SaaS Security
View Usage Data for Unsanctioned SaaS Apps
Table of Contents
Expand All
|
Collapse All
SaaS Security Docs
-
-
- Begin Scanning an Amazon S3 App
- Begin Scanning a Bitbucket App
- Begin Scanning a Box App
- Begin Scanning ChatGPT Enterprise App
- Begin Scanning a Cisco Webex Teams App
- Begin Scanning a Confluence App
- Begin Scanning a Confluence Data Center App
- Begin Scanning a Dropbox App
- Begin Scanning a GitHub App
- Begin Scanning a Gmail App
- Begin Scanning a Google Chat App
- Begin Scanning a Google Cloud Storage App
- Begin Scanning a Google Drive App
- Begin Scanning a Jira App
- Begin Scanning a Jira Data Center App
- Begin Scanning a Microsoft Azure Storage App
- Begin Scanning a Microsoft Exchange App
- Begin Scanning a Microsoft Teams App
- Begin Scanning Office 365 Apps
- Begin Scanning a Salesforce App
- Begin Scanning a ServiceNow App
- Begin Scanning a ShareFile App
- Begin Scanning a Slack Enterprise App
- Begin Scanning a Slack for Pro and Business App
- Begin Scanning a Workday App
- Begin Scanning a Zendesk App
- Begin Scanning a Zoom App
- Perform Actions on Sanctioned Apps
- API Throttling
- Configure Classification Labels
- Microsoft Labeling for Office 365
- Google Drive Labeling
- Configure Phishing Analysis
- Configure WildFire Analysis
- Fine-Tune Policy
-
- What is an Incident?
- Filter Incidents
- Configure Slack Notification Alerts on Data Security
- Security Controls Incident Details
- Track Down Threats with WildFire Report
- Customize the Incident Categories
- Close Incidents
- Download Assets for Incidents
- View Asset Snippets for Incidents
- Modify Incident Status
- Email Asset Owners
- Generate Reports on Data Security
- Integrate CIE with Data Security
- Search in Data Security
-
-
- View Usage Data for Unsanctioned SaaS Apps
- SaaS Visibility Application Attributes
- How SaaS Security Inline Determines an App's Risk Score
- Identify Risky Unsanctioned SaaS Apps and Users
- Generate the SaaS Security Report
- Filter Unsanctioned SaaS Apps
-
- SaaS Policy Rule Recommendations
- App-ID Cloud Engine
- Guidelines for SaaS Policy Rule Recommendations
- Apply Predefined SaaS Policy Rule Recommendations
- Create SaaS Policy Rule Recommendations
- Enable SaaS Policy Rule Recommendations
- Monitor SaaS Policy Rule Recommendations
- Delete SaaS Policy Rule Recommendations
- Modify Active SaaS Policy Rule Recommendations
- Manage Enforcement of Rule Recommendations on Strata Cloud Manager
- Manage Enforcement of Rule Recommendations on Panorama
- Tag Discovered SaaS Apps
- Apply Tag Recommendations to Sanctioned Apps
- Change Risk Score for Discovered SaaS Apps
- Troubleshoot Issues on SaaS Security Inline
-
-
- Onboarding Overview for Supported SaaS Apps
- Onboard an Aha.io App to SSPM
- Onboard an Alteryx Designer Cloud App to SSPM
- Onboard an Aptible App to SSPM
- Onboard an ArcGIS App to SSPM
- Onboard an Articulate Global App to SSPM
- Onboard an Atlassian App to SSPM
- Onboard a BambooHR App to SSPM
- Onboard a Basecamp App to SSPM
- Onboard a Bitbucket App to SSPM
- Onboard a Bito AI App to SSPM
- Onboard a BlueJeans App to SSPM
- Onboard a Box App to SSPM
- Onboard a Bright Security App to SSPM
- Onboard a Celonis App to SSPM
- Onboard a Cisco Meraki App to SSPM
- Onboard a Claude App to SSPM
- Onboard a ClickUp App to SSPM
- Onboard a Codeium App to SSPM
- Onboard a Cody App to SSPM
- Onboard a Confluence App to SSPM
- Onboard a Contentful App to SSPM
- Onboard a Convo App to SSPM
- Onboard a Couchbase App to SSPM
- Onboard a Coveo App to SSPM
- Onboard a Crowdin Enterprise App to SSPM
- Onboard a Customer.io App to SSPM
- Onboard a Databricks App to SSPM
- Onboard a Datadog App to SSPM
- Onboard a DocHub App to SSPM
- Onboard a DocuSign App to SSPM
- Onboard a Dropbox Business App to SSPM
- Onboard an Envoy App to SSPM
- Onboard an Expiration Reminder App to SSPM
- Onboard a Gainsight PX App to SSPM
- Onboard a GitHub Enterprise App to SSPM
- Onboard a GitLab App to SSPM
- Onboard a Google Analytics App to SSPM
- Onboard a Google Workspace App to SSPM
- Onboard a GoTo Meeting App to SSPM
- Onboard a Grammarly App to SSPM
- Onboard a Harness App to SSPM
- Onboard a Hellonext App to SSPM
- Onboard a Hugging Face App to SSPM
- Onboard an IDrive App to SSPM
- Onboard an Intercom App to SSPM
- Onboard a Jira App to SSPM
- Onboard a Kanbanize App to SSPM
- Onboard a Kanban Tool App to SSPM
- Onboard a Krisp App to SSPM
- Onboard a Kustomer App to SSPM
- Onboard a Lokalise App to SSPM
- Onboard a Microsoft 365 Copilot App to SSPM
- Onboard a Microsoft Azure AD App to SSPM
- Onboard a Microsoft Exchange App to SSPM
- Onboard a Microsoft OneDrive App to SSPM
- Onboard a Microsoft Outlook App to SSPM
- Onboard a Microsoft Power BI App to SSPM
- Onboard a Microsoft SharePoint App to SSPM
