SaaS Security
Onboard a Salesforce App to SSPM
Table of Contents
Expand All
|
Collapse All
SaaS Security Docs
Onboard a Salesforce App to SSPM
Connect a Salesforce instance to SSPM to detect posture risks.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
Or any of the following licenses that include the Data Security license:
|
For SSPM to detect posture risks in your Salesforce instance, you must onboard your
Salesforce instance to SSPM. Through the onboarding process, SSPM connects to a
Salesforce API and, through the API, scans your Salesforce instance for
misconfigured settings and account risks.
You can onboard your Salesforce instance through an interactive OAuth 2.0
authorization flow or through a Salesforce Connected App.
The interactive OAuth 2.0 Authorization flow relies on a
Salesforce user account to authorize access through a browser-based login. You first
create a permission set in Salesforce with the required access levels and assign
this permission set to the designated Salesforce user. During onboarding, SSPM
redirects you to Salesforce to log in as that user and manually approve the access
that SSPM requires for its scans. This approach can be faster to set up, because it
uses existing Salesforce credentials. It also leverages any single sign-on (SSO) or
multi-factor authentication (MFA) requirements already established by your
organization.
The Connected App approach authenticates by using application
credentials (Client ID and Client Secret). Instead of a manual login redirect, you
create a Connected App within Salesforce and configure its settings to define
security policies and a "Run As" user. During onbaording, you provide SSPM with the
application credentials, which SSPM uses to authenticate to Salesforce. This method
offers long-term stability by creating a persistent, system-to-system link. Unlike
the interactive OAuth 2.0 authorization flow, this method does not rely on the
continuous validity of OAuth refresh tokens, which can expire or be revoked.
Onboard a Salesforce App to SSPM Using OAuth 2.0
Connect a Salesforce instance to SSPM to detect posture risks.
For SSPM to detect posture risks in your Salesforce instance, you must onboard your
Salesforce instance to SSPM. Through the onboarding process, SSPM connects to a
Salesforce API and, through the API, scans your Salesforce instance for
misconfigured settings. If there are misconfigured settings, SSPM suggests a
remediation action based on best practices.
SSPM can get access to your Salesforce instance through OAuth 2.0 authorization.
During the onboarding process, you are prompted to log in to Salesforce and to grant
SSPM the access it requires.
To onboard your Salesforce instance, you complete the following actions:
Identify the Account for Granting SSPM Access
- Identify the Salesforce account that you will use to log in to Salesforce during onboarding.SSPM will use this account to establish a connection to your Salesforce instance. After SSPM establishes the connection, it will perform an initial scan of your Salesforce instance, and will then run scans at regular intervals. Depending on the access scopes that the account can grant to SSPM, SSPM can run configuration scans of your Salesforce settings, risky account scans, identity scans, and scans of third-party plugins that are connected to your Salesforce instance. For SSPM to run these scans, the Salesforce account that you use to establish the initial connection must remain available. For this reason, we recommend that you use a dedicated service account to grant SSPM access. If you delete the service account, or change the account's password, the scans will fail and you will need to onboard Salesforce again.The account that you use to connect to your Salesforce instance can have the full permissions that SSPM requires to complete all