SaaS Security
Onboard a MuleSoft App to SSPM
Table of Contents
Expand All
|
Collapse All
SaaS Security Docs
Onboard a MuleSoft App to SSPM
Connect a MuleSoft instance to SSPM to detect posture risks.
For SSPM to detect posture risks in your MuleSoft instance, you must onboard your
MuleSoft instance to SSPM. Through the onboarding process, SSPM connects to an
Anypoint Platform API and, through the API, scans your MuleSoft instance for
misconfigured settings and account risks.
SSPM gets access to your MuleSoft instance through an OAuth 2.0 application that you
create. In the Anypoint Platform, an OAuth 2.0 application is called a
Connected App. During onboarding, you supply SSPM with the
application credentials (Client ID and Client Secret) for your Connected App. SSPM
uses these credentials to access the Anypoint Platform API.
SSPM scans are supported for all MuleSoft paid plans.
To access your MuleSoft instance, SSPM requires the following information, which you
will specify during the onboarding process.
| Item | Description |
|---|---|
|
Client ID
|
SSPM will access an Anypoint Platform API through a Connected App
that you create in the Anypoint Platform. The Anypoint Platform
generates the Client ID to uniquely identify this Connected App.
|
|
Client Secret
|
SSPM will access an Anypoint Platform API through a Connected App
that you create in the Anypoint Platform. The Anypoint Platform
generates the Client Secret, which SSPM uses to authenticate to
the API through the Connected App.
|
To onboard your MuleSoft instance, you complete the following actions:
- Identify the Anypoint Platform account that you will use to create your Connected App.Required Permissions: To create the Connected App, you must use an Anypoint Platform account that is assigned to the Organization Administrator role.Create your Connected App.SSPM will use this Connected App to authenticate to an Anypoint Platform API to run scans. You will configure the Connected App to allow access to only the scopes that SSPM requires for its scans.
- Open a web browser to the MuleSoft Anypoint Platform login page and log in to the Organization Administrator account that you identified earlier.From the Anypoint Platform home screen, navigate to the Access Management page. How you navigate to the Access Management page can depend on your interface version. In some interface versions, a link to the Access Management page is on the home screen. If you do not see a link on the home screen, you can locate the Access Management link under the main navigation menu in the top-left corner of the Anypoint Platform page.From the left navigation pane of the Access Management page, select Connected Apps.On the Connected Apps page, click Create app.
![]() On the Create App page, complete the following actions:
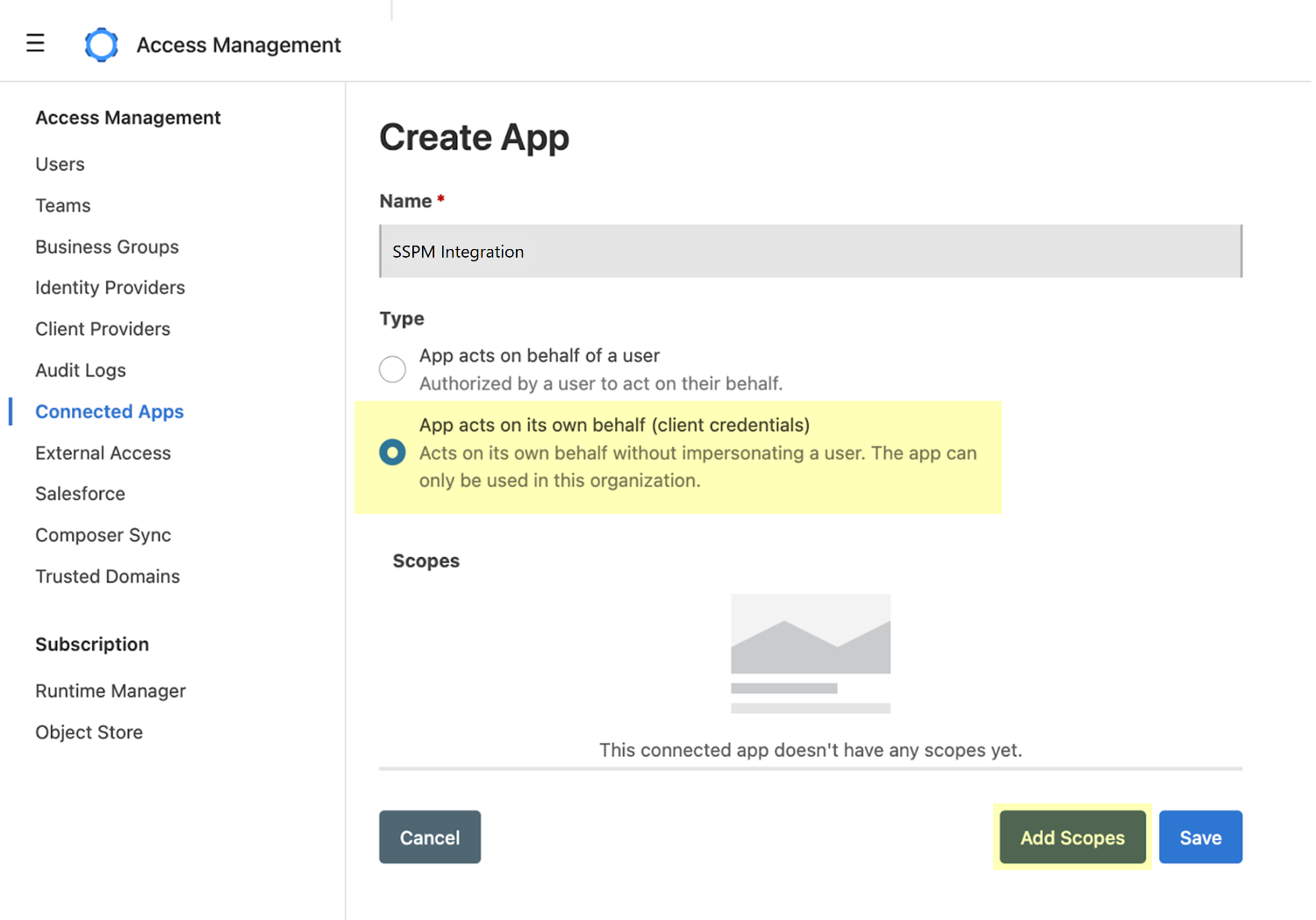
On the Create App page, complete the following actions:- Specify a Name for your Connected App. For effective logging, auditing, and future maintenance, give the Connected App a descriptive name that clearly identifies its purpose. For example, SSPM Integration.
- For the Type of application, select App acts on its own behalf (client credentials).
- Click Add Scopes, and add the following
