SaaS Security
Register an Azure AD Client Application
Table of Contents
Expand All
|
Collapse All
SaaS Security Docs
Register an Azure AD Client Application
To enable SaaS Security Posture Management to access information through the Microsoft Graph API,
you register a client app in Azure.
| Where Can I Use This? | What Do I Need? |
|---|---|
|
Or any of the following licenses that include the Data Security license:
|
For certain Microsoft apps, SaaS Security Posture Management performs its configuration scans by
accessing the Microsoft Graph API. To enable SSPM to access this API, you create a
client app in Azure AD with the necessary permissions, and allow access to the app
to users in your organization. During onboarding, SPPM prompts for the Client ID
that uniquely identifies your app.
- Identify the administrator account that you will use to register the client app in Azure.Required Permissions: The account must have Global Admin privileges.Open a web browser to the Azure portal, and log in to the administrator account.Navigate to the App registrations page. To quickly navigate to this page, enter App registrations in the search field at the top of the page.+ New registration.
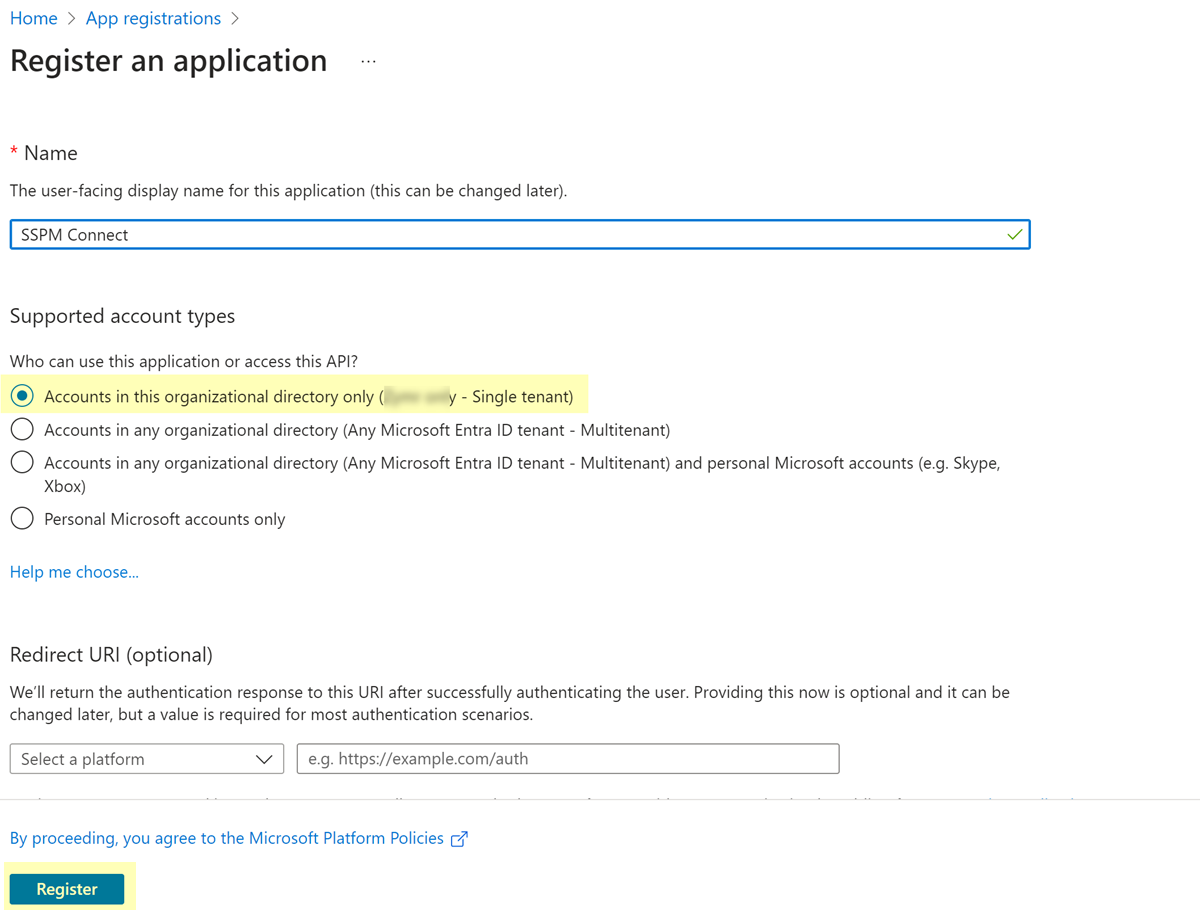
![]() On the Register an app page, specify a name for the app and select Accounts in this organizational directory only as the supported account types that can access the app.The Register an app page contains an optional field for a redirect URI. Leave this field empty.Register the app.