- Onboard a Microsoft Teams App to SSPM
- Onboard a Miro App to SSPM
- Onboard a monday.com App to SSPM
- Onboard a MongoDB Atlas App to SSPM
- Onboard a MuleSoft App to SSPM
- Onboard a Mural App to SSPM
- Onboard a Notta App to SSPM
- Onboard an Office 365 App to SSPM
- Onboard Office 365 Productivity Apps to SSPM
- Onboard an Okta App to SSPM
- Onboard an OpenAI App to SSPM
- Onboard a PagerDuty App to SSPM
- Onboard a Perplexity App to SSPM
- Onboard a Qodo App to SSPM
- Onboard a RingCentral App to SSPM
- Onboard a Salesforce App to SSPM
- Onboard an SAP Ariba App to SSPM
- Onboard a ServiceNow App to SSPM
- Onboard a Slack Enterprise App to SSPM
- Onboard a Snowflake App to SSPM
- Onboard a SparkPost App to SSPM
- Onboard a Tableau Cloud App to SSPM
- Onboard a Tabnine App to SSPM
- Onboard a Webex App to SSPM
- Onboard a Weights & Biases App to SSPM
- Onboard a Workday App to SSPM
- Onboard a Wrike App to SSPM
- Onboard a YouTrack App to SSPM
- Onboard a Zendesk App to SSPM
- Onboard a Zoom App to SSPM
- Onboarding an App Using Azure AD Credentials
- Onboarding an App Using Okta Credentials
- Register an Azure AD Client Application
- View the Health Status of Application Scans
- Delete SaaS Apps Managed by SSPM
-
-
-
- New Features Introduced in December 2024
- New Features Introduced in November 2024
- New Features Introduced in October 2024
- New Features Introduced in August 2024
- New Features Introduced in July 2024
- New Features Introduced in June 2024
- New Features Introduced in May 2024
- New Features Introduced in April 2024
- New Features Introduced in March 2024
- New Features Introduced in January 2024
-
- New Features Introduced in November 2023
- New Features Introduced in October 2023
- New Features Introduced in September 2023
- New Features Introduced in August 2023
- New Features Introduced in July 2023
- New Features Introduced in June 2023
- New Features Introduced in May 2023
- New Features Introduced in April 2023
- New Features Introduced in March 2023
- New Features Introduced in January 2023
-
- New Features Introduced in December 2021
- New Features Introduced in October 2021
- New Features Introduced in September 2021
- New Features Introduced in August 2021
- New Features Introduced in July 2021
- New Features Introduced in June 2021
- New Features Introduced in May 2021
- New Features Introduced in March 2021
- New Features Introduced in January 2021
View Usage Data for Unsanctioned SaaS Apps
Get visibility into untrusted SaaS apps that your employees are using.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
Or any of the following licenses that include the SaaS Security Inline license:
|
SaaS Security Inline identifies the SaaS apps that your employees are using by inspecting
network traffic populated from Strata Logging Service logs.
For comprehensive results, wait up to 24 hours after you activate SaaS Security Inline
on your platform to gain insight into your SaaS apps.
- Log in to Strata Cloud Manager.
- Select ManageConfigurationSaaS Security.
- Select one of the following views:ViewShows You:Helps You:Dashboard ViewGraphical view that summarizes the overall usage of SaaS apps that are in use in your organization.Assess your overall security posture before you drill down into risk data for individual SaaS apps.Discovered Applications ViewList view of SaaS apps in use in your organization.Learn about the SaaS apps that are in use and how many users are accessing them. Use the filter and sort capabilities to analyze metrics and App Details to assess risks.Discovered Users ViewList view of users in your SaaS app ecosystem and their individual, aggregated SaaS app usage.Learn about the users who are accessing discovered SaaS apps. You can filter users by SaaS apps that are important to your organization (for example, high risk apps or social media apps).Application Detail ViewDetail view with risk factors (attributes) for the SaaS apps in use in your organization.Drill down into individual SaaS apps in use in your organization to view details about the SaaS app, its app vendor, and compliance with regulatory standards.Application Dictionary ViewCatalog of SaaS apps with the ability to drill down into attributes for numerous industry-wide SaaS apps and those currently in use in your organization.Data includes information about the app, vendor, compliance, and risk characteristics that underlie those SaaS apps.Research the SaaS app, its vendor, and compliance with regulatory standards, then evaluate the risk for a given SaaS app to your organization before you decide to tag it as a sanctioned SaaS app.Policy Recommendations ViewSaaS policy rule recommendations enable you to recommend Security policy rules to your Palo Alto Networks firewall administrator.Remediate risks of unsanctioned SaaS apps and user risky behavior.
