SaaS Security
How SaaS Security Inline Determines an App's Risk Score
Table of Contents
Expand All
|
Collapse All
SaaS Security Docs
How SaaS Security Inline Determines an App's Risk Score
An app's risk score is determined by a calculation that is applied to the app's
attribute values.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
Or any of the following licenses that include the SaaS Security Inline license:
|
We designed app risk scores to help you quickly assess the security posture of an app.
Because you might be using this information to determine whether to allow or block
access to an app, it's helpful to understand how SaaS Security Inline determines
the risk score. Ultimately, an app's risk score is determined by a calculation that is
based on the app's attribute values. But to understand the significance and accuracy of
the risk score, you should understand how we identify the app attributes, how we
determine the attribute values for each app, and how the calculation considers some
attributes to have a greater impact on risk scores than others.
For all apps, SaaS Security Inline
calculates a SaaS Risk Score from Compliance, Identity Access Management,
and Security and Privacy attribute values. For the subset of apps that are GenAI apps,
SaaS Security Inline also calculates a GenAI Risk Score from
GenAI attributes. For most apps, the
SaaS Risk Score is the app's risk score. For GenAI apps only, the app's risk score is
derived from both the SaaS Risk Score and the GenAI Risk Score, with more weight
given to the GenAI Risk Score.
To determine an app's risk score, the following actions are taken by Palo Alto Networks
and by SaaS Security Inline.
- Attribute Identification: Palo Alto Networks analyzes the current SaaS Security landscape to identify characteristics of SaaS apps that can impact an app's security posture. These characteristics are the attributes that we will identify for the SaaS apps that SaaS Security Inline can detect in your environment. These attributes are divided into the following categories based on how they can impact an app's security posture.
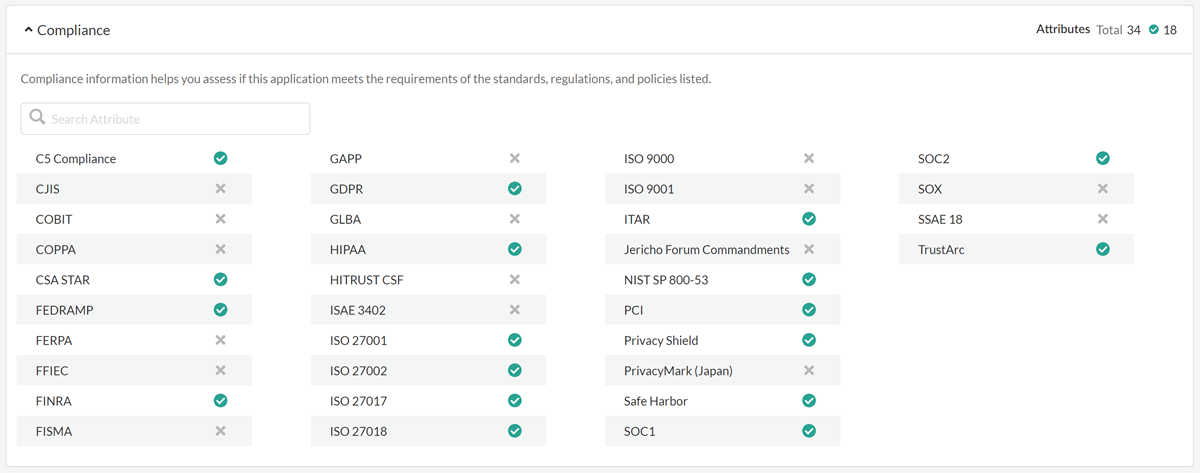
- Compliance attributes identify whether an app adheres to various regulatory
requirements and standards.
![]()
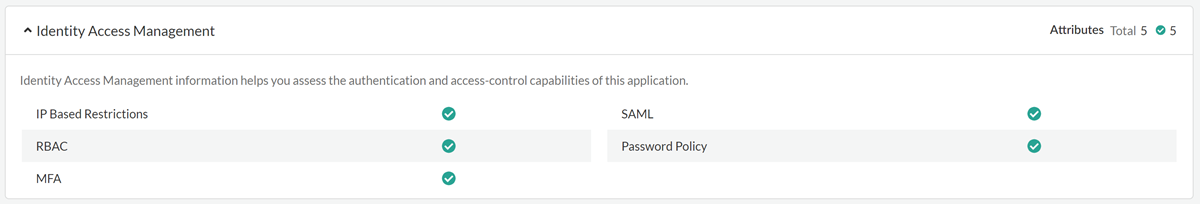
- Identity Access Management attributes identify an app's authentication and
access control capabilities.