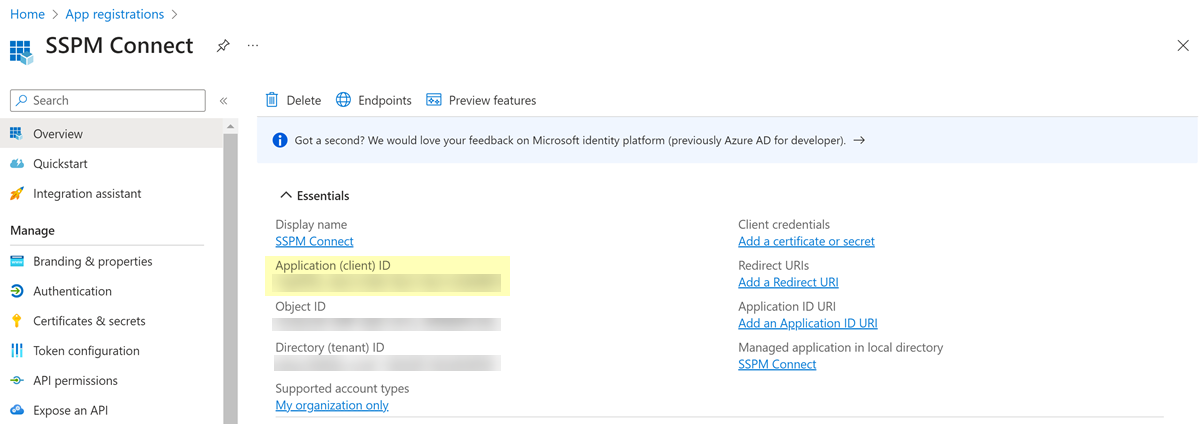
On the Register an app page, specify a name for the app and select Accounts in this organizational directory only as the supported account types that can access the app.The Register an app page contains an optional field for a redirect URI. Leave this field empty.Register the app.![]() The browser displays a configuration page for your app.From the configuration page, copy the app's Client ID and paste it into a text file.Do not continue to the next step unless you have copied the Client ID. You will provide this information to SSPM during the onboarding process.
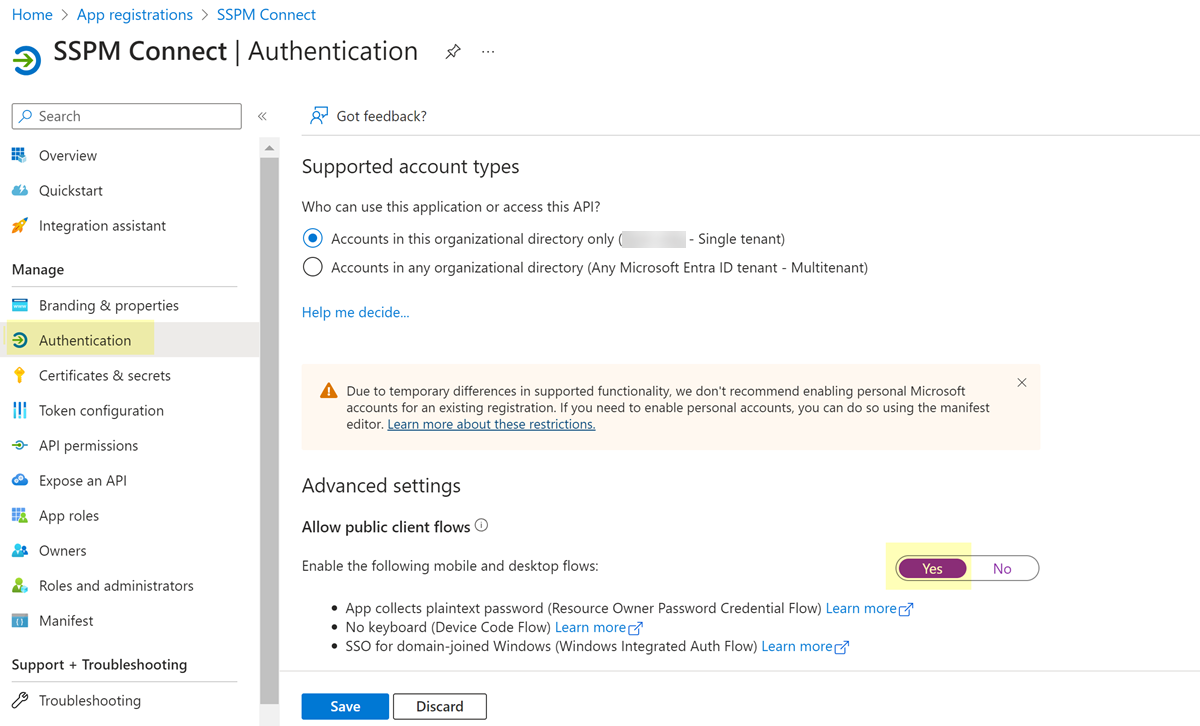
The browser displays a configuration page for your app.From the configuration page, copy the app's Client ID and paste it into a text file.Do not