Dashboard View
The SaaS Visibility Dashboard view summarizes the overall usage of SaaS
apps that are in use in your organization, the risk score for these SaaS apps, and
the number of users who are using them.
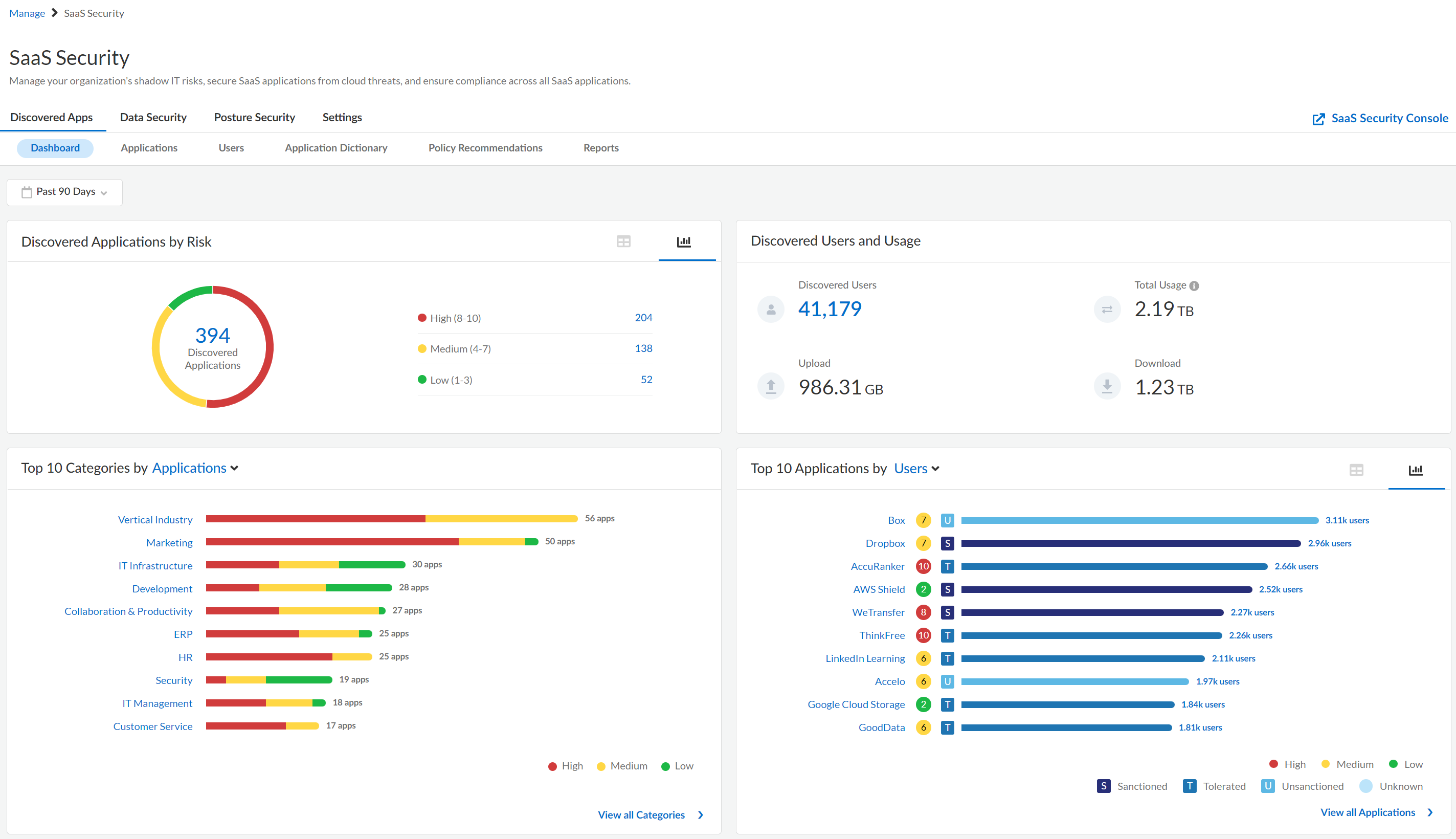
The following table describes the areas of the Dashboard view.
Dashboard | |
|---|---|
Time Range | Filter the dashboard to view overall usage
within a particular time range. You can filter the dashboard to
view usage for the last 7, 30 or 90 days. The default time range
is 90 days for new sessions. |
| Applications by Risk | Discovered SaaS app by risk level.
Move your cursor over each circle bar to display the number of
associated SaaS apps within each risk level. Display the data
using the icons provided:
|
| Top 10 Categories by Applications | Categories with
the most Usage and Applications . View
all Categories to navigate to the complete Discovered Applications . |
| Top 10 Applications by Usage | SaaS apps with the most Usage and Users of SaaS
apps in your app ecosystem. View all
Applications to navigate to the list of Discovered
Applications . |
Discovered Applications View
This Discovered Applications view displays a list of SaaS apps that are in
use in your organization, as well as their risk and usage details.