![]()
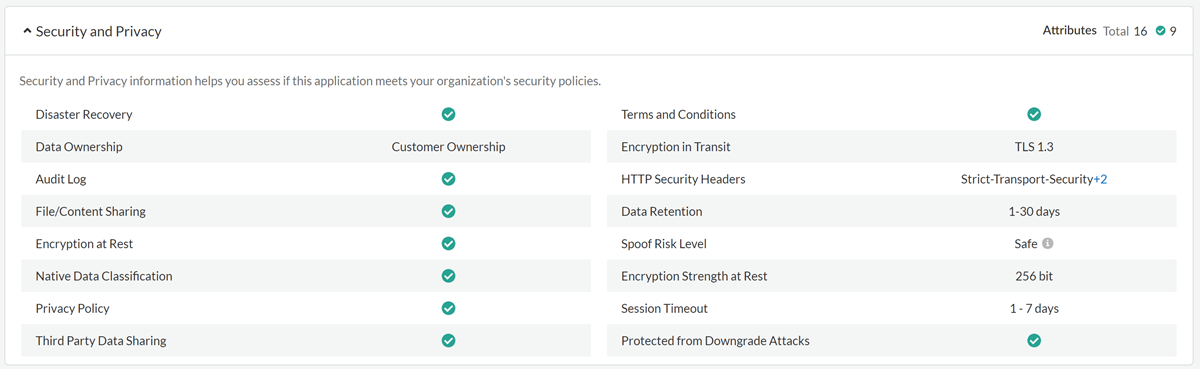
- Security and Privacy attributes identify product features for protecting
data.
![]()
Attribute Identification Updates: Palo Alto Networks's analysis of the SaaS Security landscape is ongoing. As new threats emerge, new app attributes are added to SaaS Security Inline. - Compliance attributes identify whether an app adheres to various regulatory
requirements and standards.
- Attribute Value Determination: For each SaaS app that can be detected by SaaS Security Inline, Palo Alto Networks determines the values to assign to the app attributes. Palo Alto Networks uses a variety of techniques to determine whether the SaaS app has the capabilities identified by the attributes. For many attributes, we rely on publicly available documentation to determine attribute values. This publicly available documentation includes a SaaS app's help documentation, privacy policy, and security documents. For other attributes, we examine the app domain or app traffic to determine attribute values.In most cases, the determination of attribute values is an automated process. For certain priority apps, we manually determine attribute values. We identify apps as priority apps based on app usage and user feedback.
- Compliance Attribute Determination: To determine these attribute values, we rely completely on the documentation and public links of the app.
- Identity Access Management Attribute Determination: To determine these attribute values, we rely mostly on the documentation and public links of the app. For a subset of apps that we have identified as priority apps, we access the app to determine attribute values.
- Security and Privacy Attribute Determination: We use several methods
to determine these attribute values. The method we use depends on the
particular attribute.
Attributes Attribute Determination Method - Data Ownership
- File/Content Sharing
- Audit Log
- Disaster Recovery
- Encryption at Rest
- Encryption Strength at Rest
- Native Data Classification
- Data Retention
- Privacy Policy
- Terms and Conditions
- Session Timeout
- Third Party Data Sharing
To determine values for these attributes, we rely completely on the documentation and public links of the app. Encryption in Transit We examine the SaaS app domain to identify the TLS versions that the app supports. HTTP Security Headers We analyze app traffic to identify whether the SaaS app is using security headers. Protected from Downgrade Attacks We examine the SaaS app domain to identify the TLS versions that the app supports. We also examine whether the SaaS app allows TLS 1.0 or TLS 1.1 connections. Spoof Risk Level We analyze the DMARC and SPF records for the SaaS app domain to determine the value for this attribute.
Attribute Value Determination Updates:- On a monthly basis, we identify new SaaS apps and add the apps to the app library. We determine the attribute values for these new apps.
- On a monthly basis, we manually verify attribute data for priority apps. If necessary, we update attribute values based on this research.
- On a monthly basis, we measure the accuracy of the attribute data collected by our automated processes. On a quarterly basis, we update our automated processes based on this research.
- On a quarterly basis, we collect and update attribute values for apps by using our updated automated processes.
