SaaS Security
Begin Scanning a Microsoft Teams App
Table of Contents
Expand All
|
Collapse All
SaaS Security Docs
Begin Scanning a Microsoft Teams App
Learn how to add the Microsoft Teams app so that Data Security can protect the assets on them from data exfiltration
and malware propagation.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
Or any of the following licenses that include the Data Security license:
|
Support for automated remediation
capabilities varies by SaaS application.
Supported Content
|
Support For
|
Details
|
|---|---|
|
Scan Content
|
|
|
Backward Scan
|
No
|
|
Forward Scan
|
Yes
|
|
Rescan
|
No
|
|
Selective Scan
|
N/A
|
|
Exposure
|
Internal, External, Company
Attachments are supported using Office 365.
Due to new Microsoft licensing
requirements, the Microsoft Teams connector will work
only for customers running the E5 licenses. |
|
Remediation Actions
|
Quarantine for Attachments is
supported using Office 365. Remediation actions are not
available if you onboard using
Read-Only permissions. |
|
Post-Remediation Actions (Actions after Admin
Quarantine):
You can delete, restore, or download a quarantined file
after performing a remediation action (for example
quarantine or incident generation).
|
Quarantine for Attachments is
supported using Office 365. Post-Remediation actions are not
available if you onboard using
Read-Only permissions. |
|
Notifications
|
|
|
User Activities
|
|
|
Snippet Support
|
Yes
|
|
Known License and Version restrictions
|
Supported Versions
|
|
Caveats and Notes
|
None
|
Onboard Microsoft Teams App
- Prerequisites
- Plan to add the Office 365 app before you add the Microsoft Teams app, if you haven’t already done so. Data Security depends on the Office 365 app to scan Microsoft Teams attachments. In doing so, you must meet the onboarding requirements for the Office 365 app.Ensure that you have an Office 365 account with Global Administrator role permissions.Due to new Microsoft licensing requirements, ensure you are running the E5 licenses. The Microsoft Teams connector will work only for the E5 licenses.Grant Data Security access to Microsoft Teams.Establish