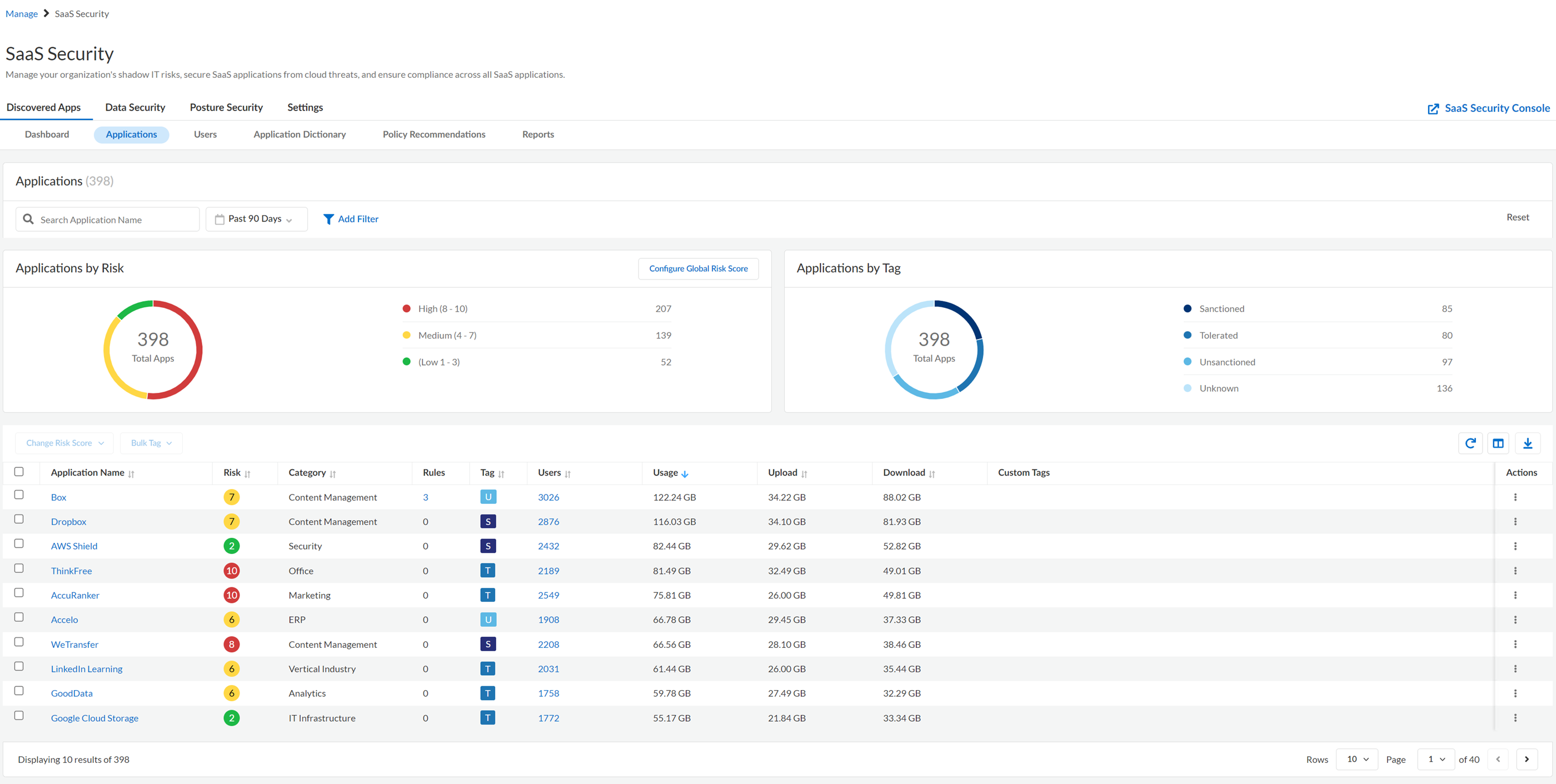
The following table describes the areas of the Discovered Applications view.
Discovered Applications | |
|---|---|
Filter by Time Range: Risk,
Category,
Tags, Rules,
Custom Tags to render a data set for
the selected time frame. Your filter selection persists across
the session. Default time range is 90 days for new sessions. | |
Applications by Risk | Graph that displays the total number of SaaS apps in your organization that are
Low, Medium,
or High
risk
score. |
Applications by Tag | Graph that displays the total number of SaaS apps in your organization by tag. |
Configure Global Risk Score | Capability to assign
unequal weights to the attributes that underlie each SaaS app’s
risk score. |

| Search SaaS apps in use by Application Name
only. |
Bulk Tag | Tags to help you assign a
policy decision to your selected SaaS apps. This action is
available only after you select one or more apps in the
table. |
Change Risk Score | Change the risk score
for the selected SaaS app. This action is available only after
you select one or more apps in the table. |
Download CSV | Export of the results (data set) of the Discovered SaaS apps in CSV file format. To view this element you
must be Super Admin role or Admin role, and not Read Only Admin
role. |
|
Tag Recommendations
| The Tag Recommendations action is displayed only if you activated the Cloud Identity Engine on your tenant, and configured directory sync in Cloud Identity Engine for Azure AD or Okta Directory. When these conditions are met, SaaS Security Inline can provide tagging recommendations. Specifically, SaaS Security Inline uses information from the Cloud Identity Engine to determine if a detected app is an enterprise app accessible through your identity provider. If the app is an enterprise app, SaaS Security Inline will recommend that you tag the app as Sanctioned. |
Application Name | SaaS app name as it’s known in the industry. |
Risk | Default, manual, or custom risk score
for the SaaS app. |
|
Tenants
|
If SaaS Security Inline supports tenant-level detection for
the SaaS Application, the number of separate app instances or
tenants that were accessed by users. Click on the link to go to
the Tenant Details view, which lists all of the tenants for the
SaaS app.