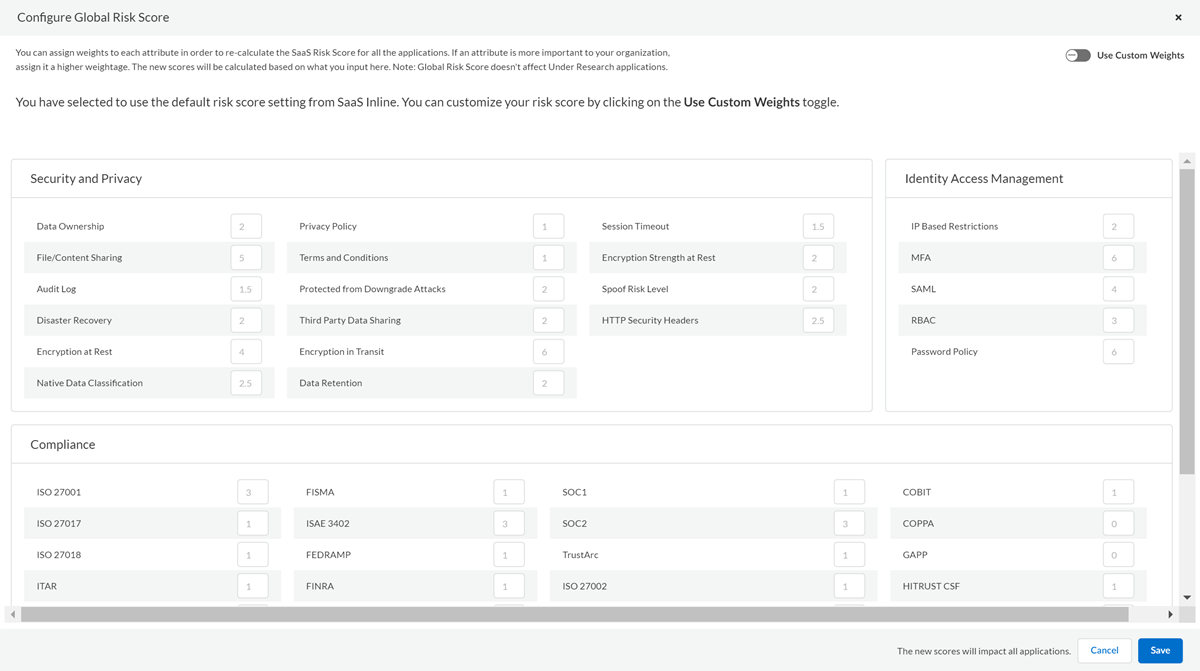
- Attribute Weight Assignment: We assign weights to app attributes, which will affect the risk score calculation. We assign each attribute a default weight from 0-100. As required by the risk score calculation, the combined weights for all of the attributes total 100.To assign default weights, we assess the security impact of the attribute categories and the individual attributes. Attributes that we consider to have a greater security impact are assigned greater weights, and will have a greater impact on an app's risk score. You can view the default weights from the SaaS Security Settings page (ConfigurationSaaS SecuritySettingsConfigureConfigure Global Risk Score). From this page, you can also adjust the weights assigned to attributes.
![]() Attribute Weight Assignment Updates: As we add attributes to SaaS Security Inline, we revise the attribute weight assignments, which in turn can affect the app risk scores. We might also update weight assignments if we determine that certain attributes should have a greater or lesser impact on an app's risk score.
Attribute Weight Assignment Updates: As we add attributes to SaaS Security Inline, we revise the attribute weight assignments, which in turn can affect the app risk scores. We might also update weight assignments if we determine that certain attributes should have a greater or lesser impact on an app's risk score. - Risk Score Calculation: SaaS Security Inline assigns a risk score for each app by completing the following actions:
- SaaS Security Inline assigns a risk score to each attribute based on the attribute value. The attribute value identifies an app characteristic that strengthens or weakens the app's overall security posture. If the value weakens the security posture, the attribute is assigned a higher risk score. For example, the MFA attribute value indicates whether an app offers multi-factor authentication (MFA). If the app does support MFA, the attribute is assigned the lowest risk score. However, if the attribute value indicates that the app does not offer MFA (or that MFA support cannot be derived from the app documentation), the attribute is assigned a higher risk score.
- To determine the app's overall risk score, SaaS Security Inline calculates the weighted average of the individual attribute risk scores. The weighted average is based on the weights that were assigned to the attributes.
- SaaS Security Inline scales the risk score within a range of 1-5, with 1 representing the lowest risk and 5 representing the greatest risk, and assigns the risk score to the app.
If you think there are adjustments that we should make to an app's risk score, send us feedback. To send us feedback, click on the following icon, which appears on the Application Dictionary, Discovered Applications, and Application Detail views.![]() In the Give App Feedback form, select Risk score adjustment as the Feedback Type.
In the Give App Feedback form, select Risk score adjustment as the Feedback Type.
GenAI Risk Score
For GenAI apps only, the risk score calculation considers GenAI attributes. SaaS Security Inline calculates a
separate GenAI Risk Score from the following attribute values. This GenAI risk score
is combined with the risk score calculated from the Compliance, Identity Access
Management, and Security and Privacy attributes, which is called the SaaS Risk
Score, to determine the GenAI apps final risk score.
- SaaS Security Inline determines the values for the following GenAI
attributes, which have the following assigned weights:
Attribute Weight Input Data Types 10% Output Data Types 15% Interface 10% Data Used in Model Training 45% Popularity 20% - SaaS Security Inline calculates the GenAI Risk Score based on these values
and then combines it with the SaaS Risk Score. The risk score calculation gives
more weight to the GenAI risk score.
Risk Score Weight GenAI Risk Score 70% SaaS Risk Score 30%