its scans and perform automated remediation. You can also use an account that has reduced permissions, in which case some SSPM function will not be available. For example, you might want to use an account with reduced permissions if your organization places limits on service-account permissions. During onboarding, SSPM gives you an option to connect with read-only permissions or with read and write permissions. The onboarding screen also lists the API scopes that SSPM requires for each scan type. After establishing a connection, SSPM will notify you if it is unable to run certain scans because the account did not have the required permissions to grant access to certain scopes.Permissions for Read Access: To grant SSPM reduced permissions to perform configuration scans, identity scans, and risky account scans, the account that you use to connect SSPM to your Salesforce instance requires the following permissions. With only these reduced permissions, SSPM will not be able to perform third-party plugin scans or automated remediation.
Scan Type Required Permission Configuration- API Enabled
- View Health Check
Risky Accounts- API Enabled
In addition to API Enabled permission, you must also disable login with Salesforce credentials for the account. You can do this by selecting the Disable login with Salesforce credentials checkbox on the Single Sign-on Settings page. More information on this setting is available in the following step.Identity- API Enabled
- View Event Log Files
- View Setup and Configuration
- View All Users
The Identity permissions described in the preceding table typically give SSPM access to the Salesforce objects and fields that SSPM needs to complete its identity scans. During onboarding, SSPM will verify that it can access these objects and fields. If it cannot access these fields, onboarding will fail with the following message.Your Salesforce org may be missing required fields or permissions for our Identity security moitoring queries.If onboarding fails with this message, verify that the account can access the required objects and fields. See Required Objects and Fields for Identity Scans for more information.Additional Permissions for Write Access: To grant SSPM full read and write access, the account that you use to connect SSPM to your Salesforce instance requires the permissions for read access described above, and also the following additional permissions. These additional permissions are required for third-party plugin scans, and for automated remediation of misconfigured settings.Scan Type / Remediation Required Permission Configuration Remediation - API Enabled
- View Health Check
- Download AppExchange Packages
Third-Party Plugins - API Enabled
- Download AppExchange Packages
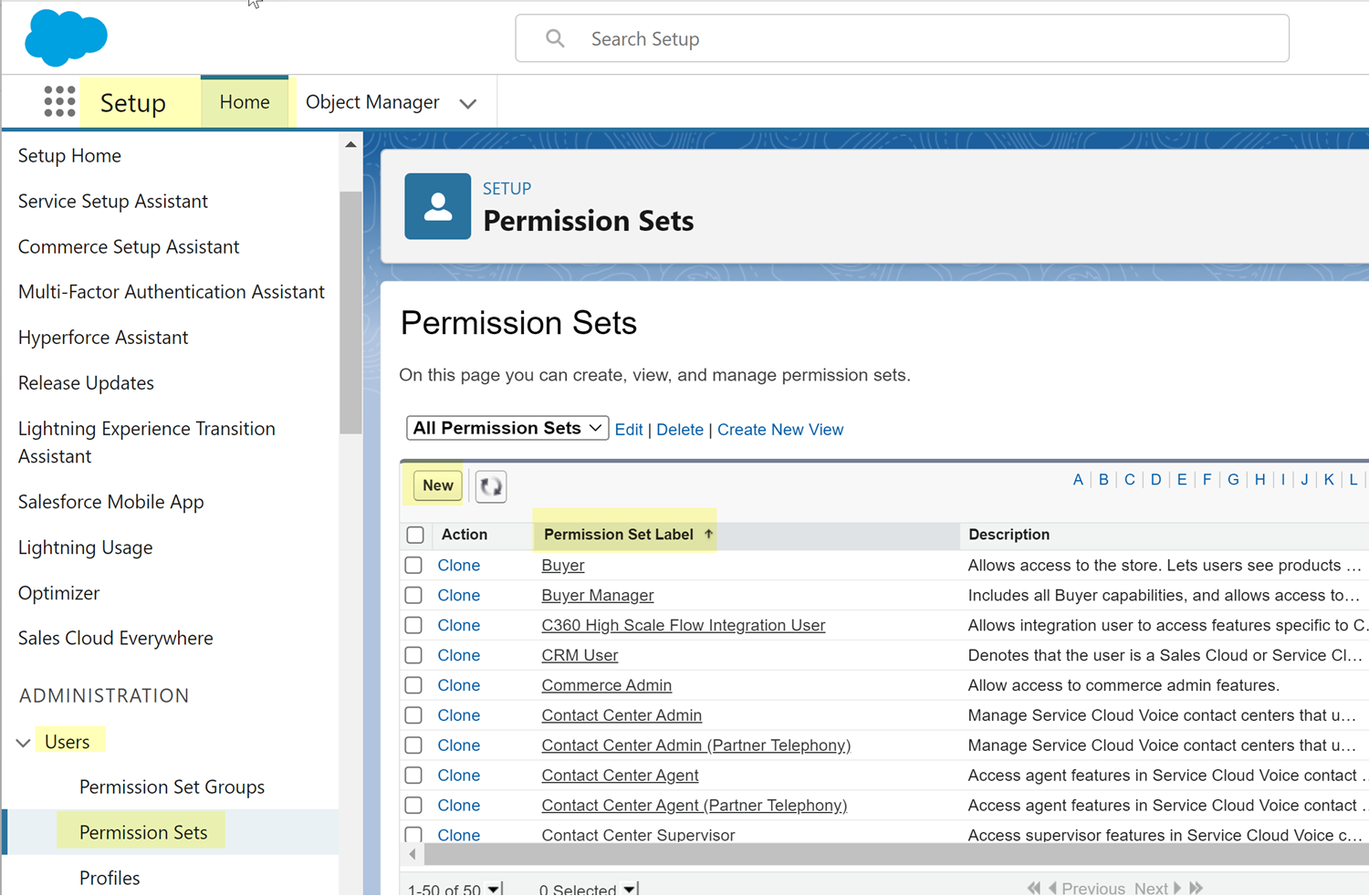
To grant the permissions to the user account, you can add the permissions to a permission set, and then assign the permission set to a Salesforce user account.- Add the required permissions to a permission set.
- From the setup home page in Salesforce, select UsersPermission Sets.
- You can create a new permission set or edit an existing
permission set to add the permissions.To create a permission set, click New, fill in the basic information, and Save.To edit an existing permission set, click its name in the Permission Set Label column.
![]()
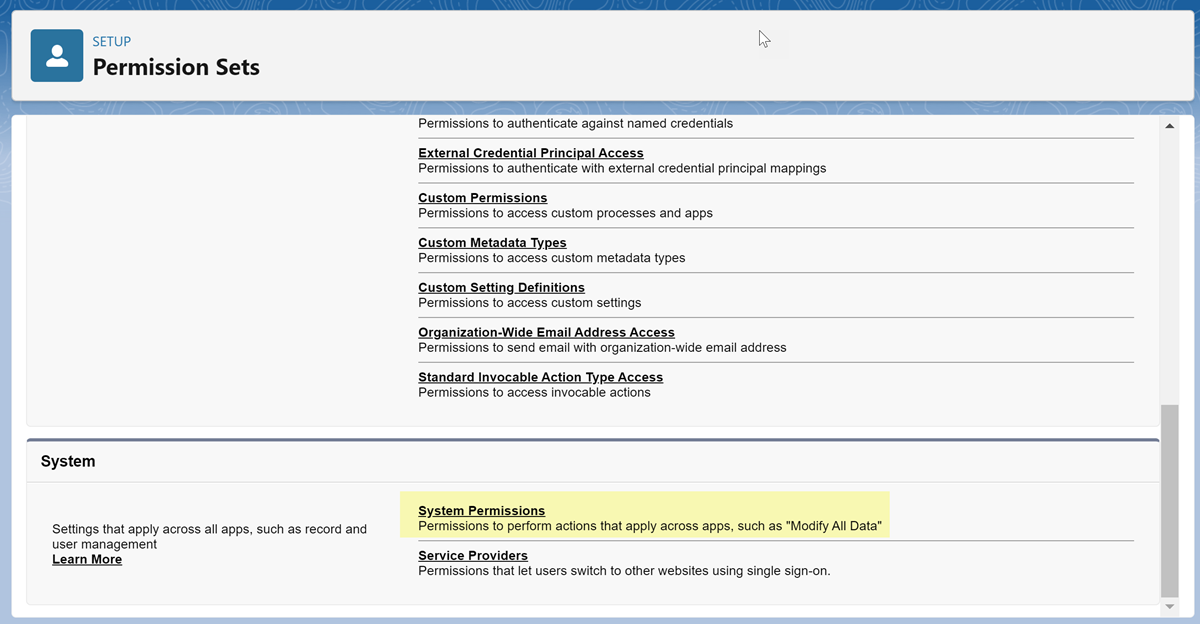
- On the setup page for the permission set, locate the System
area and navigate to System
Permissions.
![]()
- On the System Permissions page for the permission set, Edit the permissions.
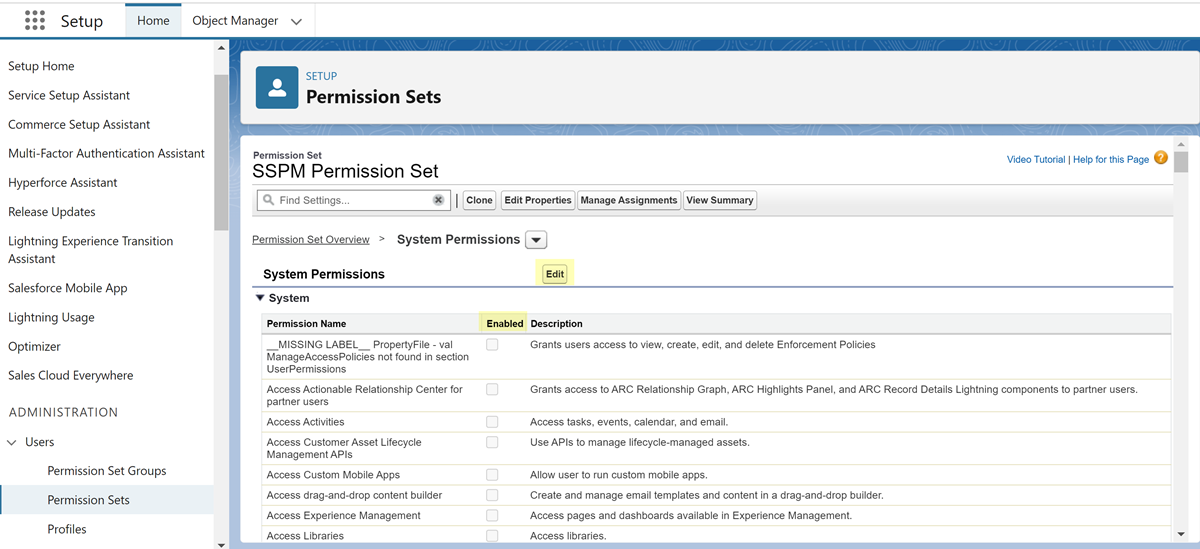
- In the list of system permissions, select the
Enabled check box for each of the
required permissions. When you enable a permission that requires other permissions, Salesforce will automatically enable the other required permissions.