scopes:
- View Users in a particular organization
- View Connected Applications
![]()
- Save your Connected App.
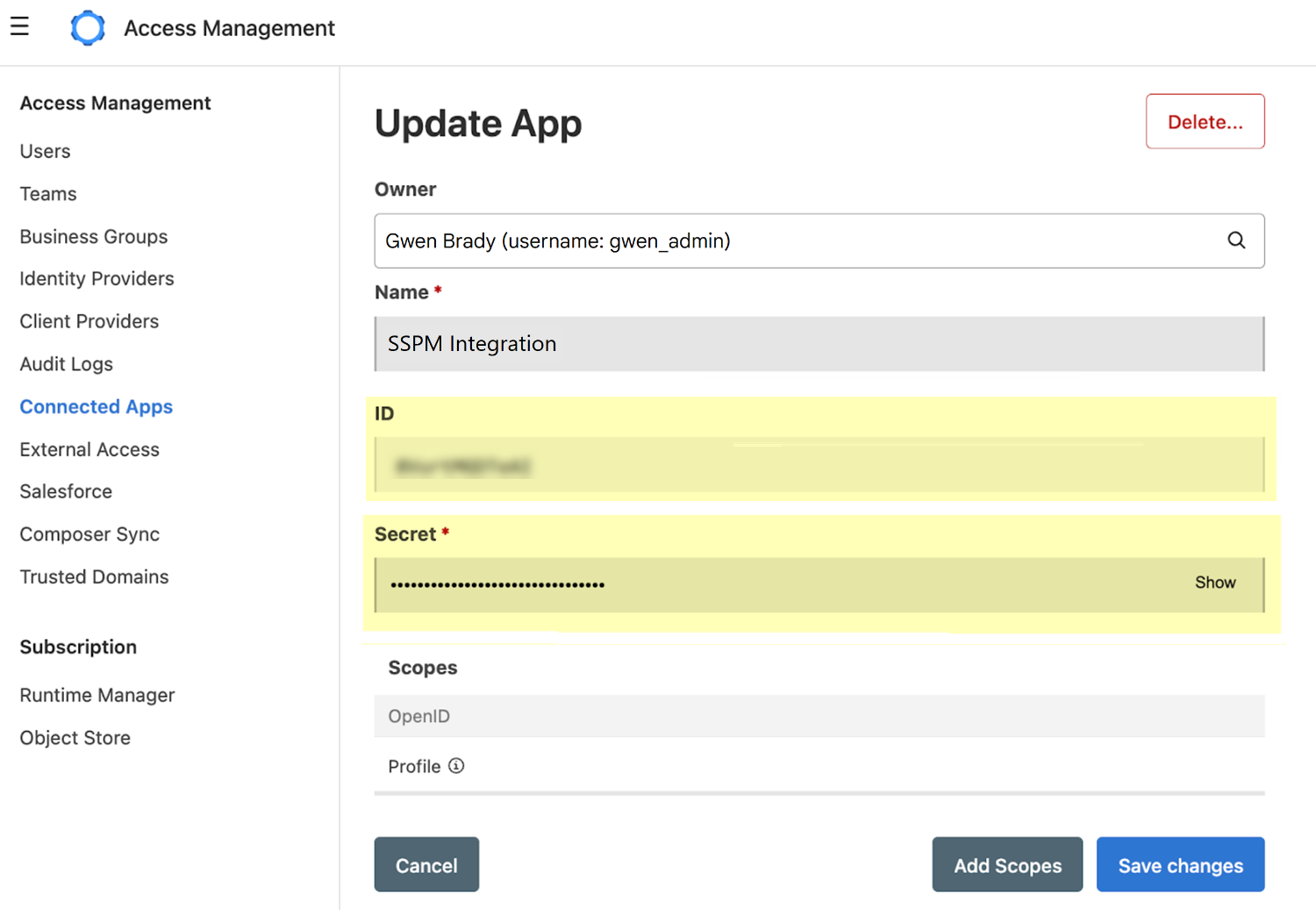
The Anypoint Platform creates the Connected App, which it displays in the list of Connected Apps on the Connected Apps page.From the list on the Connected Apps page, click the name of your Connected App.The Anypoint Platform displays the Update App page, which shows details about your Connected App. The details include the Connected App credentials (Client ID and Client Secret), which SSPM will use to authenticate to an Anypoint Platform API to run scans.![]() Copy the Client ID and Client Secret and paste them into a text file.Do not continue to the next step unless you have copied the Client ID and Client Secret. You must provide this information to SSPM during the onboarding process.Connect SSPM to your MuleSoft instance.In SSPM, complete the following steps to enable SSPM to connect to your MuleSoft instance.
Copy the Client ID and Client Secret and paste them into a text file.Do not continue to the next step unless you have copied the Client ID and Client Secret. You must provide this information to SSPM during the onboarding process.Connect SSPM to your MuleSoft instance.In SSPM, complete the following steps to enable SSPM to connect to your MuleSoft instance.- Log in to Strata Cloud Manager.Select ConfigurationSaaS SecurityPosture SecurityApplicationsAdd Application and click the MuleSoft tile.On the Posture Security tab, Add New instance.Log in with Credentials.Enter the Client ID and Client Secret for your Connected App.Connect.