communication between Data Security and Microsoft Teams. Go to http://portal.microsoftonline.com and log out of Office 365 to ensure that you're not logged in as a user other than an account with Global Admin role permissions.
![]() Log in to Office 365 using an account that has the Global Admin role permissions:
Log in to Office 365 using an account that has the Global Admin role permissions:![]() Add your MS Teams app
Add your MS Teams app- Log in to Strata Cloud Manager.Select ConfigurationSaaS SecurityData SecurityApplicationsAdd ApplicationMicrosoft Teams and click on the tile.
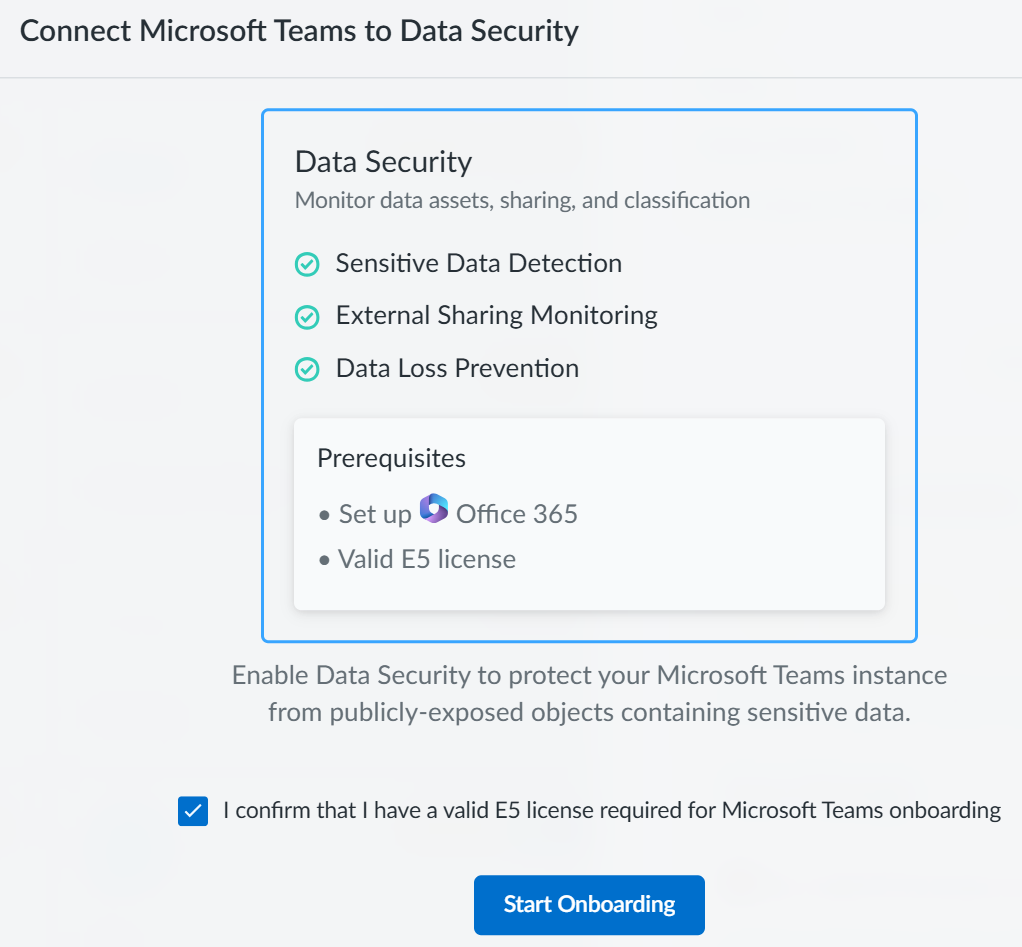
![]() Confirm that you have a valid E5 license and Start Onboarding.
Confirm that you have a valid E5 license and Start Onboarding.![]() On the Step 1 Permissions page, review the type of onboarding you need and their capabilities and click Next Authentication.
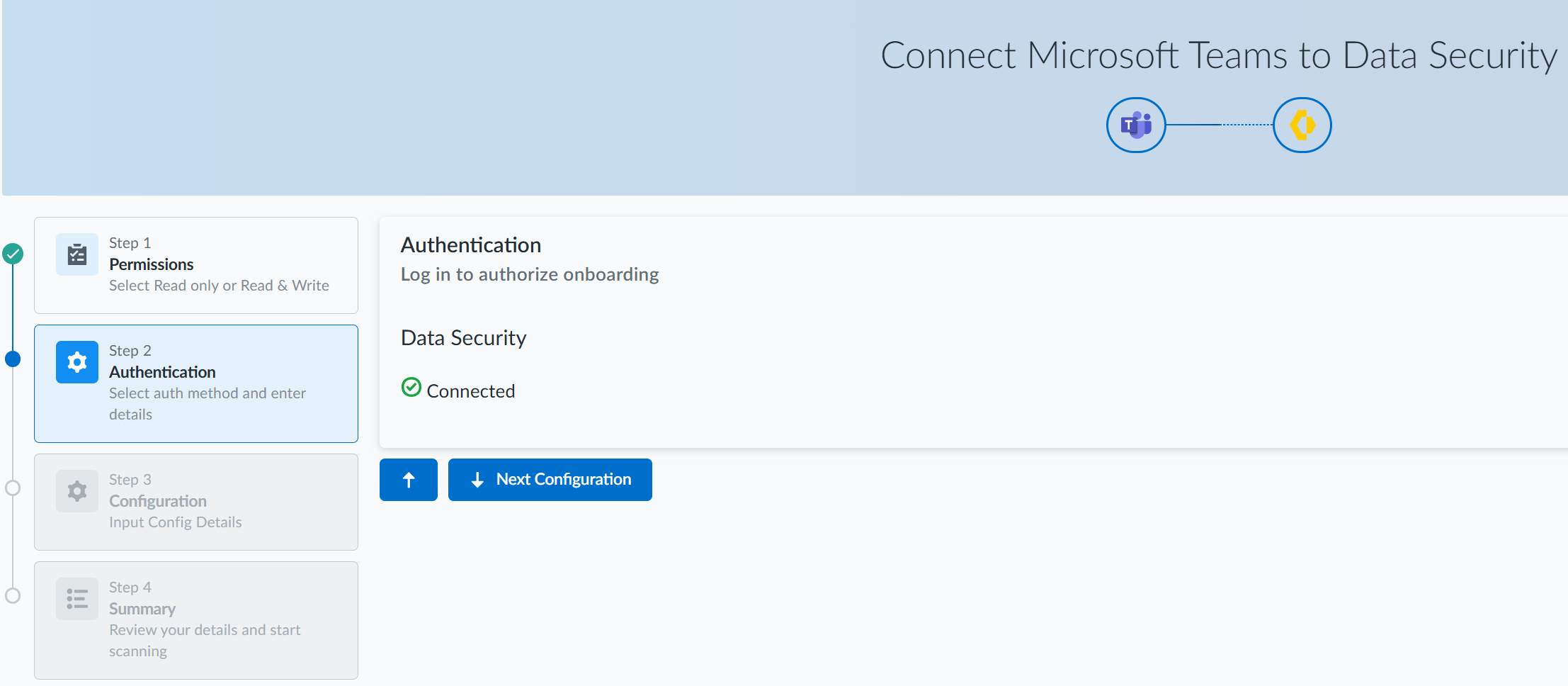
On the Step 1 Permissions page, review the type of onboarding you need and their capabilities and click Next Authentication.![]() On the Step 2 Authentication page, select the type of permissions you want to use during onboarding and Connect.
