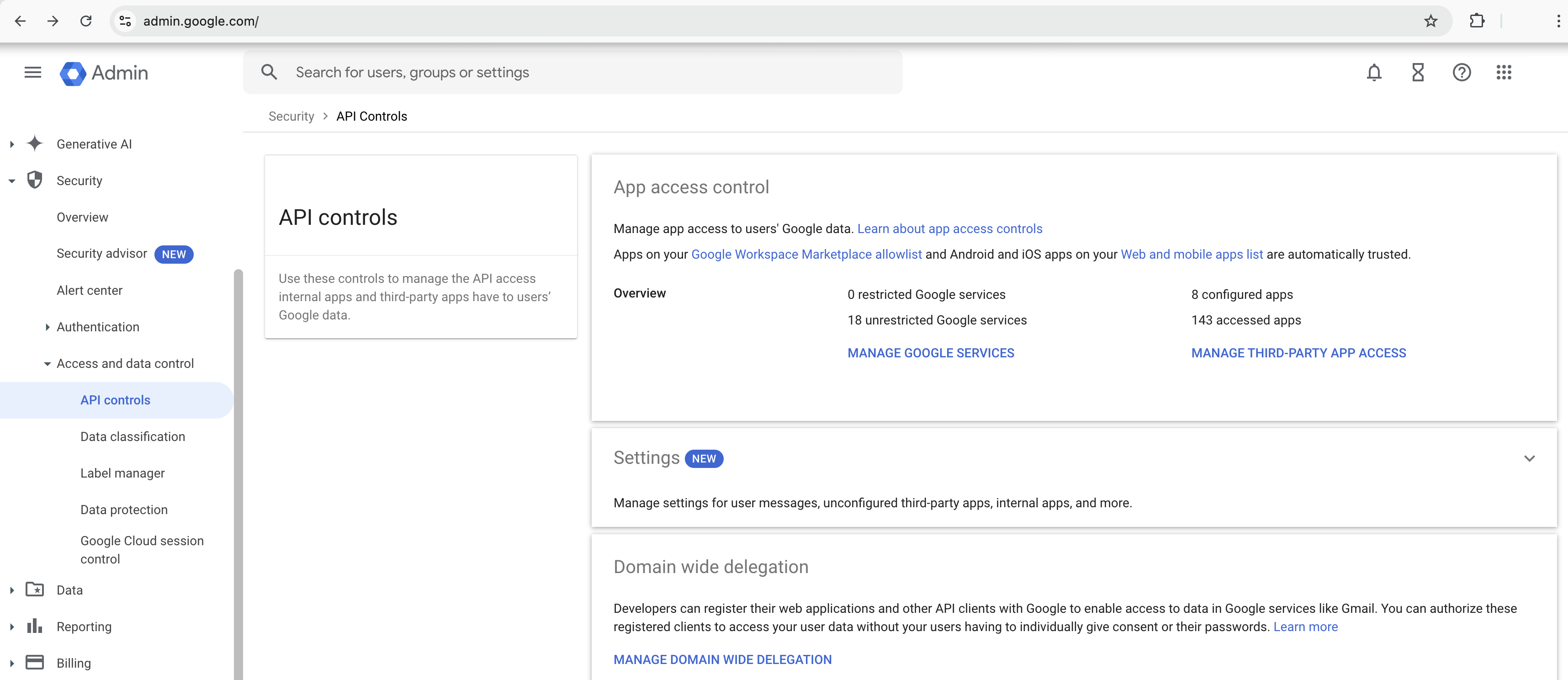
Ensure that the Google Chat administrator account’s domain matches the existing domain on Data Security.(Recommended) Add your Google Chat domain as an internal domain.Log in to Google Admin console.![]() Select SecurityAccess and data controlAPI controls.Select MANAGE DOMAIN WIDE DELEGATION and add the required scopes and service account mentioned in Step 2 of the Google Chat app onboarding Configuration wizard.Add the same email address of the Google Chat administrator to Data Security and assign a Superuser role.
Select SecurityAccess and data controlAPI controls.Select MANAGE DOMAIN WIDE DELEGATION and add the required scopes and service account mentioned in Step 2 of the Google Chat app onboarding Configuration wizard.Add the same email address of the Google Chat administrator to Data Security and assign a Superuser role.![]() Next step: Proceed to Add Google Chat App.
Next step: Proceed to Add Google Chat App.Add Google Chat App
For Data Security to scan assets, you must consent to specific permissions when adding the Google Chat app.- Log in to Strata Cloud Manager.Select ConfigurationSaaS SecurityData SecurityApplicationsAdd ApplicationGoogle Chat .