![]()
- Save your changes.
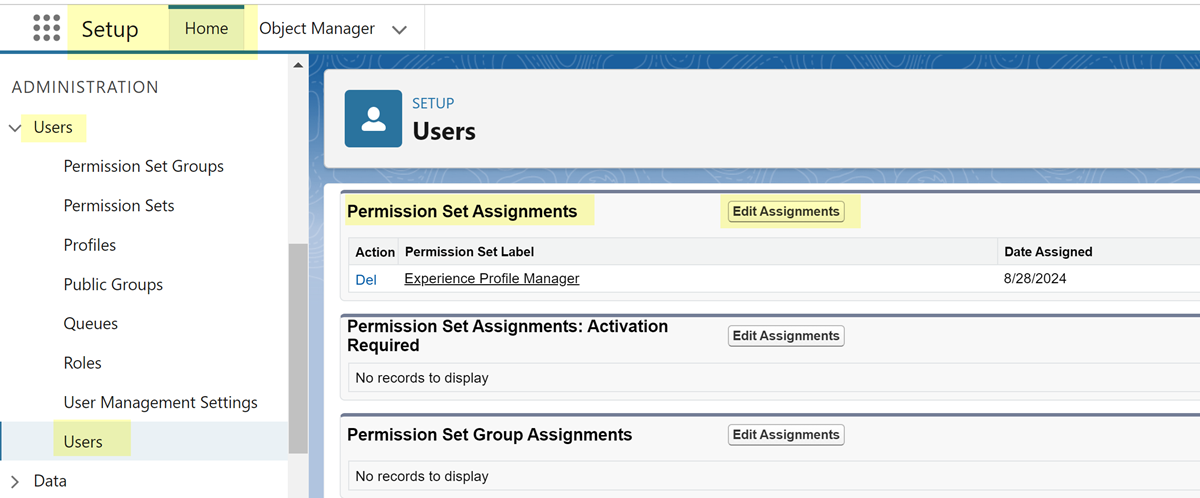
Assign the permission set to a Salesforce user account.- From the setup home page in Salesforce, select UsersUsers.
- From the list of users, click the name of the user.
- On the setup page for the user, locate the Permission Set
Assignments area to Edit
Assignments.
![]()
- On the Permission Set Assignments page, locate the permission set in the Available Permission Sets list, Add it to the Enabled Permission Sets list for the user, and Save your changes.
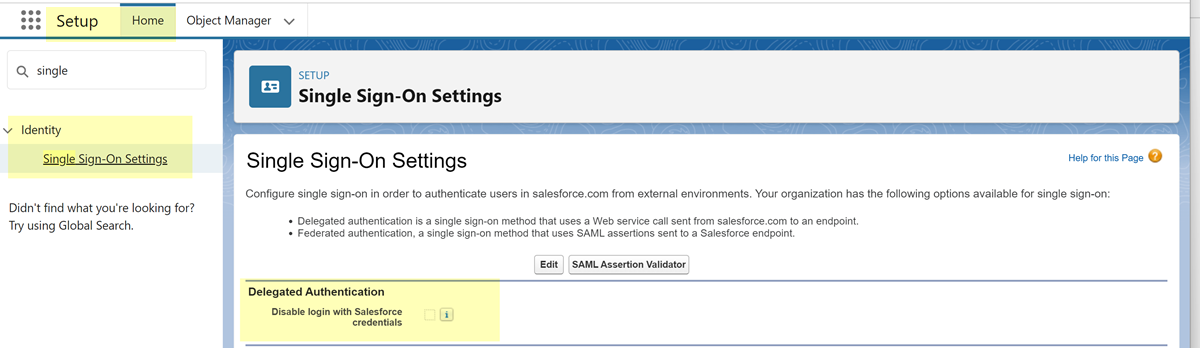
Verify that your account configuration supports SSPM risky account scans.SSPM supports risky account detection for Salesforce. For the risky account scan to work correctly, SSPM requires that you enable a particular setting on the Single Sign-on Settings page. This step is required only for the risky account scan; the configuration scans and third-party plugin scans will be unaffected.- From the setup home page in Salesforce, navigate to the Single Sign-on Settings page. To navigate to this page, select IdentitySingle Sign-on Settings.On the Single Sign-on Settings page, locate the Delegated Authentication area, and make sure that the Disable login with Salesforce credentials checkbox is selected.If the Disable login with Salesforce credentials checkbox is not already selected, make sure that you understand the implications of selecting this checkbox. Modifying any setting on your Salesforce Single Sign-on Settings page might affect your users.
![]() Make note of your organization's Salesforce instance URL. The instance URL has the format https://<instance_name>.my.salesforce.com.Log out of all Salesforce accounts.Logging out of all Salesforce accounts helps ensure that you log in under the correct account during the onboarding process. Some browsers can automatically log you in by using saved credentials. To ensure that the browser does not automatically log you in to the wrong account, you can turn off any automatic log-in option or clear your saved credentials. Alternatively, you can prevent the browser from using saved credentials by opening the Cloud Management Console in an incognito window.
Make note of your organization's Salesforce instance URL. The instance URL has the format https://<instance_name>.my.salesforce.com.Log out of all Salesforce accounts.Logging out of all Salesforce accounts helps ensure that you log in under the correct account during the onboarding process. Some browsers can automatically log you in by using saved credentials. To ensure that the browser does not automatically log you in to the wrong account, you can turn off any automatic log-in option or clear your saved credentials. Alternatively, you can prevent the browser from using saved credentials by opening the Cloud Management Console in an incognito window.Connect SSPM to Your Salesforce Instance
By adding a Salesforce app in SSPM, you enable SSPM to connect to your Salesforce instance. You must consent to specific permissions when adding the Salesforce app. In September 2025, Salesforce updated its security policy for connected OAuth apps. This update impacted our Salesforce connector, causing onboarding and re-authencation to fail. To onboard or re-authenticate to Salesforce, you might need to complete additional configuration steps to meet new Salesforce requirements. Before onboarding, review the information in Install the SSPM OAuth App in Salesforce.- Log in to Strata Cloud Manager.Select ConfigurationSaaS SecurityPosture SecurityApplicationsAdd Application and click the Salesforce tile.On the Posture Security tab, Add New instance.Specify your instance URL in the field provided. You can also specify the generic login URL (login.salesforce.com).Specify whether you want SSPM to connect with Read Permissions only or with Read and Write permissions.The onboarding page lists the API scopes that SSPM will access to complete its various scans and to perform remediation.Connect with Salesforce.SSPM redirects you to the Salesforce login page.Log in to the Salesforce account.Salesforce displays a consent form that details the access permissions that SSPM requires.Review the consent form and allow the requested permissions.SSPM connects to your Salesforce instance, and displays whether it was able to access the API scopes that it requires for its scans. If SSPM is unable to access necessary scopes, it indicates which scan types it will not be able to perform.
