SaaS Security
Perform Actions on Sanctioned Apps
Table of Contents
Expand All
|
Collapse All
SaaS Security Docs
Perform Actions on Sanctioned Apps
Learn about the various actions that you can perform on Sanctioned Apps.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
Or any of the following licenses that include the Data Security license:
|
Learn more about the actions you can perform on sanctioned apps after you add them to
Data Security.
Start Scanning a Cloud App
Learn how to start scanning a recently onboarding cloud
app on Data Security.
After you onboard a cloud app, you must initiate
scanning on that cloud app so that Data Security can scan for
policy violations and data exposure. When you initiate scanning—known
as discovery or initial backward scan—Data Security scans all assets in the associated cloud app. During
the discovery process, Data Security also matches the assets
against enabled default policy
rules and identifies incidents. The time required to complete
the discovery process depends on the number of assets on your cloud
app. However, as soon as you begin to see the assets populate on
the Data Security Dashboard, you can assess
incidents.
After the discovery process completes, Data Security periodically queries for scannable root
entities (for example, user, channel, shared drive, etc.) that are not on its list
of known entities, and this scan frequency depends on the SaaS app, taking into
account optimal performance; however, Data Security scans most SaaS apps every 5
minutes and is able to do so without delay if Data Security hasn’t reached the
rate limit. Each cloud app has
unique entities for scanning purposes. When Data Security detects such entities,
two distinct scan processes trigger automatically:
- Forward scan—Process of scanning newly detected, scanable root entities after the point of detection. This process occurs automatically, and there is no way to manually trigger this process, nor do you need to.
- Backward scan—Process of scanning newly detected, scanable root entities before the point of detection. This process occurs automatically, and there is no way to manually trigger this process, nor do you need to.
- Log in to Strata Cloud Manager.Select ConfigurationSaaS SecurityData SecurityApplications<Your Application>View SettingsActionsStart Scanning.The status changes to Up.
Reauthenticate to a Cloud App
Learn how to reauthenticate.
When you connect Data Security to one
of your sanctioned SaaS applications, you must provide login credentials
that enable the service to establish a secure connection with the
cloud app. Data Security and the app maintain this secure connection
(in most cases using token-based authentication). In some cases,
you might need to reauthenticate to a cloud app when:
- Network—There is a network connectivity issue between the two services.
- Password—You changed the password associated with the
login account.Chrome caches credentials. Use an Incognito window to reauthenticate to avoid applying those cached credentials.
- Account—The administrator associated with the login account changed credentials to those associated with a different administrator.
- Permissions—You unintentionally revoked access permissions you formerly granted Data Security or the required permissions changed.
- Token expiration—Your SaaS app exceeded its RTL (Refresh Token Lifespan), which varies by SaaS application. 100 days is a common RTL. RTL is not configurable.
If you encounter authentication
errors when you retrieve a token for Data Security, see Authentication Errors.
Reauthentication is not applicable for the following SaaS
apps:
- Google Drive
- Gmail
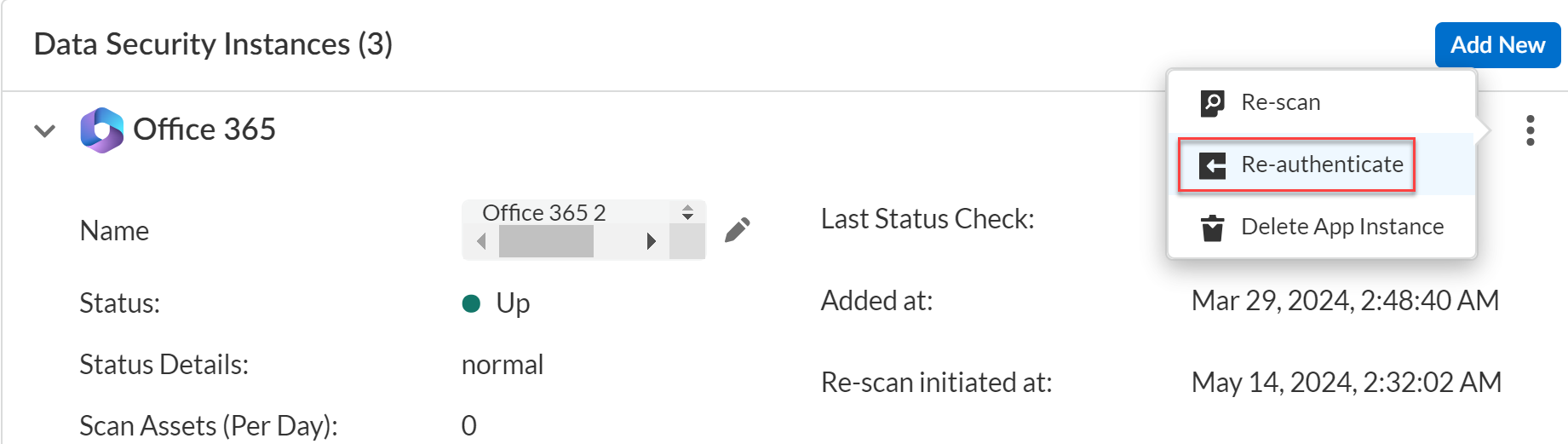
- Log in to Strata Cloud Manager.Select ConfigurationSaaS SecurityData SecurityApplications<Your Application>View SettingsVertical EllipsesRe-authenticate.