![]()
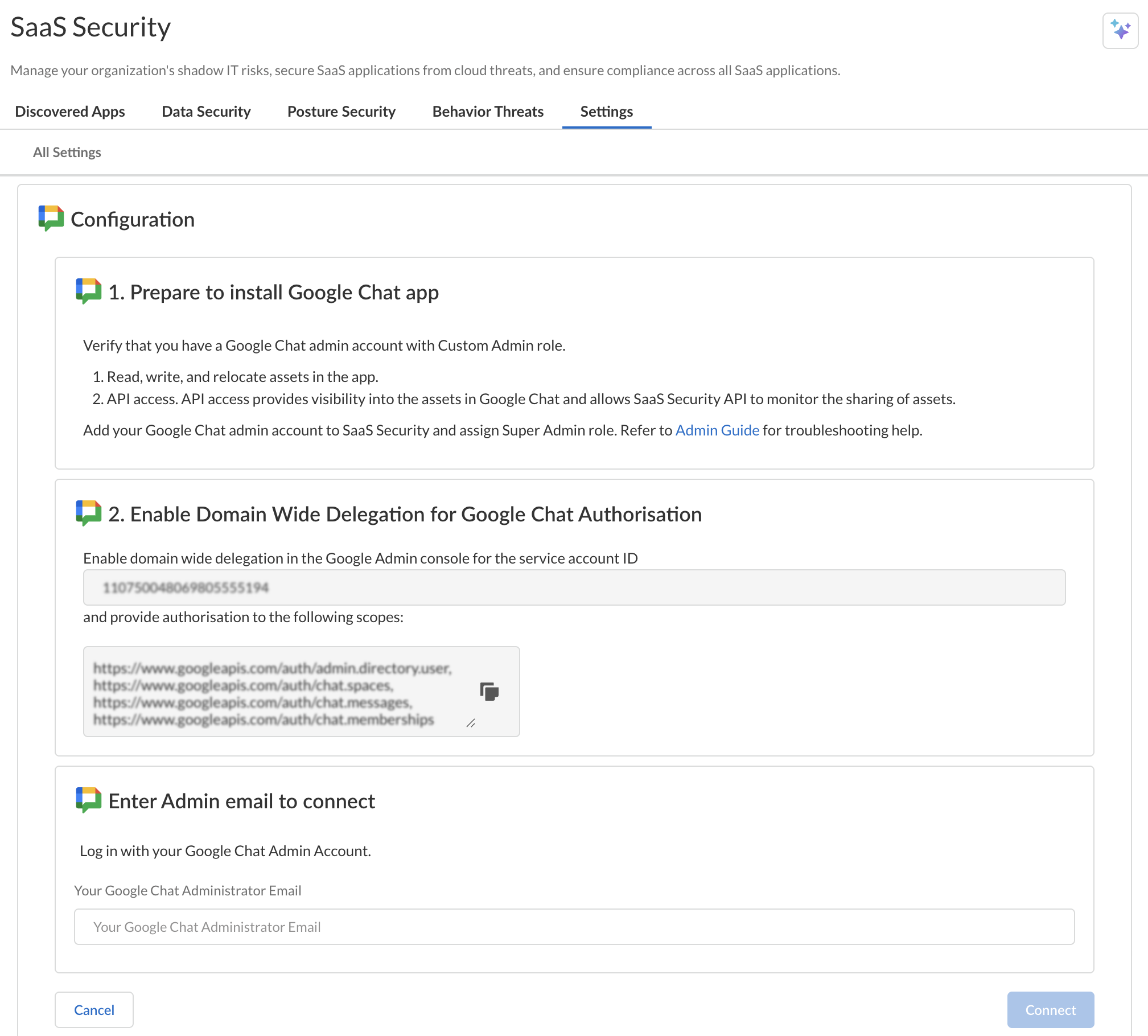
![]() As indicated in the onscreen Configuration wizard (screenshot above), Prepare to Add Google Chat App.To onboard your Google Chat app, follow steps 4 to 6 to set up your Domain Wide Delegation mentioned in the Prepare to Add Google Chat App section.Follow the final step in the onscreen Configuration wizard: Enter Admin email to connect and Connect.After you enter the Google Chat admin email, the Google Chat app is installed.
As indicated in the onscreen Configuration wizard (screenshot above), Prepare to Add Google Chat App.To onboard your Google Chat app, follow steps 4 to 6 to set up your Domain Wide Delegation mentioned in the Prepare to Add Google Chat App section.Follow the final step in the onscreen Configuration wizard: Enter Admin email to connect and Connect.After you enter the Google Chat admin email, the Google Chat app is installed.![]()
Identify Risks
When you add a new cloud app and enable scanning, Data Security automatically scans the cloud app against the default data patterns and displays the match occurrences. You can take action now to improve your scan results and identify risks.- To start scanning the new Google Chat app for risks, select ConfigurationSaaS SecurityData SecurityApplicationsGoogle ChatView Settings...Start Scanning.Monitor the scan results.During the discovery phase, Data Security scans files and matches them against enabled default policy rules.Verify that your default policy rules are effective. If the results don’t capture all the risks or you see false positives, proceed to the next step.(Optional) Modify match criteria for existing policy rules.(Optional) Add new policy rules.Consider the business use of your app, then identify risks unique to your enterprise. As necessary, add new:(Optional) Configure or edit a data pattern.You can Configure Data Patterns to identify specific strings of text, characters, words, or patterns to make it possible to find all instances of text that match a data pattern you specify.