On the Step 2 Authentication page, select the type of permissions you want to use during onboarding and Connect.![]() If you choose Read_Write Permissions, you can perform the following actions:
If you choose Read_Write Permissions, you can perform the following actions:- Data Discovery
- User Activity
- Remediation
If you choose Read Permissions, you cannot perform remediation actions. Only the following two actions are available:- Data Discovery
- User Activity
Enter the login credentials for the account with Global admin role privileges on the Microsoft online page to which Data Security redirects you.Review and Accept the permissions requested.The permissions requested are different for onboarding using Read_Write Permissions and Read Permissions. Data Security requires these permissions to scan your assets on Office 365.![]() On successful authentication, click Next Configuration.
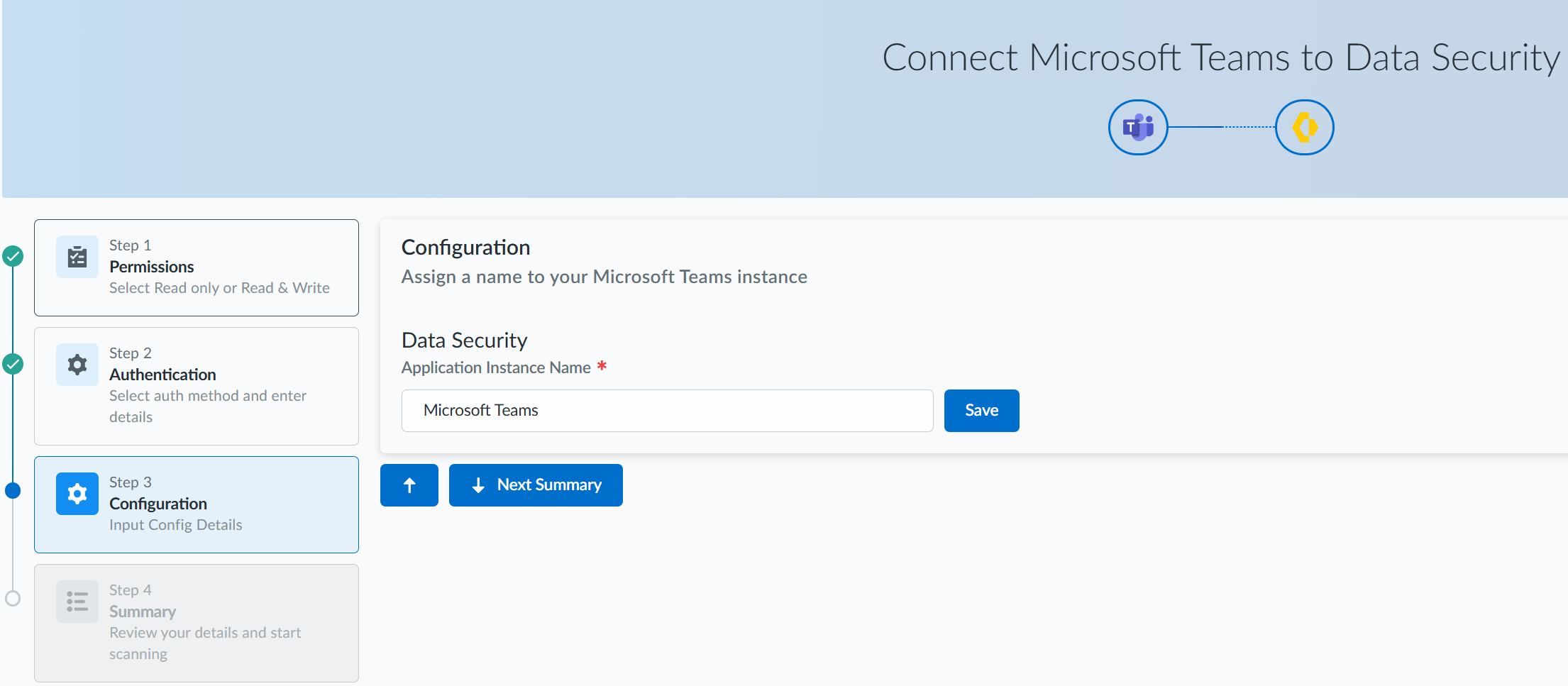