Install the SSPM OAuth App in Salesforce
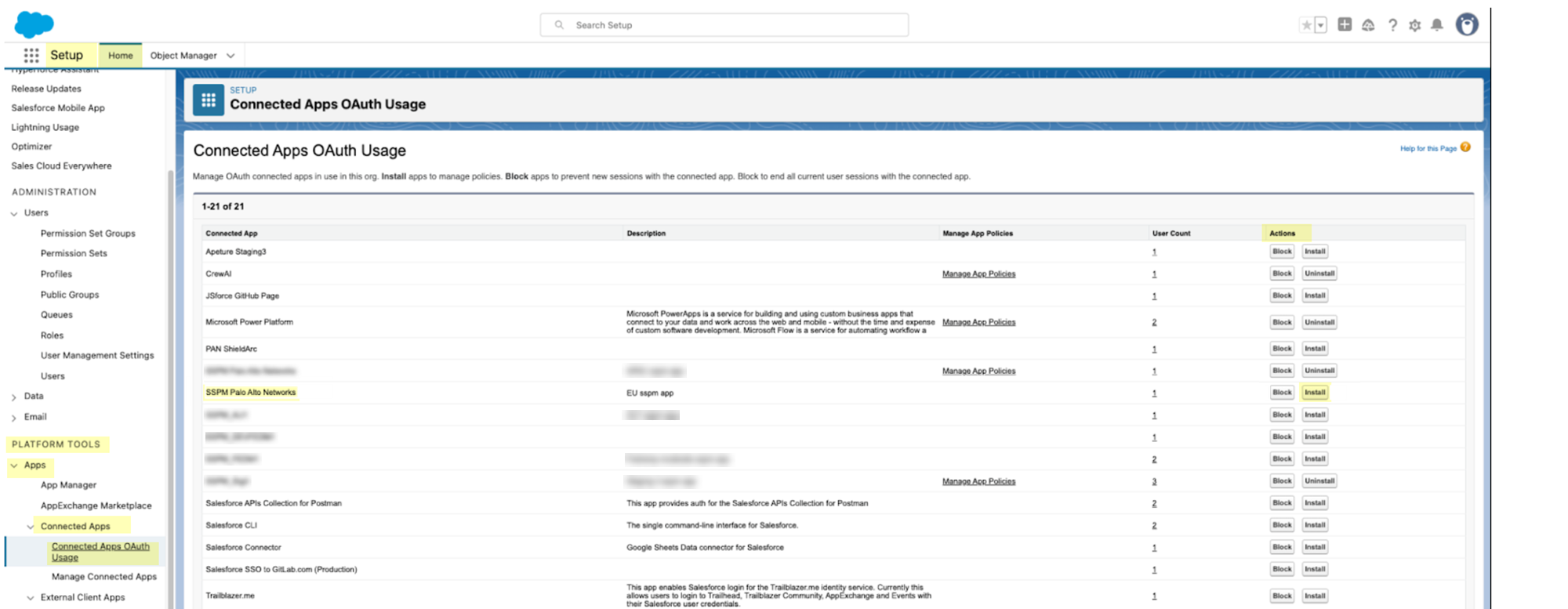
In September 2025, Salesforce updated its security policy for connected OAuth apps. This update impacted our Salesforce connector, causing onboarding and re-authencation to fail. To onboard or re-authenticate to Salesforce, you need to complete these additional configuration steps to install the SSPM OAuth app in Salesforce. You will need to complete these steps for your Salesforce instance only once.Salesforce now restricts the use of uninstalled connected OAuth apps. These are apps that a user has authorized during the OAuth flow, and which weren’t formally installed by a Salesforce administrator. Salesforce now requires the connected OAuth apps to be installed. Our connector uses the OAuth 2.0 flow, which creates an uninstalled OAuth app in Salesforce. Because this approach violates Salesforce's new requirements, onboarding and re-authentication are failing. To fix this problem, you will navigate to the Connected Apps OAuth Usage page in Salesforce, locate SSPM's uninstalled OAuth app, and install the app.- If you have never onboarded Salesforce to SSPM, Salesforce will never have created an uninstalled connected OAuth app for SSPM. In that case, you must first connect your Salesforce instance to SSPM to have Salesforce create an uninstalled connected app.If you previously connected SSPM to your Salesforce instance (prior to the new restriction introduced in September 2025), you don’t need to complete this step. Salesforce will have already created the uninstalled connected OAuth app.As a Salesforce System Administrator, or as a user with Salesforce's new Approve Uninstalled Connected Apps user permission, complete the onboarding steps described in Connect SSPM to Your Salesforce Instance.Required Permissions: The account you use to onboard must have the Approve Uninstalled Connected Apps permission, which Salesforce automatically includes in the System Administrator user profile.Install the uninstalled connected OAuth app.
- Log in to Salesforce as a System Administrator.From the setup home page in Salesforce, select AppsConnected Apps Connected Apps OAuth Usage. These items appear under the PLATFORM TOOLS section of the menu.On the Connected Apps OAuth Usage page, locate the entry for SSPM's connected OAuth app.The name of SSPM's connected OAuth app differs by region, but begins with SSPM.From the Activities column of the table, Install SSPM's connected OAuth app.
![]() If you had never onboarded Salesforce to SSPM, and completed step 1 of these instructions, you will now want to reduce the permissions of the account you used for onboarding.If you had previously connected SSPM to your Salesforce instance, you needed only to complete step 2. You don’t need to complete this step.In Step 1 of these instructions, you onboarded Salesforce to SSPM by using a System Administrator account or another account with Approve Uninstalled Connected Apps permission. SSPM no longer needs these extra permissions. These added permissions were required only for the initial onboarding for Salesforce to create the connected OAuth app. Now that the initial onboarding is complete, reduce to account's permissions to only the permissions the SSPM requires. These permissions are listed earlier in this topic.
If you had never onboarded Salesforce to SSPM, and completed step 1 of these instructions, you will now want to reduce the permissions of the account you used for onboarding.If you had previously connected SSPM to your Salesforce instance, you needed only to complete step 2. You don’t need to complete this step.In Step 1 of these instructions, you onboarded Salesforce to SSPM by using a System Administrator account or another account with Approve Uninstalled Connected Apps permission. SSPM no longer needs these extra permissions. These added permissions were required only for the initial onboarding for Salesforce to create the connected OAuth app. Now that the initial onboarding is complete, reduce to account's permissions to only the permissions the SSPM requires. These permissions are listed earlier in this topic.- If you granted the Approve Uninstalled Connected Apps permission to a user account, remove that permission.