Because PAN-OS can detect individual
tenants only from unencrypted traffic, SSL decryption must be
enabled on the firewall. If SSL decryption isn’t enabled on the
firewall, or if tenant-level detection isn’t supported for the
SaaS app, this column displays 0. |
Category | SaaS app’s service category. For example, Google Meet is categorized as Internet
Conferencing. |
Rules | SaaS policy rule
recommendations that apply to the SaaS app. |
Tag | Tags that you assigned to
these SaaS apps. If you have not tagged a SaaS app, it's
automatically tagged as Unknown. |
Users | Displays the total number of users of the SaaS app.
Click on the link to go to the Discovered Users view with the
necessary filters applied to display a list of those users and
related activity. From this Discovered View, you can export a
list of the usernames. |
Usage | Number
of bytes transferred for the selected app. |
Upload | Number of bytes uploaded for the selected
app. |
Download | Number of bytes downloaded for the selected
app. |
Custom Tags | Tags that you
assigned to the SaaS app. |
Actions | Actions
to:
|
|
|
Give App Feedback icon. Click this icon to send us feedback about
the app and attribute information that is displayed in SaaS Security Inline. For example, you can notify us of
outdated attributes or adjustments you think we should make to
an app's risk
score. You can also request new apps or attributes.
Our app research team will review all feedback and will schedule
product updates on an individual basis. You can submit feedback
up to 10 times each day.
|
Discovered Users View
The Discovered Users view displays a list of known users in your
organization and their app usage aggregated across all discovered SaaS apps from
which you can apply filters to customize the view.
SaaS Security Inline discovers users by using Strata Logging Service
logs, specifically the source_user_info field. If the firewall
forwards a log to Strata Logging Service and this field isn’t populated for a
given user, SaaS Security Inline considers that user unknown.
The SaaS Security web interface excludes all app usage data for unknown users.
If you activated the Cloud Identity Engine on your
tenant and configured directory sync in Cloud Identity Engine for one or more instances
of Azure AD, SaaS Security Inline attempts to match the users it discovered
from Strata Logging Service logs with user information from Azure AD. If SaaS Security Inline can match the discovered users to Azure AD information,
SaaS Security Inline gets additional details about the user, such as the
user's department, region, and manager.

The following table describes the areas of the Discovered Users view.
Discovered Users | |
|---|---|
Add Filter |
Filter by Time Range to render a data set
for the selected time frame. Your filter selection persists
across the session. Default time range is 90 days for new
sessions.
Add additional filters to filter by user attributes, such as Apps
Used, Tenants, and Users. Some filters apply to user information
that SaaS Security Inline obtains from Azure AD through
the Cloud Identity Engine. These filters include filters for a
user's Role, Department, and Region.
|
User Name | Sort the column to display users alphabetically. |

| Search that enables you to identify distinct
users across filtered and unfiltered apps. |
| Applications Used | The number of apps that the user accessed. Click on the number of apps to drill down into details about the apps. |
|
Tenants
|
If SaaS Security Inline supports tenant-level detection for
the SaaS app, the number of separate app instances or tenants
that were accessed by the user. Click on the link to go to the
Tenant Details view, which lists all of the SaaS app tenants
that the user accessed.
Because PAN-OS can detect individual
tenants only from unencrypted traffic, SSL decryption must be
enabled on the firewall. If SSL decryption isn’t enabled on the
firewall, or if tenant-level detection isn’t supported for the
SaaS app, this column displays 0. |
Sessions | Total number of login sessions across filtered
and unfiltered apps. |
Total Usage | Number
of bytes transferred by the user across filtered or unfiltered apps. |
Upload | Number of bytes uploaded by the user across
filtered or unfiltered apps. |
Download | Number of bytes downloaded by the user across
filtered or unfiltered apps. |
Last Session | Last session initiated by the specific user. |
|
Email
|
The user's email address. SaaS Security Inline obtains this
information from Azure AD through the Cloud Identity Engine. This
column displays only if the Cloud Identity Engine is activated on
your tenant.
|
|
Active Directory Account
|
If SaaS Security Inline obtained additional information
about the user from Azure AD through the Cloud Identity Engine, the
name of the Azure AD instance that contains the user
information.
|
|
Role
|
The user's role within your organization. SaaS Security Inline obtains this information from Azure
AD through the Cloud Identity Engine. This column displays only if
the Cloud Identity Engine is activated on your tenant.
|
|
Department
|
The department to which the user belongs. SaaS Security Inline obtains this information from Azure
AD through the Cloud Identity Engine. This column displays only if
the Cloud Identity Engine is activated on your tenant.
|
|
Region
|
The user's country or region of residence. SaaS Security Inline obtains this information from Azure
AD through the Cloud Identity Engine. This column displays only if
the Cloud Identity Engine is activated on your tenant.
|
|
Manager Name
|
The user's manager. SaaS Security Inline obtains this
information from Azure AD through the Cloud Identity Engine. This
column displays only if the Cloud Identity Engine is activated on
your tenant.
|
Download CSV | Export the results (data set) for all users to a CSV file. To view this element you must be Super
Admin role or Admin role, and not Read Only Admin role. |
Application Detail View
The Application Detail view displays details about the app, app vendor,
and compliance with regulatory standards for the selected SaaS app that is in use in
your organization.
