SaaS Security
Onboard a MongoDB Atlas App to SSPM
Table of Contents
Expand All
|
Collapse All
SaaS Security Docs
Onboard a MongoDB Atlas App to SSPM
Connect a MongoDB Atlas App instance to SSPM to detect posture risks.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
Or any of the following licenses that include the Data Security license:
|
For SSPM to detect posture risks in your MongoDB Atlas instance, you must onboard
your MongoDB Atlas instance to SSPM. Through the onboarding process, SSPM connects
to the MongoDB Atlas Administration API by using programmatic credentials (Client ID
and Client Secret) that you provide. After connecting to the MongoDB Atlas
Administration API, SSPM scans your MongoDB Atlas organization for misconfigured
settings and account risks.
To access your MongoDB Atlas instance, SSPM requires the following information, which
you will specify during the onboarding process.
| Item | Description |
|---|---|
|
Client ID
|
SSPM will access the MongoDB Atlas Administration API through a
MongoDB service account that you create. MongoDB Atlas generates
a Client ID to uniquely identify the service account.
|
|
Client Secret
|
SSPM will access the MongoDB Atlas Administration API through a
MongoDB service account that you create. MongoDB Atlas generates
a client secret for the service account. The API verifies the
client secret against the client ID to confirm requests are
legitimate.
|
To onboard your MongoDB Atlas instance, you complete the following actions:
- Create a service account in MongoDB Atlas and save its credentials.A MongoDB Atlas service account is a non-human, programmatic identity that SSPM will use to scan your MongoDB organization. When you create a service account, MongoDB Atlas generates and displays the programmatic credentials (Client ID and Client Secret) that SSPM will use to access information about your organization.By following these steps, you onboard only one MongoDB Atlas organization to SSPM. If you want SSPM to scan for multiple organizations, you can onboard each organization separately.
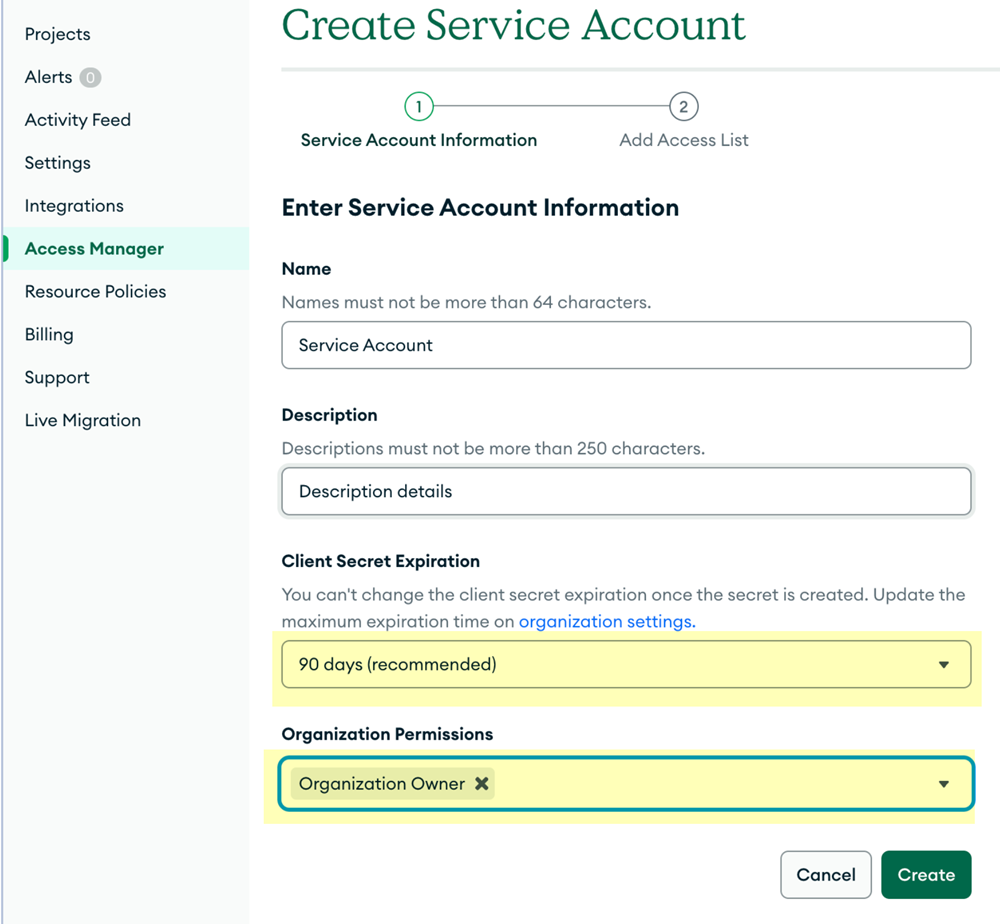
- Identify the MongoDB Atlas account that you will use to create the service account.Required Permissions: A service account is scoped to one organization. To create a service account, you must be assigned to the Organization Owner role for the organization that you want SSPM to scan.Open a web browser to the MongoDB Atlas website, and log in to the Organization Owner account.If you're a member of multiple organizations, make sure you're in the organization that you want SSPM to scan.A selection list in the top-left corner of the MongoDB Atlas page shows your current organization. If necessary, you can select a different organization from this list.Navigate to the Organization Access Manager page, To do this, from the left navigation pane, select Access Manager.On the Organization Access Manager page, select Add New Service Account.On the Create Service account page, specify the following information:
- A Name for the service account. For example, SSPM Service Account.
- A Description of the service account. For example, Service account for SSPM authentication.
- A Client Secret Expiration date. The recommended expiration period is 90 days.
- The Organization Permissions that you will grant to the service account. Select Organization Owner permissions. SSPM requires this level of access to complete its scans.
![]() Create the service account.MongoDB Atlas creates the service account and displays the programmatic credentials (Client ID and Client Secret) that SSPM will use for authentication.Copy the Client ID and Client Secret and paste them into a text file.Don’t continue to the next step unless you have copied the Client ID and Client Secret. You will provide this information to SSPM during the onboarding process.Connect SSPM to your MongoDB Atlas instance.In SSPM, complete the following steps to enable SSPM to connect to your MongoDB Atlas instance.
Create the service account.MongoDB Atlas creates the service account and displays the programmatic credentials (Client ID and Client Secret) that SSPM will use for authentication.Copy the Client ID and Client Secret and paste them into a text file.Don’t continue to the next step unless you have copied the Client ID and Client Secret. You will provide this information to SSPM during the onboarding process.Connect SSPM to your MongoDB Atlas instance.In SSPM, complete the following steps to enable SSPM to connect to your MongoDB Atlas instance.- Log in to Strata Cloud Manager.Select ConfigurationSaaS SecurityPosture SecurityApplicationsAdd Application and click the MongoDB Atlas tile.On the Posture Security tab, Add New instance.Log in with Credentials.Enter the Client ID and Client Secret and Connect.