- If you used a System Administrator account to onboard, change the account profile to a profile other than the System Administrator profile. If you need to keep that account as a System Administrator account, remove the Salesforce app from SSPM and re-onboard using an account with reduced permissions.
Required Objects and Fields for Identity Scans
To complete identity scans, SSPM requires access to certain Salesforce objects and their fields. During onboarding, SSPM will verify that it can access these objects and fields. If it cannot access these fields, onboarding will fail with the following message. Your Salesforce org may be missing required fields or permissions for our Identity security monitoring queries.If you get this message, check the following possible causes:- Verify that you account has the permissions that SSPM requires to run
identity scans. The following permissions are required:
- API Enabled
- View Event Log Files
- View Setup and Configuration
- View All Users
- Verify that the account can access the following objects and fields. Confirm that your user profile and permission sets are not blocking access to the required Salesforce objects and fields
Salesforce Object Required Fields EventLogFile Id, EventType, LogFile, Interval, LogDate ConnectedApplication Id, Name, CreatedDate, CreatedById, LastModifiedDate, LastModifiedById SetupAuditTrail Id, Action, Section, CreatedDate, CreatedById, Display, CreatedByIssuer User Id, Name, Email, LastLoginDate, CreatedDate, LastPasswordChangeDate PermissionSetAssignment PermissionSet. PermissionsModifyAllData, AssigneeId Onboard a Salesforce App to SSPM Using a Connected App
Connect a Salesforce instance to SSPM to detect posture risks.For SSPM to detect posture risks in your Salesforce instance, you must onboard your Salesforce instance to SSPM. Through the onboarding process, SSPM can connect to the Salesforce API through a Connected App that you create. By leveraging the OAuth 2.0 protocol, the Connected App provides the secure framework for SSPM to access your Salesforce configuration. Once authenticated, SSPM uses the API to scan your Salesforce environment for misconfigured settings and account risks.The supported Salesforce editions for SSPM scans are the following editions:- Enterprise Edition
- Unlimited Edition
- Developer Edition
- Professional Edition with the API Add-on
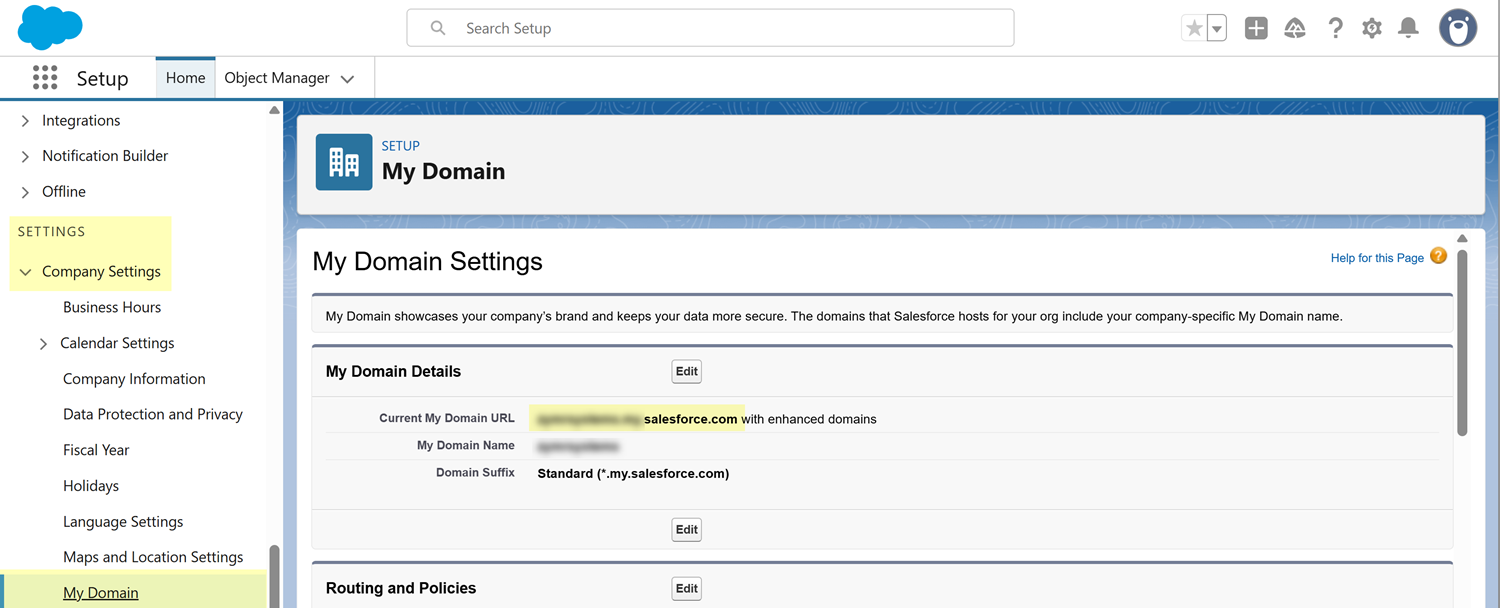
To access your Salesforce instance, SSPM requires the following information, which you will specify during the onboarding process.Item Description Instance URL The unique web address for your Salesforce instance. SSPM uses this address to locate and communicate with your specific environment. The instance URL has the format https://<instance_name>.my.salesforce.com. Client ID SSPM will access a Salesforce API through a Salesforce Connected App that you create. Salesforce generates the Client ID to uniquely identify the Connected App. The Client ID acts as a username for SSPM to identify itself during the connection process.The Salesforce interface calls this ID the Consumer Key.Client Secret SSPM will access a Salesforce API through a Salesforce Connected App that you create. Salesforce generates the Client Secret, which acts as a password that SSPM uses to securely authenticate and establish the OAuth connection.The Salesforce interface calls this secret the Consumer Secret.To onboard your Salesforce instance, you complete the following actions:The following steps assume that you are using the Salesforce Lightning Experience UI, which is now the default UI for most Salesforce accounts. If you are using the Salesforce Classic UI, you can click the Switch to Lightening Experience in your page header to follow these instructions.- Make note of your organization's Salesforce instance (domain) URL.Your instance URL, which is typically used as your login URL, has the format https://<instance_name>.my.salesforce.com. You will provide this entire URL, including the https:// prefix, to SSPM during the onboarding process.If necessary, you can locate your instance URL from the My Domain Settings page.
- Click the settings icon (gear icon) in the upper-right corner of the page, and select Setup.From the Setup page's left navigation pane, select Company SettingsMy Domain. These items appear under the SETTINGS section of the menu.On the My Domain Settings page, the Current My Domain URL field contains your instance URL. Remember to add the https:// prefix when you provide this URL to SSPM.