![]() Follow the same process to log in to the app that you did when you first added the app. See the specific app section in Onboard Sanctioned SaaS Apps to Data Security for details on what privileges are required for each app and for specific steps to successfully authenticate.To begin scanning the app after you successfully reauthenticate, select Vertical EllipsesStart Scanning.
Follow the same process to log in to the app that you did when you first added the app. See the specific app section in Onboard Sanctioned SaaS Apps to Data Security for details on what privileges are required for each app and for specific steps to successfully authenticate.To begin scanning the app after you successfully reauthenticate, select Vertical EllipsesStart Scanning.Verify Permissions on Cloud Apps
Learn how to verify permissions on cloud apps.A permission refresh is supported for the Gmail app, Box app, and Google Drive app.When you initially onboard a cloud app, Data Security automatically verifies that the administrator account has the necessary permissions. Additionally, using API calls to the cloud app, Data Security continues to periodically perform this check on a regular, scheduled basis. Although the cloud app in Data Security can indicate a Monitoring status, there might be an undetected permissions issue if permissions changed after the last health check.You might want to verify permissions outside this scheduled event if:- New assets are not displaying in Data Security.
- New incidents are not being created.
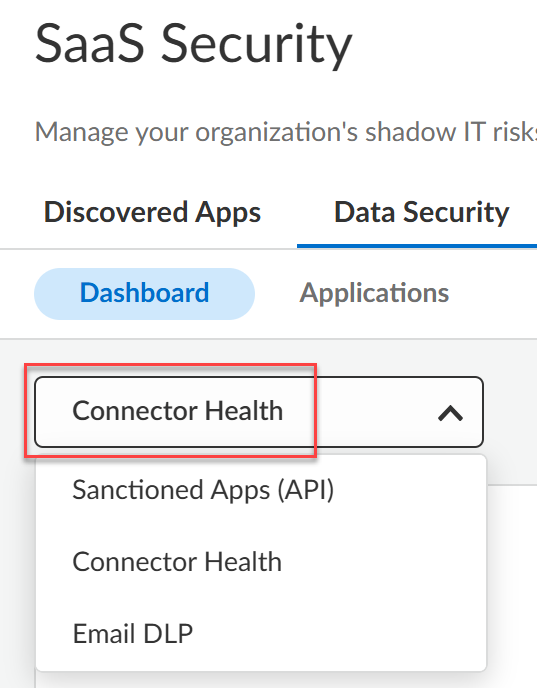
- Select Data SecurityDashboard.Choose Connector Health from the drop-down below the Dashboard tab.
![]()
Rescan a Managed Cloud App
Learn how to rescan a cloud app on Data Security to update match results.When you Configure Data Patterns, Data Security scans all connected cloud apps automatically to detect sensitive content that match on these patterns. This is the discovery process. Unlike a forward scan, a rescan does not request assets from the cloud; rather, a rescan downloads previously discovered assets from the cloud app.Rescan is a resource‑intensive and time‑consuming operation. Depending on the volume of assets in your cloud app, the rescan might take a long time to complete.Consider a rescan if:- You added or modified a data pattern. Data Security matches content from that time onwards, but does not automatically look for matches on previous scan results. To find matches for content that Data Security already scanned, you can Rescan a specific cloud app.
- You updated your internal domains list and you want Data Security to recalculate exposure for previously discovered assets.
![]()
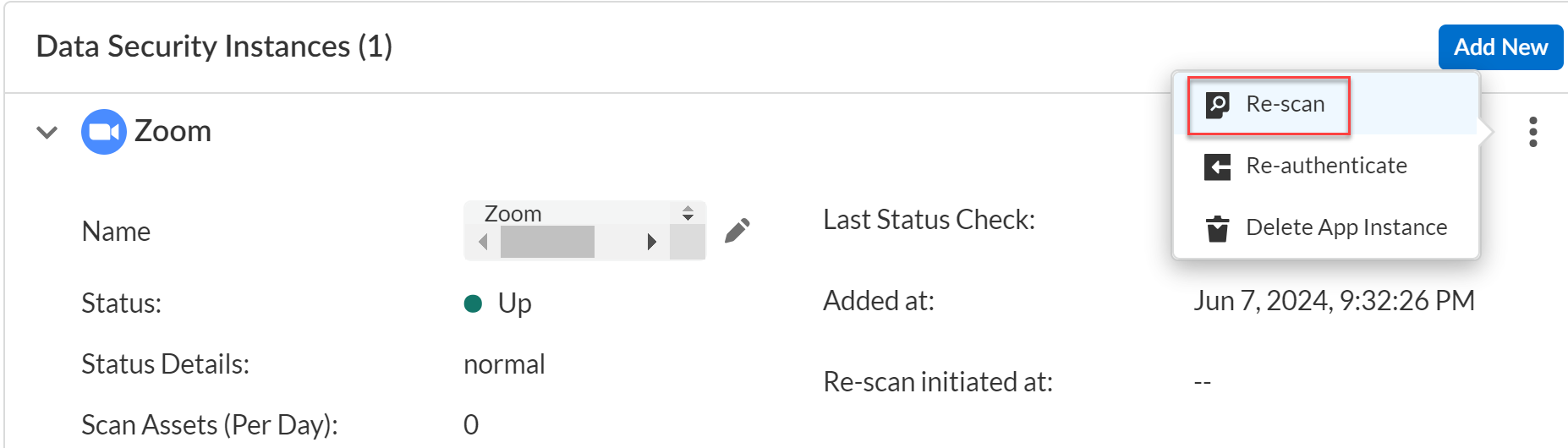
- Log in to Strata Cloud Manager.Select ConfigurationSaaS SecurityData SecurityApplications<Your Application>View SettingsActionsRescan.The Rescan option is available for the cloud app if the option is displayed, and rescans are limited to once every three days. A rescan timestamp indicates when you initiated it.