On successful authentication, click Next Configuration.![]() In the Step 3 Configuration page, specify a name for your Microsoft Teams instance, save it, and click Next Summary.
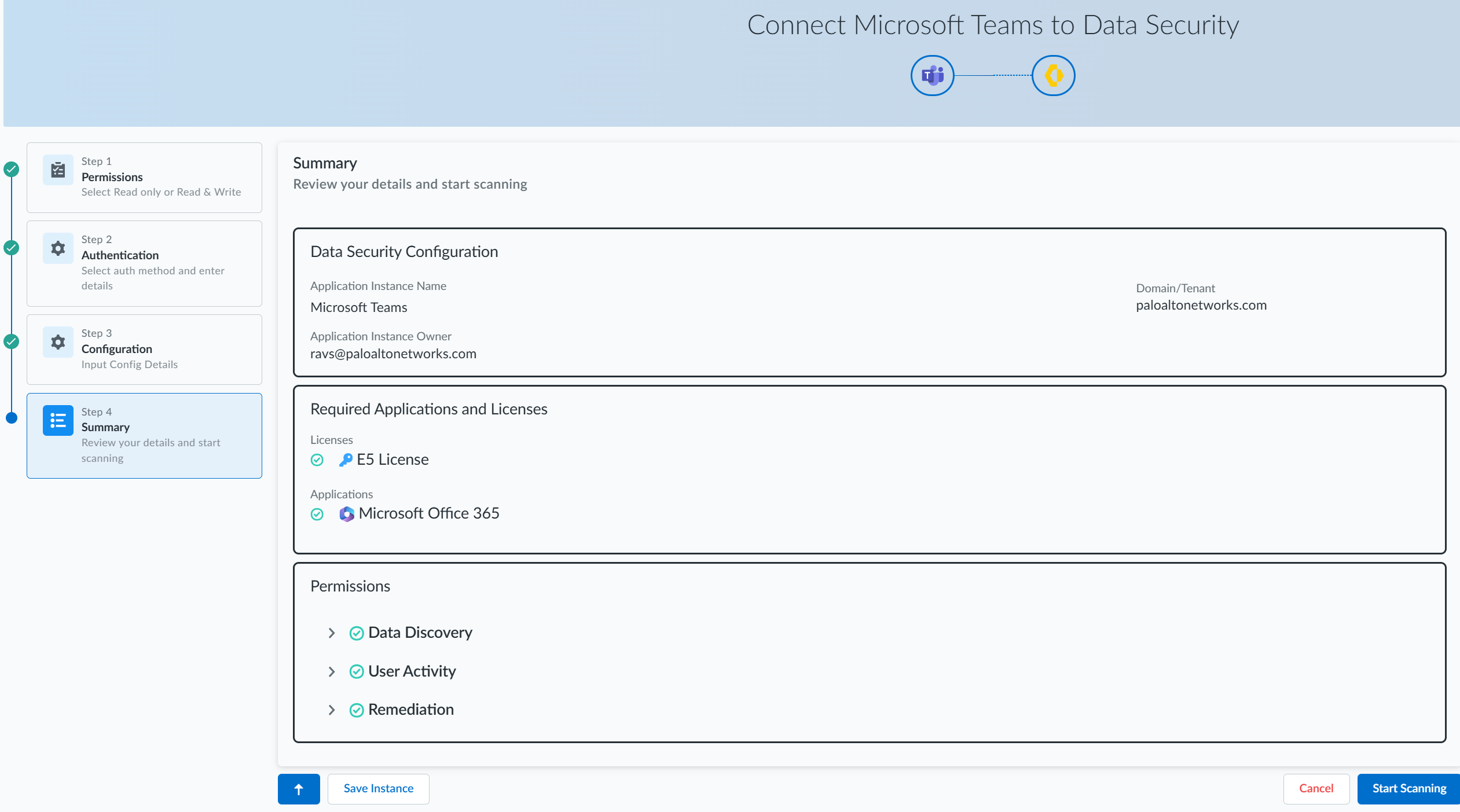
In the Step 3 Configuration page, specify a name for your Microsoft Teams instance, save it, and click Next Summary.![]() In the Step 4 Summary page, review your details. You can either save your instance or Start Scanning.
In the Step 4 Summary page, review your details. You can either save your instance or Start Scanning.![]()
Troubleshooting Onboarding for Microsoft Teams App
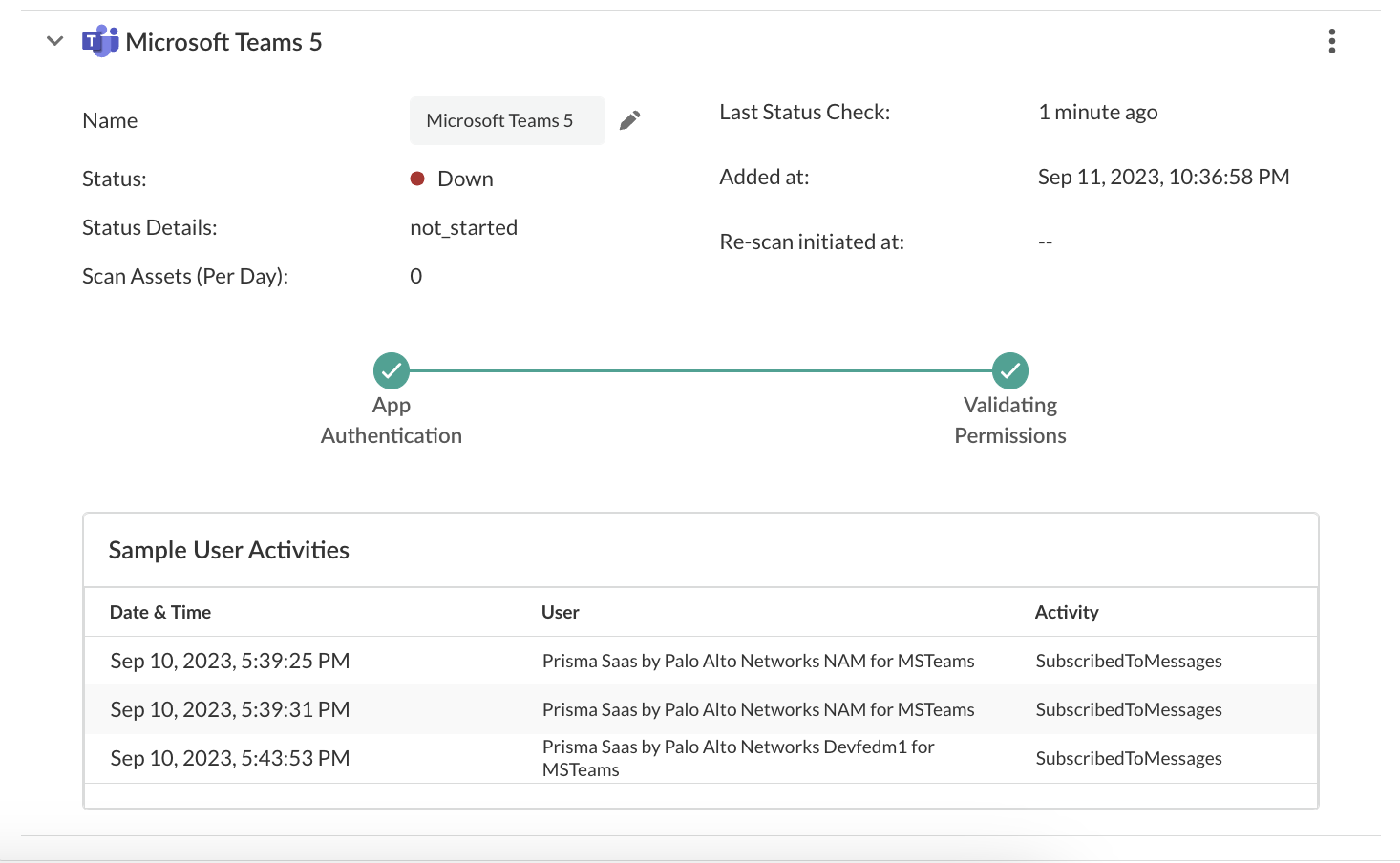
To ensure that your app has onboarded correctly without any issues in authentication or permissions, Data Security performs validation checks between the onboarding and scanning process. You can start scanning only after a successful validation. For Microsoft Teams, the following two validations happen:- App Authentication
- Validating Permissions
After the validation is successful, Data Security displays the sample user activities.![]() If the App Authentication or Validating Permissions checks fail, try the following:
If the App Authentication or Validating Permissions checks fail, try the following:- Ensure you have administrator permissions.
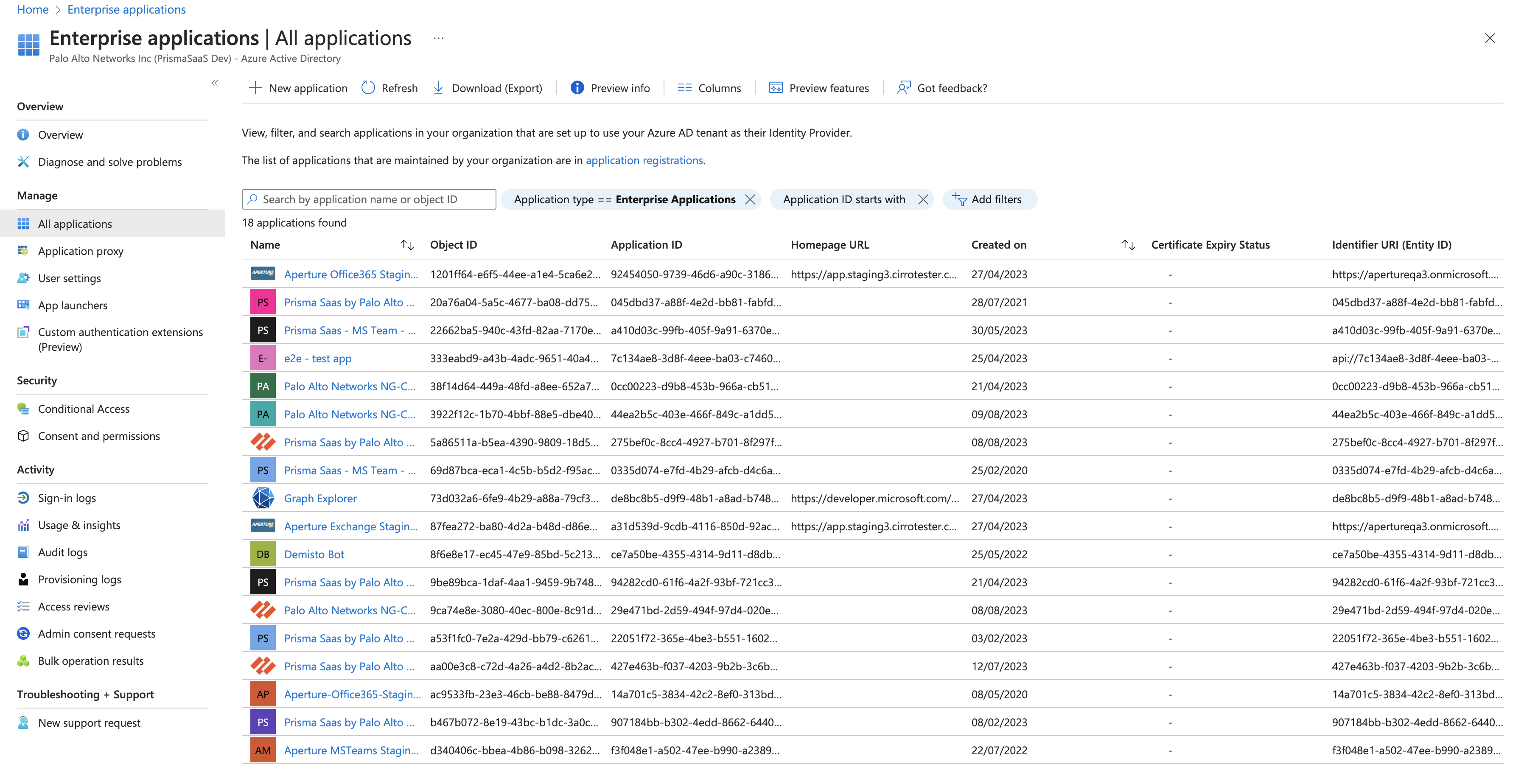
- Check if Palo Alto Networks application is listed in the list of Enterprise
Applications. Following are the app names for specific regions:
- Prisma SaaS by Palo Alto Networks AP1 for MSTeams
- Prisma SaaS by Palo Alto Networks EU1 for MSTeams
- Prisma SaaS by Palo Alto Networks IN for MSTeams
- Prisma SaaS by Palo Alto Networks NAM for MSTeams
- Prisma SaaS by Palo Alto Networks UK1 for MSTeams
- Palo Alto Networks NG-CASB - AUS - Teams
![]()
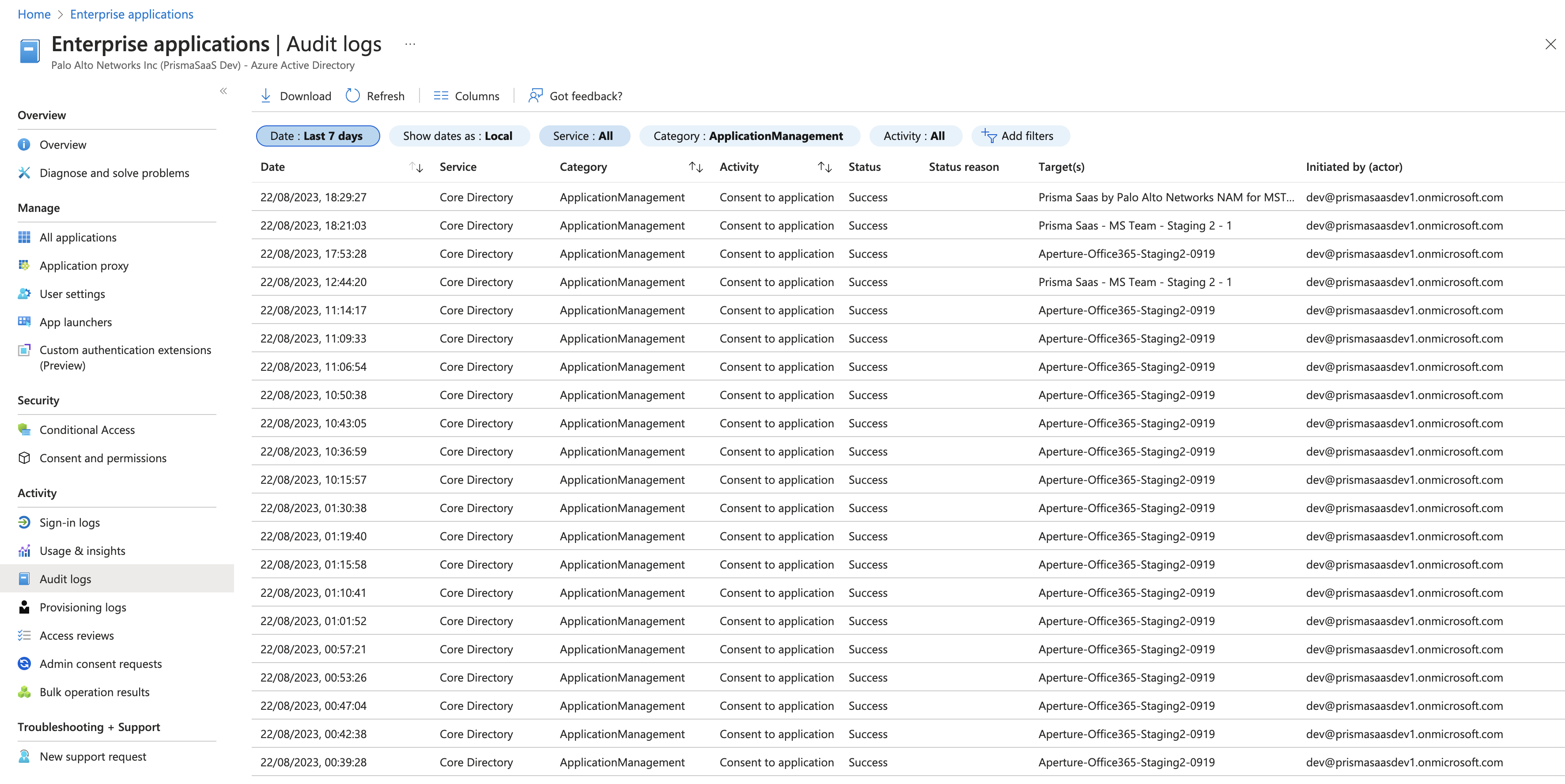
- If a Palo Alto Networks application isn’t listed, check if the Audit Logs
Activity displays as Consent to application, Target as
<app from the list given above>, and Status as
Success.
![]()
See the following table to understand the errors you are facing during validation.Error CodesDescriptionErrors in App Authenticationinvalid_requestRequest is invalid.invalid_grantInternal