![]() Create a Connected App in Salesforce.Creating a Connected App establishes a secure identity for SSPM within your Salesforce environment. This identity enables Salesforce to recognize SSPM and authorize its API requests.
Create a Connected App in Salesforce.Creating a Connected App establishes a secure identity for SSPM within your Salesforce environment. This identity enables Salesforce to recognize SSPM and authorize its API requests.- Identify the Salesforce user account that you will use to create your Connected App.Required Permissions: To create a Connected App, the account must be assigned to the System Administrator Profile, or have a permission set that includes the following permissions:
- Customize Application
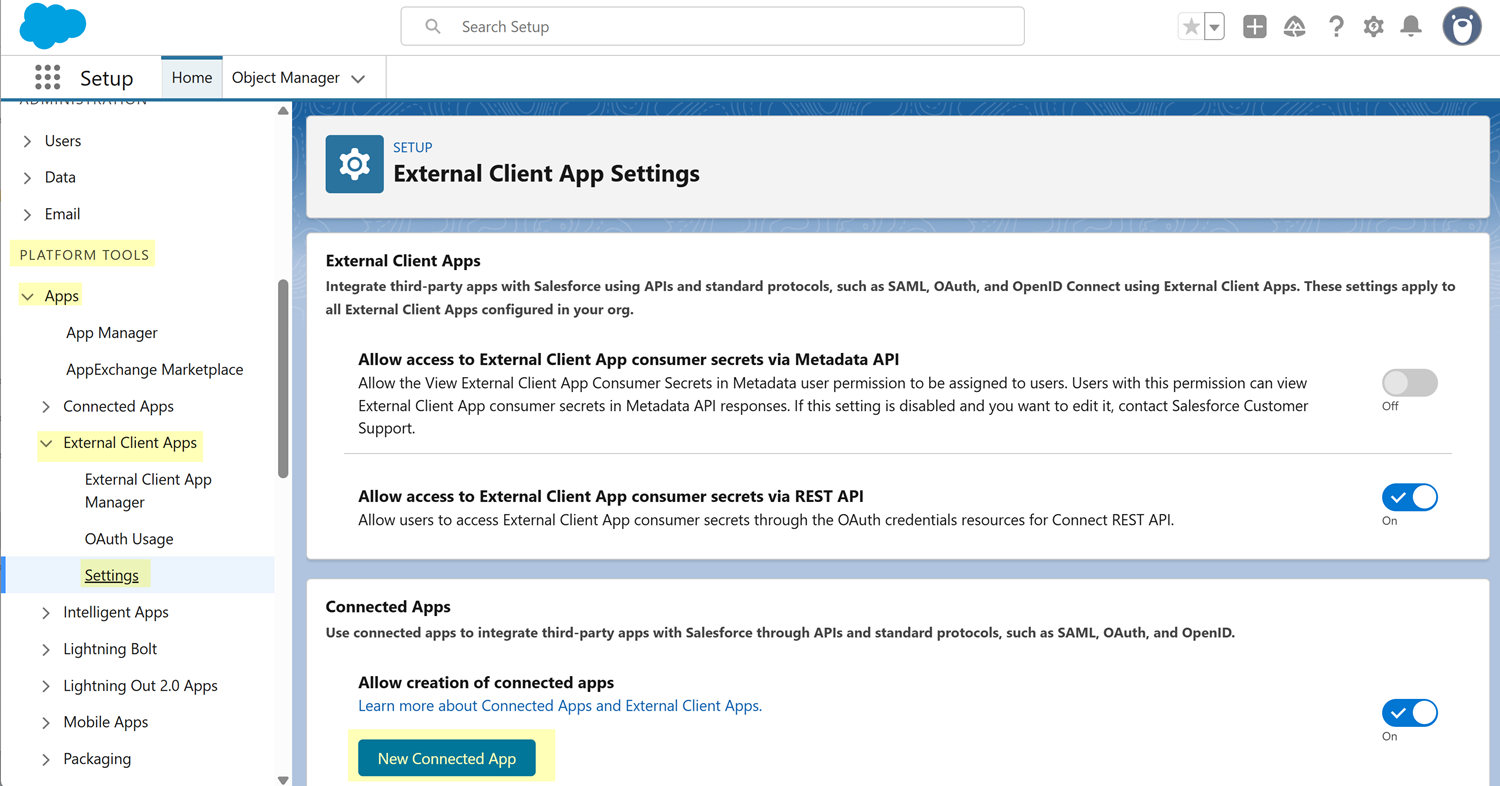
- Manage Connected Apps or Modify All Data
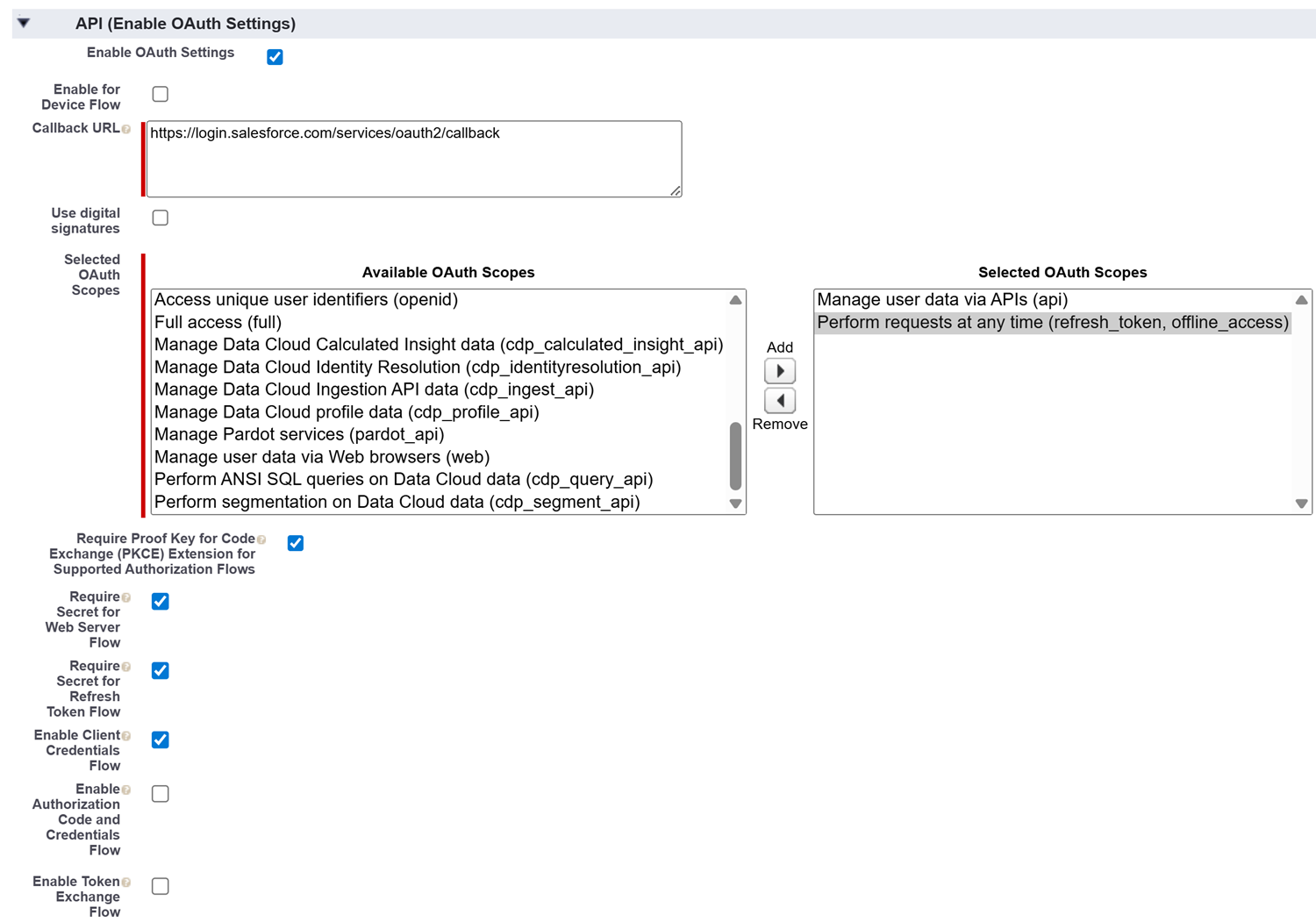
Log in to the Salesforce account that you identified.Navigate to your Setup page. To do this, click the settings icon (gear icon) in the upper-right corner of the page, and select Setup.Navigate to the External Client App Settings page. To navigate to this page, from the Setup page's left navigation pane, select Apps External Client AppsSettings. These items appear under the PLATFORM TOOLS section of the menu.On the External Client App Settings page, click New Connected App.![]() Fill in the fields on the New Connected App page.