continue to the next step unless you have copied the Client ID. You will provide this information to SSPM during the onboarding process.![]() Configure the app to be a public client app.
Configure the app to be a public client app.- From the left navigation pane, navigate to the Authentication settings.In the Advanced settings section of the Authentication page, Set Allow public client flows to Yes.Save your changes.
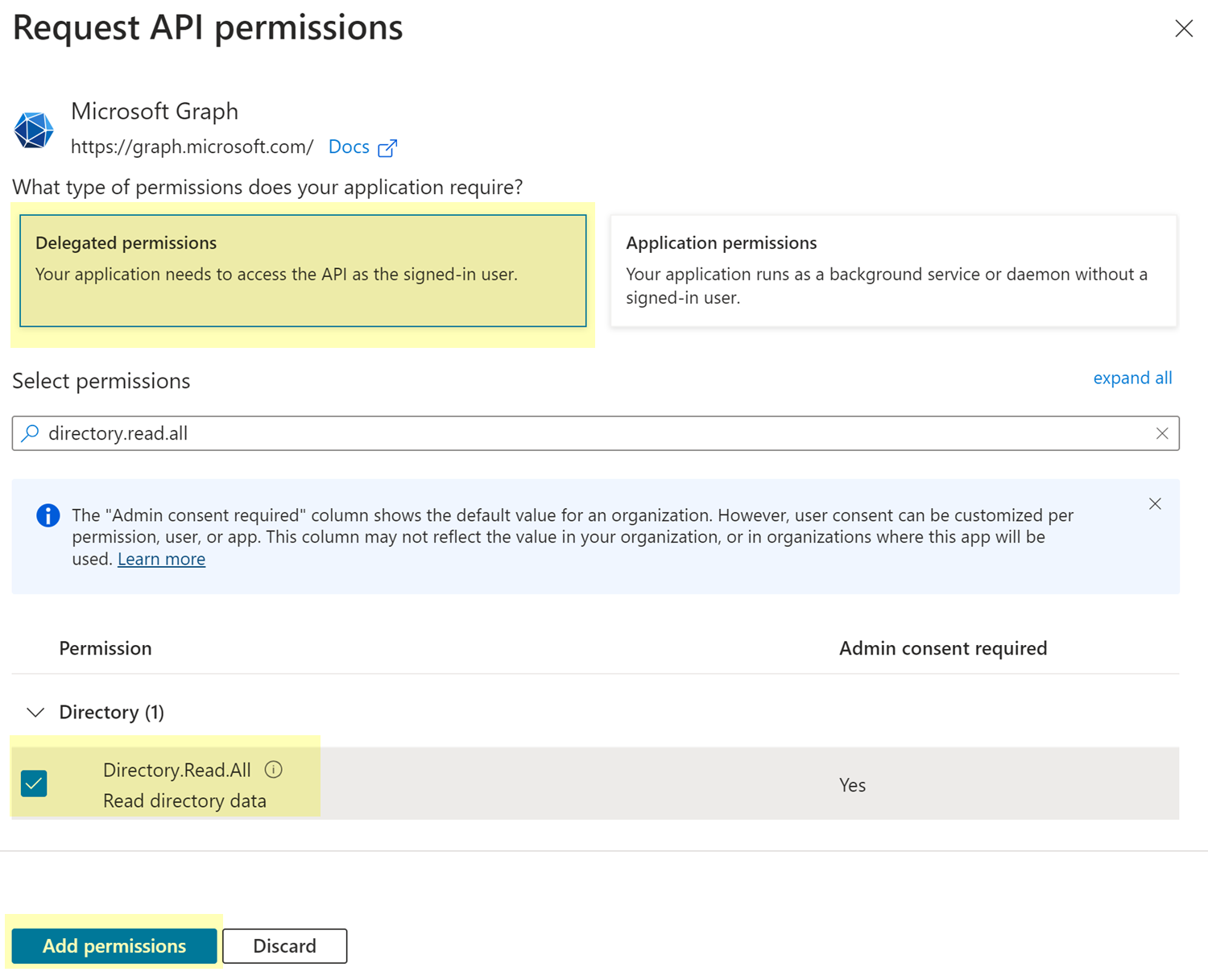
![]() Configure permissions to enable SSPM to read your organization's directory data.
Configure permissions to enable SSPM to read your organization's directory data.- From the left navigation pane, navigate to the API permissions settings.