![]()
Delete Cloud Apps Managed by Data Security
Learn how to delete a cloud app from Data Security.When you delete a cloud app, Data Security purges all related cloud app data from Data Security, removes the cloud app from the Dashboard, and relinquishes permissions to access the cloud app. Deleting a cloud app does not remove the integration from the cloud app’s marketplace—you must do so manually.For specific cloud apps, the cloud app vendor automatically notifies Data Security when you delete the integration. If you do not delete the cloud app, the SaaS Security displays Marketplace integration deleted. Finish installing.. In this case, we recommend that you also delete the cloud app to complete your uninstall.Delete a cloud app if:Before you delete a managed cloud app, contact SaaS Security Technical Support to speak with an experienced Support Engineer who will help you troubleshoot your issue.- Cloud app not in use—Your organization no longer uses the cloud app or was only using the cloud app on a trial basis, and you have no need to view the analytics that Data Security compiled for the cloud app.
- Integration deleted—You already deleted the integration on the cloud app’s marketplace and have no use for the cloud app data.
- Asset display issues—Asset information isn't displaying as expected, and you intend to add the cloud app again. A scan from scratch (includes both forward and backward scans) usually resolves this behavior, but a scan can take 24 hours or more to complete, depending on the number of assets. Before you delete the cloud app, try to resolve using reauthentication or, if available for your cloud app rescan.
- Scan issues—You’re having unusual scan issues, and you don't have any assets on your tenant.
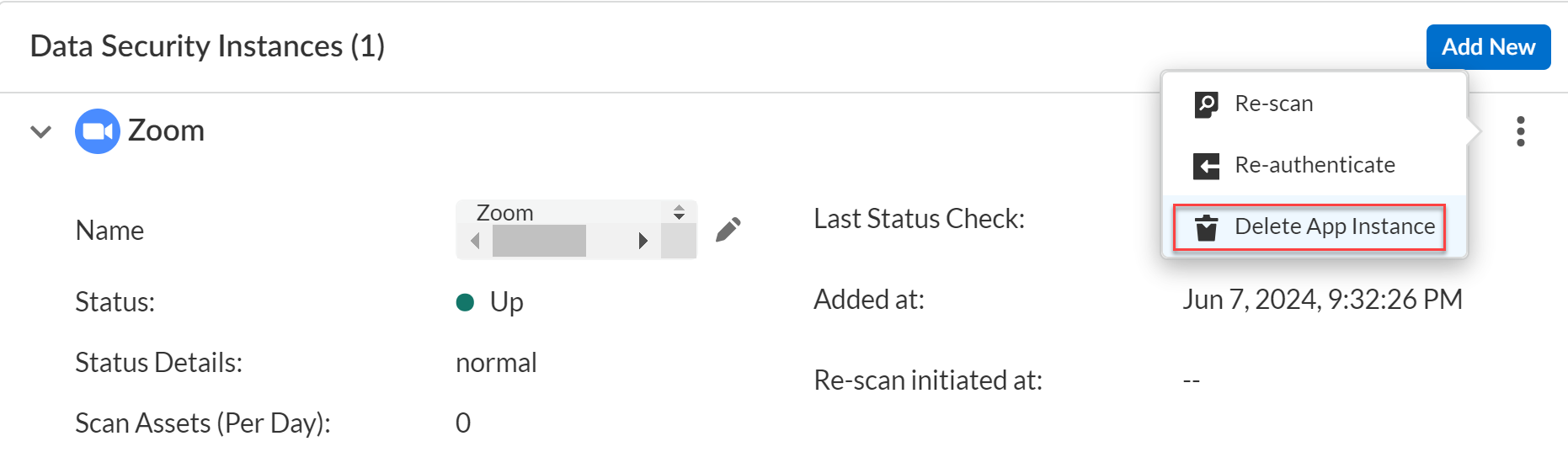
- (Recommended) Log in to your cloud app’s marketplace and delete the Data Security integration.Log in to Strata Cloud Manager.Select ConfigurationSaaS SecurityData SecurityApplications<Your Application>View SettingsVertical Ellipses (…)Delete App Instance.
![]()