Fill in the fields on the New Connected App page.- Under Basic Information, take the
following actions:
- In the Connected App Name field, specify a meaningful name, such as SSPM Connector. Salesforce will also automatically format this name for system use (such as replacing spaces with underscores) in the API Name field. Using a clear, descriptive name ensures that SSPM activity is easily identifiable in your Salesforce audit logs and describes the Connected App's purpose to other administrators.
- In the Contact Email field, enter a valid email address that Salesforce can use to contact you or your support team regarding this integration. We recommend using a shared administrative or security team email alias to ensure that these alerts are seen even if a specific individual leaves the organization.
- Under API (Enable OAuth Settings), take
the following actions:
- Select the Enable OAuth Settings
checkbox. Selecting the Enable OAuth Settings checkbox expands the API (Enable OAuth Settings) section to show additional fields.
- In the Callback URL field, specify the following
callback URL:
https://login.salesforce.com/services/oauth2/callbackThis URL acts as a secure "return address" that allows Salesforce to safely complete the authentication process with SSPM. Ensure you enter the URL exactly as shown, as this field is case-sensitive.
- In the Available OAuth Scopes list, select the following scopes and click the Add arrow to move them to the Selected OAuth Scopes list:
- Manage user data via APIs (api)
- Perform requests at any time (refresh_token, offline_access)
- Select the following checkboxes:
- Require Proof Key for Code Exchange (PKCE) Extension for Supported Authorization Flows
- Require Secret for Web Server Flow
- Require Secret for Refresh Token Flow
- Enable Client Credentials Flow
- Select the Enable OAuth Settings
checkbox.
![]() Save your Connected App.Salesforce saves the Connected App.Salesforce requires a brief period (typically up to 10 minutes) to propagate your new Connected App settings across its global network. You do not need to wait before completing the remaining steps. You can Continue with the next steps.You won't receive a confirmation message when this propagation is complete. If you receive an authentication error when you first attempt to connect SSPM to Salesforce, wait a few minutes and try again. This pause will allow the Salesforce Identity service to fully update.Configure access policies for your Connected App.Now that you have created the Connected App, you must define its security policies. These settings enable the authorization flow for your SSPM users, and specify which user account will provide the underlying permissions for SSPM’s activity.
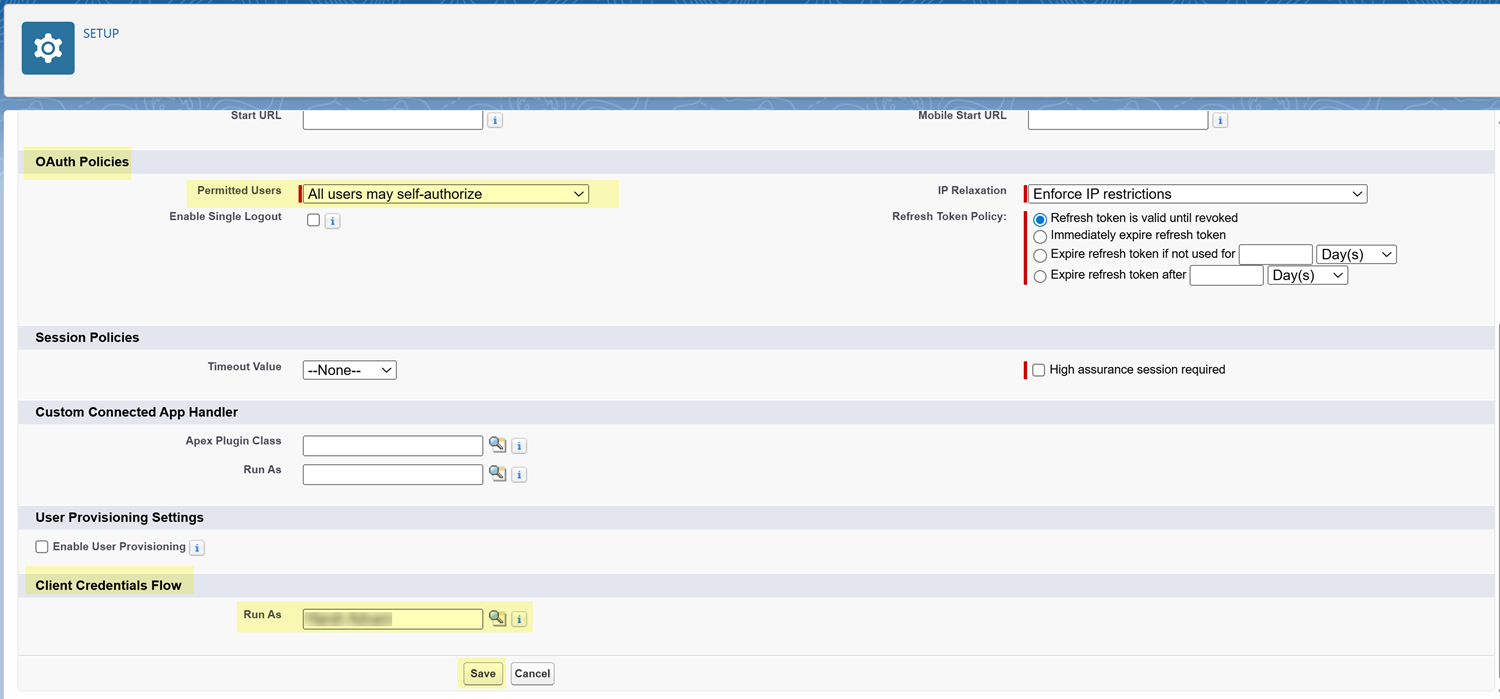
Save your Connected App.Salesforce saves the Connected App.Salesforce requires a brief period (typically up to 10 minutes) to propagate your new Connected App settings across its global network. You do not need to wait before completing the remaining steps. You can Continue with the next steps.You won't receive a confirmation message when this propagation is complete. If you receive an authentication error when you first attempt to connect SSPM to Salesforce, wait a few minutes and try again. This pause will allow the Salesforce Identity service to fully update.Configure access policies for your Connected App.Now that you have created the Connected App, you must define its security policies. These settings enable the authorization flow for your SSPM users, and specify which user account will provide the underlying permissions for SSPM’s activity.- On the Connected App Detail page, click Edit.If you navigated away from the Connected App Detail page, complete the following steps to open the Connected App Detail page:
- From the Setup page's left navigation, select Apps Connected AppsManage Connected Apps. These items appear under the PLATFORM TOOLS section of the menu.