+ Add a permission to open the Request API permissions page.On the Microsoft APIs tab of the Request API permissions dialog, select Microsoft Graph.Select Delegated permissions.From the list of permissions, select the Directory.Read.All permissions. To easily locate these permissions, use the search field to filter the list of permissions.Add permissions.
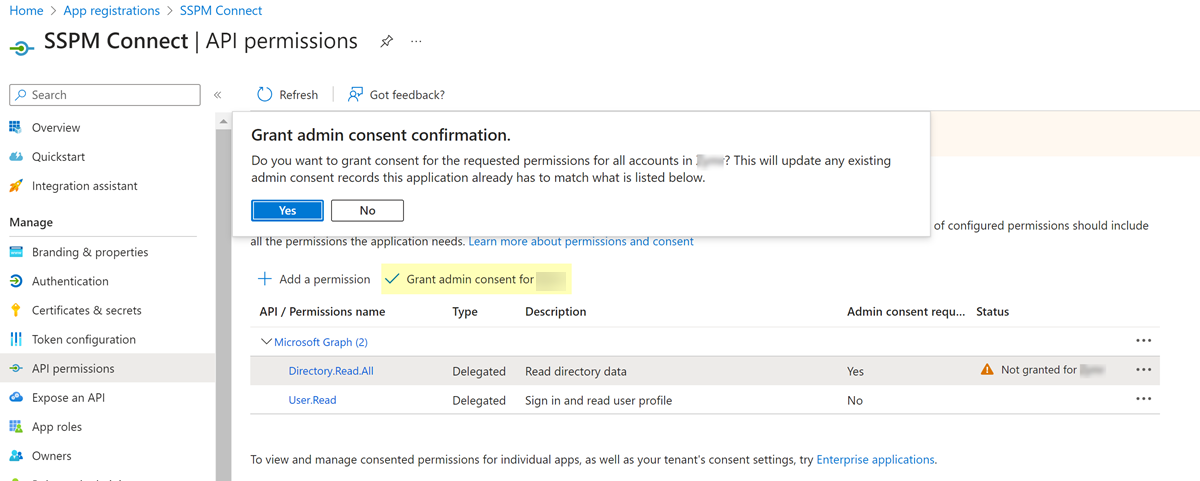
![]() On the Configured permissions page, Grant admin consent for <your-organization>.A confirmation dialog displays. Select Yes in the dialog to confirm that users in your organization who access this app are granted Directory.Read.All permissions.
On the Configured permissions page, Grant admin consent for <your-organization>.A confirmation dialog displays. Select Yes in the dialog to confirm that users in your organization who access this app are granted Directory.Read.All permissions.![]()