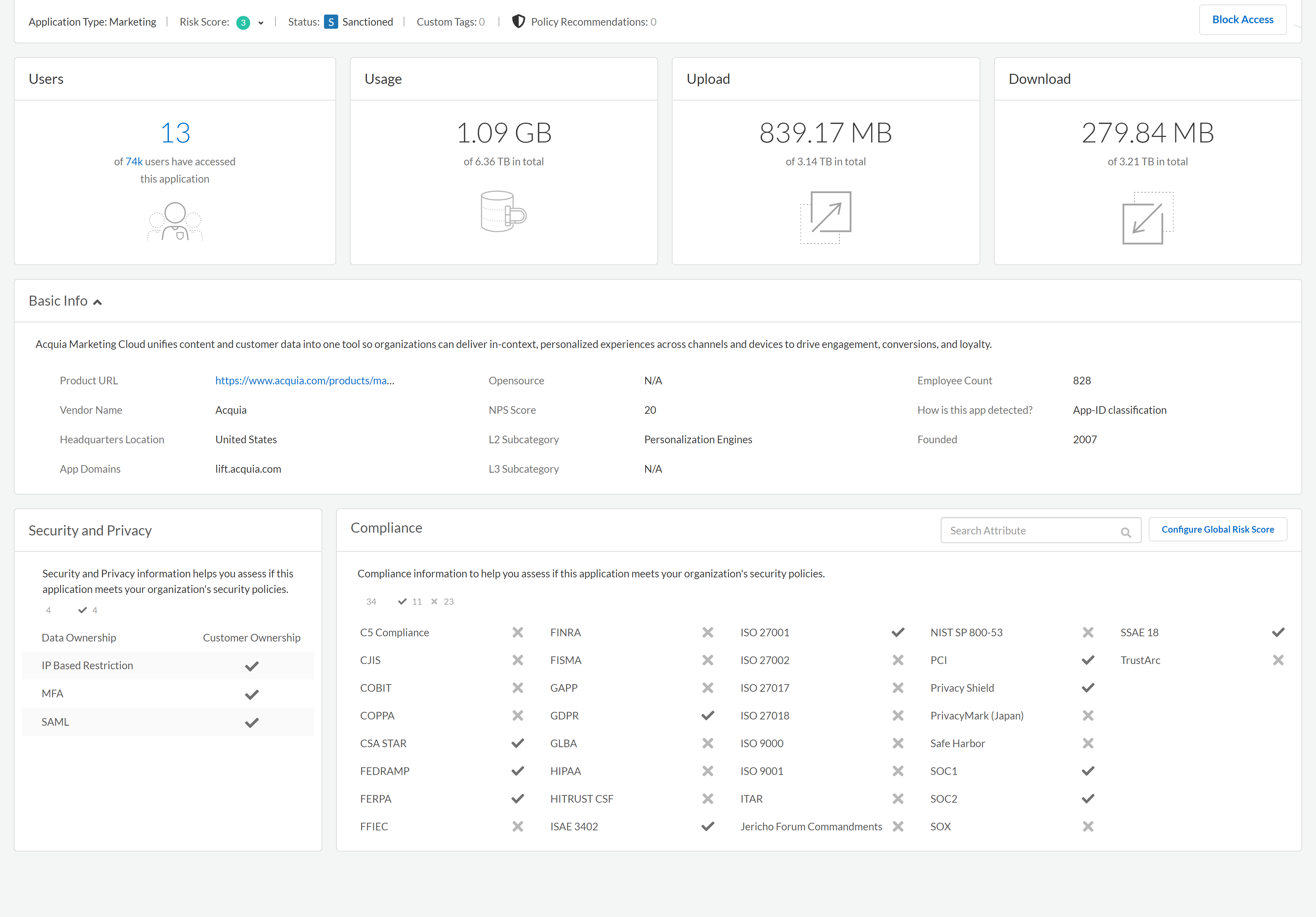
Application Detail | |
|---|---|
Application Type | Product’s
service category. For example, SugarCRM is categorized as ERP. |
Risk Score | Displays the risk score
for the SaaS app. |
Status | Default Tag (aka Sanctioned
Status) that you assigned to the SaaS app. |
Custom Tags | Tags that you assigned to
the SaaS app. |
Policy Recommendations | Recommendations that define this SaaS app. |
Block Access | Quick method to create a recommendation that blocks access to this SaaS
app. |
Users | Total number of users of the selected SaaS app. |
Usage | Total volume of traffic, both uploads and downloads, transferred by users of the selected the
SaaS app. |
Upload | Total number of bytes uploaded for the selected SaaS app. |
Download | Number of bytes downloaded by the user across
filtered or unfiltered apps. |
Basic Info | Vendor and market information about this SaaS app, including NPS. |

| Search that enables you to find compliance
attributes by name of a specific compliance regulation, standard,
framework, or certification. |
Configure Global Risk Score | Capability to assign
unequal weights to the attributes that underlie each SaaS app’s
risk score. |
Security and Privacy | Security
attributes to help you assess if this SaaS app meets
your organization’s security policies. |
Compliance | Compliance
information to help you assess if this SaaS app meets
your organization’s security policies. |
Risk Score | SaaS app’s risk score . |
|
|
Give App Feedback icon. Click this icon to send us feedback about
the app and attribute information that is displayed in SaaS Security Inline. For example, you can notify us of
outdated attributes or adjustments you think we should make to
an app's risk
score. You can also request new apps or attributes.