error encountered.unauthorized_clientThe installed app in the Marketplace was uninstalled manually from your cloud app.invalid_clientIssue related to Marketplace instance.temporarily_unavailableMicrosoft Teams app issue on the server side. Please reinstall.Errors in fetching sample assets and activitiesaccessDeniedAccess is denied for ${user}.activityLimitReachedApp's API limit reached. Try after sometime.invalidRangeYou don't have any thing to get for this entity.invalidRequestRequest is invalid.itemNotFoundNo data associated with this entity.notAllowedAuthentication failure while retrieving the entity.notSupportedGetting entity with required information is no longer supported.serviceNotAvailableMicrosoft Teams server is not responding.quotaLimitReachedQuota for app request has been exhausted for now.unauthenticatedMicrosoft Teams app issue from server side.If the issue persists, contact SaaS Security Technical Support.Start Scanning and Monitor Results
When you add a new cloud app, then enable scanning, Data Security automatically scans the cloud app against the default data patterns and displays the match occurrences. You can take action now to improve your scan results and identify risks.- To start scanning the new Microsoft Teams app for risks, select ConfigurationSaaS SecurityData SecurityApplicationsMicrosoft TeamsView Settings...Start Scanning.Monitor the scan results.During the discovery phase, as Data Security scans files and matches them against enabled policy rules:
- Verify that Data Security displays assets.
- Verify that your default policy rules are effective. If the results don’t capture all risks or you see false positives, proceed to next step to improve your results.
(Optional) Modify match criteria for existing policy rules.(Optional) Add new policy rules.Consider the business use of your cloud app, then identify risks unique to your enterprise. As necessary, add new:(Optional) Configure or edit a data pattern.You can Configure Data Patterns to identify specific strings of text, characters, words, or patterns to make it possible to find all instances of text that match a data pattern you specify.