- Locate your Connected App on this page, and click Edit.
On the Connected App Detail page, click Manage.Edit Policies.Under OAuth Policies, set the Permitted Users to All users may self-authorize.Under Client Credentials Flow, specify the Run As user. The Run As user must be a user assigned to the System Administrator Profile.Save your changes.![]() Copy the credentials (Client ID and Client Secret) for your Connected App.SSPM will use these credentials to establish a secure connection to your Salesforce instance.
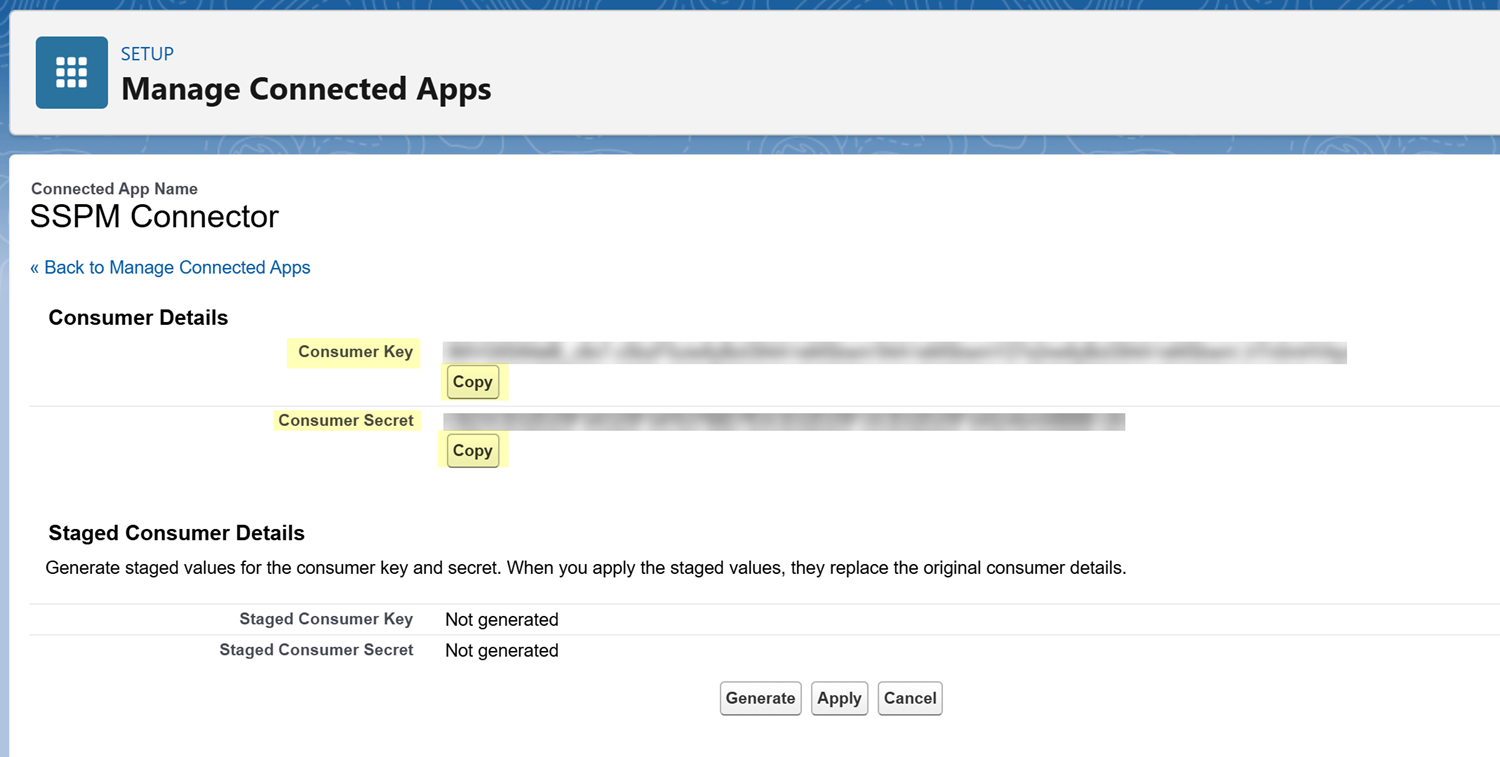
Copy the credentials (Client ID and Client Secret) for your Connected App.SSPM will use these credentials to establish a secure connection to your Salesforce instance.- Navigate to the App Manager page.From the Setup page's left navigation pane, select Apps App Manager. These items appear under the PLATFORM TOOLS section of the menu.On the Connected App Detail page, locate the API (Enable OAuth Settings) section and click Manage Consumer Details.Salesforce displays the Consumer Key (Client ID) and Consumer Secret (Client Secret).Copy the Client ID and Client Secret and paste them into a text file.Do not continue to the next step unless you have copied the Client ID and Client Secret. You must provide this information to SSPM during the onboarding process.
![]() Connect SSPM to your Salesforce instance.In SSPM, complete the following steps to enable SSPM to connect to your Salesforce instance.
Connect SSPM to your Salesforce instance.In SSPM, complete the following steps to enable SSPM to connect to your Salesforce instance.- Log in to Strata Cloud Manager.Select ConfigurationSaaS SecurityPosture SecurityApplicationsAdd Application and click the Salesforce tile.On the Posture Security tab, Add New instance.On the Permissions page, select whether you want SSPM to connect with Read Permissions only or Read and Write Permissions.On the Authentication page, select Service Principal.Enter your Instance URL and the application credentials (Client ID and Client Secret).Connect.