Our app research team will review all feedback and will schedule
product updates on an individual basis. You can submit feedback
up to 10 times each day.
|
Application Dictionary View
The Application Dictionary view simplifies the process of identifying SaaS
apps that are security risks. You can use this dictionary as an impartial security
analysis to help you evaluate a given SaaS app.
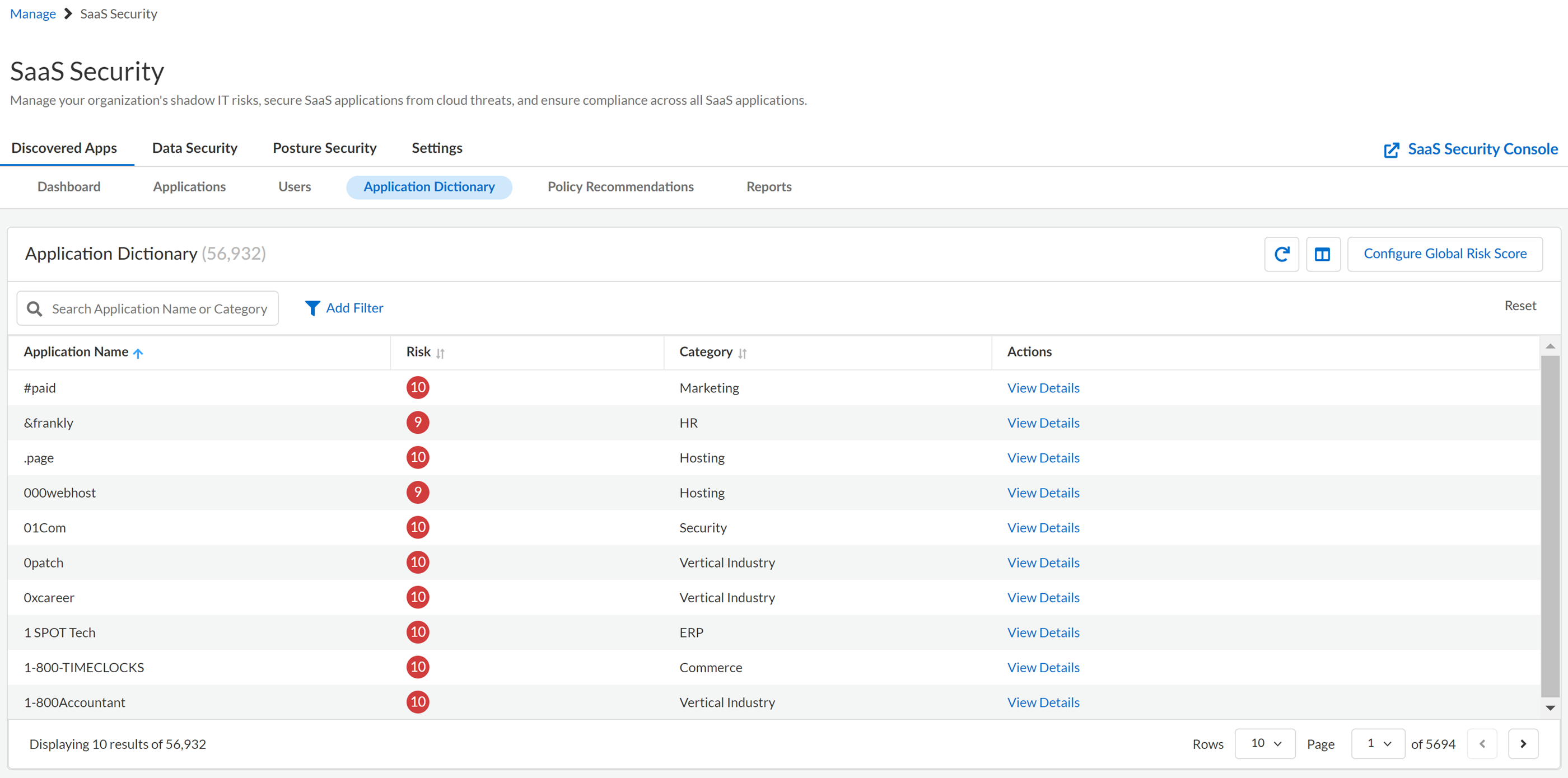
The following table describes the areas of the Application Dictionary view.
Application Dictionary | |
|---|---|
View Details | Displays App Details for the SaaS app, including
SaaS app characteristics such as Vendor
Attributes and Compliance
Attributes. |
| Application Name | The SaaS app name as it’s known in the industry. |
| Risk | Displays the risk score
for the SaaS app. |
| Category | Product’s
service category. For example, SugarCRM is categorized as ERP. |

| Search that enables you to find SaaS apps by category and
Application
Name . |
|
|
Give App Feedback icon. Click this icon to send us feedback about
the app and attribute information that is displayed in SaaS Security Inline. For example, you can notify us of
outdated attributes or adjustments you think we should make to
an app's risk
score. You can also request new apps or attributes.
Our app research team will review all feedback and will schedule
product updates on an individual basis. You can submit feedback
up to 10 times each day.
|
Policy Recommendations View
The Policy Recommendations view
enables you to filter on or search for the SaaS rule recommendations you
created or edited and determine if those rules were approved by
your firewall administrator or pending.
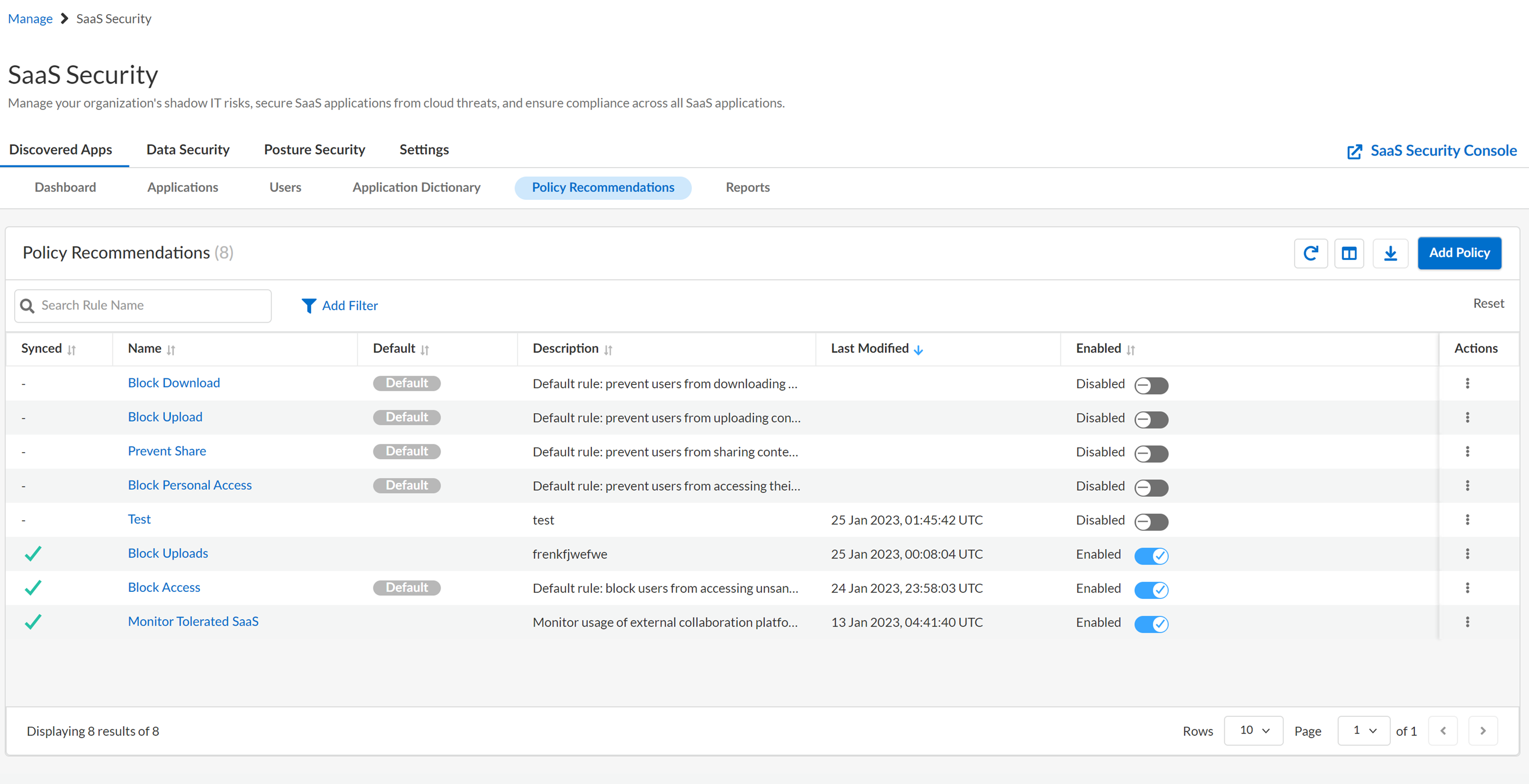
The following table describes the areas of the Policy Recommendations view.
Policy Recommendations | |
|---|---|
Synced | Status that
indicates whether or not your firewall received the SaaS policy rule recommendations. |
Name | Name assigned to the SaaS policy rule recommendations. |
Default | Recommendation type |
Description | Description assigned to the SaaS policy rule recommendations. |
Last Modified | Date that indicates the last time you changed
the rule. |
Enabled | Toggle to submit your SaaS policy rule recommendations. |

| Keyword search that enables you to find SaaS policy rule recommendations that
you created. |
Download CSV | Export the results (data set) to a CSV file. To
view this element you must be Super Admin role or Admin role, and
not Read Only Admin role. |



